- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
- MSSPs
- Scale multi-tenant security with predictable economics.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Nitish Singh, and Nikhil Kumar Chadha
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in July 2025. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. Each threat has a comprehensive summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below-mentioned threats, refer to our Threat Labs home page.
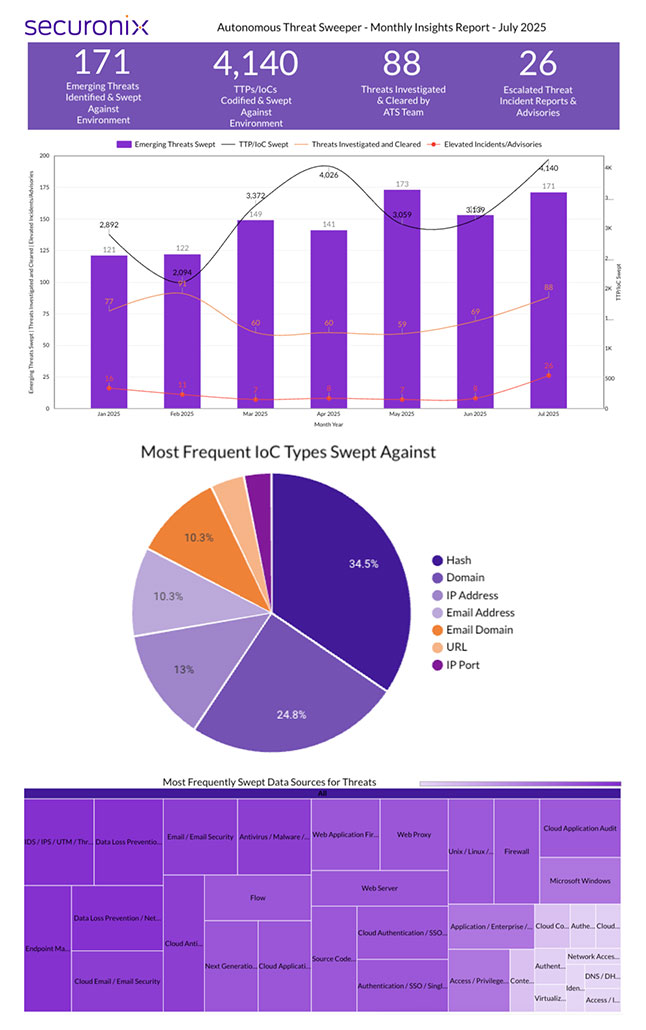
Last month Securonix Autonomous Threat Sweeper identified and analyzed 4,140 TTPs and IoCs, 171 emerging threats, investigated 88 potential threats, and elevated 26 threat incidents. The top data sources swept against include IDS / IPS / UTM / Threat Detection, Data Loss Prevention, Endpoint Management Systems, and Email / Email Security.
In July 2025, the Autonomous Threat Sweeper team identified a cyber threat environment characterized by advanced exploitation techniques, targeted espionage campaigns, and the continued proliferation of ransomware-as-a-service (RaaS) models. ToolShell activity intensified with the simulation and real-world exploitation of CVE-2025-53770 in Microsoft SharePoint, enabling unauthenticated remote code execution (RCE) scenarios. Additional vulnerabilities emerged, such as the Tomcat Partial PUT Camel Header Hijack, which posed stealthy risks to web application integrity. Phishing operations surged, with campaigns like Rainbow Hyena targeting global users, the Taiwan Chip espionage campaign seeking intellectual property, and the DoNot APT conducting spear-phishing against Southern European diplomatic entities. Malware activity expanded as Hpingbot leveraged Pastebin for payload delivery, CL-STA-1020 targeted government bodies, and GhostContainer exploited Microsoft Exchange servers across Asia. Notably, Silver Fox deployed rootkits signed with expired certificates, while Batavia malware campaigns intensified against Russian networks. Ransomware threats reached new heights with variants such as DEVMAN, Pay2Key.I2P targeting Western organizations, Dark 101, KAWA4096, and specialized strains like NailaoLocker Cheese, Interlock leveraging ClickFix-style delivery, and Chaos Ransomware Group attacks. These developments underscore the critical necessity for timely vulnerability patching, heightened phishing awareness, and resilient multi-layered security defenses to counter the evolving threat spectrum.
