- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
- MSSPs
- Scale multi-tenant security with predictable economics.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar and Nitish Singh
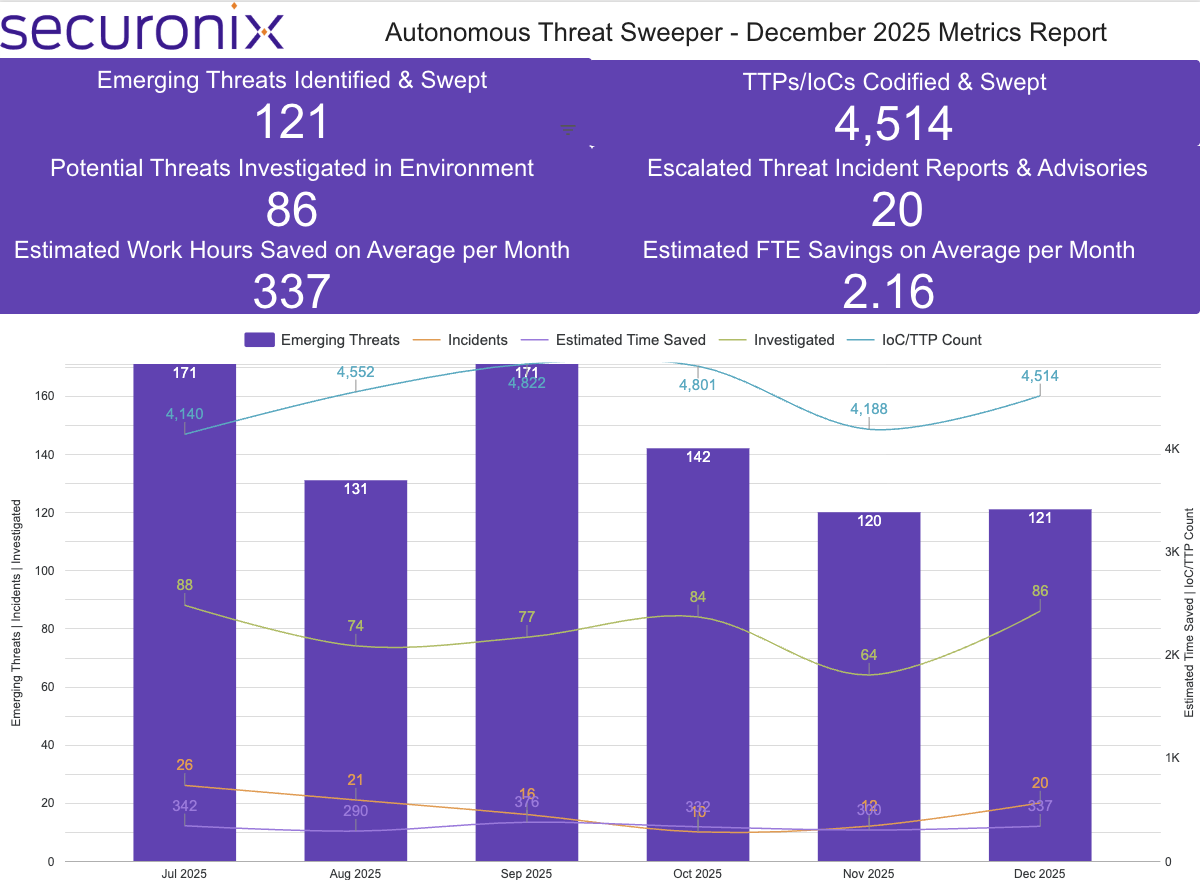
The Monthly Intelligence Insights report provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in December 2025. The report also includes a synopsis of the threats, indicators of compromise (IoCs), tactics, techniques, and procedures (TTPs), and related tags. Each threat has a comprehensive summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below-mentioned threats, refer to our Threat Labs home page.
Last month, Securonix Autonomous Threat Sweeper identified and analyzed 4,514 TTPs and IoCs; identified 121 emerging threats; investigated 86 potential threats; and elevated 20 incidents. The top data sources swept against include IDS / IPS / UTM / Threat Detection, Data Loss Prevention, Endpoint Management Systems, and Email / Email Security.
