- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
- MSSPs
- Scale multi-tenant security with predictable economics.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar and Tanmay Kumar
The Monthly Intelligence Insights report provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in October 2025. The report also includes a synopsis of the threats, indicators of compromise (IoCs), tactics, techniques, and procedures (TTPs), and related tags. Each threat has a comprehensive summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below-mentioned threats, refer to our Threat Labs home page.
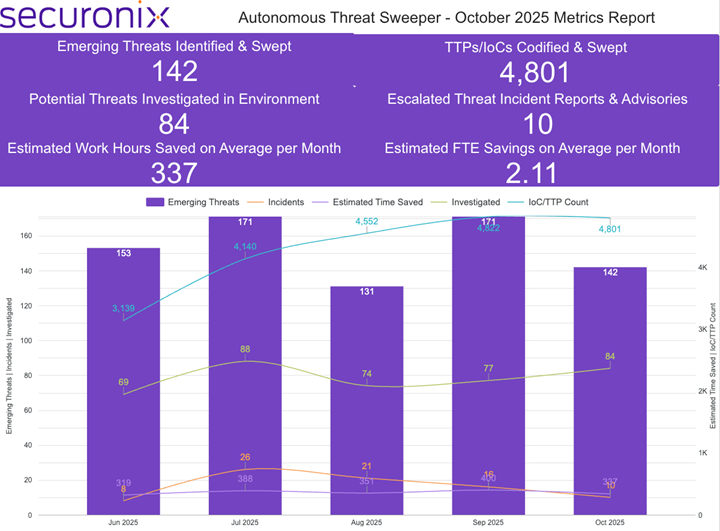
Last month, Securonix Autonomous Threat Sweeper identified and analyzed 4,801 TTPs and IoCs; identified 142 emerging threats; investigated 84 potential threats; and elevated 10 incidents. The top data sources swept against include IDS / IPS / UTM / Threat Detection, Data Loss Prevention, Endpoint Management Systems, and Email / Email Security.
In October 2025, the Autonomous Threat Sweeper team observed a surge in global cyber threats driven by state-backed espionage, advanced backdoors, and ransomware. Russia-linked COLDRIVER deployed new credential theft malware, Earth Krahang and Bitter APT expanded government-focused attacks, and Chinese and South Asian groups like Confucius advanced their espionage campaigns. Backdoor activity rose with WARMCOOKIE’s fileless execution, the CAPI .NET stealer, ChaosBot automation, fake Teams installers delivering Oyster, and the AI-powered EvilAI malware. Ransomware operations intensified with new Chaos variants, BlackSuit outbreaks, and Agenda’s BYOVD attacks, while active exploitation of CVE-2025-59287 and the F5 BIG-IP breach fueled RCE and BRICKSTORM intrusions. These trends highlight the growing fusion of AI, automation, and zero-day exploits, stressing the need for rapid patching and proactive defense.
Key Highlights of Recent APT Campaigns
(Originally published in October 2025)
| COLDRIVER (Russia) – New “Robot” Malware Lineage | An investigation into COLDRIVER (also known as Star Blizzard/Callisto) reveals a rapid evolution from its earlier LOSTKEYS malware to a new chain of DLL and PowerShell-based backdoors under the ROBOT family, NOROBOT, YESROBOT, and MAYBEROBOT. Delivered via the COLDCOPY “ClickFix” lure, this chain imitates CAPTCHA verification to trick users into execution. NOROBOT functions as a downloader to retrieve and decrypt payloads, YESROBOT (Python-based) acted as an interim tool, and MAYBEROBOT (PowerShell-based) became the primary flexible backdoor for executing commands. This evolution demonstrates accelerated development focused on evading detection while sustaining persistent intelligence-gathering operations. |
| Earth Krahang – Global Cyberespionage Campaign | The Earth Krahang group, active since 2022, has conducted extensive government espionage across 23 countries, compromising over 70 public sector organizations by exploiting intergovernmental trust. Their tactics include spear-phishing from compromised government email accounts, exploiting vulnerabilities such as CVE-2023-32315 (OpenFire), and hosting malware on legitimate government domains. The group’s toolkit features malware like XDealer, persistence via SoftEther VPN, and heavy use of Cobalt Strike for DLL side-loading. Krahang’s strategy of leveraging official communication channels and trusted relationships to spread infections reflects a sophisticated operational model that combines social engineering with infrastructure-level compromise. |
| Bitter (APT-Q-37) – New Delivery Chains for C# Backdoors | The Bitter APT group, operating primarily from South Asia, has evolved its backdoor delivery methods with two new infection chains deploying C#-based malware. The first chain uses Excel XLAM macros to compile and install a backdoor via csc.exe and InstallUtil.exe, while the second exploits a WinRAR path traversal vulnerability to replace Word’s Normal.dotm template, enabling malicious macros when the document is opened. The backdoor communicates with C2 servers to retrieve additional payloads and collect system information. The attack infrastructure aligns with previously observed Bitter campaigns, utilizing domains. |
