- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
Securonix observes a significant uptick in phishing, business email compromise, and data compromise attacks.
By Oleg Kolesnikov, Kayzad Vanskuiwalla, Aditya TS, Securonix Threat Research Team
The Securonix “COVID-19 Work From Home” task force continues to research the cyber security challenges organizations are facing during this pandemic. In this briefing we are laser focused on phishing campaigns, business email compromise, and increasing data compromise.
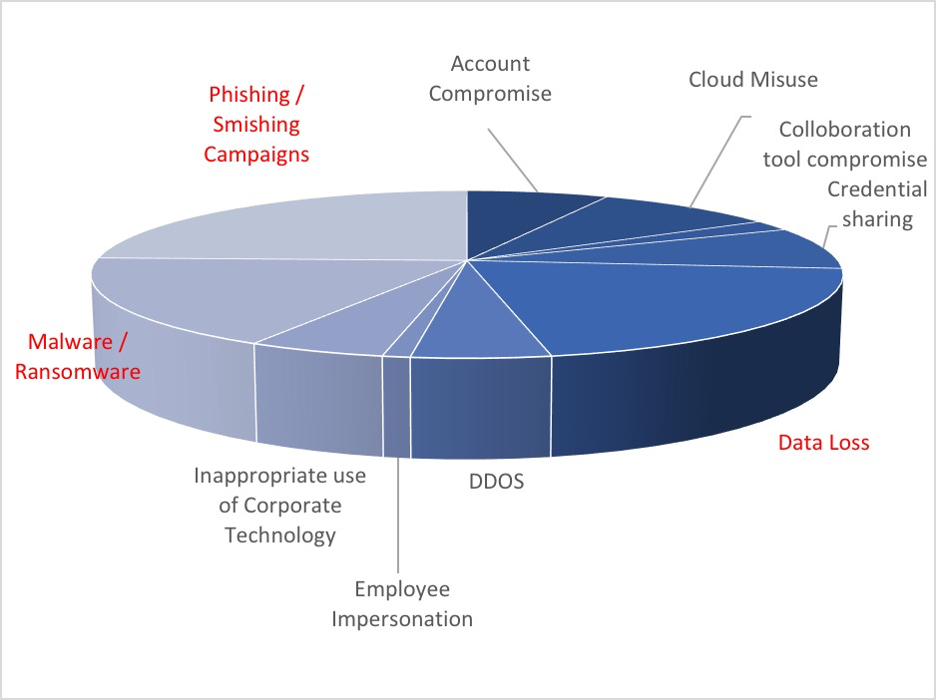
Phishing Campaigns
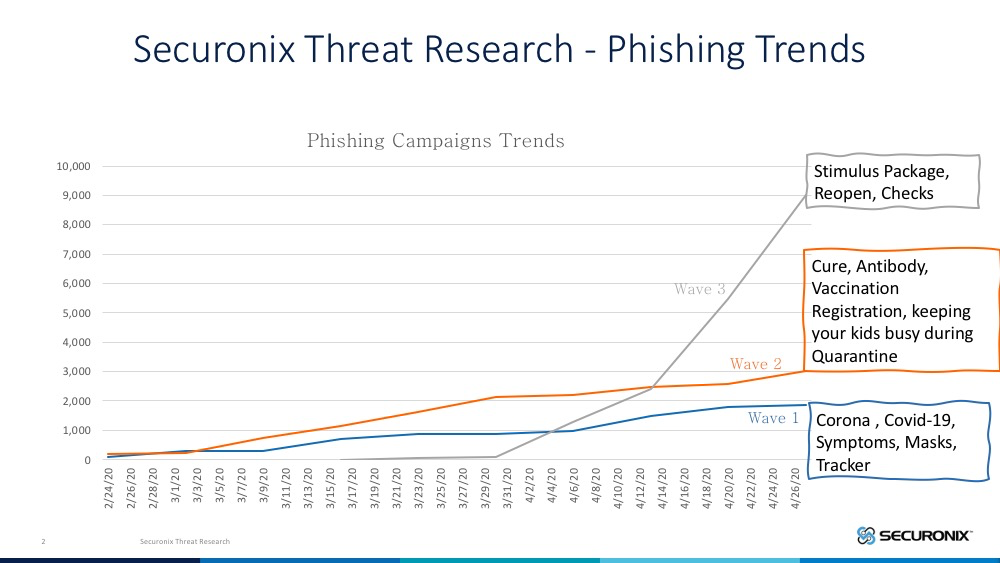
It should not be a surprise to security teams that attackers are tuned in to the latest news and craft emails with subjects relating to current affairs in order to make it compelling for victims to open them. When we dig into the subjects used during these phishing campaigns, there are 3 clear waves:
- Wave 1: Focused on coronavirus, the symptoms, and how to self-diagnose.
