Securonix Integration with CrowdStrike |
| CrowdStrike API | Data Type | Description | |
|---|---|---|---|
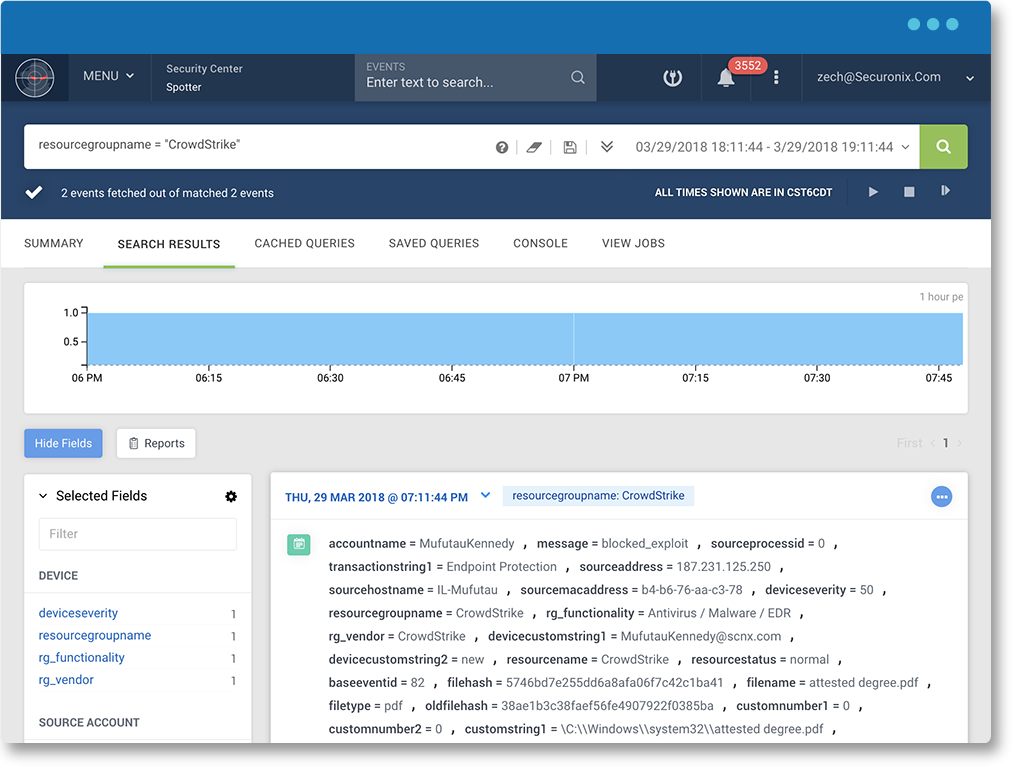
| Securonix has a bi-directional integration with CrowdStrike to collect endpoint events and take action to stop malicious services, block activity, or quarantine suspicious files. | Falcon Streaming API | Real-time detections and audit events from CrowdStrike | The Falcon Streaming API allows you to receive real-time event and alerts from instances as they occur within a single data stream, providing a low-latency, high- throughput delivery mechanism. |
| Securonix uses REST API integration to collect endpoint data from CrowdStrike. This information is enriched and analyzed to detect behavior anomalies and threats to your endpoint devices. | Falcon Query API | Custom IOCs and manage detection status | The Falcon Query API allows you to upload IOCs for monitoring, obtain device information about systems with the Falcon agent installed, search for IOCs and related processes, and manage detection status. |

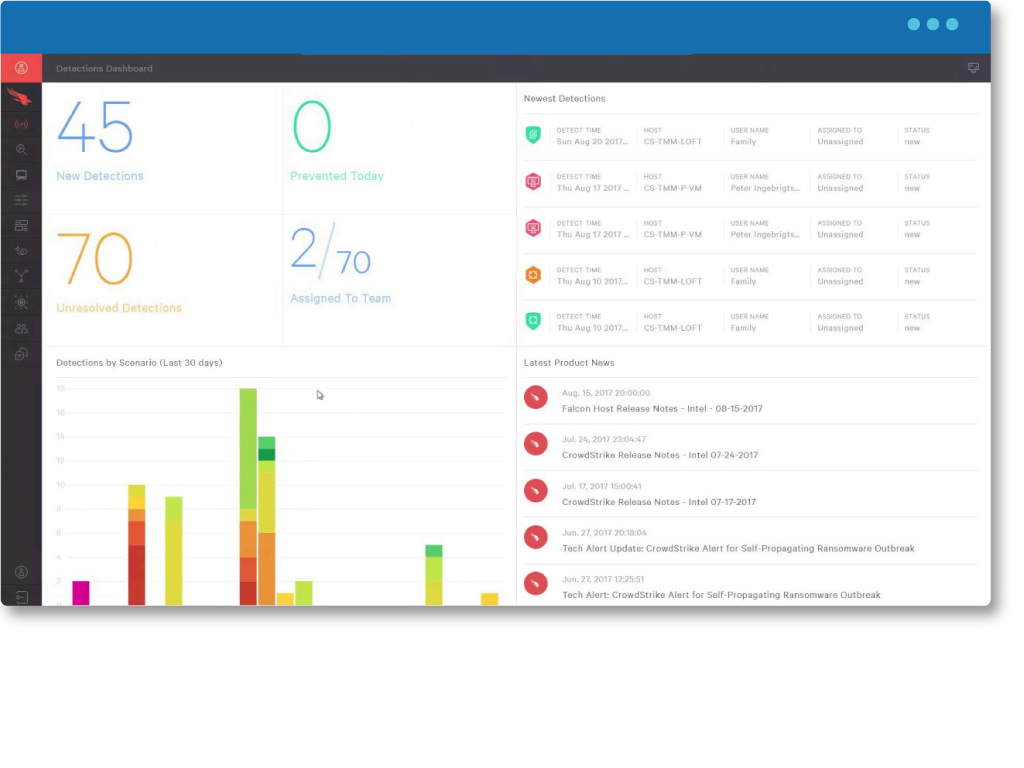
Securonix Threat Modeling
Securonix combines the endpoint events from CrowdStrike with user and entity context and activities, including information from other cloud and on-premises data sources in your environment. It detects suspicious behavior patterns which would indicate an advanced cyberattack against your organization.
Key use cases include:
- Identify account takeover
- Detect endpoint compromise including suspicious process, file hash, and registry changes
- Identify credential theft
- Detect malware or ransomware activities including file encryptions, beaconing, and DGA
- Find data leakage
- Privilege account misuse
- Locate insider threats
- Spot lateral movement

Advanced Threat Monitoring
Monitoring your endpoints is a critical component of detecting advanced threats in your environment. CrowdStrike provides advanced endpoint monitoring capabilities. Combined with the behavior analytics of Securonix, you can correlate endpoint data with contextual information and events from other data sources to help you detect threat patterns.
Securonix also provides visualization of endpoint events through data insights and intelligent incident response through API integration in order to enable your security operations center with the necessary tools to detect and respond to advanced cyberattacks.

Intelligent Incident Response
Upon detecting a threat, Securonix has the ability to respond by enforcing policies in CrowdStrike to take actions such as quarantine files, block connections, or stop malicious processes.