In December 2025, the Autonomous Threat Sweeper team observed an acceleration in exploitation-led intrusions and refined ransomware access chains, driven by rapid weaponization of developer frameworks, trusted tooling, and stealthy delivery mechanisms. Widespread React2Shell activity dominated the month, with multiple campaigns exploiting React Server Component remote code execution flaws, including in-the-wild abuse of React4Shell Redux (CVE-2025-55182), enabling direct server-side compromise through vulnerable React components and sustaining ongoing exploitation of the RSC attack surface. At the same time, adversaries sharpened their post-exploitation and monetization tradecraft, with Storm-0249 shifting toward precision targeting, GOLD SALEM expanding Warlock ransomware operations, and Matanbuchus 3.0 reestablishing itself as a dependable loader within ransomware access pipelines. Malware delivery increasingly abused trusted ecosystems, including ShadyPanda sleeper spyware and GhostPoster malware hidden inside browser extensions, AutoIT3 loaders deploying shellcode via FileInstall abuse, and the emergence of SantaStealer as a new infostealer focused on credential and session theft, while Intellexa-linked actors continued to demonstrate the persistence of zero-day exploitation frameworks. Advanced threat activity remained elevated, with Tomiris APT conducting espionage operations, the Prince of Persia APT resuming targeting, and UAT-9686 exploiting Cisco AsyncOS infrastructure, collectively reinforcing how attackers are converging framework-level RCE, trusted-platform abuse, and streamlined ransomware access chains to enable faster, stealthier, and more targeted intrusions.
React2Shell: Critical RCE Exploitation
(Originally published in December 2025)
This month saw widespread and active exploitation of CVE-2025-55182 (React2Shell), a critical pre-authentication remote code execution vulnerability affecting React Server Components (RSC) used by React, Next.js, and related frameworks. The vulnerability originates from unsafe deserialization in the React Flight protocol, where attacker-controlled objects are insufficiently validated during request reconstruction. By abusing prototype chain traversal, promise resolution (then), and the Blob handler mechanism ($B), attackers can reach the JavaScript Function constructor and execute arbitrary code in the Node.js runtime using a single crafted HTTP request, without authentication and under default configurations.
In-the-wild activity shows that exploitation began almost immediately after public disclosure and rapidly escalated from proof-of-concept testing to full post-exploitation operations. Multiple campaigns were observed deploying cryptominers (such as XMRig), botnets, and advanced post-exploitation frameworks, including interactive command-and-control implants. Both Linux and Windows environments were targeted, with significant focus on containerized and cloud-native workloads. Attackers actively harvest credentials by querying cloud instance metadata services (AWS, Azure, GCP), scanning filesystems for secrets, and abusing developers and CI/CD artifacts. Persistence mechanisms included fileless Node.js backdoors, systemd and cron job installation, and the use of covert network tunnels for command-and-control traffic.
Mitigation guidance indicates that while upgrading to patched versions of affected frameworks addresses the root cause, patching alone is insufficient. Organizations should prioritize remediation of internet-facing assets, deploy web application firewall rules capable of detecting React Flight protocol abuse, monitor Node.js processes for anomalous command execution or in-memory manipulation, and review historical logs for indicators of compromise. Overall, React2Shell represents a high-impact, low-effort attack vector that has already matured into large-scale active exploitation and remains a significant risk to modern web application environments.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these React2Shell flaws.
- Identify all applications using React Server Components and upgrade to patched versions of React and related frameworks, prioritizing internet-facing and cloud-hosted services.
- Where patching is delayed, deploy web application firewall (WAF) rules to detect and block malicious React Flight protocol abuse, including suspicious chunk references, promise manipulation (then), and dynamic code execution patterns.
- Enable monitoring and alerting for anomalous Node.js behavior such as unexpected child process execution, in-memory code execution, use of system utilities (curl, wget, bash, powershell), and abnormal file access.
- Restrict access to cloud instance metadata services, enforce least-privilege permissions, and monitor containers for fileless execution, unauthorized persistence, and unusual outbound network connections.
- Conduct retrospective log analysis to identify signs of compromise, including credential harvesting, unauthorized scheduled tasks, systemd services, cron jobs, and covert command-and-control communications.
- 260 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the React2Shell: Critical RCE Exploitation include but are not limited to the following:
- Monitor for pre-authentication HTTP POST requests to React Server Component endpoints containing abnormal or malformed React Flight payloads, including self-referencing chunk identifiers or unexpected promise resolution markers.
- Monitor for Node.js processes executing system commands such as whoami, id, uname, curl, wget, bash, sh, or powershell shortly after handling web requests.
