- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
- MSSPs
- Scale multi-tenant security with predictable economics.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Nitish Singh, Nikhil Kumar Chadha, and Tanmay Kumar
The Monthly Intelligence Insights report provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in November 2025. The report also includes a synopsis of the threats, indicators of compromise (IoCs), tactics, techniques, and procedures (TTPs), and related tags. Each threat has a comprehensive summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below-mentioned threats, refer to our Threat Labs home page.
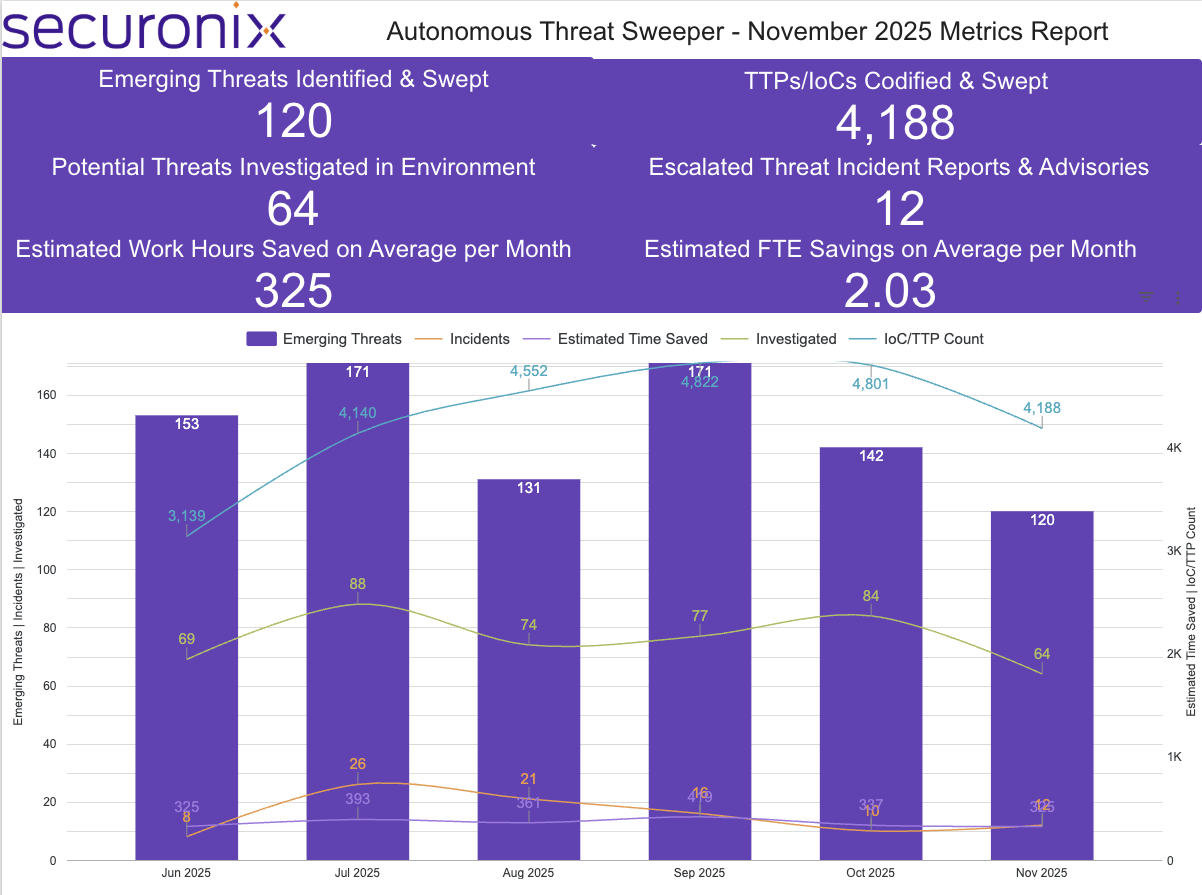
Last month, Securonix Autonomous Threat Sweeper identified and analyzed 4,188 TTPs and IoCs; identified 120 emerging threats; investigated 64 potential threats; and elevated 12 incidents. The top data sources swept against include IDS / IPS / UTM / Threat Detection, Data Loss Prevention, Endpoint Management Systems, and Email / Email Security.
In November 2025, the Autonomous Threat Sweeper team observed a broad escalation in global cyber activity marked by state-backed espionage, credential theft, cloud intrusion, and aggressive ransomware operations. Key campaigns included Operation SkyCloak, Peek-a-Baku in Central Asia, MuddyWater’s Phoenix v4, SmudgedSerpent’s Iranian credential harvesting activity, and Lazarus deploying a new Comebacker variant, along with continued targeting from UNC1549 across aerospace and defense. Threat actors expanded their malware ecosystems with Kinsing exploiting ActiveMQ for backdoor deployment, NotDoor abusing Outlook for C2 and persistence, COLDPRIVER rolling out its latest toolset, and TruffleNet driving large-scale cloud credential abuse, while CHAMELEON#NET pushed FormBook through DarkTortilla. The month also saw a jump in AI-enabled malware and macOS infections distributed through malicious AppleScript, deepening attacker automation. Ransomware pressure increased with new Kraken variants, ongoing Akira attacks, the Lynx intrusion campaign, and the reemergence of ShadowRay 2.0, reinforcing how quickly adversaries are combining AI, cloud exploitation, and identity-focused techniques to accelerate intrusions.
