- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
- MSSPs
- Scale multi-tenant security with predictable economics.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, and Sina Chehreghani
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in August 2025. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. Each threat has a comprehensive summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below-mentioned threats, refer to our Threat Labs home page.
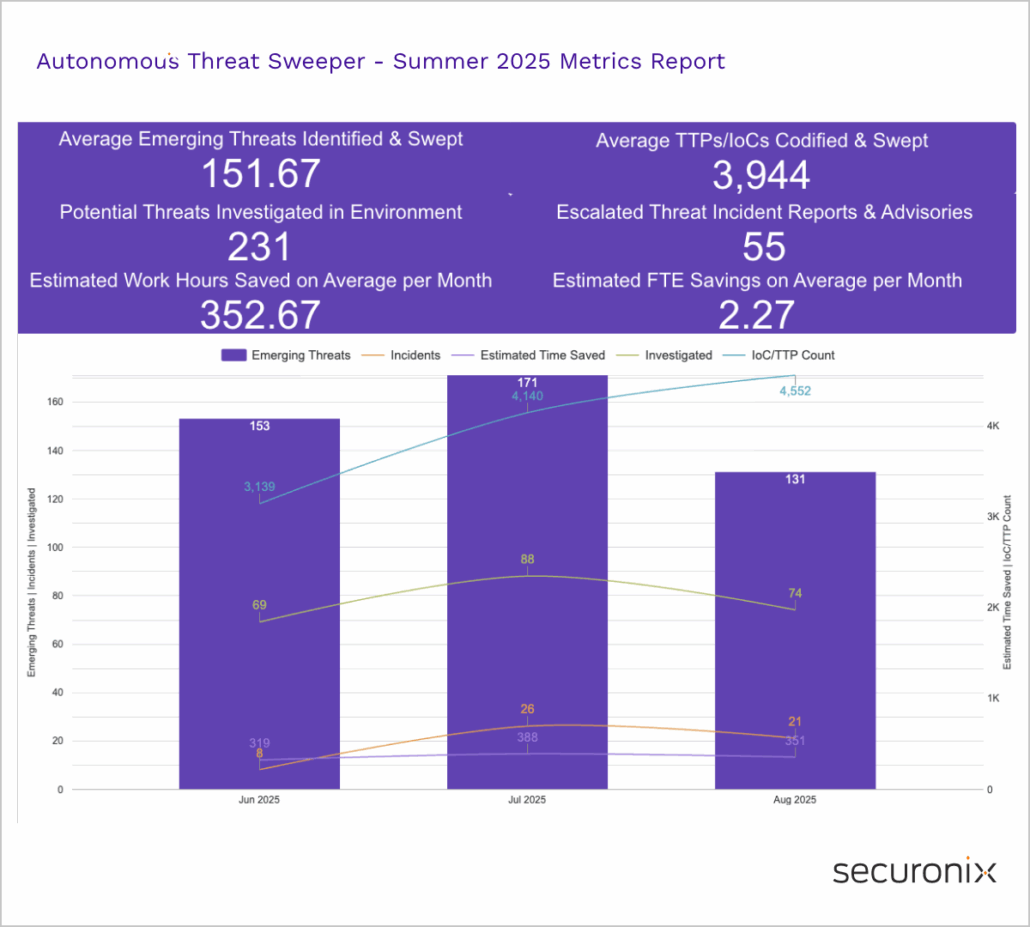
Last month Securonix Autonomous Threat Sweeper identified and analyzed 4,552 TTPs and IoCs, 131 emerging threats, investigated 74 potential threats, and elevated 21 threat incidents. The top data sources swept against include IDS / IPS / UTM / Threat Detection, Data Loss Prevention, Endpoint Management Systems, and Email / Email Security.
In August 2025, the Autonomous Threat Sweeper team observed a threat landscape marked by precision intrusions, evolving backdoors, and a steady drumbeat of ransomware operations. State-aligned activity persisted: APT37 operationalized RokRAT malware, while APT36 intensified tasking against India—specifically targeting BOSS Linux systems and broadening operations against critical Indian entities. Backdoor and loader activity expanded in both capability and tradecraft, with CORNFLAKE.V3 surfacing in coordinated campaigns, a Linux backdoor leveraging PAM hooking for stealthy persistence, the rapid evolution of the PipeMagic backdoor family, and the emergence of PS1Bot as a multi-stage, modular malware framework. Ransomware actors continued to diversify their playbooks: PromptLock appeared as an AI-driven proof-of-concept leveraging Lua scripts, while Blue Locker, BQTLock (a double-extortion RaaS focusing on Windows environments), MedusaLocker deployments, LeeMe, and Charon collectively underscored the breadth of criminal monetization. Exploitation activity remained active, including RomCom’s operational use of a WinRAR vulnerability and the AK47 campaign targeting Microsoft SharePoint deployments. Long-running espionage also featured prominently, with the Static Tundra campaign sustaining multi-phase collection over extended periods, and a PRC-aligned router-level global effort highlighting the strategic value of edge-device footholds. These developments reinforce the imperative for accelerated patch cycles (especially for client-side and collaboration platforms), rigorous Linux and identity-stack hardening, continuous phishing and malware-delivery awareness, and layered detection/response programs capable of surfacing stealthy backdoors and ransomware precursors before impact.