Exploitation of SharePoint ToolShell Zero-Day
(Originally published in July 2025)
The ToolShell exploit chain (CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, and CVE-2025-53771) targets on-premises Microsoft SharePoint Servers, allowing unauthenticated remote code execution (RCE).
Exploit Chain and CVEs:
- CVE-2025-49706: Authentication bypass via the misuse of the Referer header (/_layouts/SignOut.aspx) to access the aspx endpoint.
- CVE-2025-49704: Insecure deserialization vulnerability leading to RCE.
- CVE-2025-53770: Variant of the above, combining the bypass and deserialization in a new form.
- CVE-2025-53771: Further bypass discovered after patches for the above were released.
Microsoft confirmed that attackers chain these CVEs to deploy .aspx webshells like spinstall0.aspx and steal ASP.NET MachineKeys used to sign __VIEWSTATE data
Behavior in the Wild:
- Payload: The aspx webshell extracts MachineKeys using internal .NET reflection APIs.
- Process Lineage: exe (IIS worker) → cmd.exe → powershell.exe executing base64-encoded payloads.
- Execution Flow: Webshell does not execute commands interactively. It passively leaks secrets via HTTP GET requests.
Persistence: Attackers maintain access using extracted cryptographic secrets, bypassing login even after patching.
Microsoft attributed ToolShell exploitation to China-based threat actors:
- Storm-2603: Used ToolShell to deploy Warlock ransomware via Group Policy Object (GPO)
- Linen Typhoon and Violet Typhoon: Known state-sponsored APTs leveraging similar techniques for espionage and credential theft.
Securonix Threat Lab simulated the exploit chain to develop real-world detection logic:
- Event ID 11 (Sysmon): File creation of aspx under w3wp.exe → cmd.exe/powershell.exe.
- Event ID 1: PowerShell spawned from exe with suspicious encoded commands.
- Introduced OOTB detection content to identify:
- Suspicious file drops in LAYOUTS directory
- Child process anomalies (e.g., exe spawning LOLBINs)
- Encoded PowerShell use within web server context.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against this exploitation of SharePoint ToolShell Zero-Day attack.
- Deploy Microsoft’s July 2025 security updates across all on-premises SharePoint servers. Following patching, rotate the ASP.NET MachineKeys and restart IIS to prevent reuse of compromised cryptographic tokens.
- Isolate SharePoint environments by limiting access to approved internal or VPN-protected networks. Where applicable, implement Zero Trust Network Access (ZTNA) to reduce the external attack surface.
- Prioritize systems showing anomalous ToolPane.aspx or SignOut.aspx access.
- Leverage behavior-based detections that monitor for:
- File creation in \LAYOUTS directory (e.g., spinstall0.aspx)
- Encoded PowerShell or cmd.exe execution from w3wp.exe
- Abnormal child processes under IIS worker processes
- 75 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the SharePoint ToolShell Zero-Day include but are not limited to the following:
- Monitor for HTTP POST requests to /ToolPane.aspx with spoofed Referer: /_layouts/SignOut.aspx.
- Monitor creation of .aspx files in SharePoint LAYOUTS directories. File creation in:
- C:\Program Files\Common Files\microsoft shared\Web Server Extensions\15|16\TEMPLATE\LAYOUTS\
for files like spinstall0.aspx, spinstall.aspx, xxx.aspx, 3plx.aspx, debug_dev.js, or info.js is a key post-exploitation behavior.
- Monitor w3wp.exe spawning PowerShell, CMD, or LOLBINs.
- Monitor for PowerShell usage with -EncodedCommand or Base64 payloads.
- Monitor access to .aspx pages that return cryptographic keys (MachineKeys).
- Monitor process chains where w3wp.exe → cmd.exe → powershell.exe occurs.
- Monitor for web requests that generate 160-byte HTTP responses from spinstall0.aspx.
- Monitor for Microsoft Edge sub-processes misused for sandbox evasion (e.g., –type=gpu-process, –type=crashpad-handler).
- Monitor use of .NET reflection and System.Web.Configuration.MachineKeySection in ASP.NET scripts.
- Monitor file access to SharePoint config files (e.g., web.config) followed by network exfiltration.
