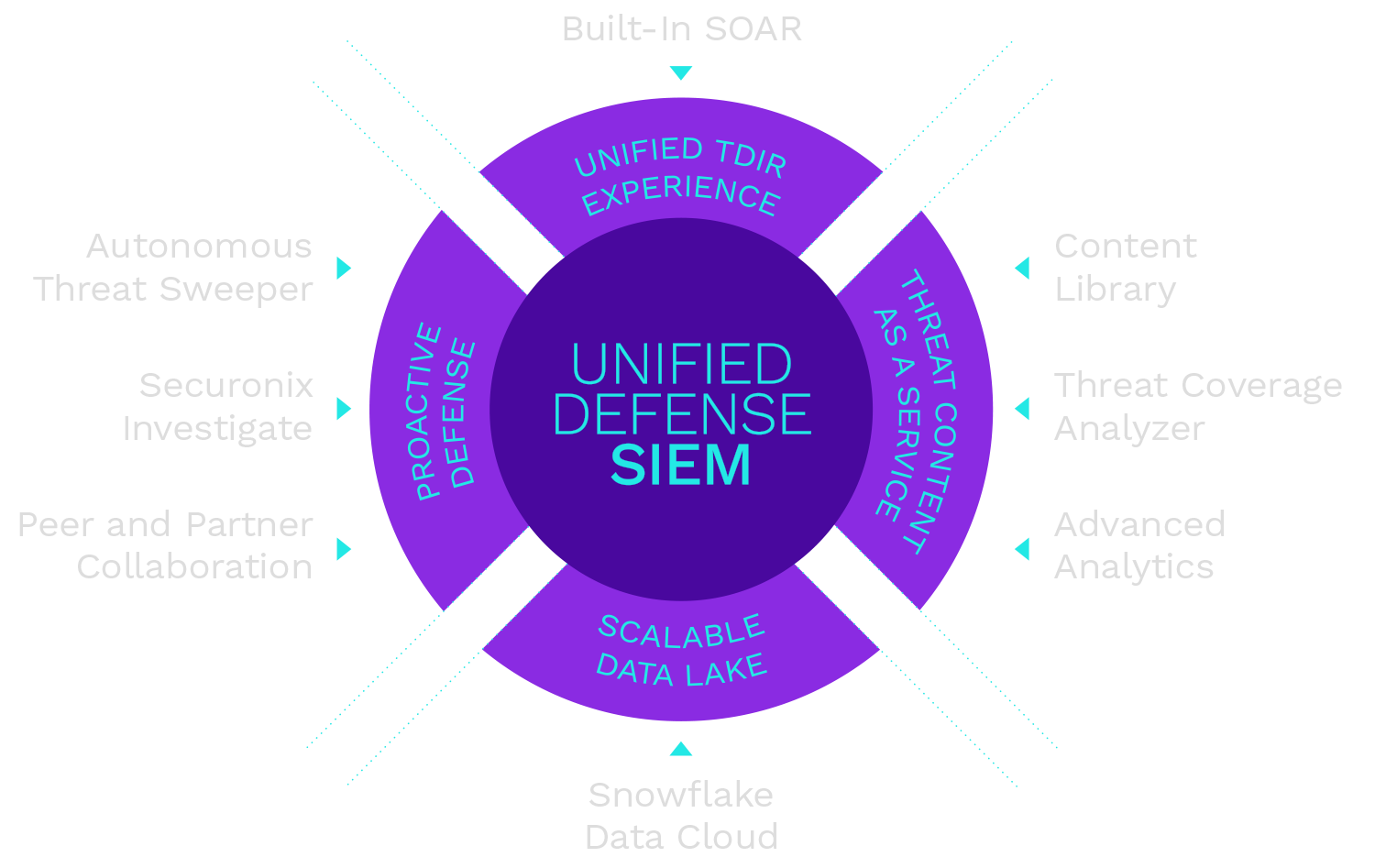
Introducing Unified Defense SIEM
Scale up your threat defense with a SIEM that unifies threat detection, investigation, and response (TDIR) on the Data Cloud.
Scale up your threat defense with a SIEM that unifies threat detection, investigation, and response (TDIR) on the Data Cloud.
Our most comprehensive TDIR solution is built on Snowflake’s highly scalable Data Cloud and offers a seamless end-to-end experience from the analyst to the CISO.

Leveraging the Snowflake Data Cloud, Securonix lets you easily handle large data requirements with a scalable data storage solution that provides access to 365 days of ‘Hot’ searchable data.

Get comprehensive threat coverage with continuously updated threat content-as-a-service, tapping into the expertise of our industry-leading Threat Labs team as an extension of your own team.

Take a more collaborative approach to defense with tools that let you share intelligence with your peers and partners, and easily investigate threats with autonomous threat sweeps and automated response.
Eliminate context-switching and elevate your analyst experience. Leveraging a single interface and built-in SOAR capabilities, you can now detect, investigate, and respond in a single workflow.