- Wave 2: Tailored towards the cure/vaccine, disease progress tracking, and tips to engage kids at home.
- Wave 3: Focused on stimulus checks and impersonation emails with subjects focused on reduction in force, layoff forecasts, and end of work from home/reopen.
Some of the attack patterns observed are outlined below:
A Portfolio Associate from a global investment company was phished using a CDC-themed phishing email. A fake OneDrive login page was presented. The associate provided their credentials, leading to the suspicious forwarding of emails to an unknown Gmail account.
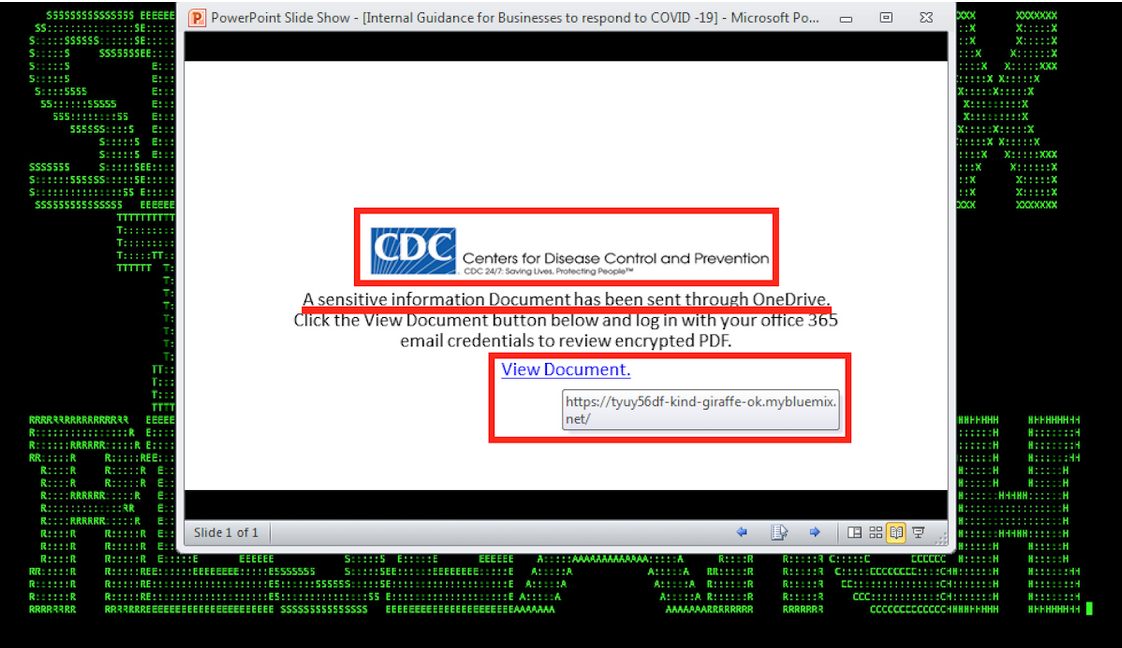
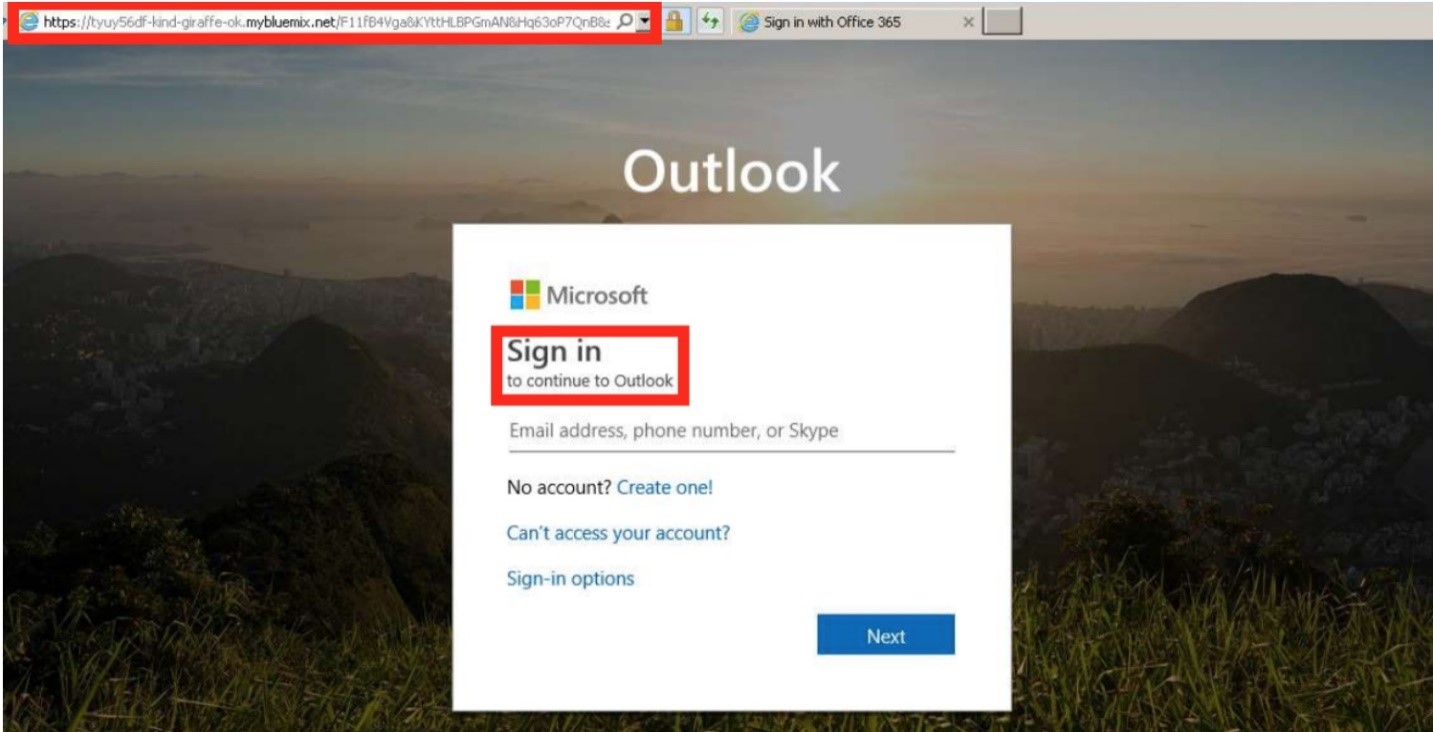
