- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
- MSSPs
- Scale multi-tenant security with predictable economics.
-
- Resources
- Partners
- Company
- Blog
Threat Intelligence, Threat Research
Securonix Threat Labs 2025 Annual Autonomous Threat Sweeper Intelligence Insights
Authors: Dheeraj Kumar and Sina Chehreghani
Executive Summary:
The 2025 Annual Cyber Threat Intelligence Report captures the year’s most impactful attack patterns across exploitation-led intrusion, advanced malware (including AI-assisted techniques), and the ongoing evolution of ransomware/RaaS economics. Across multiple campaigns, threat actors prioritized speed-to-impact through weaponized vulnerabilities (notably ToolShell SharePoint exploitation and React2Shell / CVE-2025-55182), while simultaneously improving stealth using in-memory execution, cloud-native abuse, living-off-the-land tooling, and increasingly AI-enabled obfuscation.
The year also reinforced that defenders must track threats as repeatable behaviors, not only as malware names: webshell placement, privilege escalation, rapid lateral movement, exfiltration via common tools (e.g., rclone), defense evasion (shadow copy deletion / log clearing), and identity compromise pathways (MFA abuse, remote tool coercion). The report combines research-driven deep dives (e.g., CHAMELEON#NET, SERPENTINE#CLOUD, OBSCURE#BAT, DEEP#DRIVE, SHADOW#REACTOR) with major exploitation themes (ToolShell, React2Shell), ransomware ecosystem movement (e.g., LockBit/LockBit 5.0, Akira, Ghost/Cring, VanHelsing, Dire Wolf, Gunra, FunkSec, Nnice), and advanced/nation-state-aligned activity (e.g., EvilAI, LummaC2, BRICKSTORM, PerfhLoader → PondRAT/POOLRAT, plus Zbot/DarkGate staging observed in high-impact intrusion chains).
Key Findings:
- Vulnerability Exploitation Became the Fastest Path to Enterprise Impact
Large-scale exploitation cycles, especially ToolShell SharePoint campaigns (including CVE sets such as CVE-2025-53770 / CVE-2025-53771 and related chains) and React2Shell (CVE-2025-55182), enabled rapid post-exploitation activity including webshell deployment, credential access, and lateral movement—often compressing breach timelines from days to hours. - Threat Actors Operationalized “In-Memory + Staged Delivery” as a Default
Multiple campaigns relied on reflective loading, custom decryption, and in-memory execution to reduce disk artifacts. This was consistently reinforced in deep dives such as CHAMELEON#NET and SHADOW#REACTOR, where staging layers and in-memory payload deployment were central to stealth and persistence. - Cloud and Trusted Platform Abuse Increased Stealth and Reach
Adversaries used legitimate infrastructure and trusted services for distribution and tunneling. SERPENTINE#CLOUD highlighted abuse patterns (e.g., tunnels) that complicate perimeter-based detection, while DEEP#DRIVE emphasized the operational value of blending into normal cloud/workflow activity. - Ransomware/RaaS Shifted Further Toward a “Product + Affiliate + Supply Chain” Model
2025 ransomware activity reflected mature service models and cross-platform targeting (Windows/Linux/ESXi), including VanHelsing (RaaS) and LockBit 5.0, alongside continued impact from Akira and Ghost/Cring. Newer or fast-moving strains such as Dire Wolf, Gunra, FunkSec, and Nnice reinforced that branding changes quickly, while TTPs remain stable. - Exfiltration and Defense Evasion Were the Most Reliable “Late-Stage” Warning Signals
Across intrusion types, the highest-confidence pre-impact signals included: shadow copy deletion, event log clearing, mass file modifications, and bulk outbound transfers (e.g., rclone-style exfiltration), often preceding ransomware deployment or data extortion. - AI-Enabled Threats Matured Beyond Lure Creation into Evasion and Automation
2025 saw AI increasingly used to mutate code and evade static controls (AI-obfuscated phishing and AI-generated malware workflows). Threats such as EvilAI and AI-associated capability clusters (e.g., PROMPTFLUX / PROMPTSTEAL / PROMPTLOCK / FRUITSHELL / QUIETVAULT) highlighted the need for behavior-based correlation rather than content-only detection. - Nation-State and Advanced Operations Maintained Long-Dwell, Covert Tradecraft
Tooling such as BRICKSTORM and loader chains like PerfhLoader → PondRAT/POOLRAT demonstrated continued investment in covert C2 methods and stealthy persistence, while exploit chains against enterprise platforms (e.g., SAP NetWeaver webshelling) showed how strategic access can be gained at scale. - Identity and Remote-Tool Coercion Remained High-Impact Entry Paths
Intrusion chains tied to social engineering and remote tool installation—seen in campaigns associated with Scattered Spider patterns and Black Basta enablement workflows—showed that “trusted workflow abuse” (MFA manipulation, helpdesk coercion, remote access tools) remains a top driver of successful compromise.
About Securonix Autonomous Threat Sweeper
Securonix Threat Labs curates and analyzes emerging threats throughout the year to help defenders prioritize what matters and respond faster. As part of that mission, the Autonomous Threat Sweeper (ATS) team provides continuous, analyst-led threat monitoring and analysis. They track threats as surfaced in public intelligence reporting and open research, vets what’s investigation-worthy, and turns that signal into structured, defender-usable insight. ATS analysts document key behaviors and indicators in clear summaries, apply an internal severity triage to support prioritization, and capture contextual details, such as victim region and impacted industries, as described in reporting.
ATS also helps turn emerging threat reporting into practical defensive action. ATS maps reported indicators of compromise (IoCs) and observed tactics, techniques, and procedures (TTPs) to relevant telemetry fields so the team can quickly build targeted hunt queries and conduct retrospective searches in environments where ATS is enabled. When ATS identifies matches worth investigating, the team escalates findings through analyst-authored reporting (including Threat Detection Reports) and ongoing metrics and insights. This helps security teams prioritize follow-up, tune detections, and guide retrospective hunting with clarity and context. ATS continues to adapt workflows to improve speed and usability, including capabilities such as on-demand intelligence submission and automated case creation to accelerate review and response.