- Monitor for Node.js or Next.js parent processes spawning child processes associated with shell execution, scripting, or network utilities.
- Monitor for execution of dynamically generated or in-memory JavaScript code within the Node.js runtime, especially code invoking the Function constructor or eval-like behavior.
- Monitor for outbound network connections from application servers to command-and-control infrastructure, including webhook endpoints, tunneling services, or dynamic DNS providers.
- Monitor for access attempts to cloud instance metadata service endpoints (AWS, Azure, GCP) originating from web application processes.
- Monitor for installation or modification of persistence mechanisms, including new systemd services, cron jobs, scheduled tasks, or startup scripts initiated by application runtimes.
- Monitor for disabling or tampering with host security controls such as firewalls, SELinux, AppArmor, or logging mechanisms.
- Monitor for fileless persistence techniques, including runtime hooking or modification of Node.js core modules or server request handlers.
Tags: Threat Name: React2Shell | CVE ID: CVE-2025-55182 | Threat Type: Remote Code Execution (RCE) | Attack Vector: Pre-authentication, single HTTP request | Vulnerability Class: Unsafe Deserialization / Prototype Chain Abuse | Target Sector: Cloud Service Providers, Technology & SaaS, E-commerce, Web Hosting Platforms, Software Development / CI-CD Environments | Target Location: Global | Target Systems: Linux Servers, Windows Servers, Cloud Virtual Machines, Kubernetes Nodes, Containerized Application Hosts | Target Platforms: React Server Components (RSC), Next.js Applications, Node.js Runtime, Cloud-native Platforms (AWS, Azure, GCP), Kubernetes & Container Platforms
Notable APT Group Operations
(Originally published in December 2025)
| UAT-9686 Targets Cisco Secure Email Gateway | A China-linked threat group tracked as UAT-9686 is conducting an active campaign targeting Cisco AsyncOS software used by Cisco Secure Email Gateway and Secure Email and Web Manager appliances. The group’s objective is to establish persistent, covert access to email security infrastructure that operates at network perimeters and responsible for handling sensitive communications. After gaining initial access, the attackers deploy a custom Python-based backdoor, AquaShell, which provides system-level command execution, along with additional tooling to enable traffic tunneling and manipulate logs in order to evade detection. The activity primarily affects organizations operating these appliances with non-standard configurations, and the impact is significant, as compromise of these systems can expose email traffic and provide a privileged foothold for lateral movement within the network. |
| Prince of Persia cyber-espionage Operation | The Iranian state-aligned threat group known as Prince of Persia (also tracked as Infy) has been conducting long-running cyber-espionage campaigns since at least 2017. The group primarily targets Iranian dissidents, journalists, and organizations associated with critical infrastructure across Iran, Europe, and the Middle East. Its operations rely on custom malware families, notably Foude and Tonnerre, which are commonly delivered through weaponized Excel documents containing malicious macros. Once executed, the malware establishes communication with attacker-controlled servers, fingerprints on the infected host, and enables the staged deployment of additional payloads or updates. The tooling incorporates advanced domain generation techniques, encrypted data exfiltration, and a recent shift toward using the Telegram API for C2 communications. Overall, the activity demonstrates strong operational discipline, supported by resilient infrastructure, multiple active control nodes, and interconnected loaders designed to systematically exfiltrate sensitive victim data. |
| Tomiris cyber-espionage operation | The Tomiris APT group has intensified its cyber espionage activities since early 2025, with a primary focus on government institutions, including foreign ministries, intergovernmental bodies, and other state-linked organizations. The campaign typically starts with phishing emails carrying password-protected archives that lure recipients to open malicious files posing as legitimate Office documents. After initial access, the group deploys additional payloads written in multiple programming languages to establish backdoors and ensure long-term persistence. To conceal command-and-control communications, Tomiris commonly exploits popular platforms such as Telegram and Discord, allowing malicious traffic to blend in with normal network activity. The operators then introduce further tools to support data exfiltration, lateral movement, and traffic tunneling, often leveraging modified open-source components to complicate attribution. Targeting patterns show a clear emphasis on Russian-speaking entities, particularly across Russia and Central Asia. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these APT group’s activities.
- Immediately review all Cisco Secure Email Gateway (ESA) and Secure Email and Web Manager (SMA) appliances for non-standard, unsupported, or insecure configurations, and remove or remediate any deviations.