Another email campaign involved the use of Google Drive or One Drive links in an attachment or the body of the email in order to evade existing email security solutions. When the victims clicked on these sites, the URLs were redirected to malicious sites which dropped a malicious payload.
In one such email, the “Download PDF” link took the user to a file hosted on One Drive, which then redirected to a different site that dropped the malicious payload onto the victim’s machine.
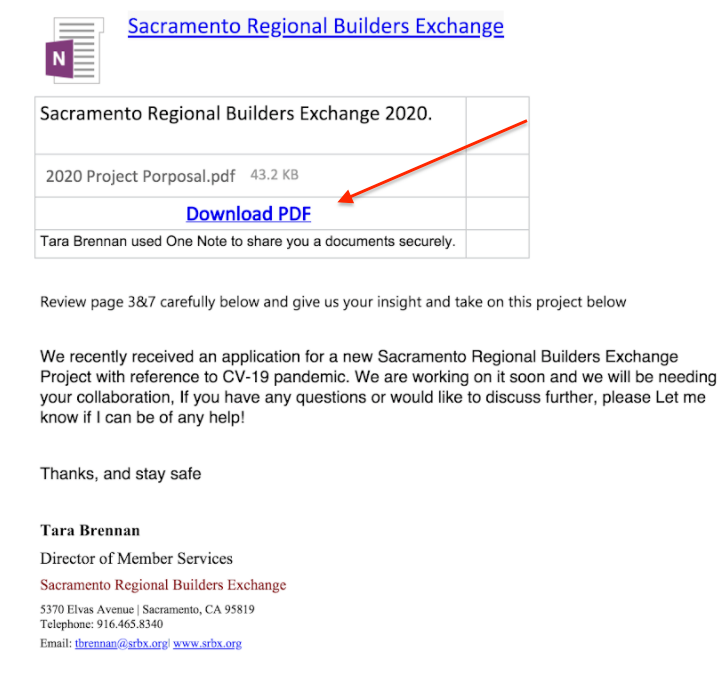
Similar campaigns have also been used as part of the initial recon process to gather basic details about users. Using forms and other input capture features offered by these platforms, attackers send out links that can avoid getting picked up by email security solutions.
