- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Cloud Security

Cloud solutions are growing in adoption because they offer organizations increased operational efficiency, higher scalability, and improved agility. While cloud adoption continues at a rapid pace, cloud security monitoring has lagged behind. Many cloud service providers provide basic security controls to protect their platform, but they do not guard against sophisticated threats. It is the customer’s responsibility to secure their applications and cloud data.
Cloud security concerns include:
- Data loss and data leakage
- Data privacy
- Account hijacking
- Lack of visibility of who can access the cloud data
- Vulnerabilities in cloud based applications
- Compliance requirements
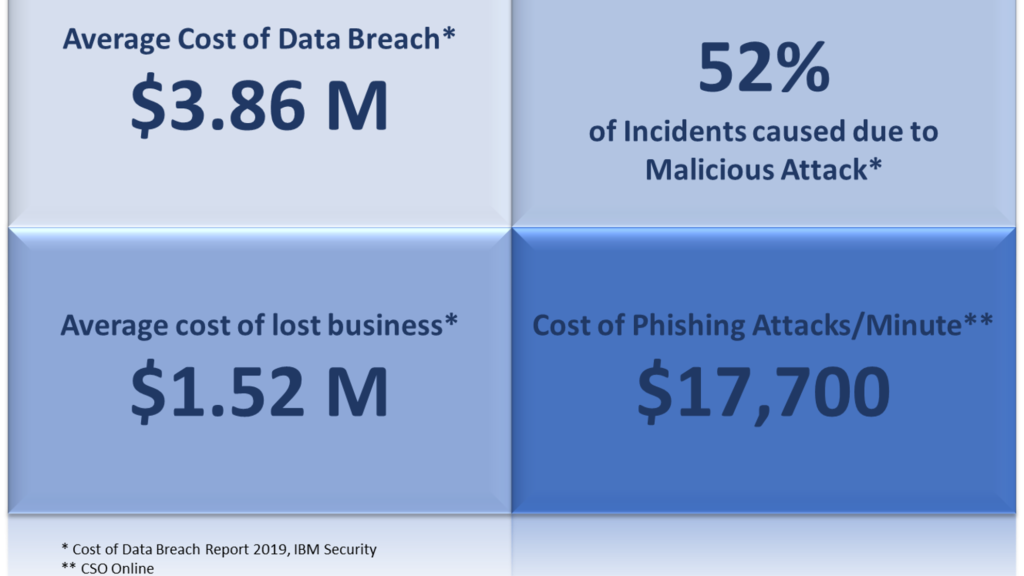
A cloud data breach can result in financial losses, damage to brand reputation, fines, legal penalties, and damage to an organization’s business and IT infrastructure.
Cloud security is critical to protect your data, help you adhere to regulatory compliance, and safeguard your customers’ privacy – which in turn protects your organization from the reputational, financial, and legal ramifications of a data breach.
The Path To Stronger Cloud Security
It is crucial to assess your cloud security practices across 5 core areas to make sure that your data is protected, and your security team can detect and respond to potential threats.
- Data Encryption & Data Privacy – Encryption ensures your cloud data is not tampered or misused by cyber threat actors or accessed by unauthorized users.
- Identity & Access Management – The ability to monitor privileged users is key to prevent unauthorized access and account hijacking.
- Cloud SIEM – Cloud native SIEM overcomes the visibility and control limitations of legacy SIEMs. Cloud SIEMs are architected to provide complete visibility and better control over cloud applications. Wider and tighter integration with cloud apps and services helps provide effective cloud monitoring and faster incident response.
- Analytics-Based Threat Detection – User and entity behavior analytics (UEBA) helps to detect and uncover advanced insider threats, fraud, cloud data compromise, and non-compliance with fewer false positives than rule-based approaches.
- Threat Hunting – Search for specific threats that may have evaded your existing security on live and historical data.
- Wider Integration, APIs & Connectors – Wide integration and multiple APIs and connectors helps to provide faster detection and response to threats.
No matter where your organization is within its cloud journey, cloud security is vitally important. For cloud data security and compliance, Securonix Next-Gen SIEM equips your security teams with the visibility required to detect and respond to threats to your cloud environments.