- Ensure that all Cisco email and web security appliances are fully patched and running the latest supported versions of AsyncOS.
- Conduct an inspection of appliance file systems for unauthorized or modified Python files, particularly within web server directories, as the AquaShell backdoor is embedded in this location.
- Monitor for suspicious outbound network activity that resembles reverse SSH tunneling or HTTP-based proxy traffic originating from security appliances.
- Proactively block and continuously monitor domains generated through domain generation algorithms (DGAs), with particular attention to short, algorithmically constructed hostnames.
- Restrict the use of Excel macros across the organization and enforce a policy that disables macro execution by default.
- Monitor for abnormal use of legitimate cloud and messaging platforms, such as Telegram, for command-and-control communications from internal hosts.
- Strengthen email security controls to detect and block phishing messages that contain password-protected archives, a common delivery mechanism.
- Continuously analyze outbound network traffic for anomalous connections to legitimate platforms such as Telegram and Discord, including unusual API calls or webhook activity.
- 140 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the UAT-9686 Targets Cisco Secure Email Gateway include but are not limited to the following:
- Monitor for unexpected modifications to Python files within Cisco Secure Email Gateway or Secure Email and Web Manager web directories, especially changes to /data/web/euq_webui/htdocs/index.py, which may indicate deployment of the AquaShell backdoor.
- Monitor for unauthenticated or anomalous HTTP POST requests sent to internal Cisco appliance web interfaces containing encoded or obfuscated payloads, consistent with AquaShell command delivery and execution.
- Monitor for execution of system-level shell commands initiated by Python-based web server processes, which may signal exploitation of AquaShell for remote command execution.
- Monitor for creation or execution of unfamiliar GoLang ELF binaries on Cisco appliances, particularly those establishing outbound reverse SSH connections, indicative of AquaTunnel usage.
- Monitor for the presence or execution of tunneling tools such as Chisel, which may be used to proxy internal traffic and enable lateral movement through compromised edge devices.
- Monitor for suspicious log manipulation activities, including repeated use of commands like egrep with inverted searches followed by overwriting of log files, which may indicate AquaPurge being used to erase attacker artifacts.
TTPs related to the Prince of Persia Cyber-Espionage Operation include but are not limited to the following:
- Monitor for inbound emails delivering Excel attachments that contain macros and drop files like ccupdate.tmp.
- Monitor for repeated HTTP GET connections to index.php that send device details back to a server.
- Monitor for the execution of Foudre or Tonnerre-linked binaries, particularly those that perform initial system fingerprinting and profile collection prior to C2 communication
- Monitor for Excel macros that launch other programs to unpack and run hidden malware files.
- Monitor for internet traffic going to new or low-reputation domains, especially [.]org, [.]site, or dynamic DNS hosts.
- Monitor for long-term persistence or reinstallation attempts, where the same host contacts different versions of C2 servers such as those linked to Foudre v34, and Tonnerre v17/v12/v50.
- Monitor for unauthorized creation of temporary staging folders that store exfiltration artifacts, using names like blk, dir, dirm, or ep.
TTPs related to the Tomiris Cyber-Espionage Operation include but are not limited to the following:
- Monitor for phishing emails that deliver password-protected archives containing double-extension executables or files along with long filenames.
- Monitor for the creation or execution of Rust-, Go-, C++-, C#-, or Python-based binaries originating from user-writable locations or temporary directories.
- Monitor for outbound HTTP or HTTPS connections initiated by curl, bitsadmin, or PowerShell Invoke-WebRequest that retrieve second-stage payloads from external IP addresses or URLs.
- Monitor for the unexpected creation and execution of temporary .vbs or .ps1 scripts used as loaders or downloaders for follow-on payloads.
- Monitor for registry changes under HKCU\Software\Microsoft\Windows\CurrentVersion\Run that establish persistence for newly deployed executables.
- Monitor for outbound connections to the Telegram Bot API and Discord webhook endpoints initiated by non-browser or non-interactive processes.
- Monitor for the presence or execution of artifacts associated with open-source post-exploitation frameworks, including Havoc and AdaptixC2.