ATS 2025 Emerging Threat Intelligence Insights
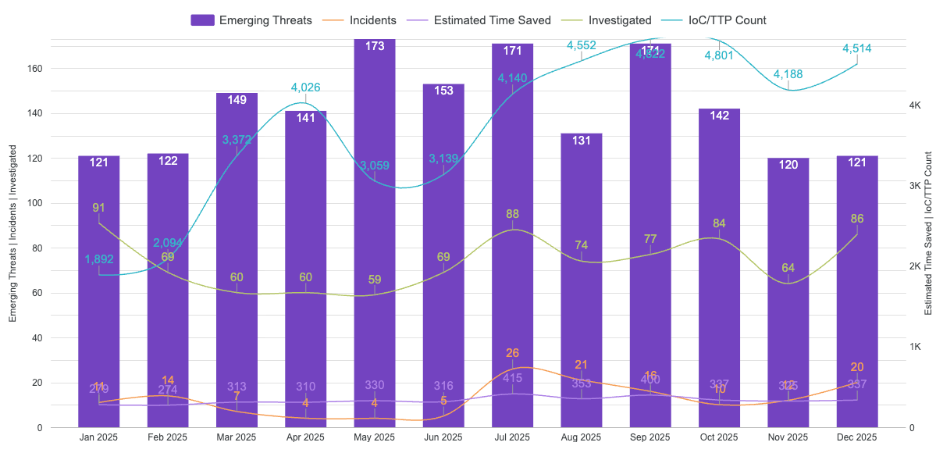
Across the year, ATS tracked and analyzed 1,695 curated emerging-threat items, sustaining a steady cadence of ~141 items per month. Monthly volumes ranged from 109 to 168, with the highest months (July and September, 168 each) modestly above baseline rather than single-event anomalies. Overall volume remained consistent throughout the year. This supports a retrospective focused less on isolated “spikes” and more on how the mix of threat narratives evolved within what ATS tracked over time.
ATS also maintained broad intake coverage across the intelligence ecosystem. In 2025, ATS referenced 355 distinct normalized sources, and no single publisher dominated the tracked set. The largest single source represented 4.7% of all tracked items, and the top publishers remained individually below 5%. This suggests ATS continues to capture signals across a diverse stream rather than reflecting one source’s editorial lens.
Severity in this report is an ATS internal triage used to support prioritization, not a claim of real-world prevalence or verified impact beyond what ATS tracked in reporting. Across 2025, ATS triaged 455 items (26.8%) as HIGH, 704 (41.5%) as MEDIUM, and 536 (31.5%) as LOW. The most pronounced shift was in late-year prioritization mix: Q4 was 72.3% HIGH (298 of 412), and Q4 alone accounted for 65.6% of all HIGH-triaged items recorded in 2025 (298 of 455), despite representing ~24% of total tracked volume.
What emerged in 2025 reporting: macro-themes that explain the year
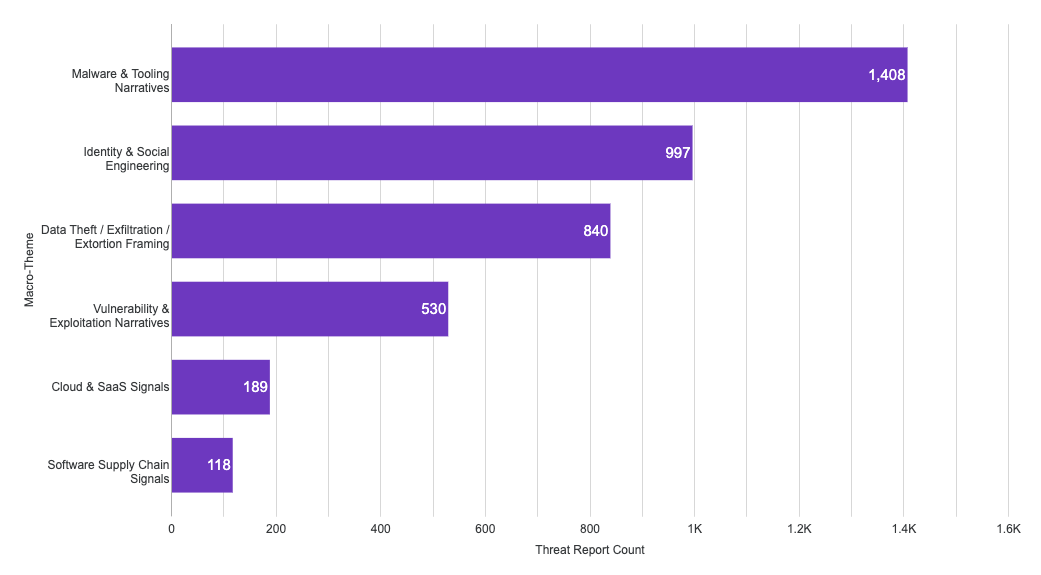
From the intelligence ATS produced, a small set of macro-themes explains the vast majority of what surfaced in 2025 reporting (themes derived from consistent keyword-based tagging across ATS-authored titles and summaries; individual items may map to multiple themes). Across six macro-themes, 97.8% of tracked items mapped to at least one theme:
- Malware & tooling narratives: 1,408 items (83.1%)
- Identity & social engineering: 997 (58.8%)
- Data theft / exfiltration / extortion framing: 840 (49.6%)
- Vulnerability & exploitation narratives: 530 (31.3%)
- Cloud & SaaS signals: 189 (11.1%)
- Software supply chain signals: 118 (7.0%)
These themes frequently co-occur, reflecting how reporting increasingly describes multi-stage intrusions rather than isolated techniques. In particular, the year’s dominant storyline is an “access → enablement → outcome” chain: 47.3% of all tracked items (802) combined identity/social engineering with malware/tooling language, and 27.8% (472) combined identity + malware/tooling + data-theft/extortion language. Overall, what surfaced most consistently in 2025 reporting was a repeated pattern: identity-driven access and social engineering enabling commodity and bespoke tooling, culminating in theft, extortion pressure, or both.
