- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Oleg Kolesnikov, Securonix Threat Research Team
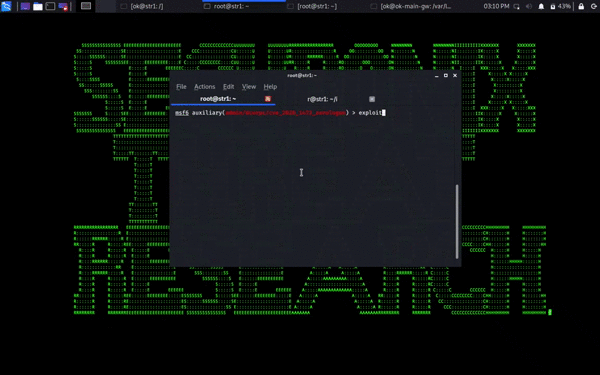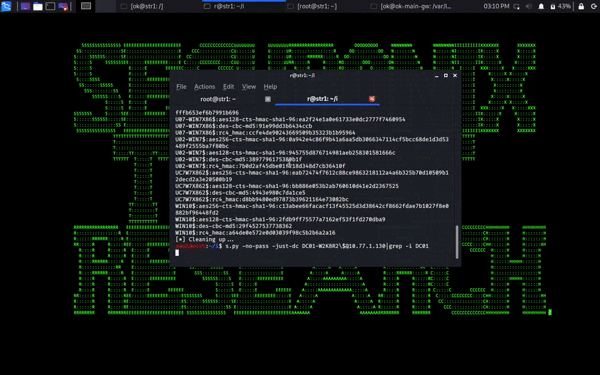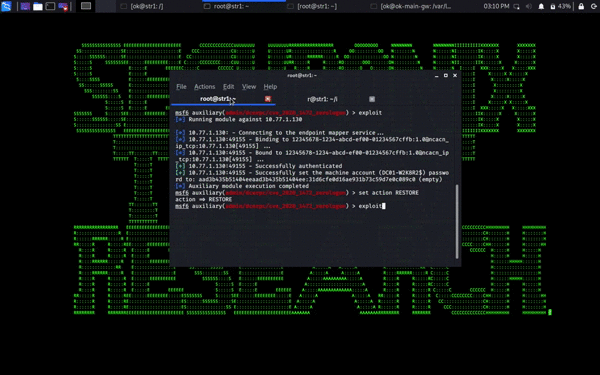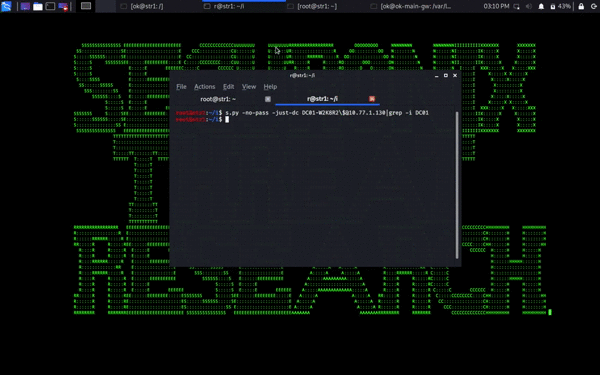
Some security experts are calling the new CVSS 10/10 Windows Zerologon EP (ZEP) Vulnerability (CVE-2020-1472) the GenZ/Alpha variant of the good ol’ GenX/Y MS08-067 (see attack screen cap above for what an actual ZEP attack might look like in action.)
As you probably know, there are *multiple* vectors to exploit ZEP, not only via the naive direct DC password reset, but also, e.g., via DRSUAPI relay *w/o the need to reset DC m/a password* (see https://dirkjanm.io/a-different-way-of-abusing-zerologon/, for instance).
I’ve distilled some of the latest technical insights from real-world exploitation of ZEP from red team/opsec and blue team/detection standpoint below.
Impact:
- Allows you to EP from *no domain access* to DC *machine* account compromise in <1 minute. Multiple ready-to-use publicly available exploits. Affects DC running on, e.g. Windows Server 2008*, 2012*, 2016*, 2019* (see Secura blog for more details—https://www.secura.com/blog/zero-logon).
Some common attack vector examples:
- No domain account available to attacker – Auth bypass for netlogon protocol, can be used to e.g. reset your DC *machine* account password; In the basic attack variant (DC pwd reset), your DC machine attempts to connect to *itself* multiple times w/ClientChallenge IV set to 8 zeros, using a timestamp of 0 (1970-01-01*), takes on the order of 256 requests to succeed;
- Domain account (unelevated) available to attacker – Auth bypass for netlogon *without resetting your DC machine password*, trigger the Print Spooler vulnerability/DRSUAPI followed by ntlmrelayx in DCSYNC relay mode; Requires at least 2 DCs/domain, and a print spooler running on the target DC (see https://dirkjanm.io/a-different-way-of-abusing-zerologon/);
Red team/real-world attack exploitation insights:
- Important: DC *machine* account != Domain admin account. ZEP allows an attacker to authenticate as DC to same DC or another DC, which is a high-privilege activity particularly because DC can leverage DRSUAPI to synchronize AD data (DCsync etc) which can expose kerberos and NT hash data. This can then be used for pth/dcsync/compromising domain users, generating fake tickets, etc.