Key Highlights of Recent APT Campaigns
(Originally published in November 2025)
| Lazarus Group: Comebacker Variant | A new espionage campaign linked to the North Korea–aligned Lazarus Group is targeting aerospace and defense organizations. Since early 2025, the group has been distributing malicious Word documents themed around well-known aerospace and academic entities to deliver a multi-stage variant of the Comebacker backdoor. The infection chain uses VBA-based droppers, DLL loaders and ChaCha20/AES encryption to hide payloads and support encrypted HTTPS communication. Researchers note refinements compared to earlier versions, including more polished multi-layer loaders and spear-phishing lures that closely resemble legitimate defense paperwork. |
| Iranian Activity Cluster UNK_SmudgedSerpent | A newly identified Iran-aligned phishing and remote-management abuse cluster active from June to August 2025 targeted U.S. academics and policy experts focused on Iran by posing as researchers from well-known think tanks. The operators used convincing OnlyOffice and Microsoft 365 login spoofs to steal credentials and then deployed remote-management tools such as PDQConnect and ISL Online to gain persistent access. Analysis shows technique overlap with several established Iranian groups, including those commonly linked to Charming Kitten, Smoke Sandstorm and MuddyWater, pointing to shared contractors or tooling rather than a single unified actor. The reuse of themed infrastructure and recruitment-style decoys reflects the increasingly blended nature of Iran’s contractor-driven espionage ecosystem. |
| MuddyWater: Phoenix v4 Backdoor | An Iran-aligned phishing campaign attributed to the group commonly known as MuddyWater has been targeting government agencies across the Middle East and North Africa with an updated Phoenix v4 backdoor. The attackers used macro-enabled Word documents sent from compromised mailboxes accessed through commercial VPN services. These documents delivered a FakeUpdate-style injector that decrypted Phoenix, set persistence through Winlogon registry changes and established encrypted command-and-control communication. After gaining a foothold, the operators used Chromium-based credential stealers and legitimate remote-management tools such as PDQ and Action1 to maintain long-term access. The backdoor exfiltrates browser passwords and system information, reinforcing the group’s broader intelligence-gathering objectives. |
| Operation SkyCloak | A 2025 campaign known as Operation SkyCloak targeted Russian and Belarusian military networks using Tor-enabled backdoors. The operation relied on spear-phishing ZIP files containing LNK shortcuts disguised as official military documents, which launched PowerShell stagers that installed OpenSSH servers and obfs4 Tor bridges for covert communication. The tooling exposed local SSH, RDP and SMB services through hidden onion endpoints and maintained persistence through scheduled tasks. The lures referenced real military units, including the 83rd Airborne Brigade in Russia and the 5th Spetsnaz Brigade in Belarus. |
| Operation Peek-a-Baku | Recent research outlines two connected espionage waves carried out by the group often referred to as Silent Lynx (also known as YoroTrooper or Cavalry Werewolf) across Central Asia, Russia and China. The operators delivered RAR archives containing malicious LNK files and PowerShell loaders hosted on public code platforms, pulling down reverse shells and implants such as Silent Loader, Laplas and SilentSweeper. One wave in October 2025 targeted Russia–Azerbaijan diplomatic missions around the Dushanbe summit, while an earlier wave in September 2025 focused on the China–Central Asia Summit in Astana. Both relied on Base64-encoded PowerShell payloads, Ligolo-ng tunneling and scheduled-task persistence, reflecting steady refinement despite recurring OPSEC errors. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these APT group’s campaigns.
- Implement strict attachment and macro-blocking policies for Office files, especially those referencing aerospace or defense entities.
- Prevent execution of VBA macros in downloaded documents unless digitally signed and verified.
- Encourage manual verification of sender identities for unsolicited collaboration requests, especially those imitating think-tank or policy experts.
- Regularly inspect Winlogon registry keys for unauthorized shell modifications and persistence artifacts.
- Enforce browser password encryption and disable automatic credential storage where possible.
- Deny or closely monitor Tor bridge and onion network connections, especially those involving obfs4 proxies or port 20321.
