- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Rajesh Lohani, Tim Johny
The Monthly Intelligence Insights published by Securonix Threat Labs provides a summary of the total number of threats tracked and highlights the top threats during the month. It also provides a synopsis of the threats, indicators of compromise (IOC), tactics, techniques and procedures (TTP), and related tags. This may be followed by a comprehensive threat summary from Threat Labs and search queries from the Threat Research team. For a full list of the search queries used on Autonomous Threat Sweeper to detect the below mentioned threats, refer to our Github page.
During the month, Threat Labs analyzed and monitored cyber activities in the Middle East, activities of Emotet, REvil Ransomware Group, and Linux-based backdoor BPFDoor, additionally tracking numerous threat campaigns like — a new phishing-as-a-service called “Frappo” that lets threat actors host and generate high-quality phishing pages which impersonate online-banking, e-commerce, popular retailers, and online-services to steal sensitive customer information. In another campaign, there were five 0-day vulnerabilities targeting Android users. The campaign delivers one-time links mimicking URL shortener services to the targeted users via Email. Once clicked on the links, it will redirect users to an attacker-owned domain that delivered the exploits before redirecting to a legitimate website.
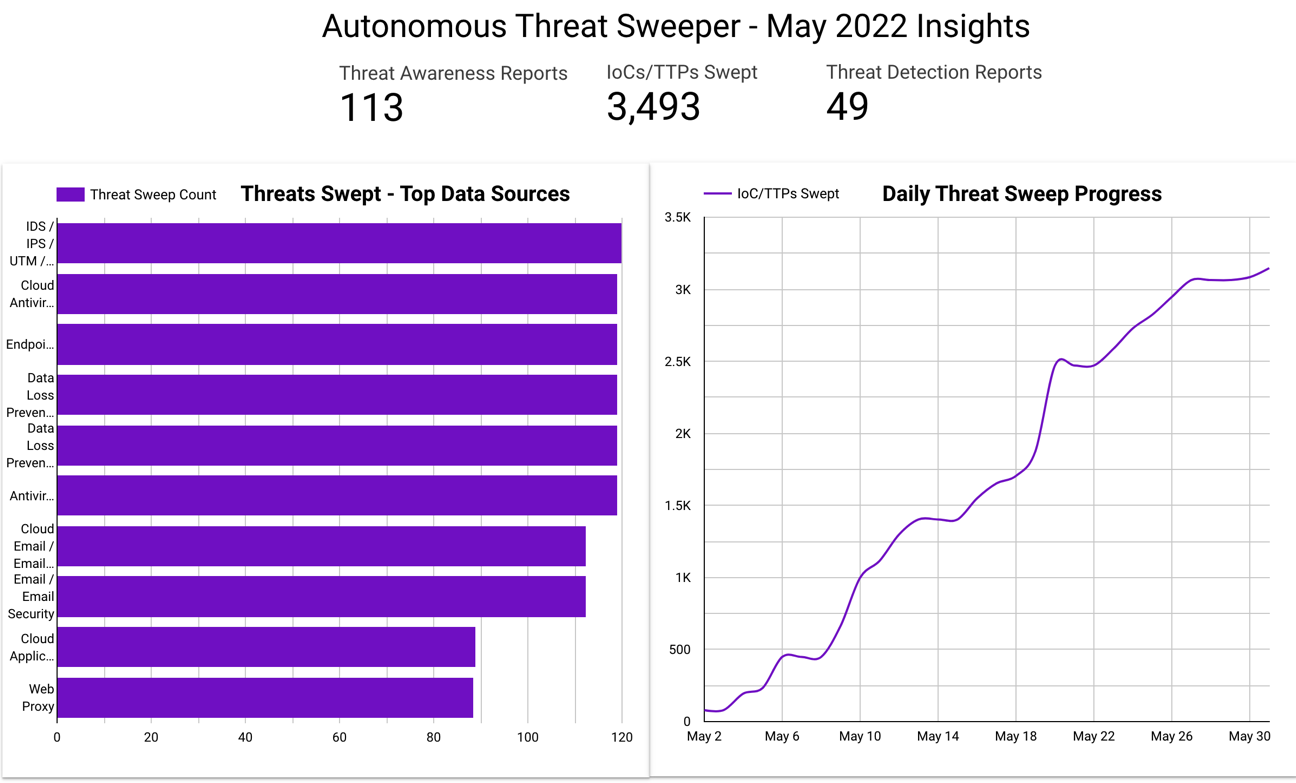
In May, Securonix Autonomous Threat Sweeper identified 3,493 IOCs, 113 distinct threats, and reported 49 threat detections. The top data sources swept against include email / email security, cloud application security broker, authentication / single sign-on, and web application firewall.
