- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
Securonix announced the expansion of its Threat Labs Alliance program with the addition of Picus Security, the pioneer in breach and attack simulation technology (BAS).
The Picus Complete Security Control Validation Platform simulates the behavior of emerging and advanced cyber threat actors, allowing enterprises to validate the effectiveness of their security controls and identify gaps to remediate before a real attacker can exploit them. By automating the simulation of attacks before they occur, organizations can continuously test their defenses against the latest up-to-date adversary intelligence with low risk and effort, enabling a proactive, threat-informed defense program.
By integrating the Picus platform with Securonix Next-Gen SIEM and XDR, users can finally benefit from automated end-to-end security control validation built directly into their security monitoring architecture to support continuous, repeatable, and measurable detection lifecycle management.
The Picus platform automates simulating the latest attacks and adversaries as soon as intelligence about new emerging threats or evolving existing threats becomes known. Securonix activity logs and policy violations are automatically reviewed to determine if an attack was blocked or detected by existing security controls, thus ensuring that the SIEM has sufficient visibility and is correctly configured for effective incident response and digital forensics. If a gap is identified, actionable guidance is provided, including which policy to enable or which SIGMA rule to add. This creates a closed feedback loop that continuously optimizes and adapts the organization’s security monitoring stance to meet the latest threat, ensuring defense readiness and increasing resilience.
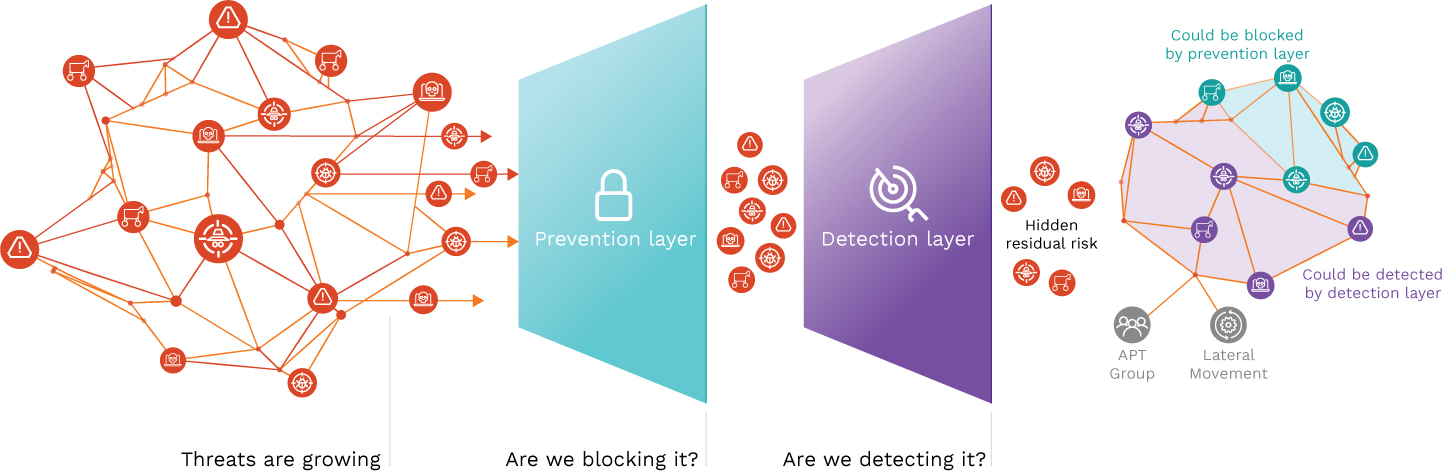
Users of Securonix and Picus Security can now benefit from being able to:
- Rapidly assess their level of readiness against current and emerging cyber threats before an attack occurs.
- Continuously evaluate the effectiveness of deployed preventative controls, such as endpoint protection platforms, web gateways, email gateways, firewalls, and intrusion detection and prevention systems.
- Ensure visibility into ongoing attacks and end-to-end coverage of logging and detection rules and policies for effective incident response and digital forensics.
- Immediately obtain actionable guidance on relevant policies and SIGMA rules to mitigate security control gaps.
- Measure and quantify cyber resilience against cyberattacks through comprehensive risk scoring, modeling against MITRE ATT&CK and adversary kill chains.
- Establish an agile detection-as-code CI/CD pipeline and automate detection development lifecycle management.
“Breach and attack simulation is one of the few genuinely proactive and scalable technologies you can deploy to test your defenses before you get hit by a known threat,” according to Nanda Santhana, Senior Vice President of Cybersecurity Solutions for Securonix. “Combined with our Next-Gen SIEM, this is a game-changer. It’s as close as we can get to prediction and allows us to answer the most critical question an organization can have: ‘Are we prepared if we were attacked by X?’”
“The rapidly evolving threat landscape makes it vital for organizations to optimize the protection they receive from their security controls at all times,” said Volkan Erturk, Chief Technology Officer and Co-founder at Picus Security. “By leveraging the Picus Platform, Securonix customers can ensure that their detection and response processes are continuously tuned to identify the very latest adversary behaviors. Seamless integration between the solutions ensures that simulating threats and mitigating visibility gaps is simple, swift, and hassle-free.
The partnership with Picus is another milestone in Securonix’s vision to develop the industry’s first truly modern cyber security operations mesh framework, based on modular and composable best-of-breed security capabilities, data-driven analytics, machine learning, and following DevSecOps methodologies.


