- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Cloud Security
By Kayzad Vanskuiwalla, Threat Detection & Analytics, Securonix Threat Labs
Businesses Continue Migrating to the Cloud
Over the last decade, organizations have begun to embark on their journey towards cloud. This started with specific services like Office 365 Email / SharePoint where there was a need to manage some of these on-premises services externally. This was either due to the inability to manage systems (lack of skills) or a shift from a capital expenditure model of depreciating / redundant assets to a more operational expenditure model, where organizations prefer to pay for a service.
Owing to the pandemic, organizations that were on the fence about remote work were forced to re-think their original strategy and culture. With the availability and scalability that cloud service models like SaaS, PaaS, and IaaS offer, organizations are realigning their strategy to incorporate cloud models into even their most critical assets. Now most organizations are incorporating cloud in some form or another to stay competitive.
The Need to Secure the Cloud
Once an organization has identified the need to migrate to the cloud, the next question is what the risk involved with this migration is. Risk assessment is a cycle involving identification, assessment, mitigation, and continuous monitoring. Just as with any new technology, an organization must evaluate how well its cloud strategy supports the overall mission of the organization. With cloud there is an added exposure since the data / infrastructure is at times under the complete control of the cloud service provider.
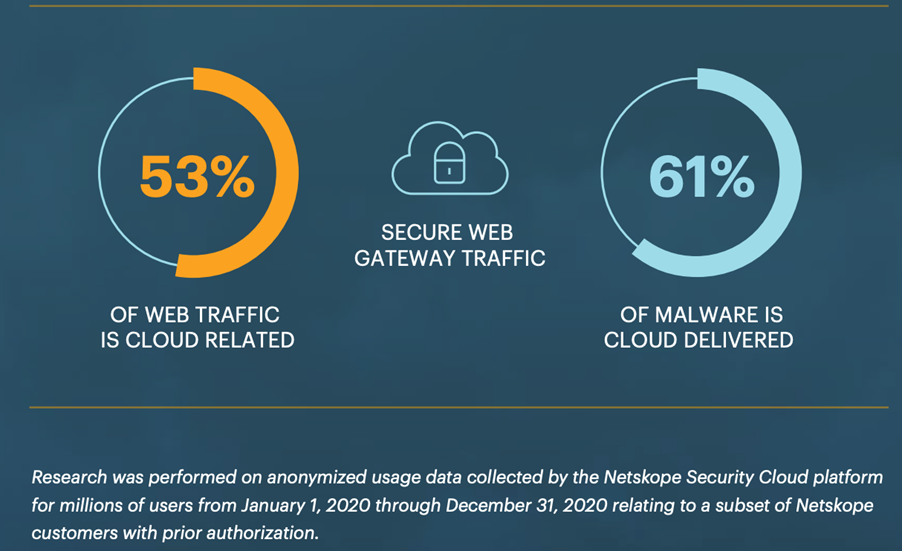
Netskope, in a survey of usage data, identified that 61% of malware is cloud delivered.
While the cloud is built on the principles of rapid elasticity, scalability, and broad network access, this acts as a double-edged sword. If the cloud control pane were to be compromised, or objects misconfigured to make them publicly accessible, it would lead to a great deal of complexity and challenges in the organization’s operations.
Compromised accounts can be misused. Elevated admin privileges or admin account compromise can ultimately lead to sabotage, data loss, and exfiltration. An organization needs to monitor various aspects of its operations in the cloud, including critical / sensitive data essential for its operations (i.e. intellectual property) as well as information that has regulations associated with it like PCI / PII data.
Required Telemetry / Continuous Monitoring
After identifying what we need to protect, the next question revolves around continuous monitoring of this data and how we can achieve this. This involves robust logging of every cloud service, application, and infrastructure being used.
Despite existing preventive measures there are always alternative ways defenses can be evaded, so just as there is a need for defense in depth, there is an equal necessity for detection in depth. When an organization is undergoing an active attack / investigation they shouldn’t be in a spot where there is a lack of relevant data to show a complete picture of the threat.
The Open Web Application Security Project provides a great cheat sheet for required logging on application logs. This should be applicable for all types of key logs including authentication, authorization, privilege events, sessions, data modification, configuration changes, data traversal (import / export or downloads). This reference should be used as a base standard to ensure the organization has the right telemetry available for the cloud services / infrastructure it integrates with.
In the first part of this series we will begin describing a risk-based approach to building a cloud kill chain to proactively detect anomalies and identify threats to cloud services and data. We will use AWS as an example to show how organizations can test these controls and ensure they have the right mechanism to detect these threats.
Cloud Kill Chain
Initial Risk Associated With Entities
A compromise or abuse of the Key / IAM would ultimately mean the adversary (internal or otherwise) would have complete control over the cloud.
An insider threat is a key aspect to monitor for in non-technical feeds, such as using performance reviews to continuously monitor intent.
Account hijacking and reusing compromised credentials are also a key area to monitor in order to identify signs of an account being misused.
Abuse Controls
An insider or an adversary will attempt to control an account / gain foothold to an identity through which they will attempt to abuse existing controls / configurations. With the ease of use and availability of cloud this acts as a double-edged sword and an attacker can easily take control over the entire cloud infrastructure and misuse services.
Consequence
The end result of this could include data loss (missing or deleted keys), data breach (publicly available objects), or lack of availability (misuse of cloud infrastructure), all of which can be detected.
In our next blog we will cover the essentials needed to generate the logging required, as well as mechanisms to detect some of these threats.