Tags: Threat Actor: Storm-2603, Linen Typhoon, Violet Typhoon | Target Sector: Government, Healthcare (including hospitals), Education, Manufacturing, Critical Infrastructure, Technology Consulting, Professional Services | Target Location: United States, Iran, Germany, Greece, Ireland, Russia | Target Systems: Microsoft SharePoint Server (on-premises) Versions 2016, 2019, Subscription Edition | Target Platforms: Windows Server (IIS), .NET Framework, ASP.NET | Adversary Location: China | Malware/Tools: spinstall0.aspx webshell, SharpyShell, 4L4MD4R Ransomware (variant of Mauri870), Mimikatz, Impacket Toolkit, PowerShell encoded payloads, debug_dev.js / info.js output files, IIS .dll backdoors, Edge Utility Abuse (gpu-process, crashpad-handler)
Phishing Campaign Analysis and Trends
(Originally published in July 2025)
| DoNot APT Group – Southern European Government Campaign | In this operation, the DoNot APT group targeted a Ministry of Foreign Affairs via a highly tailored spear-phishing email impersonating a defense attaché, leveraging HTML tricks and a Google Drive link to deliver a password-protected RAR. Once opened, the victim executes notflog.exe, which drops a BAT loader in %TEMP% that creates two scheduled tasks (“PerformTaskMaintain” and “MicorsoftVelocity”) to install a custom LoptikMod DLL backdoor. The malware employs runtime string decryption, selective section packing, dynamic API resolution and anti-VM checks to evade analysis, and communicates with its C2 over AES-encrypted, Base64-wrapped HTTPS to C2 server domain. |
| China-Aligned Espionage Against Taiwan’s Semiconductor Industry | Three distinct clusters (UNK_FistBump, UNK_DropPitch and UNK_SparkyCarp) used themed lures—graduate-student job offers, investment-research collaborations and MiTM phishing kits—to breach semiconductor targets. They delivered payloads via ZIP→LNK→VBS loaders and DLL sideloads in legitimate Java/Cisco binaries (Cobalt Strike Beacon, Voldemort, HealthKick backdoor and raw TCP shells), established persistence through scheduled tasks, and in select cases installed Intel EMA agents. Infrastructure included SoftEther VPN servers with “elliot-alderson” hostnames and overlapping TLS certificates tied to known tooling, with C2 channels spanning GoToMeeting-style beaconing, Google Sheets API, WebSocket-over-TLS and raw TCP. |
| Rainbow Hyena “PhantomRemote” Campaign | The threat actor group “Rainbow Hyena” launched a sophisticated phishing campaign targeting healthcare and IT organizations in Russia. Leveraging compromised email accounts, the attackers distributed deceptive messages containing malicious polyglot ZIP files and LNK shortcuts, which executed embedded DLLs. The campaign introduced a new custom backdoor dubbed PhantomRemote, capable of system reconnaissance, command execution, and file download via HTTP-based C2 communication. This tool masqueraded as legitimate services using fake User-Agent headers and exploited native Windows utilities like rundll32.exe and cmd.exe. The shift in tactics—particularly the use of masquerading techniques and evasion strategies—highlights the group’s evolution from hacktivist motives toward more structured espionage and financial objectives. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these phishing campaigns.
- Block or sandbox all .lnk, polyglot ZIP and archive-within-archive attachments.
- Inspect and rewrite or block cloud-hosted links (Google Drive, Netlify) via a secure URL proxy.
- Enforce strict DMARC/DKIM/SPF policies to reduce successful spear-phishing delivery.
- Disable or sandbox VBA macros, VBS and embedded PowerShell by default.
- Enable Constrained Language Mode for PowerShell, and enforce AppLocker or Windows Defender Application Control policies to prevent unsigned scripts from executing.
- 67 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the DoNot APT Group include but are not limited to the following:
- Monitor for creation of new scheduled tasks named “PerformTaskMaintain” or “MicorsoftVelocity” on endpoints receiving email attachments.
- Monitor for execution of unfamiliar executables (notflog.exe) dropped into %TEMP% followed by BAT script launches.
- Monitor for runtime behaviors indicative of in-memory string decryption or dynamic API resolution in unknown processes.
TTPs related to the China-Aligned Espionage Actors include but are not limited to the following:
- Monitor for archive extractions that spawn .lnk→VBS loader chains (Store.vbs) and subsequent DLL sideloads in javaw.exe/jli.dll or CiscoCollabHost.exe/CiscoSparkLauncher.dll.
