Autonomous Threat Sweeper
Acting as your own dedicated Cyber Rapid Response Team, Securonix Autonomous Threat Sweeper (ATS) automatically and retroactively hunts for new and emerging threats based on the latest threat intelligence from our Threat Labs Team.
Latest ATS Entries
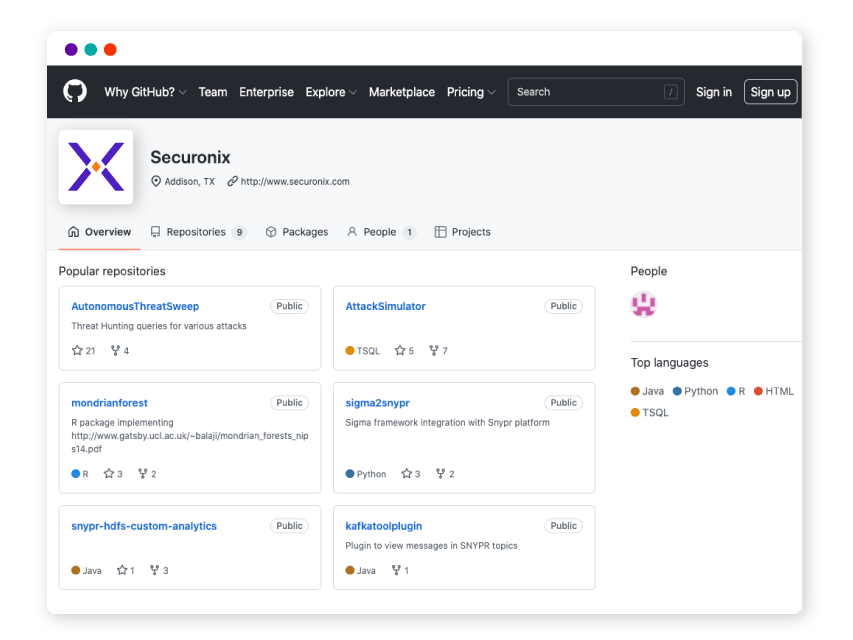
All indicators of compromise (IOC) and Spotter queries are available on our GitHub repository.
—
- Intel Source:
- Cisco Talos
- Intel Name:
- ArcaneDoor_Unmasked
- Date of Scan:
- 2024-04-25
- Impact:
- LOW
- Summary:
- Cisco Talos researchers have discovered a campaign called “ArcaneDoor” aimed at perimeter network devices made by different companies. These devices are important because they control how data goes in and out of networks. The campaign is run by a skilled group, called UAT4356 by Talos, who use special tools like “Line Runner” and “Line Dancer” to do bad things, like changing settings and spying on network traffic.
—
- Intel Source:
- ISC.SANS
- Intel Name:
- Examining_How_Iptables_Configuration_Affects_Honeypot_Data
- Date of Scan:
- 2024-04-25
- Impact:
- LOW
- Summary:
- ISC.SANS researchers have investigated the impact of iptables settings on honeypot efficacy in detecting and evaluating malicious activities. Researchers show how the lack of iptables might reduce the attack surface, resulting in missed possibilities for identifying malware and other malicious behaviors through a comparative examination of honeypot data. The results highlight how crucial iptables is for managing network traffic and how crucial its configuration is for boosting security and facilitating in-depth threat analysis.
Source:
https://isc.sans.edu/diary/Does+it+matter+if+iptables+isnt+running+on+my+honeypot/30862/
—
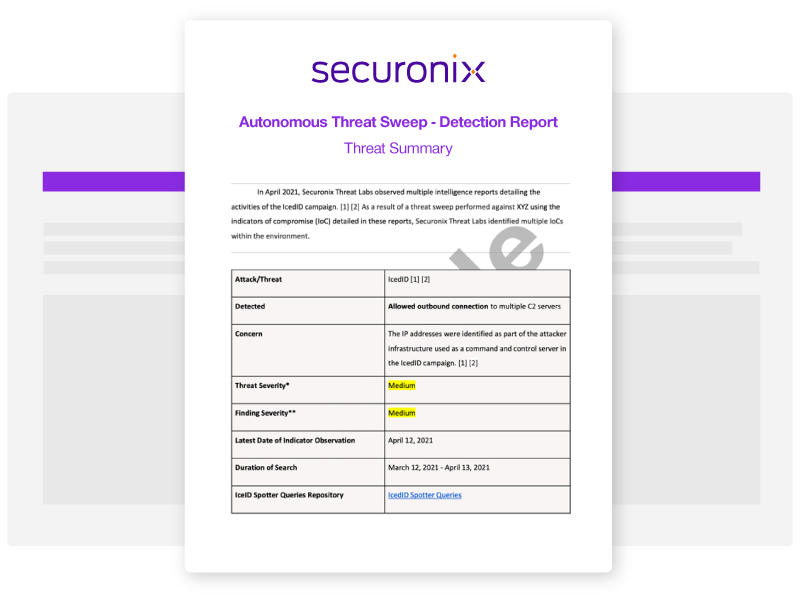
- Intel Source:
- Securonix Threat Labs
- Intel Name:
- An_Investigation_of_Ongoing_FROZEN_SHADOW_Attack_Campaign
- Date of Scan:
- 2024-04-25
- Impact:
- MEDIUM
- Summary:
- Securonix researchers discovered an interesting attack campaign that uses SSLoad malware and Cobalt Strike implants, allowing the attackers to pivot and seize control of the entire network domain. Securonix has dubbed the campaign FROZEN#SHADOW. It also includes the use of the ConnectWise ScreenConnect remote desktop software and Cobalt Strike.
