- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, Ella Dragun
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs during February. The report additionally provides a synopsis of the threats; indicators of compromise (IOCs); tactics, techniques, and procedures (TTPs); and related tags. This may be followed by a comprehensive threat summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below mentioned threats, refer to our Threat Labs home page.
In February 2023, Threat Labs analyzed and monitored major threat categories, including multiple cyber campaigns involving LockBit ransomware, ransomware attacks on healthcare sectors, attack campaigns on government organizations, and ongoing phishing campaigns. Of note are the ransomware attacks targeting VMware ESXi servers to deploy ESXiArgs ransomware that continued through the month. The ESXiArgs attacks leveraged an old vulnerability that had been discovered two years ago.
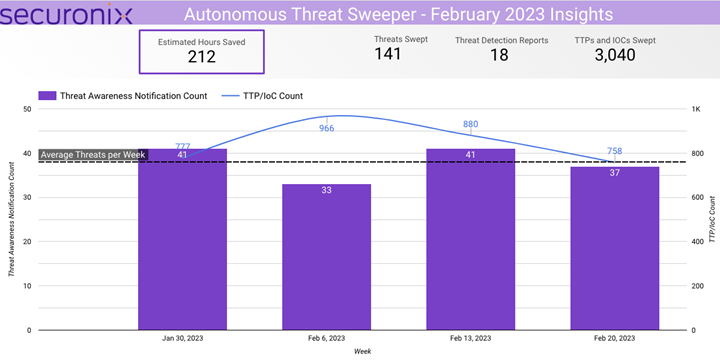
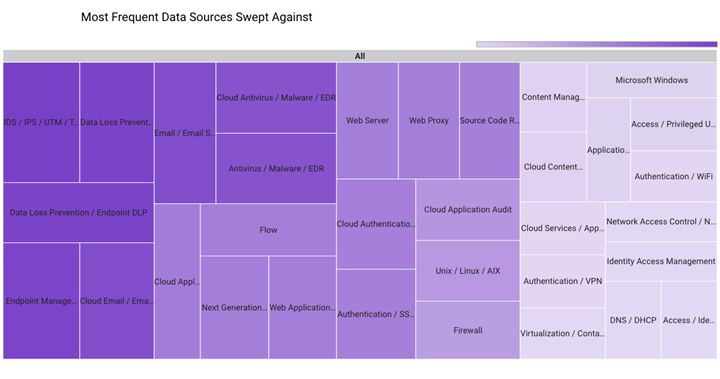
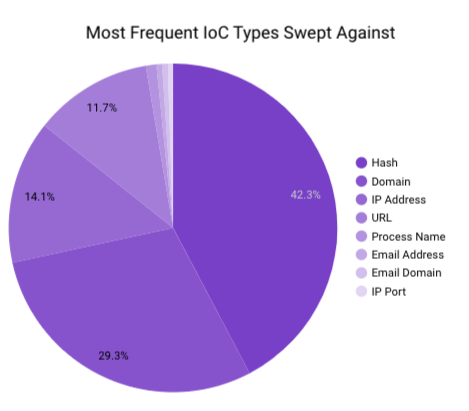
In February 2023, Securonix Autonomous Threat Sweeper identified 3,040 TTPs and IOCs, 141 distinct threats, and reported 18 threat detections. The top data sources swept against include IDS/IPS/UTM/Threat Detection, Endpoint Management Systems, Data Loss Prevention, and Email/Email Security.
LockBit ransomware
(Originally published in February 2023)
According to researchers, the LockBit 2.0 ransomware is back with a change in its distribution format. Currently, it is distributed in a MalPE format instead of the NSIS format and uses filenames that make them seem like job applications.
The research reported that LockBit 3.0 introduced a new variant called ‘Black’. An important characteristic of this variant is its high infection vector and attack chain, as well as its significant anti-forensic activity, which includes clearing event logs, killing multiple tasks, and deleting services all at once. In the initial attack, it tries brute forcing SMB from a variety of IP addresses to gain access to the victim’s network.
Threat Labs summary
Securonix Threat Labs is actively monitoring LockBit ransomware campaigns as they are spreading rapidly again.
- Threat Labs observed the LockBit 2.0 ransomware distributing its filename as “Re_su_me [230124 (Experience details are included Thank you].exe” through the MalPE format, which contains a specific string in the service area.
- Threat Labs observed a common feature of MalPE format malware is its identical icon distribution. However, its icon has been changed to reflect its disguise as a resume, so that Lockbit 2.0 can be identified as ransomware.
- Threat Labs observed a malicious BAT file is executed using the sys-internal tool PSEXEC, but the files are then removed, and the activity relates to modifying RDP and authentication settings and disabling antivirus at the same time.
