- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, Ella Dragun
The Monthly Intelligence Insights provides a summary of curated industry leading top threats monitored and analyzed by Securonix Threat Labs during October. The report additionally provides a synopsis of the threats, indicators of compromise (IOCs), tactics, techniques and procedures (TTPs), and related tags. This may be followed by a comprehensive threat summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below mentioned threats, refer to our Threat Labs home page.
During the month, Threat Labs has analyzed and monitored major threat categories, including multiple cyber campaigns involving ransomware and malware. Of note are two exploits: the Lazarus group deploying a ransomware tool on target systems that exploits the Dell DBUtil flaw to disable the monitoring of all Windows Security on compromised machines and a discovery of same threat group of hackers using the DLL Side-Loading attack technique (T1574.002) by abusing legitimate applications in the initial compromise stage to achieve the next stage of their attack process.
Furthermore, an increasing number of vulnerabilities recorded this month include several exploit attempts targeting CVE-2022-40684 on the network and requests originating from the malicious IP addresses. Hackers are exploiting the Text4Shell vulnerability with observed exploit attempts targeting two zero-day vulnerabilities in Microsoft Exchange Server tracked as CVE-2022-41040 and CVE-2022-41082. Finally, the Lazarus group exploited the Dell driver vulnerability to disable Windows Security.
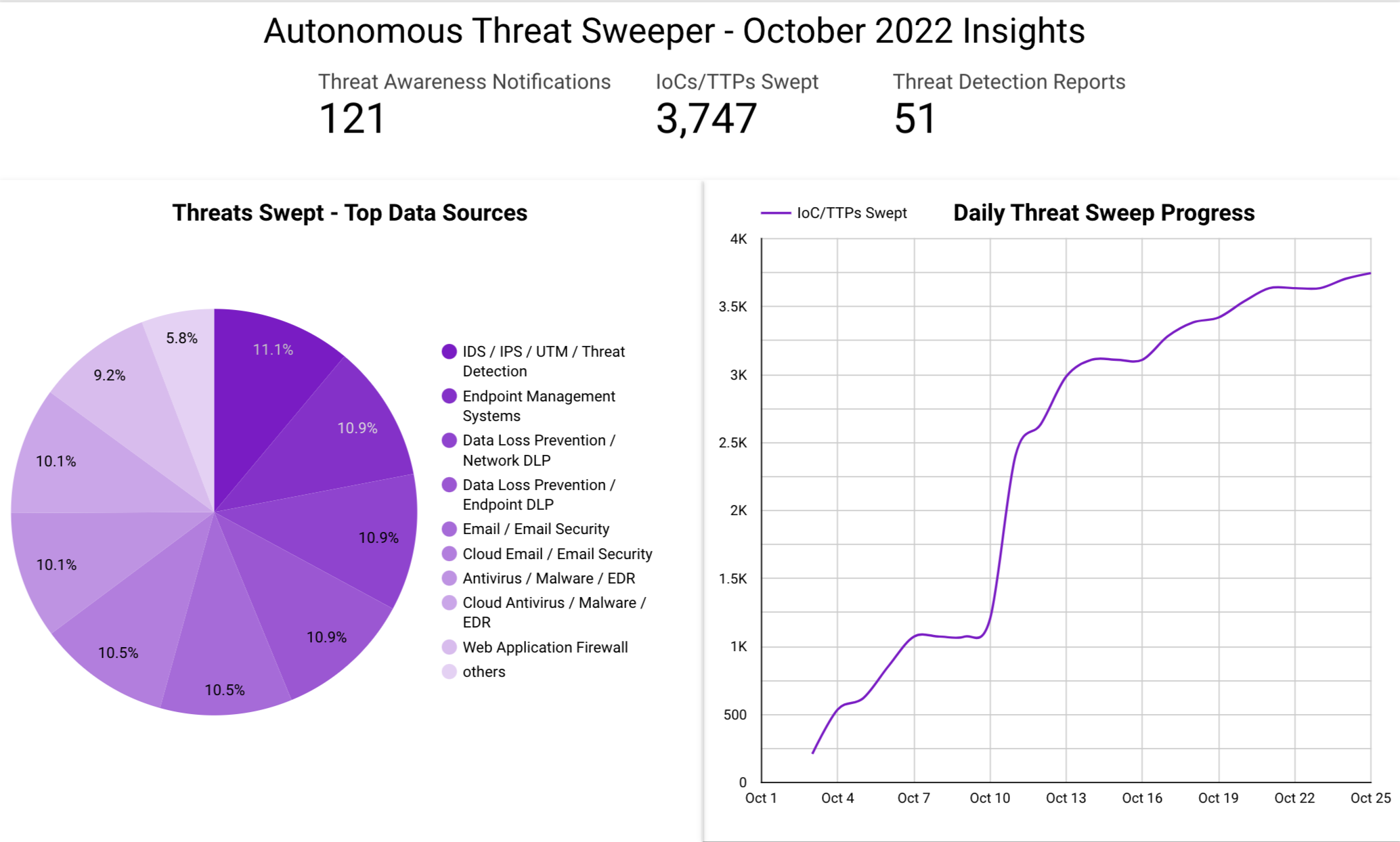
In October, Securonix Autonomous Threat Sweeper identified 3,747 IOCs, 121 distinct threats, and reported 51 threat detections. The top data sources swept against include IDS/IPS/UTM/Threat Detection, Endpoint Management Systems, Data Loss Prevention, and Email / Email Security.