Second-half signals: cloud/SaaS and supply chain narratives strengthened
Two theme-level shifts stood out in the second half. Cloud & SaaS narratives grew from 22 items in Q1 to 66 in Q3 (remaining elevated in Q4 at 61). Software supply chain signals grew from 9 in Q1 to 40 in Q3 (remaining high in Q4 at 38). These trends reinforce a practical operational reality for defenders: attacker narratives increasingly emphasize identity abuse and token/session mechanics, third-party trust relationships, and the security posture of platforms outside traditional on-prem boundaries.
Directional victimology
Where reporting provided context, ATS captured directional insights on impacted industries and victim regions, explicitly as described in reporting, not independently verified victimology. Specific impacted industries were named for 576 items (34.0%); when specified, the most frequently cited were Government (202 mentions), Technology (168), Finance (141), Defense (73), and Manufacturing (62) (with Healthcare close behind at 60). Victim region was specified for 842 items (49.7%); when specified, the most frequently cited regions were Global (141 mentions), the United States (119), Europe (53), South Korea (53), and Ukraine (53). These attributes should be read as a structured lens over what reporting chose to highlight, not as a definitive census of targeting.
What the 2025 picture shows about ATS value
Taken together, the 2025 picture shows ATS execution and defender value: sustained monitoring cadence; broad and diverse source coverage; high-consistency analyst documentation; structured triage for prioritization; and a coherent set of macro-themes that repeatedly connect identity-driven access, tooling and enablement, exploitation, and data-theft/extortion outcomes, with strengthening second-half signals in cloud/SaaS and software supply chain narratives.
This report summarizes that year of ATS work. It is a measurable, evidence-backed retrospective of what emerged in threat reporting during 2025 and how ATS tracked and analyzed it, so security teams can prioritize awareness, tune detections, and guide retrospective hunting with clarity and context.
Securonix Threat Research: 2025 Highlights
In 2025, Securonix Threat Research team repeatedly saw adversaries succeed by abusing trust and blending into normal enterprise behavior leveraging trusted services, native Windows scripting, and fileless execution to reduce detection opportunities. DEEP#DRIVE (NK/Kimsuky-aligned) demonstrated targeted intrusions that hide behind legitimate workflows (trusted cloud platforms and PowerShell-heavy tradecraft), while SERPENTINE#CLOUD showed actors staging multi-step infections via deceptive user lures and “legitimate” infrastructure (Cloudflare tunneling), ultimately reaching in-memory payload execution.
This theme of multi-stage stealth and living-off-the-land intensified at the payload layer: CHAMELEON#NET highlighted obfuscated, staged loaders optimized for in-memory execution, and OBSCURE#BAT proved that simple script entry can still culminate in stealth persistence via rootkit-level techniques. The year also reinforced proactive defense engineering through the CVE-2025-53770 SharePoint simulation work, using realistic telemetry (suspicious file writes and abnormal w3wp.exe child processes) to validate detections before public tooling spreads. Finally, SHADOW#REACTOR captured a modern access-broker style chain that combines “commodity” scripting with advanced evasion: VBS → PowerShell → .NET Reactor loader → MSBuild LOLBin handoff, using text-only staging files (qpwoe*.txt, teste*.txt, config.txt) to transport binary content and ultimately delivering Remcos RAT with in-memory execution.
Detection Summary Table:
| | ||||
|---|---|---|---|---|
| Report / Campaign | Primary Detection Signals | Securonix Hunt Query | Required Telemetry | Tuning Notes |
| DEEP#DRIVE (Kimsuky/NK-aligned) | Dropbox used for delivery/exfil + staged PowerShell scripts in user profile paths + persistence masquerading as ChromeUpdateTaskMachine. | index = activity AND requesturl CONTAINS “dl.dropboxusercontent[.]com AND (requesturl CONTAINS “kxsxhx-f.txt” OR requesturl CONTAINS “kxsxhx-x.txt” OR requesturl CONTAINS “V02_-D.pdf.pdf” OR requesturl CONTAINS “241002-2025-GA-10-v2.pdf” OR requesturl CONTAINS “cjfansgmlans1-x.txt) | Web Proxy / NGFW + Endpoint Mgmt | If Dropbox is common, keep IOC list but raise severity only when paired with suspicious PowerShell staging or task creation (ChromeUpdateTaskMachine). |
| SERPENTINE#CLOUD (Cloudflare Tunnel staging) | Startup folder persistence (.vbs/.bat/.py) + python loader artifacts (run.py, mag.bin, a.txt) + domains (nhvncpure). | index = activity AND rg_functionality = “Endpoint Management Systems” AND deviceaction = “File created” AND filepath CONTAINS “\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\” AND filename IN (“pws1.vbs”,”PWS.vbs”,”startuppp.bat”,”Wsandy1.py”,”Wsandy2.py”,”Wsandy3.py”,”Okwan1.py”,”Okwan2.py”,”Okwan3.py”) | Endpoint Mgmt (optional NGFW/Web) | Startup writes of script/Python files are uncommon—treat as high signal; confirm by hunting python.exe executing run.py / decrypting mag.bin with a.txt. |
| CHAMELEON#NET (.NET loader chain) | Word → InstallUtil LOLBin abuse + Run-key persistence (…\Run\svchost.exe) + suspicious delay behavior + known C2/port. | index = activity AND rg_functionality = “Endpoint Management Systems” AND image CONTAINS “InstallUtil.exe” AND parentimage CONTAINS “word.exe” | Endpoint Mgmt (optional NGFW/Web) | Office → InstallUtil is very high signal. Escalate further if you also see Run-key persistence or the ping 127.0.0.1 -n 37 delay pattern. |
| OBSCURE#BAT (r77 rootkit chain) | $nya- artifact prefix + registry-resident payload keys ($nya-dll32/64) + driver/service persistence (ACPIx86.sys). | index = activity AND rg_functionality = “Endpoint Management Systems” AND (deviceaction = “File created” OR deviceaction = “File created (rule: FileCreate)”) AND (filename CONTAINS “$nya-” OR filepath CONTAINS “$nya-“) | Endpoint Management Systems | $nya- is a strong discriminator. Escalate immediately if you also observe registry writes to $nya-dll* or driver creation under System32\Drivers. |
| CVE-2025-53770 (SharePoint) | Web-accessible file writes (spinstall0.aspx/.ashx) under SharePoint web paths + abnormal child processes spawned by w3wp.exe. | index = activity AND rg_functionality = “Endpoint Management Systems” AND deviceaction = “File created” AND filename IN (“spinstall0.aspx”, “spinstall0.ashx”, “w3wp.exe”) | Endpoint Management Systems | Prioritize when LAYOUTS/VDir file writes are followed by w3wp.exe spawning cmd/powershell/wscript soon after. |
| SHADOW#REACTOR (text-only staging + Remcos) | Text-only staging (qpwoe*.txt, teste*.txt, config.txt) + anomalous chain wscript → powershell → MSBuild + known C2 IPs. | index = activity AND rg_functionality = “Endpoint Management Systems” AND deviceaction = “Process Create” AND (sourceprocessname = “wscript.exe” AND destinationprocessname = “powershell.exe”) OR (sourceprocessname = “powershell.exe” AND destinationprocessname = “MSBuild.exe”) | Endpoint Mgmt + Web Proxy (recommended) | Escalate to critical when the process chain appears alongside %TEMP% text staging files or proxy hits to the C2 IPs (e.g., 91.202.233.215). |
ToolShell: SharePoint RCE Exploitation Waves
ToolShell was one of 2025’s most impactful on-premises server exploitation waves, targeting Microsoft SharePoint environments through a chained technique that combined authentication bypass with insecure deserialization to achieve unauthenticated remote code execution via SharePoint’s application endpoints. Exploitation activity commonly pivoted through the SharePoint _layouts surface, especially requests interacting with ToolPane.aspx and showed repeatable fingerprints in web traffic that helped defenders distinguish exploitation from normal administrative use.
