- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Company Insights
Have you noticed an uptick in ransomware recently? Ransomware is commonly delivered by an email that tricks users into trusting a malicious file. Many of the most recent data breaches were initiated because a user fell victim to ransomware. Threats like ransomware, which focuses on compromising the user, have more and more companies adopting user and entity behavioral analytics (UEBA) into their security operations center (SOC).
Securonix has taken note of this trend and continues to innovate our cloud SIEM platform and UEBA capabilities to better arm your SOC to combat ransomware and other threats. In our recent release, 6.3.1, we’ve added even more machine learning based detection and context-aware capabilities that empower security analysts to take on sophisticated attackers. Additionally, this release brings increasing ease of use for security architects and our growing service provider partner organization.
For the Security Analyst and Threat Hunter
Securonix introduces a number of innovations to drive down detection and response times for security analysts and threat hunters.
Improved Detection of Sophisticated Threats
- Long-Term Search helps analysts discover hidden threats by providing a capability to search on archived data that is highly scalable and doesn’t affect the performance of your SIEM.
- Analytics Sandbox helps drive down false positives by providing an inline QA environment to test and validate use cases before pushing them to production. For more information on this powerful feature, check out our blog post here.
- Persona-Based Threat Chains detect advanced threats more accurately by understanding the dynamic relationship between users, hosts, IP addresses, and email addresses. Analysts benefit from having broader visibility into the progression of an attack. This feature combines suspicious activity together from a single user together into one, prioritized alert, instead of separate, unrelated alerts.
- Relative Rarity gives analysts increased context on how rare an event is compared with all other events in their environment.
- Visualizing Security Alerts Using the MITRE ATT&CK Threat Framework helps analysts prioritize risk and decrease response times.
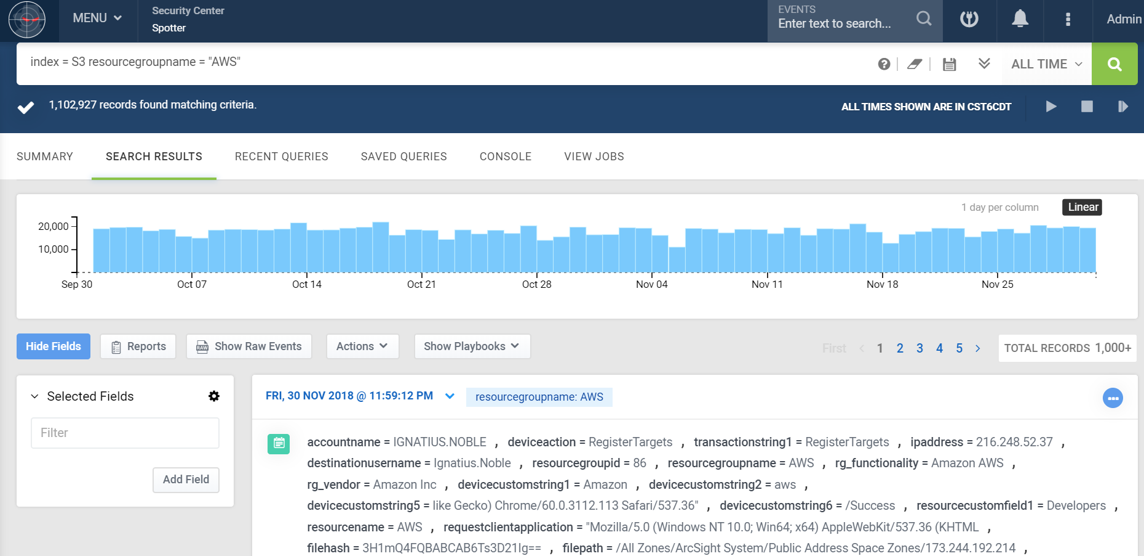
Screenshot Highlighting Long-Term Search
Decrease Incident Response Times
- Improved Case Management enables better management, sharing, and investigation of alerts, allowing them to respond quicker.
- New EDR Integrations improve incident response by bringing in more endpoint data from CarbonBlack Defense, Tanium, Symantec DLP, and others.
- Better Search Visualizations improve the analyst experience by decreasing detection and response times. They help analysts easily identify compromised accounts, data exfiltration, and associated hotspots.
For Security Architects and Service Providers
Security architects and partners will benefit from the simpler deployment and easier usability of the Securonix Next-Gen SIEM platform with improvements including:
- Easier Management of Multi-Tenant Deployments allows for more control at scale and the ability to segment customers.
- Installation Automation for Remote Ingester Nodes improves time to value.
- SAML Authorization enables easier setup and maintenance of authorization of roles and credentials.
Want more information? Reach out to your Customer Success representative at Securonix.