Malvertising & Backdoor Trends
(Originally published in August 2025)
| PS1Bot Multi Stage Modular Malware Framework | A widespread 2025 malvertising and SEO poisoning campaign has been observed delivering a multi-stage PowerShell and C#-based framework known as PS1Bot. The attack begins when a victim opens a malicious archive file, typically named something like “FULL DOCUMENT.js.” This triggers a JScript or VBScript loader that drops a looping PowerShell beacon. The beacon constructs a command-and-control (C2) URL using the victim’s C:\ drive serial number and executes additional modules entirely in memory. These modules include antivirus enumeration using WMI, screenshot capture, runtime-compiled keylogging via Add-Type, and a credential grabber targeting numerous Chromium-based browsers and cryptocurrency wallet extensions. The framework also performs domain reconnaissance and establishes persistence by placing a randomized PowerShell script and shortcut (LNK) file under both %ProgramData% and the Startup folder. |
| PipeMagic Backdoor | The PipeMagic backdoor has evolved significantly since its use in a 2022 RansomExx intrusion and is now associated with exploitation of CVE-2025-29824. Recent attack chains involve multiple loaders, including a .mshi Help Index file that uses EnumDeviceMonitor to RC4-decrypt shellcode, a deceptive Rust/Tauri-based “ChatGPT” application, and a googleupdate.dll DLL hijack that AES-CBC decrypts its payload. The 32-bit backdoor creates a named pipe (e.g., \\.\pipe\magic3301) and proxies traffic through 127.0.0.1:8082, then retrieves various plugins such as an asynchronous I/O file handler, a loader expecting an exported DllRegisterService, and a .NET-based injector that disables AMSI by patching AmsiScanString and AmsiScanBuffer. Post-exploitation activity includes LSASS dumping using a renamed version of ProcDump (dllhost.exe), aligning with known techniques used in CVE-2025-29824 exploitation. The attack infrastructure has been observed hosted on Azure, highlighting the adversary’s operational sophistication. |
| PAM Hooking Backdoor on Linux | Researchers have analyzed Linux credential-theft backdoors that abuse the Pluggable Authentication Module (PAM) system. One category involves malicious PAM modules that intercept credentials within pam_sm_authenticate() and either exfiltrate them to a command-and-control (C2) server or store them locally in paths like /tmp/sshlog. These modules are typically detected when registered with the PAM stack. Another category involves the “Plague” LD_PRELOAD technique, which hijacks pam_authenticate() to log credentials to hidden file paths such as /var/log/.-utmpx. This variant also accepts a hardcoded backdoor password (“changeme”), disables shell history logging, and conceals its presence by hiding artifacts like ld.so.preload and masqueraded libraries. Detection signatures include modifications to /etc/ld.so.preload and the presence of preloaded libraries within the sshd process. |
| CORNFLAKE.V3 Backdoor | The CORNFLAKE.V3 backdoor has been observed being delivered through fake CAPTCHA lures crafted to trick users into copying and executing a malicious PowerShell one-liner. This dropper downloads Node.js to the %AppData% directory and launches an unobfuscated Node.js-based backdoor that gathers host information, establishes persistence via the HKCU\…\Run\ChromeUpdater registry key, and retrieves payloads over HTTP using a simple XOR obfuscation method. Supported payload types include EXE, DLL, JS, and CMD files. Post-compromise activity has included Active Directory reconnaissance and Kerberoasting, with at least one case involving delivery of a WINDYTWIST.SEA DLL backdoor. A more recent PHP-based variant of the threat achieves persistence using a randomized Run key, leverages Cloudflare Tunnels for command-and-control, and continues to utilize Node.js by downloading it on demand. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these malicious campaigns.
- Add an EDR rule to alert/block when wscript.exe/cscript.exe drops a PowerShell script under %ProgramData% and PowerShell then beacons via Invoke-Expression (IEX) with dynamically delivered content—especially when it compiles C# at runtime via Add-Type (screenshot module writing %APPDATA%\Screenshot.jpg). This directly targets the JS/VBS > PS1 chain and in-memory module loading observed in this campaign.
- Monitor and block credential theft by detecting LSASS memory dumps from ProcDump—particularly when the binary is renamed to dllhost.exe—and treat any such event as high severity for rapid containment.