Beyond initial compromise, ToolShell’s operational risk came from persistence and “access-after-patching.” Post-exploitation behavior included dropping malicious ASPX artifacts under SharePoint’s LAYOUTS path and extracting ASP.NET MachineKey / ValidationKey material, enabling attackers to generate valid, signed __VIEWSTATE payloads for repeatable code execution through the normal SharePoint worker process (w3wp.exe). This makes response more complex than patching alone: defenders must also assume cryptographic material may be compromised and consider key rotation alongside detection and eradication actions.
Detection Summary Table:
| Detection Focus | High-Value Signals | Securonix Hunt Query | Required Telemetry | Tuning Notes |
|---|---|---|---|---|
| Exploit attempt: ToolPane POST | POST to /_layouts/15/ToolPane.aspx | index=activity AND (rg_functionality=”Web Proxy” OR rg_functionality=”Next Generation Firewall”) AND requestmethod=”POST” AND requesturl CONTAINS “/_layouts/15/ToolPane.aspx” | Web Proxy / NGFW | Escalate if same source hits multiple SharePoint hosts rapidly (wave behavior). |
| Auth bypass fingerprint: SignOut Referer | ToolPane access with Referer /_layouts/SignOut.aspx | index=activity AND (rg_functionality=”Web Proxy” OR rg_functionality=”Next Generation Firewall”) AND requesturl CONTAINS “/ToolPane.aspx” AND (requestcontext CONTAINS “/_layouts/SignOut.aspx” OR message CONTAINS “/_layouts/SignOut.aspx”) | Web Proxy / NGFW | Header may land in different fields; validate where Referer is stored per data source. |
| IOC sweep: exploit wave infra | Known wave IPs + Firefox/120 UA | index=activity AND (rg_functionality=”Web Proxy” OR rg_functionality=”Next Generation Firewall”) AND (sourceaddress IN (“107.191.58.76″,”104.238.159.149″,”96.9.125.147”) OR requestclientapplication CONTAINS “Firefox/120.0”) AND requesturl CONTAINS “/_layouts/” | Web Proxy / NGFW | Use for quick triage; donÕt rely on IOCs alone for durable detection. |
| Implant write: LAYOUTS ASPX | .aspx created in …\TEMPLATE\LAYOUTS\ | index=activity AND rg_functionality=”Endpoint Management Systems” AND deviceaction=”File created” AND filepath CONTAINS “\\TEMPLATE\\LAYOUTS\\” AND filename ENDS WITH “.aspx” | Endpoint Mgmt | Treat as high severity on SharePoint servers; correlate with ToolPane POSTs for confidence. |
| Webshell activity: w3wp child processes | w3wp.exe spawning shells/tools; payload execution blends into w3wp | index=activity AND rg_functionality=”Endpoint Management Systems” AND deviceaction=”Process Create” AND sourceprocessname=”w3wp.exe” AND destinationprocessname IN (“cmd.exe”,”powershell.exe”,”wscript.exe”,”cscript.exe”,”msbuild.exe”) | Endpoint Mgmt | Raise to critical if combined with LAYOUTS ASPX file creation or ViewState indicators. |
| Persistence-after-patching: ViewState abuse | __VIEWSTATE requests after key theft enables signed payloads | index=activity AND (rg_functionality=”Web Proxy” OR rg_functionality=”Next Generation Firewall”) AND requesturl CONTAINS “/_layouts/” AND (requesturl CONTAINS “__VIEWSTATE=” OR requestcontext CONTAINS “__VIEWSTATE”) | Web Proxy / NGFW | Best as correlation signal; highlight as Òpost-compromiseÓ behavior. |
React2Shell: Pre-Auth RCE at Scale
React2Shell (CVE-2025-55182) emerged as a high-impact pre-auth remote code execution issue in React Server Components (RSC), where attackers could trigger exploitation with a single crafted POST request before server-side actions are validated. The weakness is tied to improper deserialization / insufficient validation of RSC form payloads, enabling attacker-controlled “gadget” paths that reach JavaScript’s Function constructor and execute arbitrary code under the Node.js runtime context. A key operational accelerant was that the vulnerable flow could often be reached by simply including a Next-Action header—meaning attackers didn’t necessarily need to know a real action name, and payloads would still be parsed.
Exploitation behavior evolved quickly from mass probing into multi-outcome intrusion playbooks. Early traffic often looked like execution verification (e.g., whoami, arithmetic, MD5/Base64 hashing) followed by automated payload retrieval using wget/curl, and in some cases PowerShell-delivered miners on Windows. At scale, campaigns delivered botnet/miner payloads (including Mirai/Gafgyt-style variants) and in some instances pivoted toward credential theft targeting Git and cloud environments, raising the risk of downstream cloud compromise and supply-chain impact. On Linux, observed follow-on tradecraft included multi-stage loaders, persistence via systemd/cron/rc.local, and covert installation of Node.js and obfuscated JavaScript in hidden directories to maintain durable access.