Activities in the Arabian Peninsula
(Originally Published On May 2022)
In the past attacks the main motive of the Iran-based threat actors have been espionage but this time they are leaning toward financial gain and have been trying to extract money from U.S-based firms through their ransomware operations. Multiple state-sponsored threat actors from Iran have been quite active this month and have continued their operations.
Iranian threat actor activities in May 2022 |
|
| Cobalt Mirage targets US firms with ransomware operations | The threat actor targeted U.S-based firms in two clusters which involved leveraging BitLocker and DiskCryptor for ransomware campaigns aimed at financial gain while also focusing on attacks to gain initial access for collecting intelligence. Cobalt Mirage activity was also linked with another Iranian threat actor COBALT ILLUSION. |
| APT34 uses Saitama backdoor to target Jordan government | A spear phishing email campaign targeting Jordan government officials was launched to deliver Saitama backdoor through an Excel file. The threat actors used Saitama as it is stealthier than other backdoors because it uses DNS protocol for C&C communications. |
Threat Labs Summary:
- Threat Labs has continued to monitor campaigns originating from Iran-sponsored threat actors holding that these malicious activities will persist throughout the year, as the threat actors are simultaneously enhancing their TTPs while sharing attack infrastructure among themselves to target vulnerable users.
- 44 IOCs are available on our Github repository and have been swept against Securonix Autonomous Threat Sweeper customers.
TTPs related to APT34 and COBALT MIRAGE that can be detected include but are not limited to the following:
- Monitor for the abnormal spike in the exploits for Microsoft Exchange ProxyShell vulnerabilities; an exploit chain of three different CVEs:
- CVE-2021-34473
- CVE-2021-34523
- CVE-2021-31207
- Monitor for suspicious scheduled task creation that contains rare xml files and that runs with UserID S-1-5-18 (System or LocalSystem).
- Example: schtasks.exe /Create /F /XML C:\windows\temp\Wininet.xml /tn ‘\Microsoft\Windows\Maintenance\Wininet’
- Monitor for the execution of rare vbs files from schtasks, that spawns unusual or rare executables.
- Example: wininet.bat > dllhost.exe (Masquerading as the original windows binary)
- Monitor for the combination of events where a new account created is added to Administrators and Remote Desktop Users groups in a short period of time.
- Example: powershell.exe /c net user /add DefaultAccount P@ssw0rd123412; net localgroup Administrators /add DefaultAccount; net localgroup ‘Remote Desktop Users’ /add DefaultAccount
- Monitor for rare batch file execution using WshShell.Run, that spawns unusual or rare executables.
- Example: nvContainerRecovery.bat runs audio.exe
- Monitor for scanner tools in the environment that can enumerate the environment.
- Example: SoftPerfect Network Scanner tool
- Monitor FireWall rule and registry modifications that enable RDP access as they move laterally using RDP.
- Example: netsh advfirewall firewall add rule name = “Terminal Server” dir=in action=allow protocol=TCP localport=3389
- Monitor for the regmods that enable WDigest authentication and disable LSA protection.
- Example: “reg” add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1 /f
- “reg” add HKLM\SYSTEM\CurrentControlSet\Control\LSA /v RunAsPPL /t REG_DWORD /d 0 /f
- Monitor for rare and suspicious PowerShell commands to encrypt using BitLocker.
- Example: powershell -c “Install-WindowsFeature BitLocker -IncludeAllSubFeature -IncludeManagementTools -Restart”
- Look for rare and suspicious processes directing network traffic toward ngrok domains.
