- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Information Security, SIEM
Suspicious activity on the endpoint is usually an indicator that a larger cybersecurity threat or attack is occurring. Your users are continually targeted by various attacks–phishing, malicious websites, session-based attacks and more—that end up playing out on the endpoints inside your organization.
While understanding anomalous behaviors on your endpoints is important, they must also be analyzed within the broader context of events, network activity, and peer-user behavior in order to have the best chance at identifying indicators of compromise (IoCs).
Securonix and Cylance have partnered to integrate Securonix Next-Gen SIEM, with its data collection, threat detection, investigation, and response capabilities—and combine it with the capabilities of CylancePROTECT—an artificial intelligence (AI)-based antivirus and endpoint protection solution.
Working together, Securonix uses the Cylance API to gather real-time attack intelligence from the endpoints across your organization, and leverages this intelligence for threat detection and investigation.
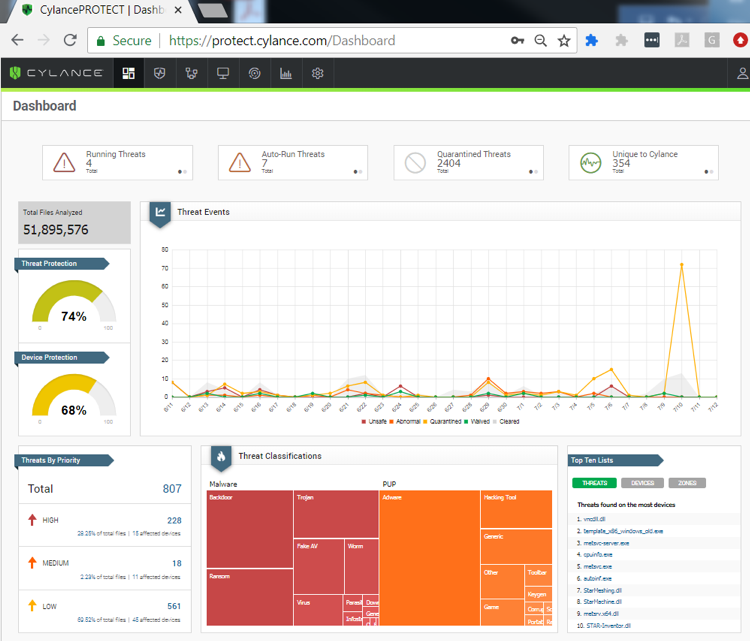
Figure 1: The CylancePROTECT dashboard gives an overall view of threats across the enterprise.
Securonix and Cylance Integration Benefits
Combining the capabilities of Securonix and Cylance provides security operations center (SOC) teams with a single-pane view of both cloud and endpoint security events along with the continuous protection and prevention capabilities they need to proactively detect and defeat virus, malware, ransomware, and other known and unknown (zero-day) threats.
The integrated solution is able to find and prevent known and unknown threats on the endpoint without any impact to the user and is also able to find complex cyberthreats that span the endpoint, network, and user spaces.
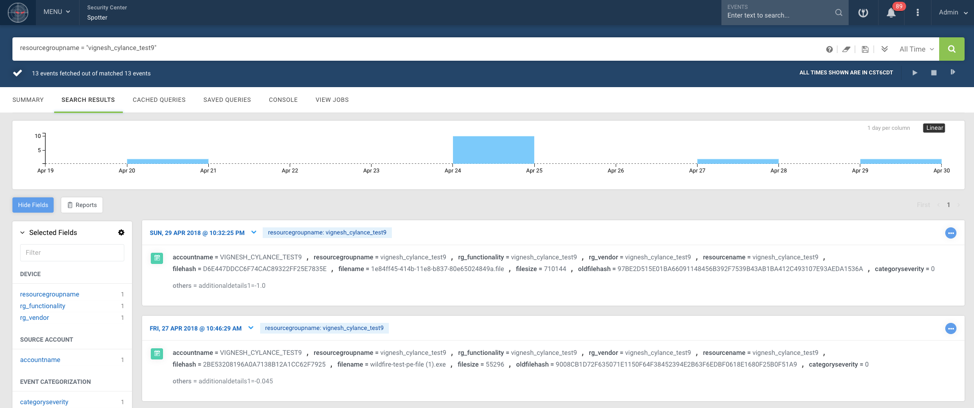
Figure 2: Securonix integrates and exposes CylancePROTECT intelligence for threat investigation.
How It Works
- CylancePROTECT prevents adversaries from gaining a foothold at the endpoint by detecting and blocking the execution of both file-based and fileless attacks, and by applying policies for device and script control, application control, and memory exploitation protection
- The Securonix Next-Gen SIEM uses RESTful APIs to ingest the security event data collected by CylancePROTECT at the endpoint – this includes not only information about suspect files, applications, scripts, and processes, but also event metadata, file attributes and more
- The Securonix Next-Gen SIEM aggregates and correlates this ingested data with user behavior analytics and network-based threat indicators, and applies sophisticated machine learning algorithms to accurately detect advanced and insider threats, ranking them based on risk scores; the Securonix Security Analytics Platform then generates prioritized alerts for threats that exceed a pre-defined risk threshold
- SOC personnel can visualize and interrogate the resulting threat-chain data within the Securonix management dashboard, drilling down and pivoting from one threat indicator to the next to trace and track the infection
- The security team is able to initiate response actions directly from the Securonix console, including manual threat mitigation and remediation actions, as well as through pre-defined incident response playbooks
Learn More About the Securonix and Cylance Integration
- Securonix – Cylance Integration – Partner Solution Brief
- Securonix and Cylance Connector Setup Video
- About Securonix Next-Gen SIEM
- About CylancePROTECT