- Monitor for creation of scheduled tasks such as “SystemHealthMonitor” invoking unsigned or unexpected DLLs.
- Monitor for non-browser processes making Google Sheets API calls for signs of covert C2 use.
TTPs related to the Rainbow Hyena “PhantomRemote” include but are not limited to the following:
- Monitor for decompression of polyglot ZIPs that contain both a decoy document and embedded .lnk file.
- Monitor for invocations of rundll32.exe loading DLLs from %PROGRAMDATA%\YandexCloud or %PROGRAMDATA%\MicrosoftAppStore.
- Monitor for HTTP POST submissions to /result endpoints carrying command outputs from endpoints.
Tags: Threat Actor: DoNot APT Group, China-aligned clusters (UNK_FistBump, UNK_DropPitch, UNK_SparkyCarp), ainbow Hyena hacktivist cluster | Target Sector: Government / Diplomatic (Ministry of Foreign Affairs), Semiconductor manufacturing / Technology, Varied industries (logistics, corporate) | Target Location: Southern Europe, Taiwan, Global | Target Systems: Windows endpoints, Windows workstations/servers in semiconductor environments | Target Platforms: Microsoft Windows
Escalation of Emerging Ransomware and RaaS Group
(Originally published in July 2025)
| DEVMan Ransome | A newly observed ransomware strain named DEVMan builds upon the DragonForce codebase but introduces its own distinct features. It appends a [.]DEVMan extension to encrypted files and uses static, deterministic ransom notes in each attack. While operating offline by default, it has limited capability to propagate across the network via SMB. Before encrypting data, DEVMan avoids backup files and shadow copies to maximize impact. It supports three encryption modes—comprehensive full‑file encryption, a faster header‑only option, or a custom stealth mode designed to balance speed and effectiveness. Additionally, DEVMAN leverages the Windows Restart Manager to unlock the files and stores session metadata in the Windows registry to maintain operational state. |
| KAWA4096 Ransomware | KAWA4096 is a newly identified ransomware strain that surfaced in June 2025, primarily targeting organizations in the United States and Japan with at least 11 known victims so far. KAWA4096’s ransom note closely mimics with Qilin ransomware, while its leak site emulates Akira’s ransomware. It employs multi-threaded execution to accelerate file encryption and extend its impact across shared network drives. Upon execution, the ransomware re-launches itself with the whole parameter to ensure full functionality, creates a mutex to enforce single-instance execution, and terminates predefined processes and services. KAWA4096 deletes shadow copies using Windows Management Instrumentation. Post-encryption, it modifies the victim’s desktop wallpaper to a plain black screen and alters the icons of encrypted files to resemble those of the SQL Monitor application. |
| Dark 101 Ransomware | The Dark 101 ransomware represents a sophisticated evolution in ransomware landscape, leveraging an obfuscated .NET binary to execute a multi-stage attack that maximizes system disruption and maintaining persistence. It begins with environmental reconnaissance to evade sandboxing, copies itself into the %AppData% directory as svchost.exe, and disables recovery options by deleting Volume Shadow Copies and the Windows Backup catalog. It modifies the registry setting to disable Task Manager. Encrypted files are appended with randomly generated four-character extensions, and ransom notes titled read_it.txt, demanding ransom in Bitcoin for decryption. |
| NailaoLocker Ransomware | A newly identified Windows ransomware variant named NailaoLocker, employs a stealthy technique by embedding its malicious payload within a legitimate diagnostic tool, usysdiag.exe to evade detection. NailaoLocker executes its payload directly in memory to reduce its forensic footprint. It avoids critical directories such as Windows and Program Files while scanning and selectively targets user’s sensitive data for encryption using AES-256 in CBC mode, appending a [.]locked extension to each encrypted file. NailaoLocker drops a plain text ransom note in every affected directory, demand payment in cryptocurrency in exchange of decryption key. Notably, the ransomware embeds a hardcoded SM2 elliptic curve key pair and includes an undocumented cheese password that trigger an internal recovery feature. |