- The direct DC machine account password reset usually breaks your config/leaves your DC in an unpredictable state => typically need to *restore* your DC password *after* resetting and dumping the hashes etc. – Just dump DC machine hash and restore after dumping hashes (see attack screen cap above for how the restore after the reset works);
Blue team/attack detection highlights:
- Here is what attempts to exploit ZEP might look like in your Windows Event Logs:
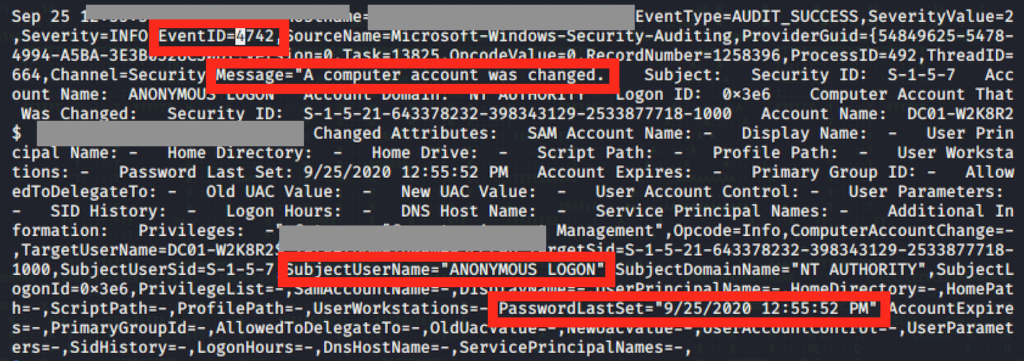
- Microsoft added five new event IDs to help detect vulnerable Netlogon connections (5827, 5828, 5829, 5830, 5831).
- Important to factor in the Microsoft Netlogon vulnerability patch *initial deployment phase* (pre-Feb 9, 2020) and *enforcement phase* (post-Feb 9, 2020) in your detections as the detection strategy may be different (see https://support.microsoft.com/en-us/help/4557222/how-to-manage-the-changes-in-netlogon-secure-channel-connections-assoc);
- To illustrate, you can see the event ID 5829 when a vulnerable Netlogon secure channel connection is *allowed* during the *initial deployment phase* (before the Feb 2021 registry change from Microsoft).n;
- Monitor event IDs 5827 and 5828 that triggered when vulnerable Netlogon connections are denied, and event IDs 5830 and 5831, triggered when vulnerable Netlogon connections are allowed by the patched domain controllers;
- Due to the nature of the patch, expect to have a some legacy systems using insecure Netlogon that the ZEP patch can potentially break, which needs to be factored in as part of your detection;
- The trivial “DCSync from non-DC IP” detection use case can also help detect some parts of the attack progression;
Your Linux machines running Samba AD can also be exploited – might be worth considering monitoring your Samba logs (/var/log/samba/smb.log and others).
- Here is what attempts to exploit ZEP against your Samba servers might look like in your Samba logs:
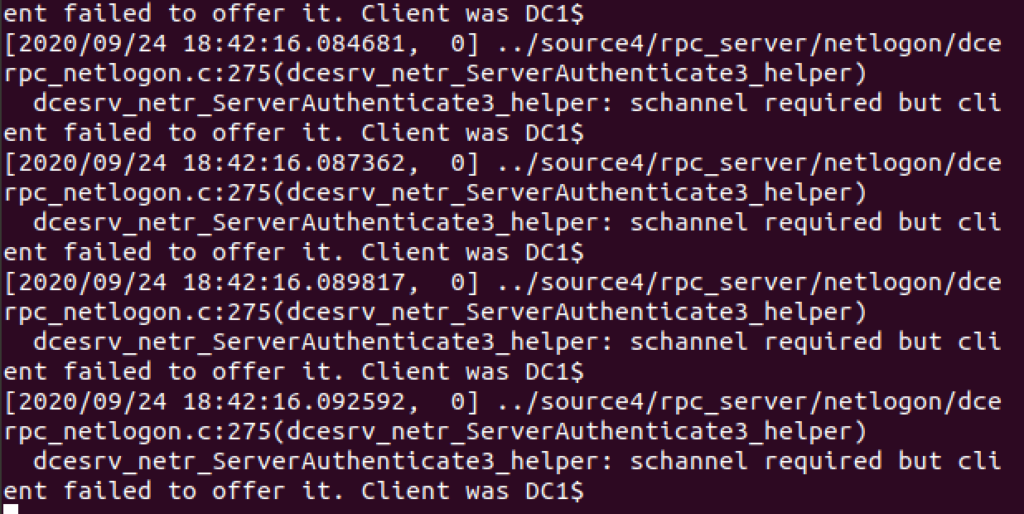
- Note DC1 is attempting to connect to itself and failing to offer an schannel, which can be used to detect attempts to exploit this vulnerability.
Additionally, for attacks targeting Linux Samba AD, if you look at the patch for Netlogon, the patch introduces some targeted checks that can further help identify attempts to exploit ZEP in your logs (DBG_WARNING below):
To summarize:
- ZEP might have a broader attack surface than expected–DC machine password reset is not the only vector, which can be important to consider from a detection viewpoint;
- Whether ZEP is the new MS08-067 still remains an open question, but it is clear the impact of this CVSS10/10 can be relatively high as yet another payload for attackers;
- Blue team has a number of options when it comes to detecting malicious activity associated with ZEP, ranging from checks related to DC machine account changes (4742), to loopback logon attempts (DC-DC 4624/4672), to ETW/SMB-RPC monitoring (NetrServerReqChallenge and NetrServerAuthenticate3, NetrServerPasswordSet2), to attack tool capability-specific detection (mimikatz/lsass dumping, for instance, since mimikatz now has a module to exploit ZEP as well);
- Focusing on the fundamental detection use cases stemming from DCsync-based credential compromises can potentially help detect some of the post-exploitation activity of ZEP;
- Consider leveraging the five newer events added for netlogon monitoring as part of your detection strategy – 5827-5831.
- In addition to Windows AD, blue teams might also need to factor in some of the other possible attack targets, including Samba AD, e.g. /var/log/samba/smb.log), if applicable to your environment.