—
- Intel Source:
- Sentinelone
- Intel Name:
- The_Ransomware_Evolution
- Date of Scan:
- 2024-04-25
- Impact:
- LOW
- Summary:
- Researchers at SentinelOne have studied the ways in which ransomware affiliates have changed over time, concentrating on how they are increasingly utilizing stolen data to make extra money on top of the initial ransom demands. It looks at current examples that shed information on the growing field of cyber extortion, such as the cooperation between affiliates and organizations like Dispossessor, Rabbit Hole, and RansomHub.
—
- Intel Source:
- CYFIRMA Research
- Intel Name:
- A_Sophisticated_Anti_Analysis_Info_Stealer_Named_Fletchen_Stealer
- Date of Scan:
- 2024-04-25
- Impact:
- LOW
- Summary:
- CYFIRMA researchers identified an information stealer called Fletchen Stealer, a malware designed with sophisticated anti-analysis tactics and sold as a service by its maker, posing a huge cybersecurity concern. The study investigates the variety of anti-analysis strategies used by threat actors to mask the true nature of the malware through in-depth analysis.
—
- Intel Source:
- Sucuri
- Intel Name:
- Cookie_hijacking_analysis
- Date of Scan:
- 2024-04-24
- Impact:
- LOW
- Summary:
- Cesar Anjos Sucuri’s Malware Researcher wrote in Sucur;’s blog how it’s important to understand what cookie hijacking is, when and how it occurs, and how to protect yourself and your website against it. Cookies usually have sensitive information, including session tokens that authenticate users to a web application. By hijacking the cookies, attackers can impersonate users and gain unauthorized access to private accounts and sensitive data.
Source:
https://blog.sucuri.net/2024/04/what-is-cookie-hijacking.html
—
- Intel Source:
- ASEC
- Intel Name:
- An_Infostealer_strain_made_with_Electron
- Date of Scan:
- 2024-04-24
- Impact:
- LOW
- Summary:
- ASEC has observed a new Infostealer strain made with Electron. Electron is a framework that lets one develop apps using JavaScript, HTML, and CSS. Discord and Microsoft VSCode are major examples of applications made with Electron. The threat actor in this attack case applied this installer format to the malware.
—
- Intel Source:
- Trend Micro
- Intel Name:
- Cracking_Down_Grandoreiro_Banking_Trojan
- Date of Scan:
- 2024-04-24
- Impact:
- LOW
- Summary:
- This month Trend Micro Intel team discussed their contributions to an Interpol-coordinated operation to help Brazilian and Spanish law enforcement agencies analyze malware samples of the Grandoreiro banking trojan. Grandoreiro spreads through phishing emails, malicious attachments, or links leading to fake websites. These emails often mimic legitimate organizations, such as banks or financial institutions, to trick users into downloading and executing the malware.
—
- Intel Source:
- Cyble
- Intel Name:
- DragonForce_Ransomware_is_linked_to_a_Lockbit_Builder
- Date of Scan:
- 2024-04-24
- Impact:
- MEDIUM
- Summary:
- Cyble Labs identified a DragonForce ransomware binary based on LOCKBIT Black ransomware, suggesting the threat actors behind DragonForce used a leaked builder of LOCKBIT Black ransomware to generate their binary.
Source:
https://cyble.com/blog/lockbit-blacks-legacy-unraveling-the-dragonforce-ransomware-connection/
—
- Intel Source:
- Seqrite Labs
- Intel Name:
- Attacks_on_Indian_Government_Are_Increasing_by_Pakistani_APTs
- Date of Scan:
- 2024-04-24
- Impact:
- MEDIUM
- Summary:
- Researchers at Seqrite Labs have uncovered several cyberattack operations in which they have detected the use of different remote access tools (RATs), such as AllaKore RAT and Crimson RAT. They explore the mechanics of these attacks, the actions of the attackers, and the features of the malicious software that is employed. The report also discusses the increase of cyberattacks by Pakistan-affiliated Advanced Persistent Threat (APT) groups, namely SideCopy and APT36 (Transparent Tribe), against Indian government institutions.

Shared Security Content on Sigma
Securonix Threat Labs publishes up-to-date IOCs and threat hunting queries on Sigma, allowing you to tap into a vast community of collective defense and stay ahead of emerging threat research.
What's New from Threat Labs
-
BlogAnalysis of DEV#POPPER: New Attack Campaign Targeting Software Developers Likely Associated With North Korean Threat ActorsLearn More
-
BlogSecuronix Threat Research Security Advisory: Analysis of Ongoing FROZEN#SHADOW Attack Campaign Leveraging SSLoad Malware and RMM Software for Domain TakeoverLearn More
-
BlogSecuronix Threat Research Knowledge Sharing Series: Detecting DLL Sideloading Techniques Found In Recent Real-world Malware Attack ChainsLearn More