- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Dheeraj Kumar, Ella Dragun, Securonix Threat Labs
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in August. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. Each threat has a comprehensive threat summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below mentioned threats, refer to our Threat Labs home page.
In August 2023, Threat Labs analyzed and monitored major threat categories, including Rhysida a new ransomware-as-a-service (RaaS), phishing emails masquerading as Microsoft Teams chats, attackers using EvilProxy phishing kit andLazarus group activity.
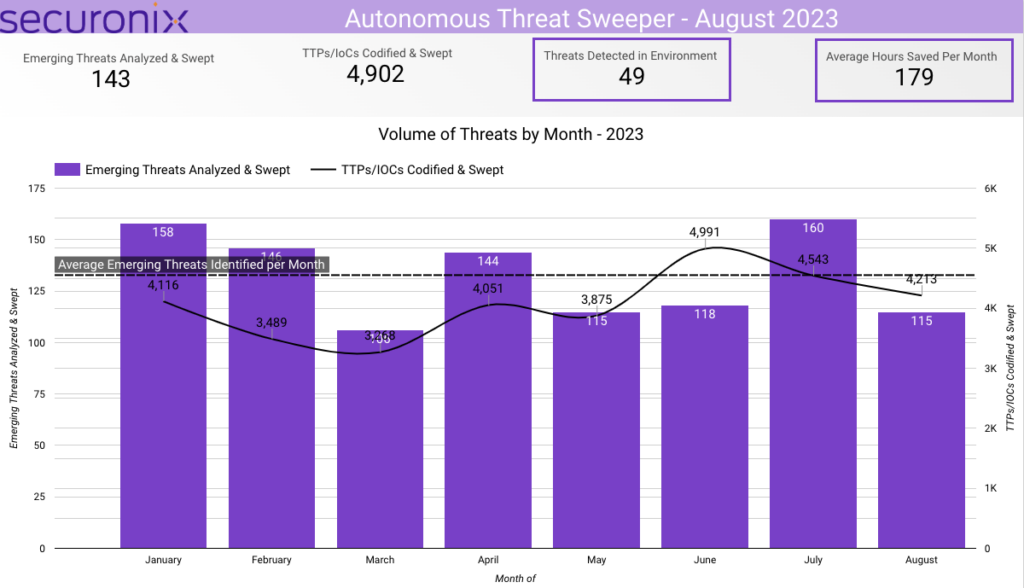
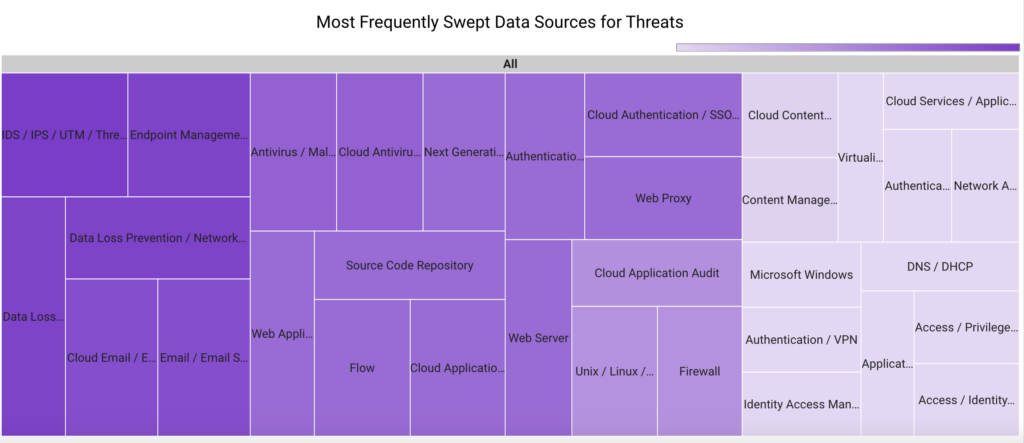
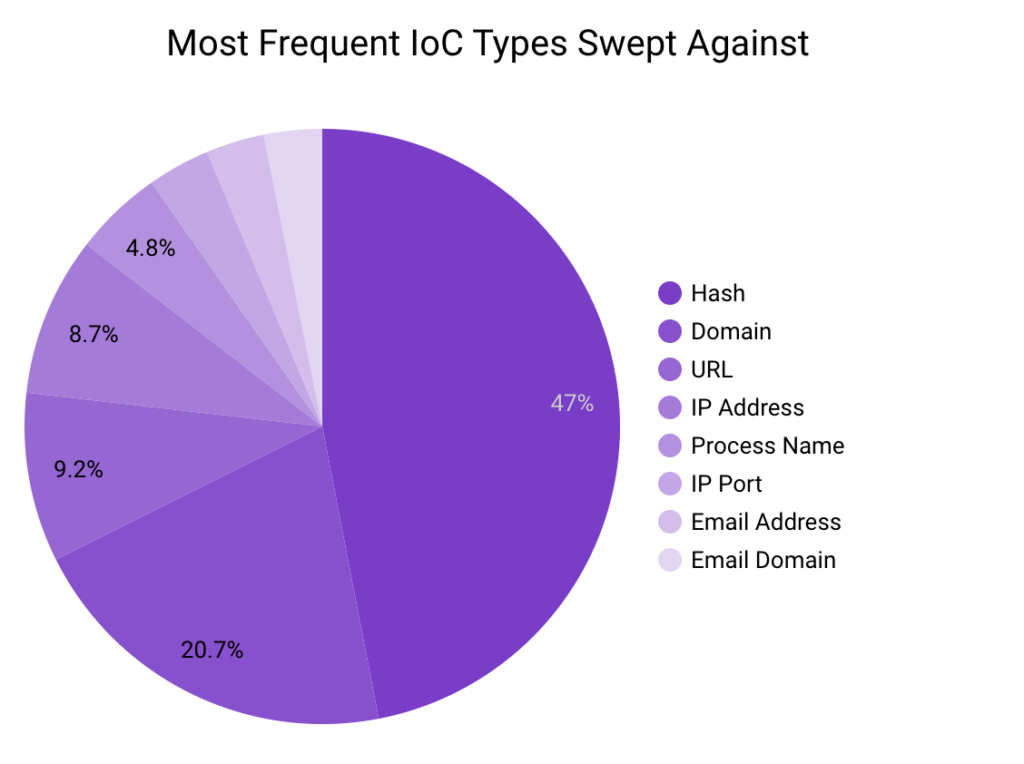
In August 2023, Securonix Autonomous Threat Sweeper identified 4,902 TTPs and IoCs, 143 distinct threats, and reported 49 threat detections. The top data sources swept against include IDS/IPS/UTM/Threat Detection, Endpoint Management Systems, Data Loss Prevention, and Email/Email Security.
Rhysida ransomware (Originally published in August 2023)
Rhysida is a new ransomware-as-a-service (RaaS) group that surfaced in May 2023. The gang employs phishing attacks and Cobalt Strike to access targets’ networks and distribute their payloads. If the ransom is not paid, the group threatens to publicly release the exfiltrated data. The absence of sophisticated features and the program name Rhysida-0.1 imply that Rhysida is still in its early phases of development. In addition, the ransomware leaves PDF documents in the infected files encouraging victims to contact the gang via their portal and pay in Bitcoin. Its victims are spread over a number of countries in Western Europe, North and South America, and Australia. They primarily target education, government, manufacturing, technology, and managed service providers; however, recent attacks have targeted the healthcare and public health sector.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures against increased threats from this ransomware.
- Rhysida is a MINGW/GCC-compiled 64-bit Portable Executable (PE) Windows cryptographic ransomware application.
- Rhysida employs a 4096-bit RSA key and the ChaCha20 algorithm for the encryption phase. Rhysida enumerates the files and folders connected to the system after the encryption details are determined. After encryption is complete, the main function calls PowerShell to remove the binary.
