- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Sina Chehreghani , Kayzad Vanskuiwalla
The Monthly Intelligence Insights published by Securonix Threat Labs provides a summary of the total number of threats tracked and highlights the top three threats during the month. It also provides a synopsis of the threats, indicators of compromise, TTPs, tags and security awareness. This may be followed by a comprehensive threat summary from Threat Labs and search queries from the Threat Research team.
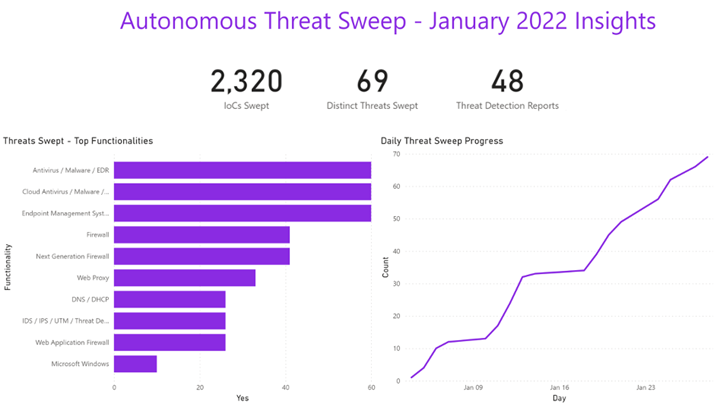
In January Securonix Autonomous Threat Sweeper detected 2,320 IOCs, 69 distinct threats and reported 48 threat detections. The top three threats swept include antivirus/malware/EDR, cloud antivirus/malware/EDR and endpoint management systems.
New SysJoker backdoor targets Windows, Linux, and macOS
(Published on: January 11, 2022)
Researchers at Intezer Labs have discovered SysJoker, a new multi-platform backdoor that targets Windows, Mac, and Linux operating systems. SysJoker is written in C++ and targets specific OS with tailored samples. This campaign was initiated during the second half of 2021. SysJoker masquerades as a system update and discovers C2 from an encoded text file hosted on Google Drive. Upon gaining the initial foothold on the targeted instance, the backdoor is able to collect system data, gain persistence and communicate to the C2 server under the attacker’s control.
Threat Labs Summary:
- Multi-platform (Linux macOS, Windows) backdoor
- Masquerades as a system update
- Used for espionage and payload delivery
- 17 IOCs are available on Github and automatically swept against for Securonix Autonomous Threat Sweeper customers
- TTPs related to SysJoker include but are not limited to the following:
- Rare files downloaded to and executed from C:\ProgramData\RecoverySystem
- Followed by rare process creations from C:\ProgramData\SystemData\ (specifically igfxCUIService.exe the Intel Graphics Common User
- Followed by Rare Registry modifications or updates against “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run”
Tags: Malware Family: SysJoker | Target: Windows, Linux, macOS | Tools: Powershell, Google Drive
WhisperGate malware targeting Ukrainian organizations and Operation Bleeding Bear
(Published on: January 15, 2022)
Microsoft and Elastic Security have been alerted about an active disruptive malware attack against Ukrainian government organizations. They identified intrusion activity in early January and noted possible Master Boot record wiper activity. This kind of wiping activity could have been done by a unique malware which they dubbed as WhisperGate. This malware attack happened in the dual stage of which the first stage overwrites the Master Boot Record (MBR) on victim systems with a ransom note. As part of the second stage the threat actor deploys file corrupting malware which is hosted on a discord channel.
Threat Labs Summary:
- Nation state targeting Ukraine government
- Overwrites / Targets the MBR (master boot record)
- Includes file corruptor malware (that may be downloaded from a discord link)
- 5 IOCs are available on Github and automatically swept against for Autonomous Threat Sweeper customers
- TTPs related to WhisperGate include but are not limited to the following:
- Rare files downloaded to and executed from any C:\PerfLogs, C:\ProgramData, C:\, and C:\temp (often called stage1.exe)
- Followed by suspicious files downloaded from the discord cdn i.e. https://cdn.discordapp.com/attachments/ (Prone to false positives – always combine with other TTPs)
- This is usually followed by or in combination with a rare executable (usually stage2.exe) and also includes the following:
- rar file written in the temp directory via VB script (i.e with the process – C:\Windows\System32\WScript.exe)
- Exclusions using PowerShell, i.e detect the process powershell.exe with new exclusion paths being set on a system in the command line parameters “-ExclusionPath”
- Stop Windows Defender via AdvancedRun.exe or specifically look for rare attempts to “stop WinDefend”.