Lazarus threat group is active and on the rise again
(Originally published on October 2022)
Recently, the Lazarus group has been observed using various attack methods. The Lazarus gang, a North Korean state-sponsored cyber threat group, is known for trojanizing open-source tools and is becoming more dangerous everyday. . This month Lazarus launched a couple of campaigns on different targets. Among these are deploying a ransomware tool on target systems that exploits the Dell DBUtil flaw to disable the monitoring of all Windows Security on compromised machines. It started with spearphishing emails containing malicious Amazon-themed documents and targeted an employee of an aerospace company in the Netherlands. The tool used in this campaign indicated the first recorded abuse of the CVE‑2021‑21551 vulnerability. The primary goal of the attackers was data exfiltration.
In another campaign the Lazarus group hackers used the DLL Side-Loading attack technique (T1574.002) by taking advantage of legitimate applications in the first stage of the compromise stage to get to the next phase of their attack process. It could be described as a malware execution technique that allows the malicious DLL to be executed by changing its name to the filename of the normal DLL located in a different path that the real program refers to. The Lazarus group has been abusing wsmprovhost.exe and dfrgui.exe both of which are legit MS files. Using a DLL that is acting in a normal process memory area to carry out malicious acts is considered to be an attempt to bypass the behavior detection of security software.
From the defenders’ point of view, it seems more effective to limit the possibilities of initial access than to block the robust toolset that would be installed after determined attackers gain a foothold in the system. As in many cases in the past, an employee falling prey to the attackers’ lure was the initial point of failure here. In sensitive networks, companies should insist that employees not pursue their personal agendas, like job hunting, on devices belonging to their company’s infrastructure.
Threat Labs summary
Securonix Threat Labs has continued to monitor the Lazarus group activity and their attack methods since its discovery and recommend the following
- Leverage our findings to inform the deployment of protective measures against Lazarus techniques.
- Implement network segmentation and maintain offline backups of data to ensure limited interruption to your organization.
- Audit user accounts with administrative privileges and configure access controls according to the principle of least privilege.
- 25 IOCs are available on our Threat Labs home page and have been swept against Securonix Autonomous Threat Sweeper customers.
TTPs related to the Lazarus Group Leveraging DLL Side-Loading Technique include but are not limited to the following:
- Monitor execution of scskapplink.dll and inisafecrosswebexsvc.exe which leads to malicious files creation on execution
Tags: Threat group: Lazarus| Target: Windows kernel mechanisms and all security solutions
Vulnerabilities exploited in October
(Originally published on October 2022)
The FortiOS, FortiProxy, and FortiSwitchManager appliances from Fortinet are susceptible to an authentication bypass vulnerability that may allow unauthorized users to access the administrative interface through specially crafted HTTP and HTTPS requests. As a result, Fortinet’s customers who leverage vulnerable product instances are at risk from the security flaw tracked as CVE-2022-40684.
The ProxyNotShell zero-day vulnerability, also known as CVE-2022-41040, has been discovered on Microsoft Exchange servers on premises. It is a server-side request forgery (SSRF) that enables privilege escalation and combines with CVE-2022-41082 to execute remote code on Exchange servers deployed on premises. In the exploit chain, newly uncovered bugs in MS Exchange Server paired together to spread Chinese Chopper web shells. According to Microsoft, a correction was made to the string in the URL rewrite rule mitigation option.
In recent days, researchers have detected attempts to exploit the newly disclosed Apache Commons Text vulnerability. It is tracked as CVE-2022-42889 aka Text4Shell and affects versions 1.5 through 1.9 of the library. In order to execute arbitrary code remotely, the attacker can use ‘script,’ ‘dns,’ and ‘url’ lookups. By exploiting the flaw successfully, a threat actor can establish a reverse shell connection with the vulnerable application, effectively opening the door to follow-on attacks.