TTPs related to the Lazarus Group: Comebacker Variant include but are not limited to:
- Monitor for execution of VBA macro code performing file writes to uncommon paths such as:
- C:\ProgramData\WPSOffice\wpsoffice_aam.ocx
- C:\ProgramData\Document\EDGE_Group_Interview_NDA.docx
- Monitor for creation of shortcut (.lnk) files in user Startup folders that execute rundll32.exe with DLLs located in:
- C:\ProgramData\USOShared\USOPrivate.dll
- Monitor for suspicious entries under:
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- Startup folder modifications referencing non-standard DLL paths.
- Monitor for use of rundll32.exe executing non-standard DLLs such as USOPrivate.dll or USOInfo.dat with unusual export names (LoadMimi, GetWindowSizedW, GetSysStartTime).
- Monitor for processes using ChaCha20, AES-128-CBC, or HC256 encryption libraries for runtime decryption of payloads
TTPs related to the MuddyWater: Phoenix v4 Backdoor include but are not limited to the following:
- Monitor for processes named FakeUpdate or similar loader activity performing AES decryption and writing secondary payloads to disk.
- Monitor for creation or execution of binaries matching the Phoenix backdoor pattern (sysprocupdate.exe) in C:\ProgramData.
- Monitor for registry modifications under HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon — especially changes to the Shell value.
- Monitor for creation of mutexes named sysprocupdate.exe or other unique synchronization objects.
- Monitor for suspicious file creation such as C:\Users\Public\Downloads\cobe-notes.txt containing encrypted credentials.
TTPs related to the Operation SkyCloak include but are not limited to the following:
- Monitor for PowerShell commands extracting files to unusual directories such as:
- %APPDATA%\dynamicUpdatingHashingScalingContext
- %USERPROFILE%\Downloads\incrementalStreamingMergingSocket
- Monitor for legitimate binaries renamed and executed from unexpected paths such as:
- githubdesktop.exe, googlemaps.exe, ssh-shellhost.exe, ebay.exe, libcrypto.dll, confluence.exe, and rider.exe located in %AppData%\logicpro or %AppData%\reaper.
TTPs related to the Operation Peek-a-Baku include but are not limited to the following:
- Monitor for creation or execution of binaries named silent_loader.exe or similar loaders using CreateProcessW to spawn new PowerShell instances.
- Monitor for .NET executables that extract and execute embedded PowerShell payloads (parameters like -extract or -debug), indicating SilentSweeper activity.
- Monitor for creation of scheduled tasks named “WindowsUpdate” or similarly benign names running every few minutes (/sc minute /mo 6).
- Monitor for PowerShell or VBScript files written to temporary user directories (AppData\Local\Temp\WindowsUpdateService.ps1 and .vbs) followed by task creation.
- Monitor for TLS or TCP-based C2 traffic using self-signed certificates, irregular beacon intervals, or repeating strings such as “HELLO, Press Enter.” or “Goodbye.” (Laplas implant signatures).
- Monitor for processes masquerading as legitimate system binaries (WindowsUpdateService.ps1, WindowsUpdateService.vbs).
- Monitor for PowerShell scripts or executables hosted in user cloud folders such as OneDrive\Рабочий стол or Desktop, as indicated by LNK metadata.
Tags: Threat Actor: Lazarus Group (DPRK-linked APT), UNK_SmudgedSerpent, MuddyWater (a.k.a. Static Kitten, Seedworm, TA450), Silent Lynx APT | Target Sector: Aerospace, Defense, Research Institutes, Academia, Think Tanks, Policy Research, Government Analysts, Energy, and Diplomatic Institutions, Military, Government (Russian Airborne Forces, Belarusian Special Forces), Diplomacy, Transportation, Communications, Mining | Target Location: India, UAE, Europe (Airbus, IIT Kanpur, Edge Group), United States, Israel, possibly EU policy circles, Middle East and North Africa (MENA), Russia, Belarus, Central Asia (Tajikistan, Kazakhstan, Azerbaijan), Russia, China | Malware / Family: Comebacker (New Variant), Phoenix Backdoor v4, FakeUpdate Injector, Custom PowerShell Stager; Tor-based SSH backdoor, Silent Loader, Laplas, SilentSweeper, Ligolo-ng Tunnel | Target Platforms: Microsoft Office (Word), Windows OS, Email (Gmail, Outlook), Web (Phishing pages), Microsoft Word (macro-based), Windows Registry (Winlogon persistence), PowerShell, Tor Network, SSH/SFTP Services, PowerShell, VBScript, .NET Framework | Adversary Location: North Korea, Iran, Central or Eastern Europe
Active Malware Operations
(Originally published in November 2025)
| CHAMELEON#NET: A Deep Dive into Multi-Stage .NET Malware | Securonix Threat Research released an analysis of CHAMELEON#NET, a DarkTortilla-delivered .NET malware campaign that distributes FormBook RAT through malspam targeting national social security agencies. The attack starts with a phishing email that leads to a .BZ2 archive containing a multi-stage JavaScript dropper, which installs a VB.NET loader (QNaZg.exe) that uses conditional XOR encryption and reflective loading to run FormBook directly in memory, enabling fileless persistence. Once active, FormBook performs keylogging, credential theft, and command-and-control activity while disguising itself under system-like process names. The malware also uses anti-sandbox delays, attempts to disable Windows Defender, and maintains persistence through registry changes and startup folder entries. |