One organization received emails from senders pretending to be one of America’s top retailers with subjects such as the ones below:
Our Covid-19 protection masks can be shipped out tomorrow
Covid-19 protection masks arrived to our US warehouse
The links take them to a Google Form which asks the users to key in their basic information.
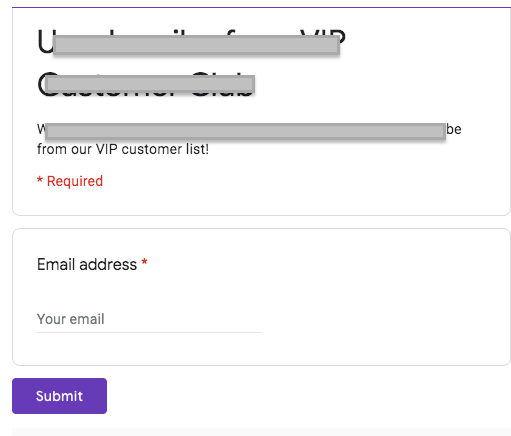
Every single user who provided their email address received further phishing emails searching for other basic information typically used for security questions with many online services.
Business Email Compromise (BEC)
Another type of phishing campaign that is significantly more frequent than before is business email compromise (BEC). BEC is when an attacker hacks into a corporate email account and impersonates the real owner to defraud the company, its customers, partners, and/or employees into sending money or sensitive data to the attacker.
Perpetrators use a variety of tactics to fool their victims. A common scheme involves the criminal group gaining access to a company’s network through a spear phishing attack and the use of malware.
In the past BEC was harder to perform, as the victim could usually walk into the sender’s office or speak to the individual directly on the phone to confirm a suspicious email. Given most, if not all of the work force is at home, now is a perfect time for attackers to launch these types of attacks.
The attack pattern observed is outlined below:
An executive from a major pharmaceutical company received a “COVID-19 Relief” document via email.
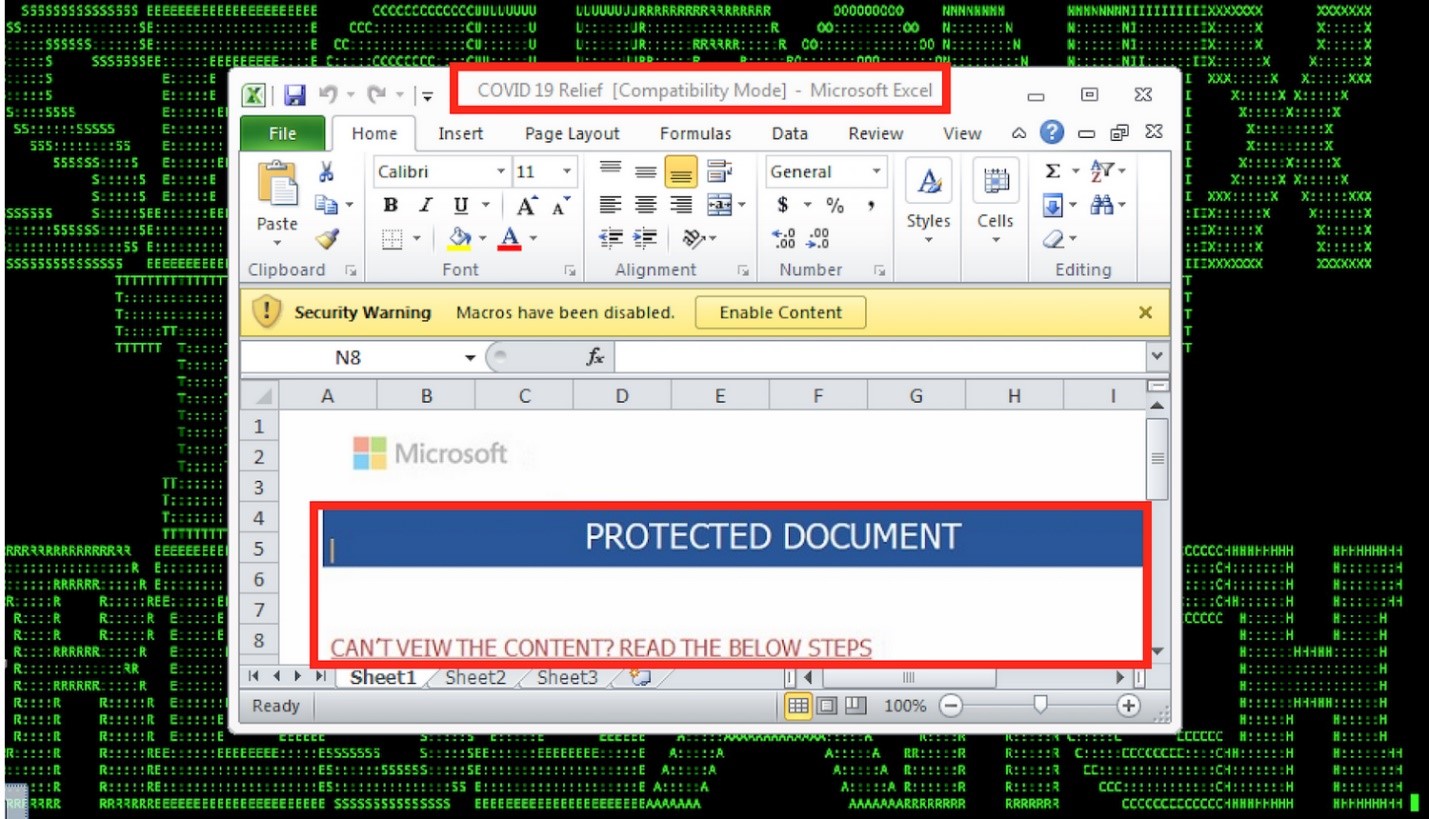
The executive opened the weaponized document, which ended up spawning suspicious scripts using Rundll32, and went on to further infect the machine.
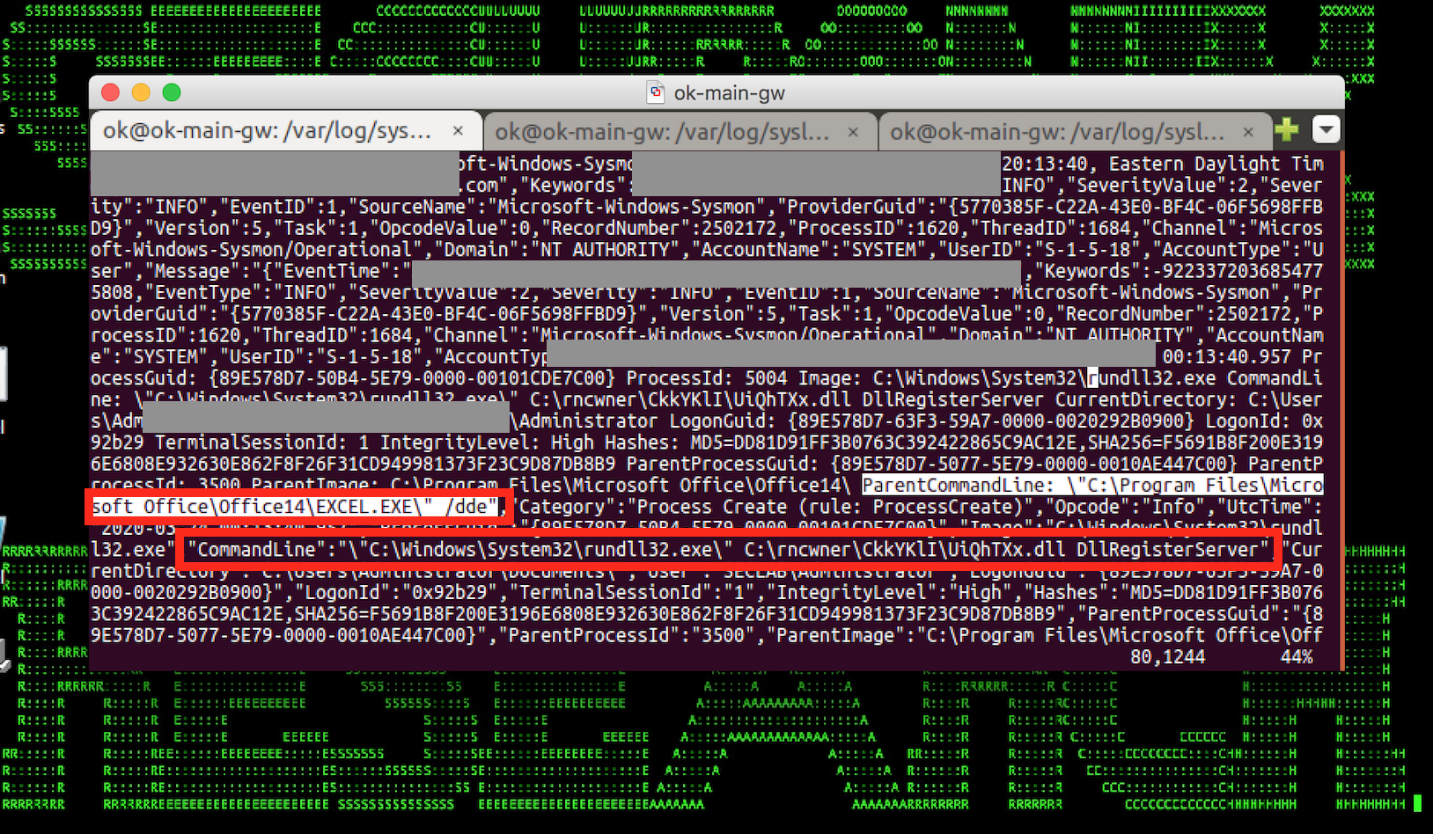
In the last couple of weeks we have observed a surge in the number of new domains registered that are themed around corona/COVID-19 stimulus/financial recovery, and are being used to maliciously target people.