- To avoid encrypting specific files, Rhysida uses a file exclusion list. This check occurs in the isFileExcluded method, which compares the current file extension to exclude_extensions, an array containing the excluded file extensions listed below. This function sets two variables, exclude_i and exclude_c, to 0 and 11, respectively, and iterates through the array of 27 disallowed file extensions and the length of the current file name.
- 15 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Ransomware: Rhysida | Target Sector: Education, Government, Manufacturing, Technology, Healthcare and Public Health | Target Location: Western Europe, North and South America, Australia
Phishing emails masquerading as Microsoft Teams chats (Originally published in August 2023)
Microsoft claims that a hacking group known as APT29 and linked to Russia’s Foreign Intelligence Service attacked hundreds of organizations globally in phishing attempts on Microsoft Teams, including government bodies. This campaign has had an impact on almost 40 distinct global organizations. The organizations targeted in this action most likely show Midnight Blizzard’s specific espionage aims directed towards the government, non-governmental organizations (NGOs), IT services, technology, discrete manufacturing, and media sectors.
Threat actors used hacked Microsoft 365 tenants to build new technical assistance-themed domains and sent tech support lures, seeking to deceive users of the targeted organizations through social engineering. The goal was to trick users into completing multifactor authentication (MFA) prompts in order to steal their credentials.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against this campaign.
- The new domain is part of the ‘onmicrosoft.com’ domain, a legal Microsoft domain that Microsoft 365 uses as a fallback if a custom domain is not registered.
- Because the communications originated from the actual onmicrosoft.com domain, they may have given the bogus Microsoft support messages the appearance of legitimacy.
- 5 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers
Tags: Attack Type: Phishing | Threat Actor: APT29 | Target Sector: government, non-governmental organizations (NGOs), IT services, technology, discrete manufacturing, and media sectors
Attackers target executives with EvilProxy (Originally published in August 2023)
Attackers are increasingly carrying out account takeover attempts on senior executives at well-known organizations using the phishing-as-a-service (PhaaS) toolkit known as EvilProxy.