| MacOS Infection Vector | A new wave of macOS malware campaigns that rely on AppleScript (.scpt) files to sidestep Gatekeeper protections. After Apple removed the ‘right-click to open’ override in 2024, threat actors began using AppleScripts disguised as documents or installers, such as ‘Zoom SDK Update.scpt’ or ‘Investment Proposal.pptx.scpt,’ to trick users into opening them through Script Editor and bypassing quarantine checks. Recent campaigns linked to stealer families like MacSync and Odyssey use this method, showing how techniques once tied to advanced threat groups are now appearing in everyday commodity malware. |
| Rise of the AI-Enabled Malware | The research outlines the rise of AI-enabled malware families that use large language models to modify themselves on the fly. Notable examples include PROMPTFLUX, PROMPTSTEAL, PROMPTLOCK, FRUITSHELL, and QUIETVAULT. PROMPTFLUX relies on external AI services for code obfuscation and persistence, while PROMPTSTEAL, tied to state-linked activity, uses embedded AI models to generate reconnaissance and data-theft commands in real time against targeted systems. PROMPTLOCK showcases AI-generated, cross-platform ransomware capable of producing its own encryption scripts. QUIETVAULT is notable for autonomous data exfiltration, abusing local command-line AI tools to locate and extract credentials and configuration files. |
| Cloud Abuse at Scale | The analysis describes a large-scale cloud credential abuse operation built around an attacker-controlled framework that automates reconnaissance and email service misuse. Stolen cloud keys were validated across hundreds of hosts through identity and quota checks before being leveraged for Business Email Compromise activity. The attackers used hijacked web infrastructure to forge email identities and send convincing corporate-themed lures, including fake onboarding and payment-related messages. The campaign relied on containerized systems managed through a centralized dashboard, along with staged identity creation and impersonation techniques to support the fraudulent activity. |
| COLDRIVER Updates Its Arsenal | The investigation outlines how COLDRIVER (also known as UNC4057 or Star Blizzard), a Russian state-sponsored group, quickly shifted tactics after its earlier malware was exposed. The updated toolkit includes the NOROBOT, YESROBOT, and MAYBEROBOT families. NOROBOT is a malicious DLL delivered through a CAPTCHA-themed lure that downloads follow-on payloads and hides its activity with cryptographic obfuscation. YESROBOT, a Python backdoor, was soon replaced by MAYBEROBOT, a PowerShell version that offers broader command execution and persistence options. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these malware campaigns.
- Disable or restrict execution of .js, .vbs, and .bz2 attachments in email gateways to prevent multi-stage dropper initiation.
- Implement EDR analytics capable of recognizing in-memory execution through .NET reflection (AppDomain.Load(byte[])) or late binding.
- Configure macOS systems to open .scpt, .applescript, and .scptd files using TextEdit or a non-executable viewer by default, preventing direct execution through Script Editor.
- Enable Finder’s “Show all filename extensions” setting globally to help users spot hidden or deceptive double extensions such as .docx.scpt or .pptx.scpt.
- Monitor for unusual outbound traffic to LLM-related APIs (Gemini, Hugging Face, OpenAI) from non-development environments.
- Revoke unused API credentials and restrict valid keys to authorized services or networks.
- Regularly audit AWS IAM roles and credentials to ensure users and services only have the permissions they require.
- Deploy anomaly-based detection for unusual AWS API activity, including repeated GetCallerIdentity, GetSendQuota, or CreateEmailIdentity calls.
- Block execution of DLLs and other script-based payloads delivered via “ClickFix” or CAPTCHA-themed phishing lures.
- 60 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the CHAMELEON#NET include but are not limited to the following:
- Monitor for phishing emails containing compressed archives (.BZ2) that deliver JavaScript-based droppers such as POP2.js.
- Monitor for downloads of files named suspiciously (81__POP1.BZ2, PROOF OF PAYMENT1.vbs, POP2.js) from unknown or untrusted domains.
- Monitor for execution of JavaScript or VBScript files (.js, .vbs) from the %TEMP% directory using wscript.exe or cscript.exe.
- Monitor for creation of new JavaScript files in %TEMP% with names resembling legitimate services (adobe.js, svchost.js).
- Monitor for ADODB.Stream and Microsoft.XMLDOM objects being instantiated in scripts, these are used for Base64 decoding and writing malicious binaries to disk.
- Monitor for the execution of dropped binaries via WScript.Shell, especially files like QNaZg.exe.