The domains listed below are a few such ones created less than 15 days ago that have been seen as part of phishing campaigns luring people to provide personal details or money by taking advantage of the recent $2 trillion stimulus package to help Americans recover.
coronafinancehelp[.]com
coronavirusfinancegroup[.]com
covid-19financialplanner[.]com
covid19homestimuluspackage[.]com
In addition to leveraging these impostor domains and URLs, scammers have also impersonated government officials and law enforcement officers on the telephone, stooping to such low levels as to intimidate and threaten people to pay fines or provide sensitive information over the phone.
Data Compromise
Due to shelter in place orders, many companies have been forced to suddenly implement contingent operations plans, which include allowing employees who do not usually have remote access to company systems, access to business-critical applications. The risks associated with remote connectivity are now magnified because the company has not been able to perform a full analysis of the risks and security measures to put in place beforehand.
In earlier advisories, we covered more about the impact caused by unintentional insiders by not following good security practices when it comes to secure remote connections, visiting nonbusiness websites, or downloading and installing freeware or other applications.
We are also observing a gradual increase in malicious insiders using this period as an opportunity to snoop and aggregate sensitive data to eventually exfiltrate later.
Our study shows an increased level of data egress activity from corporate laptops and endpoints during the time it is not connected on the corporate VPN. The ability to access data locally residing on the laptops is misused by insiders (employees and contractors) to exfiltrate the data while the device is not connected to the network. Data loss prevention (DLP) and other endpoint agents give visibility into this activity when the user reconnects to the VPN, and the transactions are reconciled back to the DLP or the endpoint detection and response (EDR) manager.