Detection Summary Table:
| Detection Focus | High-Value Signals | Securonix Hunt Query | Required Telemetry | Tuning Notes |
| Exploit attempt: Next-Action + /api/actions | POST to /api/actions/* with Next-Action header | index=activity AND (rg_functionality=”Web Proxy” OR rg_functionality=”Next Generation Firewall”) AND requestmethod=”POST” AND requesturl CONTAINS “/api/actions/” AND message CONTAINS “Next-Action” | Web Proxy / NGFW | Very high signal when URI + header both present. |
| Exploit markers: RSC payload strings | $@ chunks, resolved_model, constructor:constructor, child_process, exec*, readFileSync/writeFileSync | index=activity AND (rg_functionality=”Web Proxy” OR rg_functionality=”Next Generation Firewall”) AND requestmethod=”POST” AND (message CONTAINS “resolved_model” OR message CONTAINS “constructor:constructor” OR message CONTAINS “child_process” OR message CONTAINS “execSync” OR message CONTAINS “readFileSync”) | Web Proxy / NGFW | Use as correlation signal if your proxy logs don’t capture full bodies reliably. |
| Fast filter: keyword sweep | #constructor, vm#runInThisContext, child_process#execSync, fs#readFileSync, fs#writeFileSync | index=activity AND (rg_functionality=”Web Proxy” OR rg_functionality=”Next Generation Firewall”) AND requestmethod=”POST” AND (message CONTAINS “#constructor” OR message CONTAINS “child_process#execSync” OR message CONTAINS “fs#readFileSync”) | Web Proxy / NGFW | Don’t overfit to __proto__; viable exploits don’t require it. |
| Post-exploit: Node spawns shell/downloader | node/node.exe → sh/bash/curl/wget or cmd/powershell | index=activity AND (rg_functionality=”Endpoint Management Systems” OR rg_functionality=”Antivirus / Malware / EDR”) AND deviceaction=”Process Create” AND (sourceprocessname=”node” OR sourceprocessname=”node.exe”) AND destinationprocessname IN (“sh”,”bash”,”curl”,”wget”,”cmd.exe”,”powershell.exe”) | Endpoint / EDR | Raise to critical if it follows an exploit-marker POST on the same asset within 5–15 minutes. |
| Linux persistence after exploitation | systemd/cron/rc.local persistence | index=activity AND rg_functionality=”Endpoint Management Systems” AND (deviceaction=”File created” OR deviceaction=”File modified”) AND (filepath CONTAINS “/etc/systemd/system” OR filepath CONTAINS “/etc/cron” OR filepath CONTAINS “/etc/rc.local”) | Endpoint Mgmt | Prioritize on internet-facing/container hosts running Node/React workloads. |
| Secrets theft follow-on | .env, Git/cloud credential scraping attempts | index=activity AND (rg_functionality=”Endpoint Management Systems” OR rg_functionality=”Antivirus / Malware / EDR”) AND (message CONTAINS “.env” OR message CONTAINS “AWS_” OR message CONTAINS “id_rsa”) | Endpoint / EDR | Use as “blast radius” hunt on any confirmed exploited host. |
Ransomware & RaaS: 2025 Market Shifts
In 2025, ransomware continued to evolve into a service-driven ecosystem where capability is increasingly “assembled” rather than built: initial access (often exploit-led), commodity exfiltration tooling, affiliate-style execution, and rapid encryption at scale. This pattern was visible across established and emerging families LockBit (including LockBit 5.0), Akira, and Ghost/Cring, alongside newer or less mature brands such as Dire Wolf, Gunra, Nnice, and FunkSec with many operations prioritizing compressed timelines to impact over prolonged stealth.
A major driver of 2025 disruption was exploit-to-ransomware conversion where access gained through exposed enterprise applications or perimeter infrastructure quickly turned into data theft and encryption. One incident chain showed exploitation of Confluence leading to LockBit deployment, where exfiltration began shortly after initial access using rclone to Mega, followed by broad ransomware distribution through enterprise software deployment tooling (PDQ Deploy). In parallel, campaigns exploiting Fortinet infrastructure culminated in deployment of a new ransomware strain (“SuperBlack”) associated with an operator tracked as Mora_001, with multiple behaviors suggesting ecosystem-level reuse and customization consistent with the broader ransomware supply chain.
The RaaS market also kept expanding in a more productized direction. VanHelsing emerged as a new RaaS brand with an affiliate model and explicit cross-platform targeting (Windows, Linux, ESXi), reflecting the economics of pursuing enterprise virtualization and hybrid environments. This cross-platform shift was reinforced by LockBit 5.0, which explicitly targets Windows, Linux, and ESXi, further confirming that modern ransomware readiness requires coverage beyond Windows endpoints alone.
Operationally, 2025 reinforced that ransomware is best tracked as a TTP-led problem more than a family-led one. Ghost (Cring) exemplified this: operators were reported to rotate payloads, change extensions and ransom note text, and use multiple email addresses, complicating attribution, while consistently relying on exploitation of unpatched internet-facing systems and rapid progression to deployment. Across families, “late-stage” behaviors remained highly consistent and detection-worthy: recovery inhibition and evidence removal (log clearing and shadow copy deletion), process termination and anti-analysis steps (seen in Gunra), and extension/note-based encryption markers (FunkSec using “.funksec” and Nnice using “.xdddd” plus Readme.txt).
Finally, ransomware enablement in 2025 was not limited to vulnerability exploitation. A Black Basta intrusion chain operationalized email bombing and chat-based impersonation to initiate remote sessions and deliver malware showing how “helpdesk-shaped” workflows are being weaponized to gain interactive footholds that can later support ransomware outcomes. On the capability side, an increasing focus on defense evasion, including driver abuse to terminate AV processes, alongside early signals of automation-forward ransomware like PromptLock, assessed as AI-powered and capable of using a local LLM via Ollama to generate and execute malicious Lua scripts for reconnaissance and targeting.