Threat Labs summary
- Securonix Threat Labs has continued to actively monitor vulnerabilities and exploits while identifying notable vulnerabilities that could have a tremendous impact if not addressed.
- Securonix Threat Labs recommends updating vulnerable applications to the latest version immediately and following the mitigation guidelines.
- 93 IOCs are available on our Threat Labs home page repository and have been swept against Securonix Autonomous Threat Sweeper customers.
TTPs related to the zero day vulnerabilities in Microsoft Exchange Server include but are not limited to the following:
- Monitor for rare PowerShell commands execution with unusual urls which are used to download and execute the payload to exploit this vulnerability.
Tags: Vulnerability: Microsoft Exchange Server, Apache Commons Text library, FortiOS, FortiProxy, FortiSwitchManager | Exploitation: Unauthorized Access, Remote Code Execution, Privilege Escalation
LockBit continues its rise returning as Lockbit 3.0
LockBit 3.0 Ransomware spread again this month and was discovered by Rewterz researchers and other researchers. LockBit ransomware takes minutes to run the encryption routine on target systems once it gets on the victim network. LockBit attacks leave almost no evidence for forensics as the malware loads into the system memory, with logs and supporting files removed upon execution. Researchers observed that LockBit 3.0 ransomware is being delivered in Word document format while masquerading as job application emails in NSIS format. The particular distribution method has not yet been discovered, but given that the file names include people’s names, such as ‘Lim Gyu Min.docx’ or ‘Jeon Chae Rin.docx,’ it is possible that they were spread disguised as job applications, as in previous occurrences.
The recurrence of Lockbit was spotted by VMware researchers as well who noted that LockBit is at the top of the ransomware ecosystem and the leading ransomware strain currently. The researchers shared that the ransomware development was leaked by @ali_qushji and available for download from GitHub. This leaked source allows for complete and unhindered analysis, but also means that many new groups are emerging and using the same or modified versions of LockBit 3.0 originating from this builder development.
Threat Labs summary
Threat Labs continues to monitor Lockbit ransomware activities and recommends customers follow the steps below to avoid ransomware attacks:
- Leverage our findings to inform the deployment of protective measures against the threat group.
- Implement network segmentation and maintain offline backups of data to ensure limited interruption to your organization.
- Audit user accounts with administrative privileges and configure access controls according to the principle of least privilege.
- Disable unused ports and enable multi-factor authentication (2FA).
- 25 IOCs are available on our Threat Labs home page repository and automatically swept against for Autonomous Threat Sweeper customers.
TTPs related to the LockBit 3.0 Ransomware include but are not limited to the following:
- Monitor Suspicious MS Office Child Process (T1566.001 – Phishing: Spearphishing Attachment)
- Monitor Suspicious Rundll32 CommandLine (T1218.011 – System Binary Proxy Execution: Rundll32)
TTPs related to the “LockBit 3.0 is in the spotlight again” include but are not limited to the following:
- Monitor the execution of the following that generates public and private encryption keys that allow the creation of malicious files
DECRYPTION_ID.txt, LB3.exe, LB3Decryptor.exe ,LB3_pass.exe, LB3_RelectiveDLL_DLLMain.dll, LB3_Rundll32.dll, LB3_Rundll32_pass.dll, Password_dll.txt, Password_exe.tx
Tags: Ransomware: LockBit, LockBit 3.0 | RaaS, VBA Macro, Word Document, PowerShell, Ransomware
Prominent ransomware attacks
(Originally published on October 2022)
Ransomware attacks this month are continuing to be active and remain persistent. They continue to affect various industries and categories.
|
Ransomware campaigns in October 2022 |
|
| Campaign | Description |
| Linux ransomware Cheerscrypt | The Sygnia Threat Research team recently noticed and investigated the Cheerscrypt ransomware attack which utilized Night Sky ransomware TTPs and found Linux ransomware Cheerscrypt linked to the China-based cyber espionage group Bronze Starlight (aka DEV-0401, APT10) or ‘Emperor Dragonfly’. Although most researchers consider Cheerscrypt as a Linux-based ransomware family that targets ESXi servers, in this case Sygnia discovered that both Windows and ESXi machines were encrypted. |
| BlackByte ransomware | The BlackByte ransomware strikes back with a new variant and uncovers a new tactic for bypassing security products by abusing a known driver vulnerability as reported by Sophos. This known driver vulnerability is CVE-2019-16098. The new version of Blackbyte lets invaders read and overwrite critical drivers that EDR products rely on to provide protection, Picus Security said. The evasion technique supports disabling a whopping list of over 1,000 drivers on which security products rely to provide protection. |
| The new Royal ransomware | FortiGuard Labs shared data on a new variant that is gaining interest in the OSINT community. Royal is a reasonably new operation, having been around since at least the start of 2022. The target of this malware is Microsoft Windows platforms and Windows users and is categorized as high level severity. The aim is to gain access to a victim’s environment, encrypt their data, and extort a ransom to return access to any files encrypted. |
Threat Labs summary
Securonix Threat Labs has observed that the threat actor maintained access, minimized forensic artifacts, and increased access to systems after obtaining initial access. Threat Labs continues to monitor ransomware activities and recommends customers follow the steps below to avoid ransomware attacks:
- Leverage our findings to inform the deployment of protective measures against the threat group.