Researchers claim that between March and June 2023, a hybrid campaign that is still active used the service to target thousands of Microsoft 365 user accounts and send almost 120,000 phishing emails to several companies worldwide. Attackers initially pretended to be well-known, reputable services like Adobe, Concur and DocuSign. They sent phishing emails with links to fraudulent Microsoft 365 phishing websites using counterfeit email addresses.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from this campaign.
- Malicious URLs embedded in emails claiming to be from DocuSign, Adobe Sign, and Concur start a multi-step infection chain:
- The first step in redirecting user traffic is to use an open, trustworthy redirector (like youtube[.]com, bs.serving-sys[.]com, etc.).
- The user traffic may then travel through a few further redirection phases, including 404 redirects and harmful cookies. This reduces the likelihood of discovery by scattering the traffic in an unpredictable manner.
- Eventually, user traffic is sent to a phishing framework powered by EvilProxy. The landing page performs the role of a reverse proxy, imitating recipient branding and making an effort to manage third-party identity providers. If necessary, these sites may ask for MFA credentials to help the victim complete a true, successful authentication, thereby confirming the collected credentials.
- 86 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the EvilProxy include but are not limited to the following:
- Identify instances of phishing emails impersonating trusted services.
- Detect emails using techniques to evade security scanning bots.
- Identify patterns of user traffic involving malicious cookies and 404 redirects.
Tags: Attack Type: phishing-as-a-service (PhaaS) toolkit known as EvilProxy| Targeted Product: Microsoft 365 user accounts
Russian APT BlueCharlie campaign (Originally published in August 2023)
Researchers from Recorded Future have identified the latest campaign from BlueCharlie, a group that completely switched up its infrastructure, creating nearly 100 new domains from which to perform credential harvesting and follow-on espionage attacks.
BlueCharlie is a Russian threat group that is linked to groups that have been active the last couple years. BlueCharlie’s operations focused on espionage, but also used its methods for hack-and-leak operations. BlueCharlie’s target is individuals and organizations in North Atlantic Treaty Organization (NATO) nations, entities in Ukraine, and institutions like government, higher education, defense, and political sectors, non-governmental organizations (NGOs), activists, journalists, think tanks, and national laboratories.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from this campaign.
- Mitigating this threat requires a multi-faceted approach, including robust endpoint protection.
- Conduct employee awareness training on a regular basis.
- Secure configurations and incident response planning.
- Continual vigilance, proactive security measures, and staying informed about emerging threats are essential in safeguarding against BlueCharlie
- 186 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers
Tags: Campaign: BlueCharlie campaign | Target: individuals and organizations in NATO nations, entities in Ukraine, government agencies, higher education, defense, and political sectors,NGOs, activists, journalists, think tanks, and national laboratories | Attack Type: hack-and-leak operations
Lazarus Group Activity (Originally published in August 2023)
The Lazarus Group, a threat actor with ties to North Korea, has been seen disseminating the QuiteRAT remote access trojan against healthcare organizations in Europe and the United States by taking advantage of a now-patched critical security vulnerability affecting Zoho ManageEngine ServiceDesk Plus.
A new threat known as CollectionRAT has been found after a deeper look at the adversary’s recycling attack infrastructure employed in its cyberattacks on businesses.
While CollectionRAT and EarlyRAT (also known as Jupiter), an implant with the ability to execute instructions on the endpoint and written in PureBasic, appear to have some similarities. QuiteRAT claimed to be a follow-up to MagicRAT, which was in turn a follow-up to TigerRAT.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these campaigns.
- This is the third known effort of this actor in less than a year, and they have all used the same infrastructure.
- While MagicRAT is a larger, bulkier malware family with an average size of roughly 18 MB, QuiteRAT is a much smaller, lighter implementation, with an average size of only 4 to 5 MB.
- The increased use of the Qt framework by Lazarus Group presents difficulties for defense. Compared to threats developed using threats made using simpler programming languages like C/C++, DOT NET, etc., Qt framework makes it more challenging for human analysis.
- The DeimosC2 framework used by Lazarus Group is open-source. The fact that the DeimosC2 agent found in this campaign is an ELF binary suggests that Lazarus intended to use this implant when gaining initial access to infected Linux endpoints.
- 15 IoCs are available on our Threat Labs home page and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Lazarus group include but are not limited to the following:
- Monitor to detect cyber threat indicators associated with a specific attack scenario, encompassing vulnerability exploitation (CVE-2022-47966), Command and Control (C2) communications involving a particular URL, reconnaissance activities through commands like ‘systeminfo’ and ‘ipconfig’, the execution of a designated malware (‘QuiteRAT’) from a malevolent URL, and the establishment of persistence by executing specific commands.
Tags: Target Sector: Internet Backbone Infrastructure, Healthcare Entities | Target Geo-Location: Europe, U.S. | Malware: QuiteRAT, CollectionRAT | APT Group: Lazarus Group | Threat Actor Location: North Korea
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at scia@securonix.com.
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Sina Chehreghani, Dhanaraj K R