- Continuously watch for registration of new PAM modules and any modification/use of LD_PRELOAD (writes to /etc/ld.so.preload or PRELOADed libraries in sshd) and alert immediately; these are the core behaviors enabling credential capture and backdoor logins.
- Detect unauthorized runtime installs in user profiles and persistence via HKCU\…\Run—flag Node.js or PHP dropped into %APPDATA%/%LOCALAPPDATA% with Run keys such as ChromeUpdater or randomized names, which map to the Node.js and newer PHP variants used by this backdoor.
- 144 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers
TTPs related to the PS1Bot Multi Stage Modular Malware Framework include but are not limited to the following:
- Monitor for downloads of compressed archives from search ads/SEO-poisoned sites with lure-y names (“manual.zip”, “worksheet.zip”) and odd extra suffixes (“.zip.e49”, “.zip.081”).
- Monitor for archives that contain a single JavaScript file named “FULL DOCUMENT.js” that embeds VBScript or heavily obfuscated code.
- Monitor for wscript.exe/cscript.exe launching a scriptlet that immediately writes a PowerShell script into C:\ProgramData\ (ntu.ps1) and executes it.
- Monitor for PowerShell using Invoke-Expression (IEX) on content fetched over HTTP(S), especially in a loop with periodic Start-Sleep delays (beacon/polling pattern).
- Monitor for PowerShell dynamically compiling C# via Add-Type (namespaces like System.Drawing, System.Windows.Forms, System.Runtime.InteropServices) to capture screenshots or hook input.
- Monitor for creation of %TEMP%*.bmp followed by %APPDATA%\Screenshot.jpg, immediate deletion of those files, and a subsequent HTTP POST of Base64 image data.
- Monitor for reconnaissance WMI queries of domain membership (Win32_ComputerSystem and Win32_NTDomain) and reads of %USERDNSDOMAIN% by PowerShell.
TTPs related to the PipeMagic Backdoor include but are not limited to the following:
- Monitor for msbuild.exe spawning with a .mshi Microsoft Help Index file and long hex-blob arguments indicative of an obfuscated C# loader.
- Monitor for unsigned “ChatGPT” themed binaries (e.g., chatgpt.exe) built with Tauri/Tokio that show a blank window, then quickly allocate RWX memory and run shellcode.
- Monitor for processes calling EnumDeviceMonitor to execute a pointer/callback shortly after decrypting a payload—anomalous for typical GUI apps.
- Monitor for named pipes matching PipeMagic patterns, including: \\.\pipe\1.<16-byte hex>, \\.\pipe\magic3301, \\.\pipe\test_pipe20.<PID>, and \\.\pipe\0104201.<PID>
- Monitor for loopback communications to 127.0.0.1:8082 tied temporally to pipe activity.
TTPs related to the PAM Hooking Backdoor on Linux include but are not limited to the following:
- Monitor for the registration of new or suspicious PAM modules on Linux servers.
- Monitor for executions of the pam_sm_authenticate() function writing credentials to unusual paths such as /tmp/sshlog.
- Monitor for modifications to /etc/ld.so.preload, which may indicate LD_PRELOAD abuse.
- Monitor for libraries being loaded via the PRELOAD method into critical processes like sshd.
- Monitor for credential logs or hidden files created in suspicious locations (/var/log/.-utmpx).
- Monitor for hidden or concealed files with suspicious names (.-utmpx, ld.so.preload, libselinux.so.8).
TTPs related to the CORNFLAKE.V3 Backdoor include but are not limited to the following:
- Monitor for execution of node.exe or php.exe from user AppData directories with suspicious arguments (-e for JavaScript execution or -d for PHP covert execution).
- Monitor for persistence creation via registry Run keys (HKCU\Software\Microsoft\Windows\CurrentVersion\Run\ChromeUpdater or random AppData directory names).
- Monitor for file creation in AppData with non-standard extensions (.png or .jpg masquerading DLLs/JS payloads).
Tags: Malware family: PS1Bot (PowerShell/C# modular framework), PipeMagic backdoor (32-bit Windows), Plague (LD_PRELOAD hook) and malicious PAM modules, CORNFLAKE.V3 (Node.js or PHP backdoor; HTTP C2; Run-key persistence) | Target systems: Windows endpoints. (PowerShell/WMI/WinAPI usage such as SetWindowsHookEx.), Target systems: Windows (32-bit), Target systems: Linux (PAM/sshd), Windows endpoints (%APPDATA%\node.exe, HKCU Run key)
Nation State APT’s Campaigns
(Originally published in August 2025)
| APT 36 Linux BOSS Malware Campaign | APT36, also known as Transparent Tribe, is a Pakistan-linked threat actor that has been active for over a decade, primarily conducting cyber-espionage campaigns against Indian government, military, and diplomatic entities. In its latest operations, the group has expanded its focus to include critical Indian sectors such as Indian Railways, the oil and gas industry, and the Ministry of External Affairs.