| Interlock Ransomware | A joint advisory has been issued on financially motivated ransomware operation named Interlock ransomware, targeting businesses and critical infrastructure in North America and Europe. The group employs drive-by downloads from compromised websites and ClickFix social engineering lure to deliver payloads, deploying PowerShell based RAT that maintain persistence through the Windows Startup folder or registry modifications. Interlock operators exfiltrate system information and credentials using custom stealers and keyloggers, and enable lateral movement using RDP, AnyDesk, and PuTTY. Notably, they encrypt virtual machines (Windows and Linux) using hybrid AES-RSA scheme and appending filenames with [.]interlock or [.]1nt3rlock. Victims receive a !README!.txt ransom note via Group Policy, instructing them to contact over Tor for payment and data recovery instructions. |
| Chaos RaaS Group | A newly emerged RaaS group called Chaos has been active since February 2025. It initiates attacks through voice-based social engineering and phishing tactics to deploy RMM tools such as AnyDesk and ScreenConnect, establishing persistent access across compromised networks. Chaos employs advanced methods to encrypt local and remote files, appending [.]chaos extension and deleting shadow copies to prevent recovery. The group mainly targets organizations in the technology, manufacturing, and professional services sectors, especially in the U.S. and several other regions, threatening to leak stolen data or launch DDoS attacks. |
| Pay2Key RaaS | The Iranian-backed Pay2Key RaaS operation resurfaced with a renewed focus on targeting Western organizations and critical infrastructure. This group operates under the name Pay2Key.I2P and is linked to the Fox Kitten APT group, allowing affiliates to retain up to 80% of ransom payments. The operation has expanded to support Linux-compatible payloads alongside its existing Windows variants. Attacks are deployed via self-extracting 7-Zip archives that run dual CMD/PowerShell scripts, stealthily disabling Windows Defender and unpacking encrypted components. Additionally, the operators have publicly shared evidence of payouts, victim identifiers, and antivirus bypass demonstrations. |
| Global Group RaaS | The emergence of a new RaaS group called GLOBAL GROUP, promoted on the Ramp4u underground forum by a Russian-speaking actor known as $$$. It is believed to be rebranding of the BlackLock RaaS operation, offering its affiliates 85% revenue share and operates a Tor-hosted leak site for publishing exfiltrated data. GLOBAL GROUP significantly made headlines by compromising 17 victims across various sectors such as healthcare, manufacturing and business services in the United States, United Kingdom, Australia, and Brazil. They rely on Initial Access Brokers to infiltrate networks and employ brute-force tools against Microsoft Outlook and RDWeb portals. Notably, the group leverages AI-driven chatbots to handle ransom negotiation and can impact both Windows and Linux environments, including virtual machine deployments. |
Threat Labs summary
- Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these Ransomware and RaaS Groups
- Enforce strong patch management on remote access and browser platforms, particularly Chrome and Edge, to close the ClickFix and browser exploit pathways.
- Disable Windows Management Instrumentation (WMI) and vssadmin functionality to prevent anti-recovery operations.
- Ensure endpoints and virtual infrastructure are protected by EDR to detect unusual file-encryption activity (ChaCha20 routines).
- Isolate critical assets (ESXi hosts, domain controllers) into separate zones and apply strict firewall rules to limit lateral movement.
- Disable Volume Shadow Copy Service (VSS) usage except on designated backup servers.
- Require MFA on all remote-access interfaces and admin accounts to mitigate stolen credential reuse.
- 89 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the DEVMan Ransomware group include but are not limited to the following:
- Monitor for creation of newly encrypted files with [.]DEVMAN extension.
- Monitor for readme.txt files which are renamed to e47qfsnz2trbkhnt.devman.
- Monitor for the temp session – HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000.
- Monitor for creation of mutex hsfjuukjzloqu28oajh727190
TTPs related to the KAWA4096 Ransomware include but are not limited to the following:
- Monitor for process execution commands (vssadmin.exe and wmic.exe) for deleting shadows and shadow copies.
- Monitor for creation of the mutex named SAY_HI_2025.
- Monitor for unexpected DNS or direct connections to the Tor C2 hostname with onion domains.
- Monitor for SERVICE_CONTROL_STOP command events spawning or stopping services.
TTPs related to the Dark 101 ransomware include but are not limited to the following:
- Monitor for the creation of ransom note files such as read_it.txt across any directory.
- Monitor for execution of vssadmin, wmic, and wbadmin which are abused to disable or delete shadow copies.