- Implement network segmentation and maintain offline backups of data to ensure limited interruption to your organization.
- Audit user accounts with administrative privileges and configure access controls according to the principle of least privilege.
- Disable unused ports and enable multi-factor authentication (2FA).
- 47 IOCs are available on our Threat Labs home page repository and automatically swept against for Autonomous Threat Sweeper customers.
TTPs specifically related to the Linux ransomware Cheerscrypt include but are not limited to the following:
- Monitor Log4Shell vulnerability (CVE-2021-4428)
- Monitor binaries, scripts, and executions from suspicious folders.
- Monitor execution of Impacket’s Python module SMBExec.py executions
- Search for evidence of WMIExec executions.
Increased malware campaigns in October
(Originally published on October 2022)
Maggie is a malware that targets Microsoft SQL servers and has already infected hundreds of machines worldwide. Using SQL queries, Maggie runs commands and interacts with files. It can brute-force administrator logins to other Microsoft SQL servers and act as a gateway into the server’s network environment. A majority of cases have occured in South Korea, India, Vietnam, China, Russia, Thailand, Germany, and the United States. Maggie supports a variety of commands, including querying for system information, running programs, interacting with files and folders, setting up a SOCKS5 proxy, and enabling remote desktop services (TermService).
Earth Aughisky (also called Taidoor) is an advanced persistent threat (APT) group that has become increasingly sophisticated with its malware toolset. There has been a continuous adjustment in the tools and malware deployed on specific targets located in Taiwan, and more recently, Japan. Its primary goal is to exploit legitimate accounts, software, applications, and other weaknesses in networks and infrastructure for its own ends as part of this cyber espionage group. Among the most commonly targeted industries are government, telecom, manufacturing, industrial technology, transportation, and healthcare. Earth Aughisky has used backdoors such as SiyBot, TWTRAT, and DropNetClient (aka Buxzop) over the years.
In attacks targeting Windows, Linux, and MacOS systems, researchers discovered an attack framework called ‘Alchimist,’ which appears to be used actively. This framework, along with all its files, is written in GoLang 64-bit executables. Using Alchimist, operators can generate and configure payloads that are placed on infected devices to take screenshots, run arbitrary commands, and execute shellcode remotely. Hackers can generate PowerShell code snippets for the deployment of the ‘Insekt’ remote access trojan (RAT) from the framework in order to build custom infection mechanisms.
Threat Labs summary
Securonix Threat Labs constantly keeps an eye on all malware campaigns that persist in their malicious activities and wide area of impact, as the threat actors are often changing their TTPs while sharing attack infrastructure among themselves to target vulnerable users.
Threat Labs proactively monitors and secures identified systems and devices for any suspicious/malicious activities and recommends the following.
- Regularly checking and applying the latest patch of software, especially to public-facing applications.
- Enforcing multifactor authentication for users to ensure only those authorized are accessing your network.
- 1205 IOCs are available on our Threat Labs home page and have been swept against Securonix Autonomous Threat Sweeper customers.
TTPs related to the Maggie malware include but are not limited to the following:
- Monitor execution of “”””ExtendedProcedure.DLL”””” and “”””sqlmaggieAntiVirus_64.dll”””” which leads to malicious files creation on execution
- Monitor for the execution of backdoor via SQL queries
- $ exec maggie ‘Exec whoami’”
TTPs related to the Alchimist and Insekt Malware include but are not limited to the following:
- Monitor for the combination of new accounts created, addition of these accounts to the local Administrators group and later removal of the previously created local administrator account
- ${add_user}
- ${add_admin}
- ${domain_ls}
- ${domain_show}
- ${dc}
- ${2003_rdp_reg}
- ${close_firewall}
- ${in-port-allow-tcp}
Tags: Target: Windows, Linux, MacOS, Microsoft SQL servers | Malware: Maggie, Insekt | Target Geo-Location: South Korea, India, Vietnam, China, Russia, Thailand, Germany, United States | Adversary: Earth Aughisky
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Github page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected]
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Sina Chehreghani, Dhanaraj K R, Saujas Jadhav, Rouzbeh Radparvar