| CN APT Campaign Targeting the Serbian Government | A Chinese APT group has conducted a spear-phishing campaign targeting Serbia’s aviation sector and other European entities. The attackers used obfuscated PowerShell commands embedded in malicious LNK and ZIP files disguised as government documents, such as NAJU Plan Obuka OKTOBAR 2025. Payloads extracted via custom carving routines deployed variants of SOGU and PlugX/Korplug malware, establishing C2 connections to domains. Related phishing lures were also observed in Hungary, Belgium, Italy, and the Netherlands, leveraging decoy documents themed around European Commission and NATO events. This multi-country targeting pattern highlights a clear espionage motive and demonstrates the technical consistency characteristic of long-running Chinese cyber operations. |
| Confucius Organization – Weapon Arsenal and Source Code Exposure | An investigation into the Confucius organization has uncovered the group’s internal source code and testing environment, revealing a modular malware ecosystem. Believed to be a South Asian APT group with outsourcing characteristics, Confucius employs cost-effective and technically simple attack methods, such as LNK phishing decoys and basic trojans, to pursue state-aligned objectives. Its toolkit comprises several linked components: DeliveryBoy (dropper), FileSplitterr (file segmentation utility), MadBoy (payload loader), and Win (final CMD backdoor). Together, these form a multi-stage infection chain that enables command execution and C2 communication via Tor nodes. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these APT group’s campaigns.
- Disable execution of LNK shortcut files from untrusted sources and apply group policies restricting script execution in %ProgramData% and %Temp% directories.
- Implement enhanced phishing controls, including sandbox-based URL rewriting and attachment detonation to detect malicious ZIP/LNK combinations.
- Immediately update or disable vulnerable WinRAR versions (7.12 and below) vulnerable to path traversal exploits.
- Patch known exploited vulnerabilities such as CVE-2023-32315 (OpenFire) and CVE-2022-21587 (Oracle WADI).
- Disable rundll32 execution of untrusted DLLs via Windows Defender Application Control.
- Enforce PowerShell Constrained Language Mode to reduce backdoor command execution.
- 57 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the COLDRIVER include but are not limited to:
- Monitor for commands writing registry keys under HKEY_CURRENT_USER\SOFTWARE\Classes or subkeys named .pietas or other uncommon extensions used to store cryptographic fragments.
- Monitor for persistence achieved through logon scripts that launch PowerShell commands from the AppData or Roaming directories.
- Monitor for PowerShell executions containing encoded or obfuscated commands, including bitsadmin usage to retrieve files like libsystemhealthcheck.py or libcryptopydatasize.py.
- Monitor for PowerShell scripts that contain or execute logic like MAYBEROBOT’s three command patterns:
- Download and execute from URL
- Execute via cmd.exe
- Execute a PowerShell code block
TTPs related to the Bitter (APT-Q-37) include but are not limited to the following:
- Monitor for execution of VBA macros from .xlam or .docx files that perform Base64 decoding and write executable or log files (C:\ProgramData\cayote.log).
- Monitor for unusual use of csc.exe or InstallUtil.exe from the .NET Framework compiling C# source files outside standard developer workflows (generating vlcplayer.dll in C:\ProgramData\USOShared\).
- Monitor for creation of batch files (kefe.bat) in Startup directories that set up scheduled tasks or persistence mechanisms.
- Monitor for extraction operations from RAR archives attempting path traversal (overwriting files under C:\Users\<User>\AppData\Roaming\Microsoft\Templates\Normal.dotm).