TTPs related to the NailaoLocker Ransomware include but are not limited to the following:
- Monitor for files with [.]locked extension.
- Monitor for the execution of usysdiag.exe, senspai.dll, usysdiag.exe.dat which collectively comprise the ransomware delivery bundle.
- Monitor for the creation of mutex – lockv7.
- Monitor for the creation or modification of %ProgramData%\lock.log, as it contains plaintext status messages generated in real time by the ransomware during execution.
TTPs related to the Interlock Ransomware include but are not limited to the following:
- Monitor for cht.exe and conhost.txt files which are used for credential stealer and Keylogger.
- Monitor for files which are appended with either a [.]interlock or [.]1nt3rlock file extension.
- Monitor for ransom note file titled !__README__!.txt
TTPs related to the Chaos RaaS include but are not limited to the following:
- Monitor for files which append with [.]chaos extension.
- Monitor for RMM tools such AnyDesk, ScreenConnect, Splashtop for establishing persistent connection to the victim network.
- Monitor for command of vssadmin for volume-shadow copy deletion.
Tags: Ransomware Group: DEVMan Ransomware, KAWA4096 Ransomware, Dark 101 ransomware, NailaoLocker Ransomware, Interlock ransomware, Chaos RaaS, Pay2Key RaaS, GLOBAL GROUP | Target Locations: United States and Japan, North America, Europe, United Kingdom, Australia, and Brazil| Target Sectors: Healthcare, manufacturing, business services, critical infrastructure, technology, manufacturing, and professional services.
Malware Activity: Campaigns, Variants & Trends
(Originally published in July 2025)
| Batavia Spyware Steals Data from Russian Organizations | A targeted spyware campaign dubbed Batavia emerged, focusing on Russian industrial enterprises. Delivered via spear-phishing emails disguised as contract-related communications, the attack unfolds in three stages: a malicious VBS downloader script, a Delphi-based WebView.exe module, and a C++-based javav.exe module. Together, these components collect and exfiltrate sensitive files—including office documents, system logs, screenshots, and additional file types—while employing techniques to avoid duplicate transfers. The malware also supports downloading extra payloads, changing C2 servers, and using UAC bypass methods for persistence. By June 2025, over 100 users across several dozen organizations had been targeted. |
| New Progress of “Silver Fox” | A new variant of the “Silver Fox” remote-control trojan, which employs multiple rootkit drivers, InfinityHook kernel hooking, and kernel read/write penetration to evade detection and disable security software. Distributed via counterfeit software download pages, the malware uses leaked and expired driver signatures to load malicious drivers, hide processes and network activity, and terminate antivirus processes. It achieves persistence through concealed scheduled tasks, executes a “WinOS” remote control module for long-term control and data theft, and leverages open-source projects for stealth. |
| GhostContainer Backdoor for Exchange Servers | A new malware discovered “GhostContainer” (aka NightEagle), a highly modular .NET backdoor targeting Exchange servers—likely via CVE-2020-0688. The attackers deploy a malicious App_Web_Container_1.dll into the Exchange web root, which launches a Stub class that bypasses AMSI, leverages ASP.NET machine keys for AES-encrypted communications, and supports shellcode execution, file operations, and dynamic .NET module loading. A “virtual page injector” class creates ghost ASPX endpoints on demand, while a custom web-proxy/tunneling class (based on Neo-reGeorg) enables HTTP(s) proxying and TCP tunnels entirely over normal Exchange requests—leaving no external C2 artifacts. Two high-value targets (a government agency and a tech firm) in Asia have been identified. |
| HazyBeacon’s Novel Covert C2 via AWS Lambda URLs | HazyBeacon, an undocumented Windows backdoor that achieves persistence through DLL sideloading of mscorsvc.dll alongside the legitimate mscorsvw.exe service. Upon service start, the malicious DLL beacons to an AWS Lambda URL endpoint—hiding C2 traffic within legitimate amazonaws.com requests. The actor then issues commands to run arbitrary payloads and to exfiltrate collected data via Google Drive and Dropbox clients installed under C:\ProgramData. Persistence is ensured by creating a “msdnetsvc” Windows service. |
| Hpingbot: A New Pastebin-Driven Botnet with hping3 DDoS Module | Hpingbot, first seen June 2025, is a Go-based cross-platform botnet (Windows/Linux/IoT) that uses Pastebin to host payload URLs and hping3 as its DDoS engine. While DDoS activity (mostly against Germany, the U.S, and Turkey) has been sporadic, its core value lies in a generic payload-download-and-execute capability: embedded Pastebin links point to download scripts (payload.sh) with German comments that self-update by architecture, install via curl/wget, and establish persistence through Systemd, SysVinit, and cron. The botnet’s commands (e.g., SYN, ACK floods) map directly to hping3 parameters, and its rapid iteration—frequent C&C rotations and script revisions—suggests a professional team behind it. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these malicious campaigns.