Tags: Malware: Saitama | Adversary: APT34, COBALT MIRAGE | Target Country: U.S, Jordan | Target Sectors: Government
Surge in Emotet activity
(Originally Published On May 2022)
Emotet is considered the world’s largest malware botnet, with a collection of hundreds of C2 servers and almost two million victims till law enforcement agencies shut down its operations in January 2021. Later, In November 2021, Emotet’s new version returned with Trickbot. Since then Emotet has returned to its status as a prominent threat. The tactics and techniques have been mostly the same throughout the campaign in which they lure victims through spear phishing emails containing malicious attachments. Securonix Threat Labs has also been tracking the activities of Emotet, and this month the malware has made a lot of progress.
EMOTET ACTIVITIES IN MAY 2022 |
|
| New obfuscation technique | A new obfuscation technique used by Emotet developers makes detection and reverse engineering of the malware’s payload more difficult. This technique is known as Control Flow Flattening (CFF). CFF is an obfuscation technique that hides program flow by putting all function blocks next to each other. |
| New delivery mechanism to bypass VBA protection | After announcing the blocking of VBA macros by Microsoft, attackers have also identified a new way of delivering the payloads. Similarly, Emotet developers, where they replaced the usual office delivery system with LNK files were spotted. In this new delivery system, Emotet abuses the LNK file format (a.k.a. MS-SHLLINK and Shortcut) to execute a PowerShell script. |
| A journey from Nov 2021 to Jan 2022 | From mid-November 2021 to January 2022, Emotet was actively spammed through hundreds of thousands emails each day. The timeline of Emotet operations covers Trickbot infection, batch files noted during infection, abusing Microsoft App Installer protocol, Cobalt Strike from Emotet infections, new infection method with .hta files and PowerShell script and emails using attachments instead of links. |
| Distributed through link files (.lnk) | Emotet has been steadily distributed using Excel files, but researchers identified a new tactic where Emotet downloaders used link files (.lnk). |
Threat Labs Summary:
- Threat Labs has continued to monitor the Emotet campaign as it began spreading rapidly once again.
- Threat Labs recommends that customers treat Emotet as a significant adversary to their infrastructure since it can cause damage and enable access to other criminals, such as ransomware operators.
- 316 IOCs are available on our Github repository and have been swept against Securonix Autonomous Threat Sweeper customers.
TTPs related to the Emotet that can be detected include but are not limited to the following:
- Monitor for rare instances where an LNK file spawns PowerShell, as the latest version of Emotet abuses the LNK file format (a.k.a. MS-SHLLINK and Shortcut) to execute a PowerShell script in this new delivery system.
- Monitor for suspicious and rare usage of PowerShell Invoke-WebRequest function as the payload/binary is always a stage-2 download and the URL will be decoded only after the encoded PowerShell gets executed.
- Monitor the creation of rare or suspicious Windows processes that later executes itself via regsvr32.exe
- Example: C:\Windows\system32\regsvr32.exe “C:\Windows\system32\Llywnufkdeycn\cgyvhen.vwb”
Tags: Malware: Emotet, Trickbot | Target Operating System: Windows | Target Countries: South Korea, Italy, Germany, United States
BPFDoor — An active Chinese global surveillance tool
(Originally Published On May 7, 2022)
The PWC Threat Intelligence team documented the presence of BPFDoor, a passive network implant for Linux which has been used by Threat actor Red Menshen to target Telecommunications providers across the Middle East and Asia and also the government and logistics sector. The threat actors have been geolocated to China. BPFDoor has been severe as it allows the threat actor to backdoor a system for remote code execution, without opening any new network ports or firewall rules. This backdoor has been found in multiple versions of Linux appliances and Solaris SPARC boxes. CrowdStrike has named the same threat “Just For Fun” and has attributed it to DecisiveArchitect.
Threat Labs Summary:
- BPFDoor supports multiple protocols including TCP, UDP and ICMP which enables threat actors with lots of ways to interact with the backdoor.
- Threat Actors target Solaris using exploit for CVE-2019-3010 a vulnerability in xscreensaver.
- For persistence Red Menshen uses SysVinit scripts.
- Detects BPFDoor activity with EDR technology across supported Linux systems.
TTPs related to the BPFDoor that can be detected include but are not limited to the following:
- Monitor for a spike in the targeted scans/exploits for Solaris privilege escalation vulnerability as BPFDoor leverages this vulnerability as the initial attack vector.