- Monitor for memory allocation patterns consistent with reflective loading using methods such as System.AppDomain.Load(byte[]).
- Monitor for creation or modification of registry keys under HKCU\Software\Microsoft\Windows\CurrentVersion\Run with value names mimicking legitimate Windows processes (svchost.exe) that reference suspicious executables like word.exe.
- Monitor for new executables placed in %AppData%\Roaming\word\word.exe — especially those masquerading as Microsoft Office files.
- Monitor for execution chains where word.exe spawns administrative or installer utilities such as InstallUtil.exe.
- Monitor for creation of keylogging data files with patterns like KB_*.dat in %AppData%\Roaming.
TTPs related to the MacOS Infection Vector include but are not limited to the following:
- Monitor for execution of .scpt, .applescript, or .scptd files from non-standard directories such as ~/Downloads, ~/Desktop, or /tmp.
- Monitor for Script Editor.app (/Applications/Script Editor.app) launching unexpectedly or running child processes that initiate network connections.
- Monitor for zip or DMG archives containing .scpt files with enticing names like “InstallUpdate.scpt” or “ChromeSetup.scpt”
- Monitor for distribution of ZIP or DMG files via email or chat that contain .scpt payloads using familiar names like “Stable1 Investment Proposal” or “MSTeamsUpdate.scpt”.
TTPs related to the AI-Enabled Malware include but are not limited to the following:
- Monitor for creation or modification of %TEMP%\thinking_robot_log.txt containing LLM-generated script fragments or evasion logic.
- Monitor for creation of C:\ProgramData\info and generation of info.txt containing hardware, process, network, and Active Directory details.
- Monitor for unauthorized modification of shell startup files (~/.bashrc, ~/.zshrc) inserting sudo shutdown -h 0.
TTPs related to the COLDRIVER include but are not limited to the following:
- Monitor for use of bitsadmin to download Python scripts, archives, or similarly named files such as libsystemhealthcheck.py or libcryptopydatasize.py.
Tags: Malware: MacSync Stealer, Odyssey Stealer, PROMPTFLUX, PROMPTSTEAL, PROMPTLOCK, FRUITSHELL, QUIETVAULT, TruffleHog, TruffleNet Infrastructure, Portainer, NOROBOT, YESROBOT, MAYBEROBOT, LOSTKEYS, DarkTortilla Loader, FormBook RAT | Threat Actor: BlueNoroff, APT28, COLDRIVER | Target Sector: Cryptocurrency, Individual macOS Users, Technology Sector, Government, Critical Infrastructure, Academia, IT Services, Cloud Services, Corporate Enterprises, Oil & Gas, Technology, NGOs, Government Policy Advisors, Journalists, Academia | Target Location: Global (notably Asia-Pacific and North America), Ukraine, Europe, Global (AWS environments, focus on U.S. and France-hosted domains), Europe, North America, Asia-Pacific, United States | Target Platforms: macOS Sequoia and later, Python, Go, VBScript, JavaScript, Amazon Web Services (SES, IAM, SNS), Windows 10/11, Microsoft Office environments, .NET Framework | Adversary Origin: North Korea, Russia
Backdoor Activity Highlights
(Originally published in November 2025)
Threat actors continue to use fake utility installers to deliver small but persistent backdoors. A recent case involved a fake PDF editor that quietly dropped helper files, set up a PowerShell updater, and added a scheduled task that checks in once a day. The updater runs basic recon and cycles through several hard-coded endpoints to maintain a low-profile beacon while operators decide their next steps. Recommended actions are simple: isolate impacted hosts, remove the scheduled task and updater, and review the ad or SEO path that led users to the installer.
Some operators then shift their foothold into Outlook. They side-load a DLL through OneDrive.exe, execute encoded PowerShell, and plant a malicious VbaProject.OTM so Outlook runs their code during startup or new mail events. They also modify registry settings to auto-enable macros, lower Outlook’s macro security, and suppress warnings. This allows them to use normal email activity as a quiet C2 channel. Reliable detections highlight suspicious parent and child processes, creation of VbaProject.OTM, Outlook security key changes, and non-Outlook processes writing to the macro store.
We’re also seeing server-side activity where attackers exploit Apache ActiveMQ (CVE-2023-46604) to make a vulnerable broker run msiexec or cmd and fetch a small stager. After gaining execution, they deploy cryptominers such as XMRig and additional remote tools. Recent intrusions also include Sharpire, a .NET backdoor with file, process, and network capabilities similar to an Empire-style tasking model. The campaign targets both Windows and Linux using scripts that fetch architecture-specific payloads, turning an unpatched broker into a lasting entry point for everything from cryptojacking to hands-on operations.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these backdoor activities.
- Only allow software from trusted stores; quarantine ad-driven “utility” installers (fake PDF tools).
- Remove any new scheduled task + updater script pair dropped by the installer; isolate affected endpoints.