- Enable code-signing enforcement for kernel drivers and use Kernel PatchGuard or equivalent to detect InfinityHook techniques.
- Fully patch CVE-2020-0688 and restrict write permissions on the Exchange web root.
- Implement allow-listing or strict proxy policies for AWS Lambda endpoints to prevent HazyBeacon beacons.
- Block or proxy access to Pastebin and other public script hosts; inspect outbound HTTP(S) for payload‐fetch patterns.
- Enforce application allow-lists and disable unnecessary scripting engines (Windows Script Host for .vbe).
- 25 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Batavia spyware include but are not limited to the following:
- Monitor for downloads of .vbe script files from unfamiliar or untrusted domains.
- Monitor execution of VBS scripts that retrieve parameters or payloads from external C2 servers.
- Monitor for creation and execution of files named WebView.exe, javav.exe, or similarly unusual executables in %TEMP% or %PROGRAMDATA% directories.
- Monitor for the creation of hash-tracking files like h12 in %TEMP% to identify repeated file exfiltration prevention mechanisms.
- Monitor for creation of persistence mechanisms via .lnk shortcuts in the Windows Startup folder.
- Monitor registry modifications linked to UAC bypass techniques, especially involving ms-settings\Shell\Open\command.
TTPs related to the new progress of “Silver Fox” include but are not limited to the following:
- Monitor the loading of kernel drivers with leaked, expired, or untrusted digital signatures.
- Monitor attempts to hook or modify kernel APIs such as NtQuerySystemInformation, NtOpenProcess, or NtDuplicateObject.
- Monitor changes to nsiproxy.sys driver callbacks that alter or hide network connection data.
- Monitor the creation or execution of files in unusual system paths such as C:\Users\Public\Documents\WindowsData.
- Monitor scheduled task creation via uncommon methods like WdcRunTaskAsInteractiveUser.
TTPs related to the GhostContainer backdoor include but are not limited to the following:
- Monitor for unusual modifications to Exchange server files, especially the presence of App_Web_Container_1.dll or similarly named suspicious DLLs.
- Monitor for AMSI and Windows Event Log tampering, such as memory patching in amsi.dll or ntdll.dll.
- Monitor for suspicious use of ASP.NET machine keys or unusual cryptographic operations for AES encryption/decryption in Exchange processes.
- Monitor for requests containing anomalous or custom HTTP headers such as x-owa-urlpostdata, Qprtfva, or Dzvvlnwkccf.
- Monitor for creation of virtual ASPX pages or execution of Base64-encoded .aspx payloads within Exchange services.
- Monitor for execution of shellcode, arbitrary .NET bytecode, or direct command execution initiated from Exchange web requests.
- Monitor for unauthorized file read/write/delete actions, particularly involving App_Global directories.
TTPs related to the HazyBeacon’s Novel include but are not limited to the following:
- Monitor creation or execution of unauthorized DLL files in system directories, especially C:\Windows\assembly\mscorsvc.dll.
- Monitor for unusual execution of legitimate Windows binaries (mscorsvw.exe) loading non-Microsoft DLLs.
- Monitor creation of new or suspicious Windows services, such as msdnetsvc, for persistence.
- Monitor outbound connections to AWS Lambda URLs, especially those in the ap-southeast-1 region or unknown AWS accounts.
- Monitor file creation in C:\ProgramData\ involving tools like 7z.exe, igfx.exe, GoogleGet.exe, google.exe, GoogleDrive.exe, GoogleDriveUpload.exe, or Dropbox.exe
- Monitor processes performing targeted file searches for sensitive keywords such as “tariff,” “trade,” or political communications.