- Example: /tmp/getuid.so, /usr/lib/secure/getuid.so
- Monitor for the rare scenario, where a binary runs and makes network connections from the shared memory location /dev/shm.
- Example: /dev/shm/kdmtmpflush
- Monitor for the rare behavior, where an empty PID file is dropped in the /var/run directory.
- Example: /var/run/haldrund.pid
- Detect processes deleted from the disk after execution but is resident in memory (after process forking) as this is the tactic seen in all cases to evade detection.
- Monitor for rare traffic redirect commands toward ports ranging from 42391-43391 and TCP protocol.
- Example: /sbin/iptables -t nat -D PREROUTING -p tcp -s %s –dport %d -j REDIRECT –to-ports 42391″
- 52 IOCs are available on our Github repository and automatically swept against for Securonix Autonomous Threat Sweeper customers.
Tags: Malware: BPFDoor/Just For Fun | Adversary: Red Menshen | Target Countries: US, South Korea, Hong Kong, Turkey, India, Vietnam and Myanmar | Target Sectors: Government, Postal and Logistic Systems, Education Systems, Telecommunications
Return of REvil as Sodinokibi
(Originally Published On May 2022)
REvil Ransomware group had been shut down in October 2021, followed by a seizure and arrest of 14 members of the group by the Russia FSB in January 2022. The REvil Ransomware group appears to be back, when its old TOR site came back to life in April 2022. However the site has been modified to redirect the visitors to a new URL prepopulated with new and old ransomware victims. On 30 April, 2022, Security Researcher Jakub Kroustek discovered a sample that looks like a new REvil variant. Later, multiple researchers noticed changes to the code based on old REvil ransomware code. Moreover researchers suspect REvil’s core developer might have relaunched the ransomware operation. Some researchers analyzed the REvil ransomware code and suspects that the threat actor GOLD SOUTHFIELD has resumed its operations.
Threat Labs Summary:
- Securonix Threat Labs has been monitoring since the start of the wave of REvil activity and analyzed several sources discussing REvil’s return. The new REvil code includes a new configuration field ‘accs’ which contains credentials for the specific victim that the attack is targeting.
- The new code has the following modifications as compare to old code:
- Updates string decryption logic to rely on new command-line argument
- Updates hard-coded public keys
- Changes the configuration storage location
- Changes affiliate tracking data format
- Removes prohibited region check
- Includes new Tor domains in ransom note
- Changes safe-mode option values
- Updates registry key and values
- 14 IOCs are available on our Github repository and automatically swept against for Securonix Autonomous Threat Sweeper customers.
Tags: Ransomware: REvil, Sodinokibi | Adversary: GOLD SOUTHFIELD
F5 BIG-IP unauthenticated RCE vulnerability (CVE-2022-1388)
(Originally Published On May 4, 2022)
Securonix Threat Labs identified a critical vulnerability in iControl REST functionality in F5 systems. The critical CVE (CVE-2022-1388) which is classified as an authentication bypass vulnerability carries a 9.8/10 severity rating. The overall impact is significant as it affects the current line of network appliances such as the F5 BIG-IP systems. These include modern firewalls and network monitoring and performance hardware. An attacker has the ability to execute UNIX-based commands remotely which could give them full control over the appliance.
Threat Labs Summary:
- Multiple vulnerability scanning and active exploitation attempts were noted after the POC was in the wild.
- Though the exploit was not targeted at the education sector, it was the most scanned one.
- CVE-2022-1388 can be leveraged to drop web shells for prolonged backdoor access.
- Securonix Threat Labs additionally recommends blocking iControl REST access through local IP address ranges (ie: 127.0.0.1)
- Perform forensic analysis to ensure no past compromise has occurred
- /var/log/audit
- /var/log/restjavad-audit.0.log
- 184 IOCs are available on our Github repository and automatically swept against for Securonix Autonomous Threat Sweeper customers.
Tags: Vulnerability: F5 BIG-IP
For a full list of the search queries used on Autonomous Threat Sweeper to sweep for these threats detailed above, refer to our Github page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected]
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Amit Roshan, Sina Chehreghani


