- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, Ella Dragun
The Monthly Intelligence Insights provides a summary of curated industry leading top threats monitored and analyzed by Securonix Threat Labs every month. The report additionally provides a synopsis of the threats, indicators of compromise (IOCs), tactics, techniques and procedures (TTPs), and related tags. This may be followed by a comprehensive threat summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below mentioned threats, refer to our Threat Research Feed.
In November, Threat Labs analyzed and monitored major threat categories, including multiple cyber campaigns involving ransomware and malware. Of note are three threat groups: APT-36, Billbug, and Earth Preta which were targeting worldwide government organizations. While the APT-36 group has specifically targeted employees of the Indian government-related agencies, the Billbug group deploys signed malware to make it more difficult to detect or decrypt HTTPS traffic. Finally the Earth Preta group uses China Chopper and PlugX malware to collect data from compromised environments.
Furthermore, an increasing number of threats are targeting FIFA World Cup Qatar 2022 this month. This brought with it a spike in cyber attacks targeting football fans through fake streaming sites and lottery scams, leveraging the rush and excitement around these rare global sporting events to infect users with malware. There was a significant increase in newly registered domains related to the FIFA World Cup.
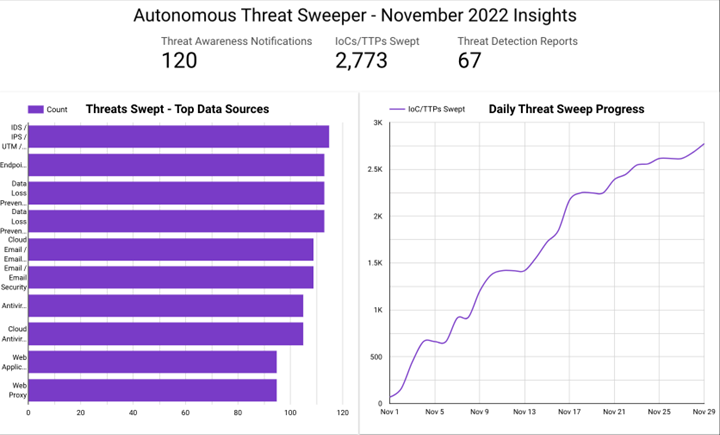
In November, Securonix Autonomous Threat Sweeper identified 2,773 IOCs, 120 distinct threats, and reported 67 threat detections. The top data sources swept against include IDS/IPS/UTM/Threat Detection, Endpoint Management Systems, Data Loss Prevention, and Email / Email Security.
Hackers target worldwide Government organizations
(Originally published on November 2022)
APT-36, formerly known as Transparent Tribe, is a hacking group based in Pakistan that launched a malicious campaign against Indian government organizations by installing Trojanized versions of a multifactor authentication solution called Kavach. The group uses Google advertising to distribute backdoored versions of Kavach multi-authentication (MFA) applications for the purpose of malvertising. Additionally, the advanced persistent threat group has engaged in low-volume credential harvesting attacks in which rogue websites masquerading as official government portals entice unwitting users to reveal their passwords.
The Chinese state-sponsored actor Billbug (also known as Thrip, Lotus Blossom, Spring Dragon) targets certificate authorities, government agencies, and defense organizations in several Asian countries. The group likely uses both a Hannotog (Backdoor.Hannotog) and a Sagerunex (Backdoor.Sagerunex) backdoor. Billbug also uses a less frequently deployed open-source tool called Stowaway, which is a multi-level proxy tool created in Go-based that allows pentesters to circumvent network access restrictions.
APT group Earth Preta (also known as Mustang Panda and Bronze President) launched a new round of spear-phishing attacks. The attacks are aimed at government, academic, foundation, and research sectors in Myanmar, Australia, the Philippines, Japan, Taiwan, and other countries in the Asia Pacific region. Hackers send spear-phishing emails using fake Google accounts, in which malware is embedded in a malicious archive file that is delivered via a Google Drive link, Dropbox link, or other IP address.