Detection Summary Table:
| Report / Cluster | Typical Entry | Highest Signal | Primary Telemetry | Securonix Hunt Query |
| Dire Wolf | (Varies) | Shadow copy / log clearing + rapid encryption | EDR + Windows logs | index=activity AND rg_functionality=”Endpoint Management Systems” AND (message CONTAINS “vssadmin delete shadows” OR message CONTAINS “wevtutil cl” OR transactionstring1 CONTAINS “vssadmin delete shadows” OR transactionstring1 CONTAINS “wevtutil cl”) |
| Gunra | (Varies) | WMI/VSS deletion + extension-based encryption | EDR + Windows logs | index=activity AND rg_functionality=”Endpoint Management Systems” AND (message CONTAINS “Win32_ShadowCopy” OR message CONTAINS “vssadmin delete” OR transactionstring1 CONTAINS “Win32_ShadowCopy” OR transactionstring1 CONTAINS “vssadmin delete”) |
| VanHelsing (RaaS) | Affiliate model | Cross-platform payload staging (Windows/Linux/ESXi) | EDR + Linux telemetry | index=activity AND hostname IS NOT NULL AND (message CONTAINS “esxi” OR message CONTAINS “/vmfs/” OR transactionstring1 CONTAINS “esxi” OR transactionstring1 CONTAINS “/vmfs/”) |
| VanHelsing (tracking) | Affiliate model | Known ext/note spikes (environment-specific) | File telemetry | index=activity AND rg_functionality=”Endpoint Management Systems” AND deviceaction=”File created” AND filename CONTAINS “.vanhelsing” |
| Fortinet→“SuperBlack” | Edge exploit | Edge compromise → rapid internal stage + ransomware deployment | Network + EDR | index=activity AND (rg_functionality CONTAINS “Network” OR rg_functionality CONTAINS “Firewall”) AND (deviceaction CONTAINS “admin” OR deviceaction CONTAINS “config”) |
| Confluence→LockBit | App exploit | rclone exfil to cloud + enterprise deployment tool abuse | EDR + Proxy/DNS | index=activity AND rg_functionality=”Endpoint Management Systems” AND deviceaction CONTAINS “Process” AND (sourceprocessname = “rclone.exe” OR destinationprocessname = “rclone.exe”) |
| Ghost/Cring | Exploit-heavy | Web shells + staged downloaders + Cobalt Strike | Web + EDR | index=activity AND rg_functionality=”Endpoint Management Systems” AND deviceaction CONTAINS “Process” AND (destinationprocessname = “powershell.exe” OR sourceprocessname = “powershell.exe” OR message CONTAINS “powershell” OR transactionstring1 CONTAINS “powershell”) AND (message CONTAINS “http” OR transactionstring1 CONTAINS “http”) |
| Nnice | (Varies) | New ext spike + “Readme.txt” note | File telemetry | index=activity AND rg_functionality=”Endpoint Management Systems” AND deviceaction=”File created” AND (filename CONTAINS “.xdddd” OR filename=”Readme.txt”) |
| FunkSec | (Varies) | New ext spike (.funksec) + mass writes | File telemetry | index=activity AND rg_functionality=”Endpoint Management Systems” AND deviceaction=”File created” AND filename CONTAINS “.funksec” |
| Black Basta (Teams lure) | Social engineering | Teams-driven remote session initiation + tool drop | Email/Collab + EDR | index=activity AND rg_functionality=”Endpoint Management Systems” AND deviceaction CONTAINS “Process” AND (sourceprocessname IN (“quickassist.exe”, “anydesk.exe”, “screenconnect.exe”, “teamviewer.exe”) OR destinationprocessname IN (“quickassist.exe”, “anydesk.exe”, “screenconnect.exe”, “teamviewer.exe”)) |
| LockBit 5.0 | Multi-platform | Windows/Linux/ESXi targeting + fast encryption behavior | EDR + Linux/ESXi | index=activity AND rg_functionality=”Endpoint Management Systems” AND (message CONTAINS “/vmfs/” OR message CONTAINS “esxi” OR transactionstring1 CONTAINS “/vmfs/” OR transactionstring1 CONTAINS “esxi” OR filename CONTAINS “.lockbit” OR filepath CONTAINS “.lockbit”) |
| Akira (advisory) | Multiple vectors | Credential access + lateral movement + encryption precursors | EDR + Windows logs | index=activity AND rg_functionality=”Endpoint Management Systems” AND (message CONTAINS “net group” OR message CONTAINS “nltest” OR message CONTAINS “vssadmin delete” OR transactionstring1 CONTAINS “net group” OR transactionstring1 CONTAINS “nltest” OR transactionstring1 CONTAINS “vssadmin delete”) |
| ThrottleStop driver abuse | BYOVD-style | Driver load → AV/EDR process termination bursts | EDR + Sysmon | index=activity AND rg_functionality=”Endpoint Management Systems” AND (deviceaction CONTAINS “Driver” OR category=”Driver”) |
| PromptLock (AI-powered PoC) | Prototype | Local LLM usage + Lua script generation + exfil/encrypt chain | EDR + process | index=activity AND rg_functionality=”Endpoint Management Systems” AND (message CONTAINS “ollama” OR message CONTAINS “lua” OR transactionstring1 CONTAINS “ollama” OR transactionstring1 CONTAINS “lua”) |
Advanced AI Malware & Nation-State Tradecraft
In 2025, advanced intrusions increasingly blended three forces into a single playbook: AI-enabled tradecraft, exploit-led entry, and long-dwell nation-state operations often converging into financially motivated outcomes. Across the year, AI was used not only to accelerate malware development, but to harden delivery and evasion. Campaigns like EvilAI operationalized AI-generated code (notably JavaScript executed via Node.js), layered obfuscation, and persistence (scheduled tasks / Run keys), supported by encrypted C2 for command execution and payload staging. AI-enabled deception also expanded: AI-obfuscated phishing matured into defender-evasion engineering, with rapidly mutating script content designed to break static detections pushing defenders toward behavior-first correlation across identity, endpoint, and network telemetry. We also tracked broader experimentation with prompt-driven capability clusters and families (PROMPTFLUX, PROMPTSTEAL / LAMEHUG, PROMPTLOCK, FRUITSHELL, QUIETVAULT) as the ecosystem explored AI-assisted reconnaissance, social engineering refinement, and automation loops.