These campaigns rely heavily on spear-phishing emails that deliver malicious archive files disguised as official government notices or documents, including lures such as National Anubhav Scheme-2025.pdf. These archives contain weaponized .desktop shortcut files designed to compromise Linux BOSS systems. When executed, the files trigger hidden commands that silently download a payload from attacker-controlled servers, convert it into an executable, and run it in the background. To avoid suspicion, the malware simultaneously launches a decoy PDF in Firefox, tricking victims into believing they have opened a legitimate document. The infection chain enables deployment of the Poseidon backdoor, a Mythic C2 framework implant written in Go, which provides persistent access, supports credential theft, and facilitates lateral movement within networks. Persistence is achieved through techniques such as configuring automatic execution on system restart or setting up cron jobs. Researchers have identified two main infection strategies: one relying on a single C2 server with obscured file paths, and another using two redundant C2 servers for resilience. More than 100 phishing domains, many impersonating Indian government organizations and hosted by AlexHost, have been linked to this activity. |
| Pakistan Aligned Campaign Against Indian Organizations | |
| APT37 Linked ROKRAT Malware Campaign | A new Campaign attributed to the North Korea–linked group APT37 employs malicious .lnk shortcut files masquerading as legitimate documents and delivered through compressed archives. These shortcuts execute PowerShell and batch commands to deploy RokRAT malware. The observed archive, titled “National Intelligence and Counterintelligence Manuscript.zip”, contained an unusually large shortcut file embedding shellcode and multiple loaders. APT37 continues to leverage DLL side-loading to deliver the payload and uses steganography to conceal the RokRAT module inside JPEG images. Once installed, it collects basic system information, documents, and screenshots from compromised machines, exfiltrating them via legitimate cloud services such as pCloud, Yandex Disk and Dropbox. These findings highlight APT37’s persistent evolution, combining shortcut delivery, side-loading, and steganography to sustain operations in South Korea. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these APT group’s campaigns.
- Deploy advanced email security solutions capable of blocking uncommon or high-risk file types within email attachments.
- Implement sandbox-based detonation to analyze and evaluate suspicious attachments before they are delivered to end users.
- Enforce the principle of least privilege, particularly across Linux environments, to minimize the impact of potential compromises.
- Continuously monitor outbound communications to cloud storage services such as Dropbox and Yandex for potential data exfiltration attempts.
- Enable URL filtering controls to restrict access to newly registered, unclassified, or suspicious domains.
- Ensure timely patching of BOSS Linux systems as well as other commonly exploited utilities to reduce the attack surface.
- 64 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Linux Boss campaign include but are not limited to the following:
- Monitor for Meeting_Ltr_ID1543ops.pdf.desktop and Meeting_Ltr_ID1543ops.pdf-.elf files.
- Monitor for Mt_dated_29.txt file which is malicious payload.
- Monitor for system-update.service and config/systemd/systemd-update.
TTPs related to the Pakistan Aligned Campaign include but are not limited to the following:
- Monitor for directories ~/.local/share/ and /dev/shm/ as they are commonly abused by threat actors to store malicious payloads.
- Monitor for p7zip-full, tcl-8.7, emacs-bin, and crond-98 files, indicating as Malicious.
- Monitor for /dev/shm/myc.txt, used for temp files such as downloading the payloads, setting up cron jobs for persistence, and cleaning up traces.
- Monitor for the .desktop files masquerading as National Anubhav Scheme-2025.pdf.
TTPs related to the RokRAT Campaign include but are not limited to the following:
- Monitor for National Intelligence and Counterintelligence Manuscript.lnk and Academy Operation for Successful Resettlement of North Korean Defectors in South Korea.lnk file in .zip / .rar attachments or download from instant messaging platforms such as SNS.
- Monitor for D:\Work\Weapon\InjectShellcode\Release\InjectShellcode.pdb – Weapon folder under which is used for developing the malware.
- Monitor for mspaint.exe, notepad.exe files under C:\Windows\SysWOW64.
- Monitor for [.]dat files (ttf01, ttf02, ttf03) which triggers a sequence of PowerShell commands.
- Monitor for ShellRunas.exe, AccessEnum.exe, Hhc.exe which loads malicious DLL credui.dll, mpr.dll, hha.dll.
- Monitor for Father.jpg file which downloads from Dropbox.
Tags: Threat Actor: APT36 (Transparent Tribe), APT37 | Target Sector: Military, Diplomatic, Oil & Gas, Railways and (Ministry of ExternalAffairs) | Target Location: India | Target Systems: Boss Linux and Windows.