Threat Labs summary
Securonix Threat Labs has continued to monitor actively running campaigns by multiple threat actors that are targeting government sectors worldwide as they begin spreading rapidly once again. Threat Labs has observed the following trends among the threat groups:
- The APT-36 group specifically targeted employees of Indian government-related organizations.
- The Billbug group deploys signed malware to make it more difficult to detect or decrypt HTTPS traffic.
- The Earth Preta group uses China Chopper and PlugX malware to collect data from compromised environments.
198 IOCs are available on our Threat Research Feed and have been swept for Securonix Autonomous Threat Sweeper customers.
TTPs related to APT-36 targeting Indian governmental organizations include but are not limited to the following:
- Monitor for network traffic containing kavach-app , kavachguide, getkavach, kavachsupport, kavachdownload, kavachauthentication in the request url.
TTPs related to the Billbug threat group include but are not limited to the following:
- Monitor for modification of firewall configurations to enable RDP access to systems.
- Example: netsh advfirewall firewall set rule group=remote desktop new enable=Yes
Tags: Threat group: APT-36, Transparent Tribe, Operation C-Major, Mythic Leopard, Billbug, Thrip, Lotus Blossom, Spring Dragon, Earth Preta, Mustang Panda | Threat actor location: Pakistan, China | Tool: Limepad, Stowaway | Target Sector: Government, Defense, Academic, Foundation, Research | Malware: TONEINS, TONESHELL, PUBLOAD, Hannotog, Sagerunex
Threats related to FIFA World Cup Qatar 2022
(Originally published on November 2022)
The much-anticipated football tournament is here! Cybercriminals are expected to exploit news trends, ticket demand, and human error to deliver cyberattacks.
Email security researchers have found that attackers are targeting Arab organizations using FIFA and football-related campaigns. As part of their social engineering tactics, attackers often target organizations related to important/popular events and particularly those that seem more likely to fall victim to the attack. Such attacks can aim at a variety of things, including financial fraud, credential harvesting, data exfiltration, surveillance, or reputation damage.
In another campaign, researchers saw a significant increase in streaming sites with newly registered domains. A fake streaming site is used to post fake streaming links on legitimate websites/portals and target users with multiple scams related to World Cup match tickets, airline tickets, and themed lottery draws.
Threat Labs summary
Securonix Threat Labs has continued to monitor actively running campaigns by multiple threat actors that are targeting the FIFA World Cup tournament as they began spreading rapidly once again.
Threat Labs has observed that different malware families have been targeting football fans during the FIFA World Cup. One significant trend includes attackers using maliciously cracked versions of FIFA/football games to target users.
113 IOCs are available on our Threat Research Feed repository and have been swept for Securonix Autonomous Threat Sweeper customers.
Tags: Malware: Qakbot, Emotet, Formbook, Remcos, QuadAgent | Attack type: Phishing email, Phishing sites
Iranian hackers breached US federal agency
(Originally published on November 2022)
According to a joint advisory by the FBI and CISA, an Iranian government-sponsored threat actor group hacked a Federal Civilian Executive Branch (FCEB) organization to deploy XMRig cryptomining malware. In order to compromise the Federal network, attackers exploited a remote code execution vulnerability in Log4Shell (CVE-2021-44228) on an unpatched VMware Horizon server. As part of their effort to maintain persistence within the FCEB’s network, the Iranian threat actors installed reverse proxies on compromised servers.
Threat Labs summary
CISA reported the threat group targeted the affected organization early this year by weaponizing the vulnerability to add a new exclusion rule to Windows Defender that allows listing the entire C:\ drive. In light of the advisory, Securonix Threat Labs recommends leveraging our findings to guide the deployment of protective measures against the threat group including the following actions.
- Update affected VMware Horizon and unified access gateway (UAG) systems to the latest version.
- Secure credentials by restricting where accounts and credentials can be used and by using local device credential protection features.
4 IOCs are available on our Threat Research Feed repository and automatically swept for Autonomous Threat Sweeper customers.