- 19 IOCs are available on our Threat Labs home page repository and have been swept against Securonix Autonomous Threat Sweeper customers.
TTPs related to the LockBit ransomware include but are not limited to the following and can be detected as follows:
- Monitor for abnormal spike in traffic on port 445/139 (SMB) from distinct IP’s as initial access is usually via SMB brute forcing.
- Monitor for rare and unusual batch file execution from command prompt.
- C:\Windows\system32\cmd.exe /c “openrdp.bat”
- C:\Windows\system32\cmd.exe /c “turnoff.bat”
- Monitor for rare and atypical service deletions, process terminations and tasks killed.
- sc delete “MsMpEng”
- net stop ShadowProtectSvc
- Monitor the usage of “net” commands to remove/delete all active network connections.
- net use * /delete /y
- Monitor rare and suspicious usage of vssadmin and wmic to delete shadowcopies.
- vssadmin delete shadows /all /quiet
- wmic shadowcopy delete
- Monitor atypical usage of the commandline utility – wevtutil to clear logs and evade detection.
- wevtutil cl application
- wevtutil cl system
Tags: Ransomware: LockBit 2.0, LockBit 3.0, LockBit Black Variant
Ransomware attack on US healthcare sector
(Originally published in February 2023)
In a joint advisory issued by the United States National Security Agency, Federal Bureau of Investigation, Cybersecurity and Infrastructure Security Agency, U.S. Department of Health and Human Services, and the Korean National Intelligence Service and Defense Security Agency, North Korean ransomware attacks were observed against public health and other critical infrastructure sectors with the Maui and H0lyGh0st ransomware. The advisory assessed that DPRK used an unspecified amount of the revenue from their cryptocurrency operations to support its national priorities, such as espionage cyber operations against the US and South Korea.
Aside from using typical ransomware tactics, the actors have also acquired and purchased infrastructure to conceal their connection to the DPRK.
Threat Labs summary
Securonix Threat Labs is actively monitoring ransomware campaigns as they are spreading rapidly again and recommends that healthcare organizations implement security measures such as multi-factor authentication (MFA) to protect their accounts, encrypted connectivity, turning off unused interfaces, monitoring network traffic, following the principle of least privilege, and updating all software products.
- 209 IOCs are available on our Threat Labs home page and have been swept against Securonix Autonomous Threat Sweeper customers.
Tags: Ransomware: Maui Ransomware, H0lyGh0st Ransomware | Threat Actor Location: North Korea | Target Sector: Healthcare
Ongoing phishing campaigns in February
(Originally published in February 2023)
Proofpoint researchers have identified an increase in threat actor use of OneNote documents to deliver malware via email to unsuspecting end-users in December 2022 and January 2023. Different threat actors are using OneNote documents, a Microsoft digital notebook available via the Microsoft 365 product suite, to deliver malware. Proofpoint noticed several OneNote campaigns that deliver different malware payloads including AsyncRAT, Redline, AgentTesla, and DOUBLEBACK.
Researchers also shared an observation of a new threat actor TA866 who was distributing malware via email and additionally had a cluster of evolving financially motivated activity which they are referring to as “Screentime”. The attack chain starts with an email containing a malicious attachment or URL and leads to malware that Proofpoint dubbed WasabiSeed and Screenshotter. All it takes to compromise the system is for a user to click on a malicious link and, if successful, it would interact with a JavaScript file to download and run additional payloads. Organizations should provide training about this technique for users and encourage them to report suspicious emails and other activities. This threat actor’s activity appears to be financially, and possibly also espionage motivated, targeting organizations in the United States and Germany.
Threat Labs summary
- Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from digital ads.
- Implement network segmentation and maintain offline backups of data to ensure limited interruption to your organization.
- Disable unused ports and enable multi-factor authentication (MFA).
- 83 IOCs are available on our Threat Labs home page and have been swept against Securonix Autonomous Threat Sweeper customers.
Tags: Attack Vector: Microsoft 365 product suite, OneNote documents, email | Malware payloads: AsyncRAT, Redline, AgentTesla, and DOUBLEBACK| Target location: the United States and Germany
Attack campaigns on government organizations
(Originally published in February 2023)
This month researchers observed campaigns targeting various government organizations. One of them was a new campaign called Havoc observed by the Zscaler ThreatLabz research team targeting a government organization. The threat actors have been using a new Command & Control (C2) framework named Havoc. At the beginning of the year the team discovered an executable named “pics.exe” in the Zscaler Cloud targeting a government organization. The executable was downloaded from a remote server: “146[.]190[.]48[.]229”. Havoc Demon payload is the implant generated via the Havoc Framework — which is a modern and malleable post-exploitation command and control framework.