Ransomware Surge: AI, APT Tactics, and Targeting
(Originally published in August 2025)
| Charon Ransomware | A newly identified ransomware family, “Charon,” has been observed in targeted attacks against the Middle East’s public sector and aviation industries. The campaign demonstrates APT-like tradecraft, leveraging DLL sideloading through a renamed Edge browser binary to load a malicious msedge.dll (codenamed SWORDLDR), which decrypts and executes the Charon payload. While attribution remains unconfirmed, toolset overlap suggests possible links to known threat activity resembling Earth Baxia campaigns. Charon employs Curve25519 for key exchange and a modified ChaCha20 cipher, favoring partial encryption to increase speed. It appends “.Charon” to affected files, drops victim-tailored ransom notes, and encrypts network shares. |
| LeeMe Ransomware | A separate phishing campaign masquerading as an SAP Ariba Quote Builder is delivering the LeeMe ransomware via password-protected ZIP archives hosted on cloud-sharing platforms—a tactic aimed at sandbox evasion. The archive contains a fake SAP-themed installer and guides victims to disable Windows Defender, allowing the ransomware to silently encrypt files using AES-256. Beyond encryption, LeeMe includes a pynput-based keylogger and scans documents for sensitive keywords, exfiltrating results via cloud storage or Telegram. |
| MedusaLocker Ransomware | A new malware strain functions as an AV-disabler, exploiting a vulnerable driver from an overclocking utility to escalate privileges to kernel mode. The malware abuses Windows Service Control Manager APIs to load the driver, identifies kernel base addresses via NtQuerySystemInformation, and leverages NtAddAtom for arbitrary kernel code execution. It disables major endpoint protection tools by enumerating and terminating their processes, effectively clearing the environment for follow-on payloads. |
| BQTLock Ransomware | Another campaign highlights the BQTLOCK ransomware, a RaaS (Ransomware-as-a-Service) offering distributed in a ZIP archive containing Update.exe. Once executed, it encrypts files (hybrid AES-256 + RSA-4096), appends “.bqtlock”, and deploys a ransom note. BQTLOCK supports double extortion, implements anti-analysis checks (debugger, VM), privilege escalation, and process hollowing. It sets persistence via a scheduled task named Microsoft\Windows\Maintenance\SystemHealthCheck and exfiltrates data using a Discord webhook. Recent variants show added obfuscation, UAC bypasses, and browser credential theft. Demands are made in Monero with time-based escalation. |
| Blue Locker Ransomware | In another case, Blue Locker ransomware has been deployed against entities in Pakistan’s oil and gas sector, including national companies, coinciding with national holidays—raising suspicion of a nation-state disguise under cybercriminal pretense. Delivered via PowerShell-based loaders, the malware appends “.blue” or “.bulock16”, drops a ransom note (HOW_TO_BACK_FILES.html), and uses threats of data leaks for pressure. Initial access vectors include phishing, drive-by downloads, and exploitation of exposed remote services. National cyber authorities have alerted multiple ministries, suspecting a connection to Conti-like tooling, though exact attribution remains unclear. |
| PromptLock AI driven ransomware | A novel ransomware variant named PromptLock has emerged, believed to be the first AI-assisted ransomware. Written in Go for cross-platform deployment on Windows and Linux, it integrates a local instance of a large language model (gpt-oss-20b via Ollama) to dynamically generate Lua scripts for system discovery, exfiltration, and encryption tasks. Though likely a proof-of-concept, PromptLock demonstrates the feasibility of LLM-powered ransomware that can autonomously adapt tactics and accelerate operations—signaling the near-term risks of AI-integrated attack automation. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these ransomware groups.
- Add an EDR rule to flag or block Edge.exe (renamed from cookie_exporter.exe) sideloading a non-Microsoft msedge.dll from user-writable or nonstandard paths (DLL search-order abuse used to launch Charon).
- Block and alert on links to anonymous file-sharing (GoFile) that deliver password-protected ZIPs in email/web gateways; this directly disrupts the delivery method and the sandbox-evasion trick.
- Enforce the Windows vulnerable-driver blocklist and monitor/deny loads of ThrottleStop.sys/ThrottleBlood.sys via SCM; treat any load attempt as high-severity.
- Create a detection to alert when a local user named BQTLockAdmin is created and added to Administrators, and auto-quarantine the host—this maps to BQTLOCK’s persistence/privilege-escalation step.
- Constrain and audit PowerShell (Constrained Language Mode + block unsigned scripts) on high-value systems, since Blue Locker is distributed via a PowerShell-based loader.
- Inventory, restrict, and alert on local LLM runtimes (Ollama) and unexpected Lua-script generation/execution by Go binaries, matching PromptLock’s technique of using Ollama to generate on-the-fly Lua for discovery/exfil/encryption.