One such incident involved a design engineer uploading over a thousand CAD design files to a personal storage site while not on the corporate VPN. The user did not connect to the network for the next 15 days. Eventually they connected to the network over the weekend, intentionally. All of the activity done during that period was published during the weekend, thus increasing the amount of data to be analyzed by the security teams in an effort to bury the incident among the noise. In this case, Securonix identified this activity as coming in from an account/asset after a period of dormancy and was able to identify abnormal offline activity and prioritize the incident for the security team.
Companies are also maximizing their usage of cloud content and collaborative platforms now more than ever. Platforms like Sharepoint, Google Drive, Box, and Dropbox have seen an increased amount of traffic.
Securonix Recommendations
Educate your workforce about the increase in phishing activity. Some simple preventative tips include:
- Check the legitimacy of the email sender and email domain before responding.
- Do not click on links or attachments from unverified senders.
- Pay close attention to spellings and errors, especially for unusual emails that seem to be coming from executives.
- Report any suspicious emails to IT immediately.
Deploy security monitoring controls that analyze incoming and outgoing emails for possible:
- Phishing attacks
- Business email compromise
- Malware payloads
- Command and control (C2) communication
How Securonix is Helping Customers
Securonix has recently announced their phishing analyzer capability. It uses machine learning-based visual similarity analytics to detect advanced phishing and business email compromise.