Tags: Threat Actor Location: Iran | Exploitation: Remote code execution | Vulnerability: Log4Shell (CVE-2021-44228) | Malware: XMRig cryptomining
Malware campaigns proliferate in November
(Originally published on November 2022)
A new wave of Emotet malware has been discovered as part of a large-scale spam campaign designed to deliver payloads such as IcedID and Bumblebee. It is clear that Emotet is returning to its full function as a malware delivery network by sending hundreds of thousands of emails per day since early November 2022. As a result of coordinated law enforcement operations in January 2021, the malware was dismantled by Mummy Spider (aka Gold Crestwood or TA542). However it staged a comeback late last year targeting a number of countries, including the U.S., the U.K., Japan, Germany, Italy, France, Spain, Mexico, and Brazil.
In another campaign, attackers use social engineering tactics to convince users to open malicious documents and enable macro content in order to download the Emotet payload.
According to CERT-UA, Ukrainian organizations have been the targets of ongoing cyberattacks using advanced Somnia malware as well as other malicious strains. Researchers provided insights into the cybersecurity incident which involved a hacking collective known as FRwL aka Z-Team. The collective has been identified as the adversary whose activity is responsible for unauthorized intrusions into targeted automated systems and computers.
QakBot’s initial compromise method is fairly typical of modern malware today and once again, it is spreading rapidly using multiple techniques. Recently, Securonix researchers observed phishing emails containing URLs that link to a remote password-protected zip file that can be accessed by the target address. In many emails, the password to the file is included as part of the body, which easily executes when the recipient downloads it. After downloading and extracting the zip file, an image disk file (usually an ISO file) appears. The user begins code execution by clicking the .LNK file inside the .iso after mounting it.
In recent years, .LNK files have become more popular for code execution, likely due to Microsoft’s decision to disable VBS macros in MS Office applications by default.
Threat Labs summary
Securonix Threat Labs continuously monitors all malware campaigns, as the threat actors are often changing their TTPs while sharing attack infrastructure among themselves to target vulnerable users.
Threat Labs proactively monitors and secures identified systems and devices for any suspicious/malicious activities and recommends the following:
- Regularly checking and applying the latest patch of software, especially to public-facing applications.
- Enforcing multifactor authentication for users to ensure only those authorized are accessing your network.
121 IOCs are available on our Threat Labs home page repository and automatically swept for Autonomous Threat Sweeper customers.
TTPs related to the QakBot Malware include but are not limited to the following:
- The TTPs for PsExec created in an abnormal location and regsvr32.exe executing a .dll remotely from SYSVOL are easy wins from a detection standpoint.
Tags: Malware: QakBot, IcedID, Bumblebee, Emotet, Somnia | Exploitation: Remote code execution | Target Countries: US, UK, Japan, Germany, Italy, France, Spain, Mexico, Brazil
ARCrypter ransomware
(Originally published on November 2022)
An increasingly global threat posed by ARCrypter ransomware previously compromised key organizations in Latin America. Using both Linux and Windows systems, this ransomware family targeted a Chilean government agency in August, encrypting files with the “.crypt” extension.
According to researchers, the ARCrypter family is responsible for a second attack on the Colombian National Food and Drug Surveillance Institute (Invima) in October. ARCrypter has expanded outside Latin America and is now targeting organizations worldwide, such as China and Canada. ARCrypter victims have also been targeted in Germany, USA, and France.
Threat Labs summary
Securonix Threat Labs has observed that the threat actor maintained access, minimized forensic artifacts, and increased access to systems after obtaining initial access. Threat Labs continues to monitor ransomware activities and recommends customers follow the steps below to avoid ransomware attacks.
- Leverage our findings to inform the deployment of protective measures against the threat group.
- Implement network segmentation and maintain offline backups of data to ensure limited interruption to your organization.
- Audit user accounts with administrative privileges and configure access controls according to the principle of least privilege.
- Disable unused ports and enable multi-factor authentication (2FA).
- 20 IOCs are available on our Threat Research Feed and have been swept for Securonix Autonomous Threat Sweeper customers.
TTPs related to the ARCrypter rRansomware include but are not limited to the following:
- Monitor for URLs facilitating the download of “win.exe” and “win.zip”
Tags: Target: Windows, Linux | Ransomware: ARCrypter
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Github page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected]
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Sina Chehreghani, Dhanaraj K R