- Restrict/disable macros; alert on VbaProject.OTM creation and Outlook macro/security key changes; block OneDrive.exe from loading unsigned/unknown DLLs (WDAC/AppLocker).
- Update Apache ActiveMQ for CVE-2023-46604; remove direct internet exposure; restrict who can reach the broker UI/API.
- If the broker launches shells/installer tools, isolate, remove miner/backdoor payloads, rotate creds, and rebuild from a known-good image.
- 22 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Fake PDF editor include but are not limited to the following:
- Monitor for creation of a new scheduled task immediately after a “utility/installer” runs, with a 12–24h repeat cadence.
- Monitor for a PowerShell updater written to a user-writable path, followed by quick recon and a first outbound check-in.
- Monitor for multiple helper files dropped by the same parent installer within seconds of each other.
TTPs related to the Outlook macro backdoor include but are not limited to the following:
- Monitor for OneDrive.exe loading an unknown DLL (DLL side-loading).
- Monitor for creation or modification of VbaProject.OTM by a non-Outlook process.
- Monitor for encoded PowerShell spawned from OneDrive/Outlook context.
- Monitor for Outlook macro/security registry keys being lowered or toggled to load macros at boot.
TTPs related to the ActiveMQ exploit include but are not limited to the following:
- Monitor for the ActiveMQ service (Java broker) spawning msiexec.exe or cmd.exe shortly after broker HTTP activity.
- Monitor for drop/exec of architecture-specific payloads (Windows/Linux) right after broker exploitation.
- Monitor for new long-running miner processes and .NET backdoor activity (Sharpire) on the broker host.
Tags: Target sectors: Broad enterprise (user workstations), email users across organizations, and server/middleware operators (ActiveMQ) | Target locations: Global | Threat actor: Outlook macro/NotDoor, ActiveMQ exploitation | Malware: Loader→light backdoor (fake utility/PDF editor), Outlook macro backdoor (NotDoor technique), Sharpire (.NET backdoor), XMRig miners | Target systems: Windows workstations (end-user), Microsoft Outlook/OneDrive app context, Apache ActiveMQ brokers | Target platforms: Windows (endpoints), Windows & Linux (servers running ActiveMQ) | Exploited CVE: CVE-2023-46604
Emerging Cyber Campaigns
(Originally published in November 2025)
UNC1549, an Iran-aligned threat group, has intensified its long-running espionage activity against aerospace, aviation, and defense organizations. The group is abusing trusted third-party access and breaking out of Citrix, VMware, and AVD environments. They’re deploying a broad set of tailored backdoors such as TWOSTROKE, MINIBIKE, DEEPROOT, LIGHTRAIL, POLLBLEND, GHOSTLINE, SIGHTGRAB, CRASHPAD, TRUSTTRAP, and DCSYNCER.SLICK. Most payloads are delivered through DLL search-order hijacking of legitimate Fortinet, VMware, Citrix, Microsoft, and NVIDIA executables, which helps them stay hidden, maintain persistence, and evade controls. Their tools support encrypted C2 over Azure Web Apps, reverse SSH tunnels with a small forensic footprint, credential theft through DCSync impersonation and Kerberoasting, browser data extraction, fake login prompts, and detailed reconnaissance using AD Explorer, RDP hijacking, AWRC, and SCCMVNC. They also use unique hashes per victim, valid code-signing certificates, and dormant backdoors that can quietly beacon for months, showing a mature and stealth-focused collection campaign across the aerospace and defense supply chain.
At the same time, the ShadowRay 2.0 operation has grown into a major exploitation campaign targeting AI infrastructure. Attackers are abusing Ray’s disputed CVE-2023-48022 to gain unauthenticated remote code execution across more than 200,000 exposed Ray clusters. They deploy AI-generated, multi-stage payloads that use Ray’s own orchestration features, including NodeAffinitySchedulingStrategy, to self-propagate. The intrusions set up multi-port Python reverse shells, cron and systemd-based persistence, and GPU-tuned cryptominers that pose as system processes like dns-filter or kworker/0:0. They also manipulate iptables and hosts entries to remove competing miners, mask resource consumption from Ray’s monitoring layer, and steal sensitive data such as environment variables, credentials, proprietary AI models, and large NFS-mounted repositories. The operation is supported by GitLab/GitHub CI/CD pipelines, geographic payload variations, protocol tunneling, and automated internet-wide scanning through OAST platforms. ShadowRay 2.0 effectively turns compromised Ray clusters into multi-role botnet nodes for cryptojacking, data theft, rapid propagation, and DDoS, marking a significant shift in cloud-first and AI-platform exploitation techniques.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these threat groups’ campaigns.
- Restrict and harden all third-party access pathways abused by UNC1549, including Citrix, VMware, and Azure Virtual Desktop connections; enforce MFA, limit vendor access scopes, and continuously audit partner credentials.