Tags: Malware: Foude and Tonnerre | Threat Actor: Prince of Persia, UAT-9686, Tomiris| Target Sector: Government, intergovernmental organizations, Foreign Minitries | Target Location: Middle East, Europe, Iran, Russia, Kyrgyzstan, Tajikistan, Uzbekistan | Target Platforms: Window Endpoints, MS Excel, Email Gateway, Email Appliance | Adversary Origin: Iran, China
Malicious Extensions Spotlight
(Originally published in December 2025)
Attackers abused Firefox extensions with a multi-stage design that hides malicious code inside the extension’s PNG logo. On load, the add-on read the image bytes, extracted a tiny loader, then waited hours or days before randomly pulling the real payload, so infections didn’t light up at once. Once active, it hijacked affiliate links, injected tracking scripts, and stripped site security headers (CSP/X-Frame-Options), weakening protections only in the infected browser. It also flashed short-lived hidden iframes for ad-fraud and rotated requests across a shared backend used by a cluster of 17 look-alike “free VPN” extensions that amassed 50k+ installs.
Separately, a long-running Chrome/Edge operation turned previously benign add-ons into spyware through malicious store updates, which impacted roughly 4.3 million installs. After updating, the extensions ran an hourly timer to fetch and execute arbitrary JavaScript with extension privileges, which allowed operators to add capabilities on demand (from page manipulation to data theft) without shipping a new version. Telemetry showed continuous exfiltration of visited URLs and search queries to infrastructure assessed as China-based, and several items quietly expanded permissions at update time easy to miss in large fleets. A prominent example, WeTab on Edge, shifted behavior after an update, illustrating how “sleeper” extensions switched to surveillance years after first install.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these malicious extension activities.
- In Chrome/Edge/Firefox enterprise policies, allow only approved extension IDs; block generic “free VPN/utility” themes by default.
- Compare inventory against the extension IDs and behaviors documented in the investigations; remove anything untrusted or recently changed.
- Alert when an extension downloads and executes remote JavaScript on a schedule, or when it reads/parses binary assets (PNG/SVG) and then runs injected code.
- Reinforce page protections. If a browser strips CSP/X-Frame-Options, restore them at the gateway/reverse proxy to maintain clickjacking/XSS defenses.
- Watch for delayed/sleeper behavior. Hunt for extensions that delay payload fetches (hours/days) or phone home hourly after a long benign period.
- Alert when an existing extension adds new permissions or changes behavior after an update especially on large fleets.
- 4 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Firefox campaign include but are not limited to the following:
- Monitor for extensions that read their own PNG/SVG assets at runtime and parse bytes looking for markers before executing injected code.
- Monitor for browser traffic patterns where the extension delays for ~48h and only fetches payloads occasionally (probabilistic check-ins).
- Monitor for pages that lose CSP/X-Frame-Options headers only when accessed via the infected browser (header stripping by the extension).
- Monitor for hidden iframes created and removed within seconds across unrelated sites (ad-fraud/redirect behavior).
TTPs related to the Chrome/Edge campaign include but are not limited to the following:
- Monitor for extensions that phone home on an hourly cadence to fetch and execute arbitrary JavaScript inside the browser.
- Monitor for sudden telemetry bursts (visited URLs / queries) from endpoints where the extension has been installed for years and only recently updated.
- Monitor for the WeTab extension on Edge and other add-ons that recently changed permissions or behavior after an update.
Tags: Target sectors: Broad consumer & enterprise users | Target locations: Global | Threat actor: ShadyPanda | Malware: Remote JS execution, tracking/affiliate abuse, ad-fraud | Target systems: Web browsers (Firefox, Chrome, Edge) | Target platforms: Windows/macOS/Linux
Evolving Threat Tradecraft & Ransomware Access Chains
(Originally published in December 2025)
The reporting highlights a clear trend toward greater precision, stealth, and operational maturity across the cybercriminal ecosystem, beginning with Storm-0249’s evolution from broad phishing into a sophisticated initial access broker model. Storm-0249 now abuses trusted enterprise security tooling, particularly EDR components, by leveraging DLL sideloading, fileless PowerShell execution, and domain spoofing to disguise malicious activity as legitimate security operations. By hijacking signed EDR processes and routing command-and-control traffic through them, the actor effectively blends into normal telemetry, enabling long-term persistence, covert reconnaissance, and rapid handoff of pre-staged access to ransomware affiliates, significantly compressing defender response windows and increasing ransomware impact across industries.