At the same time, credential theft and scalable access tooling remained persistent. Infostealers like LummaC2 sustained high-volume exfiltration of sensitive data (credentials, browser artifacts, and session material), reinforcing why containment depends on correlating endpoint process behavior with outbound beaconing and sudden credential access anomalies. Targeted phishing clusters also refined loader, in-memory execution patterns: Sapphire Werewolf delivered a .NET loader (protected with .NET Reactor) that decoded a Base64 PE, loaded it directly via Assembly.Load(), and executed in memory; the payload was an updated Amethyst stealer with extensive VM checks and Triple DES string encryption. The stealer collected credentials and artifacts from multiple browsers and tools (including FileZilla and SSH configs), leveraged scheduled task persistence, and used web-service-linked channels for exfiltration.
Intrusion-to-impact pathways were also shaped by hybrid social engineering and “living-off-trust” techniques. Black Basta campaigns weaponized collaboration workflows with impersonation lures and coercion into installing remote tools such as AnyDesk, QuickAssist, or TeamViewer, creating a trusted access channel for payload delivery. Their stack included Zbot and DarkGate, alongside obfuscated payload staging and encrypted delivery techniques that shorten the path from foothold to operational control. Parallel identity-centric intrusion tradecraft remained highly effective: Scattered Spider emphasized MFA manipulation and legitimate tooling to accelerate lateral movement toward extortion outcomes, often paired with defensive impairment using driver-based techniques (POORTRY / STONESTOP) and RAT deployment (RattyRAT).
Exploit-led entry and nation-state persistence remained constant accelerators. Beyond application-layer risks such as React2Shell (CVE-2025-55182), exploitation against SAP NetWeaver demonstrated how high-value enterprise platforms can be weaponized: attackers abused endpoints to upload JSP webshells (helper.jsp, cache.jsp, and randomly named variants) into …/servlet_jsp/irj/root/, enabling remote execution via simple GET requests. Some observed activity chained CVE-2025-31324 with CVE-2025-42999 to bypass authentication and execute more covertly (including in-memory execution), followed by post-exploitation tooling such as MSBuild abuse, PipeMagic, Brute Ratel, and evasion via Heaven’s Gate techniques. Meanwhile, long-dwell nation-state tooling such as BRICKSTORM (UNC5221 activity clusters) continued to leverage covert C2 patterns including DNS-over-HTTPS (DoH), while Lazarus-linked chains used loaders such as PerfhLoader to deploy PondRAT / POOLRAT.
Detection Summary Table:
| Report / Cluster | Typical Entry | Highest Signal | Primary Telemetry | Securonix Hunt Query |
| EvilAI (AI-generated JS via Node.js) | Fake apps / staged installers | Node/JS execution + persistence (tasks/Run keys) + encrypted beaconing | EDR / Endpoint Mgmt | index=activity AND rg_functionality=”Endpoint Management Systems” AND ((sourceprocessname IN (“node.exe”,”node”) OR destinationprocessname IN (“node.exe”,”node”) OR message CONTAINS “node”) AND (message CONTAINS “.js” OR transactionstring1 CONTAINS “.js”) AND (message CONTAINS “schtasks” OR message CONTAINS “Scheduled Task” OR message CONTAINS “Run\\” OR transactionstring1 CONTAINS “schtasks”)) |
| AI-obfuscated phishing (script mutation) | Phishing → script execution | “Phish click → script run” correlation; rapidly mutating scripts + follow-on execution | Email + IdP + Endpoint | index=activity AND rg_functionality=”Endpoint Management Systems” AND (message CONTAINS “wscript” OR message CONTAINS “cscript” OR message CONTAINS “powershell”) AND (message CONTAINS “http” OR transactionstring1 CONTAINS “http”) |
| LummaC2 (infostealer) | Malspam / drive-by | Browser data access + outbound exfil bursts | Endpoint + Proxy/DNS | index=activity AND rg_functionality=”Endpoint Management Systems” AND ((message CONTAINS “Login Data” OR message CONTAINS “Web Data” OR message CONTAINS “Cookies” OR transactionstring1 CONTAINS “Login Data” OR transactionstring1 CONTAINS “Web Data”) OR (message CONTAINS “lummac2” OR transactionstring1 CONTAINS “lummac2”)) |
| Sapphire Werewolf → Amethyst stealer | Targeted phishing | Base64 decode → Assembly.Load() in-memory execution; .NET Reactor markers; scheduled task persistence | Endpoint Mgmt | index=activity AND rg_functionality=”Endpoint Management Systems” AND (message CONTAINS “Assembly.Load” OR transactionstring1 CONTAINS “Assembly.Load” OR message CONTAINS “Base64” OR message CONTAINS “.NET Reactor” OR message CONTAINS “Triple DES”) |
| Black Basta (Teams lure → remote tool) | Social engineering | Remote tool install/use spike (AnyDesk/QuickAssist/TeamViewer) followed by payload drop | Collaboration + Endpoint | index=activity AND rg_functionality=”Endpoint Management Systems” AND (message CONTAINS “AnyDesk” OR message CONTAINS “QuickAssist” OR message CONTAINS “TeamViewer” OR transactionstring1 CONTAINS “AnyDesk” OR transactionstring1 CONTAINS “QuickAssist” OR transactionstring1 CONTAINS “TeamViewer”) |
| Zbot + DarkGate (pre-staging stack) | Loader → credential theft | Family strings (if present) + hollowing/encrypted payload hints | Endpoint + EDR | index=activity AND (message CONTAINS “Zbot” OR message CONTAINS “DarkGate” OR transactionstring1 CONTAINS “Zbot” OR transactionstring1 CONTAINS “DarkGate” OR message CONTAINS “process hollowing” OR message CONTAINS “encrypted payload”) |
| Scattered Spider (identity + tooling) | Smishing/vishing | MFA manipulation + remote tool usage + rapid privilege expansion indicators | IdP + Endpoint | index=activity AND (message CONTAINS “MFA” OR message CONTAINS “push” OR message CONTAINS “reset”) AND (message CONTAINS “AnyDesk” OR message CONTAINS “QuickAssist” OR message CONTAINS “TeamViewer”) |