Many SIEMs cannot scale to handle the volume of data generated by modern enterprises. Securonix offers a robust and cost-effective architecture built on Snowflake’s Data Cloud that reduces complexity and enables powerful, on-demand search.
The security landscape is constantly evolving, with new threats appearing daily. By staying current with the latest detection content, you can stay one step ahead of potential attacks and protect your environment and data from harm.
Securonix empowers community collaboration and knowledge sharing to combat threat actors with essential tools for collaborating with your peers and partners.
Security teams using poorly integrated security solutions can delay threat detection and response. That’s why we are streamlining the user experience to deliver detection, investigation, and response in a single interface.
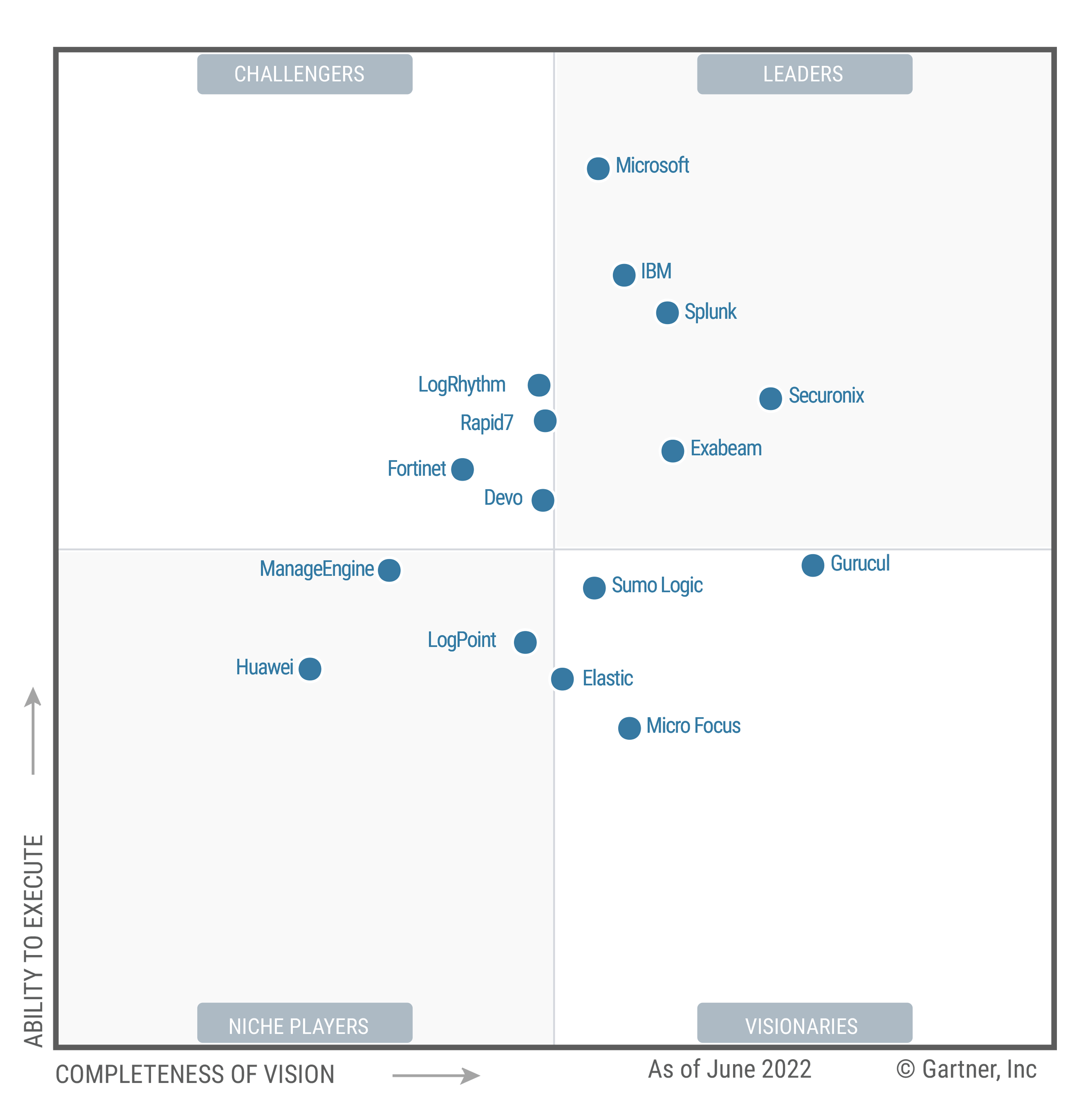
Don’t just take our word for it. Securonix has been named a Leader for the 4th consecutive year in the 2022 Gartner Magic Quadrant for Security Information and Event Management report.
WHITEPAPER
Learn how to scale security operations to keep up with threat inflation.

“We have seen a return on investment many times over. There have been data-loss events that we’ve prevented which, had they left the company, would have represented billions of dollars of intellectual property.”
“With threat chaining, we’ve found the false-positive rate has decreased very significantly. That was something that we never could have achieved before.”
“The world class SIEM helps us monitor our critical infrastructure. Being in the online education industry we are always bombarded with multiple modern attacks. Securonix never disappoints and the attackers are never missed by this tool. A five star product for sure.”
Our most comprehensive offering for TDIR is built on the Data Cloud and offers seamless end-to-end cybersecurity analytics and operations.
Thanks for contacting us! We will get in touch with you shortly.
Thanks for contacting us! We will get in touch with you shortly.