This operational shift aligns closely with observations of GOLD SALEM’s Warlock ransomware tradecraft, where access gained through exploitation of internet-facing systems, most notably SharePoint, quickly transitions into aggressive post-exploitation activity. GOLD SALEM demonstrates advanced capability by chaining zero-day exploits, deploying legitimate DFIR tools like Velociraptor for lateral movement, abusing tunneling utilities for resilient C2, and employing BYOVD techniques to disable EDR controls. These actions culminate in flexible ransomware deployment, including Warlock, LockBit, and Babuk variants, often tailored per victim. The group’s consistent tool reuse, rapid infrastructure rotation, and focus on persistence underscore how modern ransomware operations increasingly resemble structured intrusion campaigns rather than opportunistic attacks.
Completing this picture, Matanbuchus 3.0 represents the malware foundation enabling many of these hands-on-keyboard intrusions, acting as a modular backdoor and payload delivery framework favored by ransomware-adjacent actors. Its latest iteration introduces stronger obfuscation, Protobuf-based encrypted communications, advanced persistence via scheduled tasks, and extensive host profiling, including enumeration of installed security products to support tailored follow-on actions. Frequently delivered via MSI sideloading and social engineering, Matanbuchus bridges initial access and full ransomware deployment, reinforcing the broader trend seen across all these reports: attackers are prioritizing stealthy loaders, trusted binaries, and legitimate tooling to evade detection, maintain control, and maximize monetization opportunities.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these threat campaigns.
- Monitor trusted EDR processes for anomalous behavior such as unexpected DLL loads, execution from user-writable directories, and abnormal child processes.
- Enforce stricter controls and logging around Living-off-the-Land binaries (LOLBins) such as curl.exe, reg.exe, and findstr.exe.
- Prioritize patching and exposure reduction for internet-facing systems, particularly SharePoint, to mitigate common initial access vectors.
- Detect and alert on the misuse of legitimate tools (e.g., Velociraptor, VS Code tunnels, Cloudflared) when deployed from non-standard or external infrastructure.
- Detect MSI-based delivery and DLL sideloading techniques associated with initial payload execution.
- Alert on host profiling activity, including enumeration of installed security products and system metadata.
- 55 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to Storm-0249 includes but are not limited to the following:
- Monitor for legitimate, digitally signed EDR processes (for example, SentinelAgentWorker.exe) loading DLLs from non-standard or user-writable directories such as AppData, indicating potential DLL sideloading.
- Monitor for MSI installers executing with SYSTEM privileges that originate from external or spoofed domains and subsequently drop or modify files associated with EDR software.
- Monitor for curl.exe executing commands that pipe downloaded content directly into PowerShell without writing files to disk, consistent with fileless payload execution.
- Monitor for PowerShell execution initiated by curl.exe or other non-interactive parent processes, especially when command-line arguments indicate in-memory execution.
- Monitor for registry access commands such as reg.exe and string-search utilities like findstr.exe being executed under trusted EDR processes rather than standard administrative shells.
- Monitor for repeated access to system identifiers such as MachineGuid by security software processes outside of normal update or telemetry collection patterns.
TTPs related to GOLD SALEM’s include but are not limited to the following:
- Monitor for SharePoint (w3wp.exe) spawning msiexec.exe, cmd.exe, or powershell.exe, especially when followed by downloads from external infrastructure.
- Monitor for execution of msiexec.exe installing MSI packages retrieved from Cloudflare Workers (*.workers.dev) or public cloud storage shortly after SharePoint process activity.
- Monitor for Velociraptor MSI installers (v2.msi, v3.msi) being downloaded and installed from attacker-controlled domains or cloud storage locations.
- Monitor for Velociraptor launching Visual Studio Code (code.exe or vscode.exe) with tunnel or remote access options enabled.
- Monitor for the use of Cloudflared tunneling tools (cf.msi) being installed or executed on non-administrative or non-network infrastructure systems.
- Monitor for creation of new local administrator accounts via net user or net localgroup commands, especially accounts with weak or reused passwords.
- Monitor for administrator account names such as backupadmin, admin_gpo, or similarly generic service-style accounts being created outside of normal provisioning workflows.
- Monitor for attempts to enumerate or access the LSASS process, including use of tasklist followed by memory dump techniques leveraging comsvcs.dll.
- Monitor for execution of binaries named vmtools.exe, VMToolsEng.exe, or similar variants attempting to terminate antivirus or EDR processes.