- 49 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Charon Ransomware group include but are not limited to the following:
- Monitor for creation or access of unusual files like DumpStack.log containing encrypted shellcode.
- Monitor for creation of a mutex named OopsCharonHere as a persistence marker.
- Monitor for enumeration and encryption of network shares using APIs such as NetShareEnum and WNetEnumResource, skipping ADMIN$ shares.
- Monitor for files being renamed with the .Charon extension and insertion of the infection marker text “hCharon is enter to the urworld!”.
- Monitor for ransom note creation (How To Restore Your Files.txt) across drives, directories, and network shares.
TTPs related to the LeeMe Ransomware include but are not limited to the following:
- Monitor for users clicking gofile[.]io links and downloading/extracting password-protected archives named like SAP_Ariba_QuoteBuilder_v2.zip.
- Monitor for execution of SAP_Ariba_QuoteBuilder_v2.exe from user writeable paths (Downloads/Desktop/Temp).
- Monitor for a fake “installer” GUI (SAP/Ariba-branded window) spawning while a background process performs heavy file I/O.
TTPs related to the MedusaLocker Ransomware include but are not limited to the following:
- Monitor for creation of the device object \\.\\ThrottleStop, which enables user-mode to kernel-mode communication.
- Monitor for unusual IOCTL calls to ThrottleStop.sys (read/write primitives) using DeviceIoControl, which may indicate exploitation attempts.
- Monitor for use of NtQuerySystemInformation with SystemModuleInformation or SystemSuperfetchInformation flags to enumerate kernel modules and memory ranges.
- Monitor for suspicious kernel memory read/write operations leveraging MmMapIoSpace mappings.
- Monitor for repeated calls to Process32FirstW() and Process32NextW() followed by attempts to terminate security-related processes (MsMpEng.exe, AvastSvc.exe, CSFalconService.exe, etc.).
- Monitor for lateral movement using pass-the-hash techniques with Invoke-WMIExec.ps1 or Invoke-SMBExec.ps1
- Monitor for ransomware execution attempts (MedusaLocker variants like haz8.exe) following AV termination.
TTPs related to the BQTLock Ransomware include but are not limited to the following:
- Monitor for execution of suspicious files such as Update.exe within ZIP archives.
- Monitor for file modifications appending unusual extensions like .bqtlock.
- Monitor for privilege escalation attempts via APIs like SeDebugPrivilege, OpenProcessToken, and AdjustTokenPrivileges.
- Monitor for process hollowing attempts targeting legitimate processes such as explorer.exe.
- Monitor for creation of unauthorized local administrator accounts (BQTLockAdmin with default passwords).
- Monitor for persistence mechanisms such as scheduled tasks named Microsoft\Windows\Maintenance\SystemHealthCheck.
- Monitor for use of anti-debugging and anti-VM APIs like IsDebuggerPresent() and CheckRemoteDebuggerPresent().
- Monitor for creation of screenshots saved in unusual paths (e.g., C:\Windows\Temp\bqt_screenshot.png).
- Monitor for termination of security or backup-related processes using APIs like CreateToolhelp32Snapshot and TerminateProcess.
- Monitor for registry modifications altering file icons and desktop wallpaper (setting bqt_wallpaper.bmp as background).
TTPs related to the Blue Locker Ransomware include but are not limited to the following:
- Monitor for mass file encryption activity, especially with appended .Blue or .bulock16 extensions.
- Monitor for ransom note creation (restore_file.txt or HOW_TO_BACK_FILES.html) across multiple directories.
TTPs related to the PromptLock AI driven ransomware include but are not limited to the following:
- Monitor for execution of Lua scripts generated dynamically by local AI models (via Ollama API).
- Monitor for execution of binaries or scripts associated with known PromptLock IoCs (file hashes, detection names such as Linux/Filecoder.PromptLock.A and WinGo/Filecoder.PromptLock.A).
Tags: Ransomware: Charon, LeeMe, MedusaLocker, BQTLOCK, Blue Locker, PromptLock | Target sector: Public sector, Aviation, Broad/widespread, Oil & Gas | Target location: Middle East, Pakistan | Target systems: Windows hosts, End-user Windows machines (Windows EXE; advice to disable Windows real-time protection), Windows endpoints/servers (kernel-mode driver), Primarily Windows (EXE/DLL payloads), Windows workstations/servers
Infrastructure Targeting by State-Sponsored Actors
(Originally published in August 2025)
Two distinct state-sponsored campaigns were observed this month, both targeting network infrastructure across various global sectors.