- Remove footholds established through DLL search-order hijacking by deleting malicious DLLs associated with TWOSTROKE, MINIBIKE, LIGHTRAIL, POLLBLEND, GHOSTLINE, SIGHTGRAB, CRASHPAD, and DCSYNCER.SLICK, and reinstall legitimate vendor software from trusted media.
- Disable unauthorized reverse SSH tunneling and cloud C2 endpoints (Azure Web Apps domains identified in the campaign) and rotate privileged AD, Azure AD Connect, and service account credentials that may have been harvested via DCSync, Kerberoasting, browser extraction, or TRUSTTRAP prompts.
- Isolate any endpoints running compromised Ray clusters targeted in the ShadowRay 2.0 campaign; block unauthenticated exposure of Ray Dashboard/Jobs APIs, enforce network segmentation, and require authentication layers when operating Ray in production environments.
- Remove persistence artifacts associated with ShadowRay 2.0—including cron/systemd loaders, injected .bashrc entries, unauthorized SSH keys, disguised binaries such as dns-filter and .python3.6, and GPU-enabled cryptominer components—and rebuild compromised AI nodes from a known-good baseline.
- Enable GPU, CPU, DNS, and outbound proxy logging for detection of hidden miner activity, OAST-based callback traffic, and anomalous outbound TLS connections to mining pools or GitLab/GitHub infrastructure abused as attacker CI/CD systems.
- 80 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to UNC1549 include but are not limited to the following:
- Monitor for domain controller computer account password resets using net.exe (e.g., net user DC-01$ ), which is uncommon and often breaks DC functionality.
- Monitor for enumeration of logged-in users via quser.exe or wmic.exe, followed by RDP authentication using those accounts.
- Monitor for automated screenshot generation in user-accessible directories (C:\Users\Public\Videos\YYYY-MM-DD) created chronologically.
- Monitor for deletion of forensic artifacts, including Terminal Services registry keys associated with RDP history (HKEY_CURRENT_USER\Software\Microsoft\Terminal Services).
TTPs related to ShadowRay 2.0 include but are not limited to the following:
- Monitor for unauthenticated POST requests to Ray’s Jobs API (/api/jobs/) invoking arbitrary shell commands, curl/wget calls, or reconnaissance commands.
- Monitor for outbound callbacks to OAST domains such as *.oast.fun, especially immediately following job submissions.
- Monitor for Ray jobs that enumerate cluster resources (ray.cluster_resources(), CPU/GPU inventory checks, node listings).
- Monitor for Python processes spawning outbound TCP connections on unusual ports (3876, 40331, 48331, 443) consistent with reverse shells.
- Monitor for creation or modification of cronjobs running every 15 minutes that fetch remote scripts (mon.sh, aa.sh, run.sh).
- Monitor for new systemd/init scripts named deceptively (dns-filter, health-monitor) placed under /etc/init.d/ or /usr/lib/dev/systemdev/.
- Monitor for unauthorized edits to ~/.bashrc injecting downloader or execution commands.
- Monitor for processes renaming themselves by writing to /proc/<pid>/comm, especially to names resembling kernel workers like kworker/0:0.
- Monitor for binaries hidden under dot-prefixed names (.python3.6, .ddns.sh) or nonstandard paths (/tmp/dns, /usr/lib/dev/systemdev/).
Tags: Threat Actor: IronErn440, UNC1549 | Target Sector: AI/ML infrastructure, Cloud compute providers, Aerospace, aviation, defense | Target Location: Global – compromises observed across multiple continents, Middle East (Also victims in Europe, U.S., and global aerospace supply chain) | Malware / Payloads: XMRig cryptominer, Rigel GPU miner, Custom ELF dropper (LZSS compression, syscall-only execution), Reverse shell payloads, Botnet propagation scripts, sockstress (DDoS tool), MINIBIKE, TWOSTROKE, DEEPROOT, GHOSTLINE, LIGHTRAIL, POLLBLEND, CRASHPAD, SIGHTGRAB, TRUSTTRAP, DCSYNCER.SLICK | Target Platforms: Ray framework (AI orchestration), GitLab / GitHub – abused as C2 + malware distribution, Windows, Linux, Virtual Desktop platforms, Azure hosting infrastructure
Rising Ransomware Activities
(Originally published in November 2025)
| Kraken Ransomware Group | Kraken is a financially motivated, Russian-speaking ransomware group that targets large organizations worldwide using a big-game-hunting and double-extortion technique. The operators maintain a dedicated leak site to pressure victims by threatening to publish exfiltrated data. The ransomware family supports Windows, Linux, and VMware ESXi, allowing the group to disrupt enterprise environments. Initial access is typically obtained via exposed SMB services, after which the attackers steal credentials and leverage RDP for lateral movement. Once inside the network, they deploy an advanced encryptor capable of fast, parallel encryption across disks, databases, and network shares. The Windows variant is heavily obfuscated, disables WoW64 for redirection, deletes shadow copies, and incorporates aggressive anti-recovery measures. The Linux/ESXi variant performs platform validation, supports multiple encryption modes, and wipes system logs to conceal operational activity. |