- Monitor for loading of vulnerable or uncommon kernel drivers (rsndispot.sys, kl.sys, ServiceMouse.sys) indicative of Bring Your Own Vulnerable Driver (BYOVD) attacks.
- Monitor for Java processes loading unexpected DLLs (jli.dll) from non-standard directories, suggesting possible DLL side-loading.
- Monitor for the presence of ransomware encryption extensions such as .x2anylock or .xlockxlock appearing across multiple systems within a short timeframe.
- Monitor for the creation or execution of ransom notes named how to decrypt my data.log or similar filenames across endpoints.
TTPs related to Matanbuchus 3.0 include but are not limited to the following:
- Monitor for the creation of new scheduled tasks named “Update Tracker Task” or similar, particularly tasks that execute msiexec.exe with nonstandard parameters or paths.
- Monitor for the creation of randomly named directories under the user’s APPDATA path, followed by self-copying of executables with randomized lowercase filenames.
- Monitor for registry key creation under HKEY_CURRENT_USER\SOFTWARE\ paths derived from disk volume serial numbers, which may indicate malware registration or persistence tracking.
- Monitor for encrypted network traffic containing structured payloads consistent with Protocol Buffers and ChaCha20-encrypted data exchanged with command-and-control servers.
- Monitor for payload execution techniques such as process injection into msiexec.exe, in-memory execution of .NET assemblies, or DLL execution via rundll32 or regsvr32.
- Monitor for the creation and use of named pipes with formats resembling \\.\pipe\dll-<hex_pid>, which may indicate staged DLL injection.
Tags: Threat Actor: Storm-0249, GOLD SALEM | Threat Actor Type: Initial Access Broker (IAB), Ransomware operator, Malware-as-a-Service (MaaS) users | Adversary Location: Suspected China-based | Associated Ransomware: Warlock, LockBit, Babuk | Target Sectors: Cross-sector (Enterprise organizations using EDR solutions), Information Technology, Industrial, Technology, Government, Telecommunications, Research & Energy | Target Locations: Global, Europe, Southeast Asia, Taiwan, Russia | Target Systems: Enterprise endpoints, Windows endpoints, VMware ESXi servers, On-premises SharePoint servers | Target Platforms: Windows, Linux (ESXi) | Malware: Loader malware, post-exploitation payloads, Warlock ransomware, LockBit 3.0 variants, Babuk ransomware, Matanbuchus 3.0, Rhadamanthys Stealer, NetSupport RAT
Notable Malware Campaigns Overview
(Originally published in December 2025)
| Redtail Malware | Redtail is a Linux-focused malware family observed in widespread scanning and exploitation activity across the internet, primarily targeting exposed services and poorly secured systems. The malware is commonly distributed via automated attacks originating from multiple IP addresses and is frequently observed under the same filenames but with varying hashes, indicating ongoing recompilation or minor modifications. It supports multiple architectures, including x86, x86_64, ARM, and ARM64, allowing it to run across diverse environments. Once deployed, Redtail establishes persistence, executes secondary payloads, and enables remote control of the infected host. Analysis of telemetry data using graph-based visualization highlights strong relationships between source IPs, file names, and hashes, revealing coordinated infrastructure reuse over extended periods. This activity demonstrates an opportunistic, scalable threat model focused on mass compromise rather than targeted intrusion, with attackers leveraging automation to maximize reach and resilience. |
| Intellexa / Predator Spyware | Intellexa is a commercial surveillance vendor best known for its Predator spyware platform and its extensive use of zero-day exploit chains targeting mobile devices. Despite being sanctioned by the U.S. government, Intellexa continues to operate by evading restrictions and acquiring or developing new exploits. Google Threat Intelligence Group (GTIG) attributes 15 confirmed zero-day vulnerabilities to Intellexa since 2021, spanning remote code execution (RCE), sandbox escape (SBX), and local privilege escalation (LPE) across Apple iOS, Google Chrome, Android, and ARM Mali GPUs. The group delivers exploits primarily through one-time malicious links sent via encrypted messaging apps and, more recently, through malicious advertisements used for user fingerprinting and redirection. Successful exploitation results in the deployment of a sophisticated multi-stage spyware framework capable of stealthy surveillance, device validation, and persistence, often as a precursor to full Predator deployment. |
| SantaStealer | SantaStealer is a malware-as-a-service (MaaS) information stealer actively advertised on Telegram channels and Russian-speaking underground forums, recently rebranded from BluelineStealer and declared production-ready by its operators. The malware targets Windows systems and is designed to steal credentials, documents, browser data, cryptocurrency wallets, and messaging application data. SantaStealer emphasizes fileless execution, with most collection and processing performed entirely in memory to evade file-based detection. Stolen data is compressed into ZIP archives, split into 10 MB chunks, and exfiltrated over unencrypted HTTP to hard-coded command-and-control (C2) servers. Although marketed as “fully undetected” and polymorphic, analyzed samples reveal exposed symbols, plaintext configuration data, and immature anti-analysis implementations, indicating ongoing development rather than a fully mature threat. |
Threat Labs summary
Securonix Threat Labs Recommends leveraging these findings to strengthen defenses against these malicious campaigns.