Chinese State-Sponsored Campaign
A long-running global intelligence-gathering operation is compromising backbone and edge routers, as well as other network appliances, in sectors including telecommunications, government, transportation, hospitality, and defense. The actors rely on known internet-facing vulnerabilities—no zero-days identified—with frequent exploitation of:
- Ivanti CVE-2024-21887 (often chained with CVE-2023-46805)
- PAN-OS CVE-2024-3400
- Cisco IOS XE CVEs 2023-20198, 2023-20273, and 2018-0171
Post-exploitation activity includes modifying access control lists (ACLs), enabling SSH/HTTP(S) on non-standard ports, and misusing built-in features such as Cisco Guest Shell containers. For credential harvesting and lateral movement, the actors target TACACS+/RADIUS infrastructure, deploy native packet capture tools (mycap, tac.pcap), redirect traffic using SPAN/ERSPAN, and exfiltrate data through multi-hop proxy chains and GRE/IPsec tunnels.
Russian State-Sponsored Activity (“Static Tundra”)
A decade-long espionage effort attributed to a Russian threat cluster is targeting unpatched or end-of-life Cisco infrastructure within telecom, higher education, and manufacturing sectors across multiple regions. The group heavily exploits CVE-2018-0171 (Cisco Smart Install) to launch TFTP servers and extract startup configurations. They further exploit weak/default SNMP community strings for configuration changes and command execution. Persistence is maintained using the historic SYNful Knock firmware implant, while stealth is achieved through modifications to TACACS+ and ACLs. Data is exfiltrated using GRE redirection and NetFlow abuse. Organizations are strongly advised to patch or disable Smart Install, eliminate Telnet access, enforce strong credential types (Type 8 for local passwords, Type 6 for TACACS+ keys), monitor AAA activity, and replace unsupported hardware.
These campaigns highlight the critical importance of rigorous network device hygiene, proactive configuration auditing, and strong segmentation of management interfaces.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these malicious campaigns.
- Patch edge devices by risk order, prioritizing the CVEs explicitly called out (Ivanti CVE-2024-21887 often with CVE-2023-46805; PAN-OS CVE-2024-3400; Cisco IOS XE CVE-2023-20198/CVE-2023-20273; Cisco Smart Install CVE-2018-0171); if cannot, disable Smart Install (no vstack).
- Verify image hashes and integrity; alert on on-box PCAP/SPAN creation and track common PCAP naming patterns (mycap.pcap, tac.pcap).
- Use strong credential storage: Type 8 for local account passwords; Type 6 for TACACS+ keys.
- Encrypt and restrict management planes: prefer SNMPv3/HTTPS/SSH/NETCONF/RESTCONF; prevent/monitor exposure of admin interfaces; verify ACLs protecting management protocols.
- Use complex passwords and SNMP community strings (no defaults); enable MFA; aggressively monitor TACACS+ and jump hosts; use AAA to prevent unauthorized config changes.
- 10 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Chinese State-Sponsored Campaign include but are not limited to the following:
- Monitor for creation of unauthorized local accounts or privilege escalations, including edits to /etc/sudoers or unexpected sudo access on IOS XR host Linux.
- Monitor for suspicious PCAP capture activity (monitor capture mycap, output files like tac.pcap or mycap.pcap) and SPAN/RSPAN/ERSPAN sessions targeting TACACS+ (TCP/49).
- Monitor for use of Guest Shell containers (commands like guestshell enable, run guestshell, chvrf, dohost) or installation of malicious Tcl/Python scripts (TCLproxy.tcl, map.tcl, siet.py).
- Monitor for custom SFTP client usage (cmd1, cmd3, new2, sft) transferring encrypted archives or packet captures.
- Monitor for unauthorized SNMP activity, including SNMPwalk enumeration, SNMP SET requests altering configs, or use of weak community strings (“public”, “private”).
TTPs related to the Russian State-Sponsored Activity (“Static Tundra”) include but are not limited to the following:
- Monitor for unauthorized enabling of TFTP servers (tftp-server nvram:startup-config) and subsequent retrieval of startup configurations.
- Monitor for use of “show” commands (show cdp neighbors) to discover additional systems without active scanning.