| Akira Ransomware | A joint advisory from multiple international cybersecurity agencies highlights ongoing activity by Akira, a financially motivated ransomware group known for double-extortion operations targeting organizations worldwide. Akira actors typically obtain initial access through compromised VPN appliances lacking MFA and other exposed remote access services. Once inside, they perform extensive reconnaissance, harvest credentials, and move laterally using native OS tools and legitimate remote-administration software to evade detection. The group escalates privileges to domain administrator, disables security controls, and targets backup infrastructure to hinder recovery efforts. Akira operators exfiltrate sensitive data using file transfer utilities and cloud-based tunnels before encrypting systems to pressure victims into paying. The group has impacted a wide range of organizations across North America, Europe, and Australia, affecting entities of all sizes, including multiple sectors of critical infrastructure. |
| Lynx Ransomware | A financially motivated threat actor executed a multi-stage intrusion that culminated in the deployment of Lynx ransomware across a Windows domain environment. The attackers gained access through exposed Remote Desktop services using valid but previously compromised credentials. Once inside, they spent more than a week conducting reconnaissance and moving laterally across domain controllers, hypervisors, file servers, and backup infrastructure. Their operations relied heavily on commercial network-scanning tools and native Windows utilities, helping them blend in with legitimate administrative activity. The actor then collected and staged data from multiple servers before exfiltrating the archives to a temporary external hosting service. The intrusion concluded with the execution of the Lynx ransomware, which encrypted data on key servers and left a ransom note instructing the victim to contact the operators. |
Threat Labs summary
Securonix Threat Labs Recommends leveraging these findings to strengthen defenses against these ransomware campaigns.
- Enforce multi-factor authentication for all remote access, close any unused external ports, and ensure remote connectivity is routed through a Zero Trust access gateway.
- Require about regular password changes, eliminate shared accounts, and use tools that continuously monitor exposed or compromised credentials.
- Enable tamper-resistant logging, restrict who can interactively log on to critical servers, and isolate domain controllers within a dedicated, secured VLAN.
- Apply least-privilege permissions on all file shares and generate alerts when users or systems rapidly enumerate large directory structures.
- Block unapproved remote administration tools and alert any unexpected installations or unusual child processes indicating lateral movement.
- Maintain immutable, offline backups and perform quarterly restoration tests to verify integrity and recovery of readiness.
- Enforce strict outbound traffic controls, block tunneling utilities, and require explicit approval for outbound SSH, FTP, or similar high-risk channels.
- Use constrained PowerShell modes, block execution of unsigned scripts, and alert on suspicious chains involving living-off-the-land binaries (LOLBins).
- 73 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Kraken ransomware include but are not limited to the following:
- Monitor for [.]zpsc file extension, which indicates files encrypted by the ransomware.
- Monitor for the presence of the ransom note “readme_you_ws_hacked.txt.”
- Monitor for any outbound communication to the data-leak platform known as “The Last Haven Board.”
- Monitor for command-line activity involving parameters such as “tests,” “-tempfile,” and “-tempsize,” which may be used to gain access to the victim’s machine.
TTPs related to the Akira Ransomware include but are not limited to the following:
- Monitor for the administrative account named itadm.
- Monitor for files with encryption [.]powerranges, [.]akira, AkiraV2, [.]akiranew or [.]aki.
- Monitor for tools like nltest /dclist: and nltest /DOMAIN_TRUSTS for network and domain discovery.
- Monitor for the execution of the remote command wimiexec.py.
- Monitor for the services Veeam.Backup.MountService.exe for privilege escalation.
TTPs related to the Lynx Ransomware include but are not limited to the following:
- Monitor for the execution of netscan.exe on any host, as this activity is a strong indicator of lateral movement.
- Monitor for the creation of temporary directories or archive files that may be used for data collection and exfiltration, particularly those uploaded to temp.sh.
- Monitor for the use of dsa.msc to create new accounts in Active Directory or on local systems.
- Monitor for user accounts whose passwords have been set to “never expire,” which may indicate persistence attempts.
- Monitor for registry and system discovery commands such as ipconfig, net user, reg query, and hostname enumeration, which are commonly used for reconnaissance.
Tags: | Target Sector: Manufacturing, Education, Information Technology, Healthcare and Public Health, Financial Services, and Food and Agriculture Sectors. | Target Locations: United States, United Kingdom, Canada, Denmark, Panama, Kuwait, North America, Europe, Australia | Target Systems: Windows Servers, Linux Servers, VMware ESXI, SMB Services, SQL Databases, file servers
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to ours Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Dheeraj Kumar and Sina Chehreghani