- Enforce strict email and web filtering to block malicious attachments, fake CAPTCHA pages, and phishing links commonly used to deliver infostealers.
- Monitor and block unencrypted HTTP exfiltration traffic, especially outbound connections to unusual IPs and ports (custom C2 endpoints).
- Restrict users from running unverified software, including pirated tools, game cheats, cracked applications, and untrusted browser extensions.
- Apply least-privilege principles to limit the impact of credential theft and prevent access to sensitive applications and stored credentials.
- Apply security patches immediately across browsers, mobile operating systems, and devices to reduce exposure to zero-day exploitation chains.
- Monitor for suspicious one-time links and malicious advertisements, particularly those delivered via encrypted messaging platforms.
- Implement Safe Browsing and DNS protections to block known exploit delivery domains and infrastructure.
- Alert and protect high-risk users (journalists, activists, government officials) who are more likely to be targeted by mercenary spyware.
- 29 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Redtail Malware include but are not limited to the following:
- Monitor for inbound connections to SSH or exposed services that result in file transfers where event.reference is tagged as “no match”, indicating activity not associated with known researchers or benign scanners.
- Monitor for the same filename being associated with multiple distinct file hashes, which may indicate polymorphic malware variants or recompiled payloads using consistent naming conventions.
- Monitor for execution or transfer attempts of suspicious shell scripts such as setup.sh or clean.sh, especially when observed alongside outbound or inbound network activity from unfamiliar IP addresses.
- Monitor for file transfer activity involving architecture-specific binaries (for example .x86_64, .i686, .arm7, .arm8) that may indicate automated malware deployment across multiple system types.
TTPs related to the Intellexa / Predator Spyware include but are not limited to the following:
- Monitor for devices executing JavaScript exploitation frameworks capable of arbitrary memory read/write, PAC bypass, or in-memory Mach-O loading and execution without a corresponding on-disk binary.
- Monitor for creation or use of suspicious Unix domain sockets such as /tmp/helper.sock, indicating inter-process communication between staged spyware components.
TTPs related to the SantaStealer include but are not limited to the following:
- Monitor the creation of temporary ZIP archives like “Log.zip” in the TEMP directory following large-scale in-memory collection of files, screenshots, or application data.
- Monitor for outbound HTTP traffic to unusual external IP addresses over non-standard ports such as 6767, particularly multipart/form-data uploads to an /upload endpoint with custom headers like auth, w, or complete.
- Monitor for systems performing bulk data exfiltration in consistent 10 MB chunks over plain HTTP shortly after a burst of local discovery or credential access activity.
Tags: Malware Family: RedTail, Predator, PREYHUNTER (GTIG tracking name), SantaStealer, BluelineStealer | Malware Type: Botnet / Backdoor (Linux-focused) | Target Systems: Internet-facing Linux servers, SSH-enabled hosts, Honeypots (Cowrie sensors), Mobile Devices, Smartphones, Tablets, Endpoint systems, User workstations | Target Location: Global, Egypt, Saudi Arabia, Pakistan, Kazakhstan, Angola, Uzbekistan, Tajikistan, Mongolia (related JSKit usage) | Target Sectors: Government, Public Sector, Political Targets, Journalists, Human Rights Activists, Civil Society, High-Value Individuals, Government, Corporate enterprises, Financial services, Cryptocurrency users, General consumer endpoints | Adversary / Operator Locations: Europe (Intellexa-linked entities), Middle East (Customer Operations), Global (Distributed Infrastructure) | Target Platforms: Windows 10, Windows 11, Windows (64-bit)
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to ours Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Nikhil Kumar Chadha and Tanmay Kumar