Tags: Threat actor: PRC state-sponsored APT cluster; overlaps with Salt Typhoon / OPERATOR PANDA / RedMike / UNC5807 / GhostEmperor, Static Tundra—Russian state-sponsored espionage cluster; likely sub-cluster of Energetic Bear linked to FSB Center 16 | Target sector: Telecommunications (backbone/PE/CE routers), government, transportation, lodging, military, higher education, manufacturing | Target location: Global; observed in the U.S, Australia, Canada, New Zealand, U.K, and elsewhere. Also, North America, Asia, Africa, Europe; focus on Ukraine and allied countries | Malware: Custom Golang SFTP exfiltration clients (cmd1, cmd3, new2, sft), SYNful Knock Cisco IOS firmware implant (persistent “magic packet” access) | Target platforms: Cisco IOS XE/IOS (incl. WSMA abuse, SNMP, TFTP/FTP, NetFlow), Ivanti Connect Secure/Policy Secure, PAN-OS GlobalProtect; Smart Install | Adversary location: China, Russia
Exploited-Now CVEs: SharePoint AK47 RCE & WinRAR 8088
(Originally published in August 2025)
Attackers spent August hitting organizations on two fronts. First, a quartet of freshly patched SharePoint remote-code-execution bugs (CVE-2025-49704, -49706, -53770 and -53771) is being chained in the wild under the banner “Project AK47.” Once a vulnerable portal is reached, the intruders tracked as cluster CL-CRI-1040 / Storm-2603 plant a dual-channel back-door called AK47C2 (its dnsclient variant hides commands in DNS-TXT, while httpclient tunnels over HTTP) and ultimately launch the custom AK47 / X2ANYLOCK ransomware. Telemetry shows a clear overlap with a former LockBit affiliate and a Warlock double-extortion site, confirming a financially motivated play against any enterprise that still hosts on-prem SharePoint for document workflows.
At the same time, endpoint users are being lured with booby-trapped RAR archives that weaponize the WinRAR path-traversal zero-day CVE-2025-8088. All Windows builds up to version 7.12 let a crafted archive use “..\” sequences and hidden alternate-data streams to drop DLLs and .lnk shortcuts straight into the Startup folder; on reboot, payloads such as Mythic, SnipBot, RustyClaw and MeltingClaw beacon to command servers like gohazeldale[.]com. The rush began on 18 July 2025, led by the RomCom (Storm-0978) group and quickly copied by another crew nicknamed Paper Werewolf. Victims so far span finance, defence, manufacturing and logistics firms across Europe and Canada. Upgrading to WinRAR 7.13 and monitoring for rogue Startup links are now critical stop gaps until patch uptake is universal.
Threat Labs summary
Securonix Threat Labs Recommends leveraging these findings to strengthen defenses against these vulnerability campaigns.
- Patch SharePoint now. Install Microsoft’s August 2025 updates for CVE-2025-49704, -49706, -53770 and -53771 on every exposed server.
- Shield your portals. Keep SharePoint behind a reverse proxy/WAF, turn off unneeded APIs and require MFA for admins to disrupt the ToolShell exploit chain.
- Hunt for Project AK47 artefacts. Look for droppers named dnsclient.exe or httpclient-cpp.exe and for encrypted files or ransom notes ending .x2anylock.
- Detect covert DNS traffic. Alert on DNS TXT queries to look-alike domains such as update.updatemicfosoft[.]com, used by the backdoor for C2.
- Upgrade WinRAR everywhere to 7.13 or newer. Versions ≤ 7.12 remain vulnerable to CVE-2025-8088.
- Lock down archive extraction. Force RAR files to unpack only in user-writeable folders and block execution from %TEMP% and Startup paths.
- Monitor WinRAR IoCs. Flag unexpected .lnk shortcuts in Startup, unknown DLLs in %LOCALAPPDATA%/%TEMP%, and suspicious outbound traffic to RomCom infrastructure.
- Enforce least-privilege & segmentation. Run SharePoint and archival tools with minimal rights and place them in isolated network zones to contain any breach.
- 39 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the SharePoint (Project “AK47”) include but are not limited to the following:
- Monitor for processes named dnsclient or httpclient-cpp running on SharePoint hosts.
- Monitor for DNS TXT lookups that carry long, chunked, XOR/hex-encoded subdomains (AK47C2 dnsclient beaconing).
- Monitor for SharePoint servers sending HTTP POST requests with hex-encoded payloads in the body (AK47C2 httpclient).
- Monitor for DLL side-loading via 7z.exe (AK47 ransomware loaders).
- Monitor for files encrypted with the “.x2anylock” extension.
TTPs related to the WinRAR CVE-2025-8088 include but are not limited to the following:
- Monitor for exe dropping .lnk files into the Startup folder after extraction.
- Monitor for unknown DLLs written to %TEMP% or %LOCALAPPDATA% right after a RAR is unpacked.
- Monitor for extraction logs/telemetry showing ..\\ path traversal and heavy use of NTFS alternate data streams (ADS).
- Monitor for COM hijack activity touching PSFactoryBuffer (Mythic execution chain).
- Monitor for post-exploitation processes exe (trojanized PuTTY CAC), Complaint.exe (RustyClaw), and related payloads.
Tags: Target System: Microsoft SharePoint, WinRAR for Windows | Target sectors: Financial, defense, manufacturing, logistics | Threat Actor: CL-CRI-1040, RomCom | CVE Exploited: CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, CVE-2025-537711 | Target Location: Global | Payload: dnsclient, httpclient
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Nitish Singh, and Nikhil Kumar Chadha