- This can also be used to launch Powershell to delete the Defender directory – “rmdir ‘C:\ProgramData\Microsoft\Windows Defender’”
- The final stage includes the file corrupter with a set list of known file names
- .3DM .3DS .602 .7Z .ACCDB .AI .ARC .ASC .ASM .ASP .ASPX .BACKUP .BAK .BAT .BMP .BRD .BZ .BZ2 .C .CGM .CLASS .CMD .CONFIG .CPP .CRT .CS .CSR .CSV .DB .DBF .DCH .DER .DIF .DIP .DJVU.SH .DOC .DOCB .DOCM .DOCX .DOT .DOTM .DOTX .DWG .EDB .EML .FRM .GIF .GO .GZ .H .HDD .HTM .HTML .HWP .IBD .INC .INI .ISO .JAR .JAVA .JPEG .JPG .JS .JSP .KDBX .KEY .LAY .LAY6 .LDF .LOG .MAX .MDB .MDF .MML .MSG .MYD .MYI .NEF .NVRAM .ODB .ODG .ODP .ODS .ODT .OGG .ONETOC2 .OST .OTG .OTP .OTS .OTT .P12 .PAQ .PAS .PDF .PEM .PFX .PHP .PHP3 .PHP4 .PHP5 .PHP6 .PHP7 .PHPS .PHTML .PL .PNG .POT .POTM .POTX .PPAM .PPK .PPS .PPSM .PPSX .PPT .PPTM .PPTX .PS1 .PSD .PST .PY .RAR .RAW .RB .RTF .SAV .SCH .SHTML .SLDM .SLDX .SLK .SLN .SNT .SQ3 .SQL .SQLITE3 .SQLITEDB .STC .STD .STI .STW .SUO .SVG .SXC .SXD .SXI .SXM .SXW .TAR .TBK .TGZ .TIF .TIFF .TXT .UOP .UOT .VB .VBS .VCD .VDI .VHD .VMDK .VMEM .VMSD .VMSN .VMSS .VMTM .VMTX .VMX .VMXF .VSD .VSDX .VSWP .WAR .WB2 .WK1 .WKS .XHTML .XLC .XLM .XLS .XLSB .XLSM .XLSX .XLT .XLTM .XLTX .XLW .YML .ZIP
-
- This is followed by attempts to remove traces with the CMD process – cmd.exe and rare command line parameters in “Del /f /q <running process path>”
Tags: Malware Family: WhisperGate | Threat Vector: MBR | Cyber Operation: Bleeding Bear | Industries: Government Organisations
Espionage campaigns targeting Energy and Industrial Technology organizations
(Published on: January 16, 2022)
A security researcher came across an espionage campaign targeting primarily renewable energy and industrial technology organizations. These attacks go way back to 2019 with 15 companies being targeted. Phishing was used as the threat vector (Mail Box phishing kit) and compromised legit websites were used to host phishing pages. High profile organizations (HoneyWell, Schneider Electric) from industries such as OT (Operational Technology) and ICS (Industrial Control System) were targeted. These attacks have been allegedly attributed to APT28 and KONNI Group, considering their frequent usage of ‘eu3.biz’, as these were among the Indicators of this campaign.
Threat Labs Summary:
- Multiple threat actors identified — APT28 & KONNI
- Targeting ICS and OT technologies
- Specifically targeting renewable energy, environmental protection organizations
- Used for espionage and payload delivery
- 43 IOCs are available on Github and automatically swept against for Autonomous Threat Sweeper customers
Tags: Threat Vector: Phishing | Industries: OT, ICS, Telecommunications, Education | Adversaries: APT28, KONNI Group
For a full list of the search queries used on Autonomous Threat Sweeper to detect SysJoker and Whispergate go to our Github page. We would like to hear from you. Please reach out to us at [email protected].
Contributors: Amit Roshan, Rajesh Lohani, Mohammed Zibran Pawar, Yashraj Manshani