Another significant campaign was the ReverseRAT backdoor attack targeting Indian government agencies. Researchers from ThreatMon observed a spear-phishing campaign directed at Indian government agencies that aims to deploy an updated version of a backdoor called ReverseRAT. Earlier a Pakistani threat group SideCopy attacked Indian government agencies with a malicious email containing a macro-enabled Word document. When it triggers the malicious code, SideCopy gains initial access. The malware ReverseRat is capable of gaining persistence and uses RC4 to collect and encrypt on the victim’s device before sending it to the C2 server.
The SideCopy group primarily attacks South Asian countries. Since 2019, it is believed SideCopy’s intention was to copy another suspected Indian threat group, Sidewinder.
Threat Labs summary
Securonix Threat Labs is actively monitoring running campaigns by Playful Taurus threat actors that are targeting Iranian government organizations as they begin spreading once again.
- Threat Labs observed threat actors using a new C2) framework named Havoc
- Threat Labs observed that the attack campaigns using Havoc target government organizations. ZScaler researchers revealed how the malware can be leveraged by the threat actors in various campaigns and discovered an executable named “pics.exe” in the Zscaler Cloud targeting a government Organization
- 8 IOCs are available on our Threat Labs home page repository and have been swept against Securonix Autonomous Threat Sweeper customers.
Tags: Threat Actor: SideCopy group | Target Sector: Government Organizations | Target location: India, South Asian countries, USA | Campaign: Havoc
ESXiArgs ransomware leveraging two year old vulnerability
(Originally published in February 2023)
This month Trellix researchers reported attacks by ESXiArgs ransomware on an old vulnerability. The vulnerability ransomware actors targeted is CVE-2021-21974 which allows an attacker to exploit the OpenSLP protocol if the affected server is exposed to the internet. Based on VMware research and observation, the threat actor activity constantly scans the internet for ESXiArgs servers that are targets for this remote code execution vulnerability. As soon as the attacker identifies the exploitable machine they attempt to create a heap buffer overflow and execute code remotely to compromise the server.
Another research team, SecurityScorecard warned about a widespread ransomware campaign exploiting the same CVE-2021-21974 VMWare ESXi vulnerability. Their analyses about this new campaign came in response to the advisories and they discovered possible communication between target IP addresses and infrastructure that were involved in the exploitation of this vulnerability. They observed that the recent “ESXiArgs” ransomware variant spread to a large number of outdated, internet-exposed ESXi servers around the world.
BitDefender, Cyble, and Wiz researchers also issued their advisories on the ransomware attack campaigns.
Threat Labs summary
- Securonix Threat Labs continues to actively monitor vulnerabilities and exploits while identifying notable threats that could have a tremendous impact if not addressed.
- Securonix Threat Labs recommends updating vulnerable applications to the latest version immediately and following mitigation guidelines.
- 468 IOCs are available on our Threat Labs home page repository and have been swept against Securonix Autonomous Threat Sweeper customers.
TTPs related to the ransomware attacks targeting VMware ESXi sServers include but are not limited to the following and can be detected as follows:
- Monitor for network traffic containing “info.php?name=”, “dn.php?name=” and “up.php?name=” in the request url.
- Monitor for the rare instance where rundll32.exe is executed with commandline parameter – ”iiiiiiii“
- Example: cmd /c rundll32 “C:\Users\username\AppData\Local\Temp\wpnprv.dll”, IIIIIIII 4 “cmd /c del /f /q C:\Windows\system32\wpcsvc.dll”
- Monitor for rare commandlines executed that contain all these parameters – “cd /d” and ”dir” and ”/a/o-d/s” and ”*.”
- Example: cmd /c cd /d “C:\Users” && dir /a/o-d/s *.*
- Monitor for cmd.exe spawning expand.exe to decompress the cab files.
- Example: cmd /c expand %TEMP%\1.cab -f:* %TEMP%
- Monitor the rare registryregisty additions that contains either of the two combinations – “system\currentcontrolset\services” and “reg_expand_sz” or “software\microsoft\windows nt\currentversion\svchost” and “reg_multi_sz”.
- Example: reg add “HKLM\SYSTEM\CurrentControlSet\Services\wpcsvc\Parameters” /v ServiceDll /t REG_EXPAND_SZ /d “%windir%\System32\wpcsvc.dll” /f > nul
- Monitor the execution of process sc.exe wherein the commandlines contain the parameters ”failure”, ”reset=” and ”actions=”
- 25 IOCs are available on our Threat Labs home page and have been swept against Securonix Autonomous Threat Sweeper customers.
Tags: Vulnerability: VMWare ESXi vulnerability CVE-2021-21974 | Exploitation: OpenSLP protocol Target: VMware ESXi servers
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at scia@securonix.com.
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Sina Chehreghani, Dhanaraj K R, Tim Johny