| SAP NetWeaver exploitation + JSP webshells | Internet-facing app exploit | Hits to /developmentserver/metadatauploader + servlet JSP execution path + *.jsp?cmd= | Web/WAF + Endpoint on servers | index=activity AND rg_functionality CONTAINS “Web” AND (message CONTAINS “/developmentserver/metadatauploader” OR transactionstring1 CONTAINS “/developmentserver/metadatauploader” OR message CONTAINS “servlet_jsp/irj/root/” OR transactionstring1 CONTAINS “servlet_jsp/irj/root/” OR message CONTAINS “.jsp\?cmd=” OR transactionstring1 CONTAINS “.jsp\?cmd=” OR message CONTAINS “helper.jsp” OR message CONTAINS “cache.jsp” OR transactionstring1 CONTAINS “helper.jsp” OR transactionstring1 CONTAINS “cache.jsp”) |
| Post-exploitation toolchain (MSBuild / PipeMagic / Brute Ratel / Heaven’s Gate) | After webshell / foothold | MSBuild execution + suspicious injection indicators (dllhost.exe) + evasion keywords | Endpoint Mgmt | index=activity AND rg_functionality=”Endpoint Management Systems” AND ((message CONTAINS “MSBuild.exe” OR transactionstring1 CONTAINS “MSBuild.exe”) AND (message CONTAINS “dllhost.exe” OR message CONTAINS “NtSetContextThread” OR message CONTAINS “Heaven” OR message CONTAINS “Brute” OR message CONTAINS “PipeMagic”)) |
| BRICKSTORM / UNC5221 (covert C2) | Long-dwell intrusion | DoH usage + rare/low-prevalence outbound beacons | DNS/Proxy/TLS + Endpoint | index=activity AND (message CONTAINS “dns over https” OR message CONTAINS “DoH” OR transactionstring1 CONTAINS “dns over https” OR transactionstring1 CONTAINS “DoH”) |
| PerfhLoader → PondRAT / POOLRAT (service/DLL abuse) | Loader via service abuse | Service creation/modification + suspicious DLL load patterns | Windows logs + Endpoint | index=activity AND rg_functionality=”Endpoint Management Systems” AND (message CONTAINS “service” OR message CONTAINS “CreateService” OR message CONTAINS “sc.exe” OR transactionstring1 CONTAINS “CreateService”) AND (message CONTAINS “.dll” OR transactionstring1 CONTAINS “.dll”) |
Conclusion: 2025 Takeaways & 2026 Outlook
2025 Takeaways
In 2025, enterprise risk increasingly came down to how quickly attackers could move from access to impact. Exploit-driven entry points, identity abuse, and stealth-focused malware techniques such as in-memory execution, staged payloads, and abuse of trusted platforms consistently enabled rapid compromise. Ransomware and RaaS models continued to mature and scale, including broader cross-platform targeting. Despite evolving tooling, late-stage attacker behavior remained predictable, with bulk data exfiltration, shadow copy deletion, log tampering, and misuse of remote administration tools serving as reliable warning signals. At the same time, AI accelerated attacker operations by enabling faster malware and script mutation and improving evasion, further eroding the effectiveness of static, indicator-only detection approaches.
2026 Outlook
Looking ahead to 2026, organizations should expect more automated exploit campaigns, deeper focus on identity-centric attack paths such as MFA abuse, token and session hijacking, and social or technical manipulation of helpdesk and remote access workflows, along with wider use of AI to operationalize attacks at scale. This includes increased polymorphism, more convincing and targeted pretexting, and faster attacker decision-making. Sustainable defense will rely less on isolated indicators and more on reducing exposed attack surface, hardening identity controls, and deploying behavior- and correlation-driven detection across endpoint, identity, network, and cloud environments, supported by response playbooks that are fast, repeatable, and well-practiced.
Mitigations & Defensive Recommendations
- Securonix Threat Research (Threat chains & stealth)
- Prioritize behavior-first detections for staged loaders, in-memory execution, and persistence (scheduled tasks, services, Run keys).
- Expand coverage for trusted-platform and cloud abuse (tunnel usage, unusual SaaS activity) using correlation across endpoint + network + identity.
- Standardize “first-hour” response playbooks: isolate host, capture triage artifacts, disable compromised accounts, block outbound C2/exfil.
- ToolShell Exploitation Campaigns (SharePoint)
- Enforce emergency patch SLAs for exploited-in-the-wild SharePoint vulnerabilities; validate with post-patch scanning.
- Reduce exposure: restrict SharePoint admin access, apply WAF/proxy protections, and limit internet reachability where possible.
- Monitor for webshell behaviors: suspicious servlet/ASP/JSP/ASPX file writes, unusual POST/GET patterns, and app pool process spawning.
- React2Shell Vulnerability Abuse
- Patch React/related server components quickly and implement app-layer request monitoring for exploit attempts.
- Add detections for post-exploit staging: PowerShell + outbound HTTP, script-host execution, suspicious child processes from app services.
- Restrict the blast radius: isolate application servers, enforce least privilege, and segment server-to-server communication.
- Ransomware Ecosystem & RaaS Evolution
- Harden against the most reliable “late-stage” signals: alert/block shadow copy deletion, log clearing, mass file modifications, and rapid encryption indicators.
- Detect and throttle exfiltration: outbound volume anomalies, suspicious transfer tools (e.g., rclone-style), and abnormal cloud upload patterns.
- Improve resilience: immutable/offline backups, tested restores, and tiered network segmentation (endpoints, servers, backups, admin plane).
- Advanced Malware, AI-Based Malware, Exploits & Nation-State Activity
- Move beyond signatures: focus on process trees, persistence, memory injection, DoH/covert C2, and rare infrastructure beacons.
- Strengthen identity controls for stealth intrusions: phishing-resistant MFA for admins, conditional access, and strict monitoring of helpdesk resets.
- Reduce exploit pathways: harden internet-facing enterprise apps (ERP/web servers), monitor for webshell placement, and restrict admin interfaces.
Contributors: Nitish Singh, Nikhil Kumar Chadha, and Tanmay Kumar
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.