TTPs related to the Hpingbot include but are not limited to the following:
- Monitor for installation or execution of the hping3 network testing tool outside of authorized administrative activities.
- Monitor for repeated SSH login attempts or brute-force activity targeting multiple architectures (amd64, mips, arm, 80386).
- Monitor for creation or modification of Systemd, SysVinit, or Cron jobs that establish unauthorized persistence.
- Monitor for unexpected download and execution of shell scripts (payload.sh) from untrusted external IP addresses.
- Monitor for execution of mixed-mode DDoS traffic patterns (SYN flood, ACK flood, UDP flood) originating from internal hosts.
Tags: Threat Actor: Batavia, Silver Fox operators, GhostContainer (aka NightEagle), HazyBeacon operators, Hpingbot operators | Target Sector: Russian enterprises & critical infrastructure, Software development / IT infrastructure, Government, Enterprise, Telecom, Finance | Target Location: Russia, Global, Asia, Southeast Asia, Germany, U.S, Turkey | Target Systems: Windows endpoints, Windows OS (kernel‐level), Microsoft Exchange servers, Windows services, IoT devices, Windows, Linux.
Tomcat Partial PUT Deserialization
(Originally published in July 2025)
A critical flaw in Apache Tomcat’s “partial PUT” handler tracked as CVE-2025-24813 has become one of the loudest security stories this July. The bug lets an attacker upload a rogue .session file via a PUT request that includes a crafted Content-Range header; when Tomcat later restores that session, it deserializes the object and executes arbitrary code with the server’s privileges. Every active Tomcat branch (9.0, 10.1 and 11.0) is affected, and opportunistic scanners have already generated well over 125 thousand probes from more than 70 countries, proving how quickly the exploit has entered commodity toolchains.
The attack is a two-step affair: first, the adversary issues PUT /<rand>.session with a Content-Range: bytes 0-452/457 header to plant the payload; seconds later they send any request bearing Cookie: JSESSIONID=.<rand>, which tricks Tomcat into loading and running the malicious session file. Successful exploitation hinges on common default settings (readonly=”false” and persistent sessions), making internet exposed servers easy targets. Most live attempts reuse the same six-character filenames and header values found in the public Nuclei template, a clear sign that scripted mass scanning is driving the campaign.
Applying the newly released Tomcat patches (or upgrading to the fixed builds) is the definitive fix; short of that, re enable readonly, disable partial PUT if it’s not a business requirement, and watch for the unmistakable .session uploads coupled with the Content-Range header. Network defenders running Palo Alto NGFWs can also block traffic with Threat-Prevention signature 96315 while patching rolls out.
Threat Labs summary
Securonix Threat Labs Recommends leveraging these findings to strengthen defenses against these malware campaigns.
- Upgrade to Tomcat 9.0.99 / 10.1.35 / 11.0.3 or later.
- Disable partial PUT and turn it off or block the Content-Range header unless truly required.
- Set readonly=”true” for sessions – prevents attacker-supplied .session files from being written.
- Validate range headers and drop suspicious Content-Range values such as bytes 0-452/457.
- Restrict HTTP verbs and allow only methods your app needs; block PUT, DELETE, etc. at the edge.
- Run under least privilege and ensure the Tomcat service account can’t spawn shells or write broadly.
- Isolate the service and place Tomcat behind a reverse proxy or run it in a container/DMZ.
- 33 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Tomcat Partial PUT Deserialization include but are not limited to the following:
- Monitor for HTTP PUT requests carrying filenames that end in .session and include a Content-Range header.
- Monitor for Content-Range: bytes 0-452/457 values.
- Monitor for follow-up requests with Cookie JSESSIONID=.<name>.
- Monitor for Apache Camel traffic for mixed-case headers such as CAmelExecCommandExecutable, CAmelExecCommandArgs, CAmelBeanMethodName, CAmelHttpResponseCode – header hijack relies on these variants to slip past the default filter.
- Monitor for six-character filenames or session IDs appended with .session.
Tags: Target System: Apache Tomcat | CVE Exploited: CVE-2025-24813, CVE-2025-27636, CVE-2025-29891 | Target Location: Global | Payload: Reverse shells, DNS/OAST beacons |Tactic: Remote Code Execution
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Dheeraj Kumar, and Sina Chehreghani