- Monitor for RAR or ZIP archives containing alternate data streams (ADS) or unexpected internal paths such as ..\AppData\Roaming\Microsoft\Templates\Normal.dotm.
TTPs related to the CN APT include but are not limited to the following:
- Monitor for execution of .lnk shortcut files that launch obfuscated PowerShell commands (-w 1 -c “;;;$oaswtd = (get-childitem …)”).
- Monitor for creation and execution of files in %TEMP% directories with random or unusual names (QXGG5H1Q-4V14-PYBM-GMIJ-UTGCPSSVXMT1\cnmpaui.exe).
- Monitor for legitimate binaries such as Canon Printer Assistant (cnmpaui.exe) executing suspicious or unsigned DLLs with matching names (cnmpaui.dll).
Tags: Threat Actor: Confucius APT, APT10 / Mustang Panda cluster, Bitter APT (APT-Q-37), Earth Krahang, COLDRIVER (aka Star Blizzard, UNC4057, Callisto Group) | Adversary Location: India, South Asia, China, Southeast Asia, Russia | Target Sector: Government, Military, Education, NGO, Power/Energy, Public Institutions, Foreign Affairs, Defense, Public Administration, Policy Institutions, Think Tanks, Political Dissidents | Target Location: Target Location: South and Southeast Asia, Serbia, Hungary, Italy, Belgium, the Netherlands, China, Pakistan, North America, Asia, Europe, Africa, and the Americas. | Target Platforms: Windows 10/11, enterprise and government workstations, Windows OS, Windows (Office 2016 and above), Linux | Malware/Payloads: DeliveryBoy (dropper), FileSplitterr (split tool), MadBoy (loader), Win CMD Trojan, SOGU, PlugX, Korplug (remote access trojans), Custom C# Backdoor (vlcplayer.dll, winnsc.exe), XDealer (primary backdoor), Cobalt Strike loaders, NOROBOT (DLL downloader), YESROBOT (Python backdoor), MAYBEROBOT (PowerShell backdoor)
Emerging Malware & Espionage Threats
(Originally published in October 2025)
| Fake Microsoft Teams Installers Push Oyster Malware | In late September 2025, analysts identified a malvertising campaign distributing the Oyster backdoor (also known as Broomstick or CleanUpLoader) through fake Microsoft Teams installers. Threat actors used SEO poisoning and search-engine advertisements to lure users to a fraudulent website that closely resembled Microsoft’s legitimate download portal. The malicious installer (MSTeamsSetup.exe), signed with certificates issued to 4th State Oy and NRM Network Risk Management Inc., deployed a DLL (CaptureService.dll) and created persistence via a scheduled task that was executed every 11 minutes. This campaign mirrors previous Oyster infections distributed through trojanized versions of PuTTY and WinSCP, showing how adversaries continue to use trusted software brands to infiltrate corporate environments using commodity backdoors. |
| EvilAI — AI-Generated Malware Campaign | First seen in August 2025, EvilAI uses AI-generated JavaScript for Node.js to produce highly obfuscated, self-modifying trojans that are often signed with legitimate certificates. Distributed as fake productivity tools via malicious sites, SEO poisoning, and social ads, the malware modifies the registry, spawns processes, moves files, and exfiltrates data over AES-256-CBC C2 channels, while AI-driven obfuscation techniques such as control-flow flattening, Unicode escaping, and MurmurHash3-based anti-analysis loops hinder static detection, primary targets include manufacturing, government, and healthcare in India and the United States. |
| ChaosBot — Rust Backdoor Using Discord C2 | A Rust-written backdoor dubbed ChaosBot has been observed abusing Discord API servers for command-and-control. It is delivered through compromised VPN accounts and WMI commands, or by phishing shortcuts disguised as Vietnamese bank documents. Once active, it can run shell commands, transfer files, and capture screenshots over Discord message channels. The malware evades telemetry by patching ntdll!EtwEventWrite, checks for virtual machines using MAC address matching, and maintains persistence using reverse proxies such as frp and VS Code Tunnels. Researchers linked the campaign to two Discord IDs, “chaos_00019” and “lovebb0024”, active since mid-2024. |
| CAPI Backdoor — .NET Stealer Targeting Russia’s Auto-Commerce Sector | A campaign called Operation MotorBeacon targeted Russia’s automotive and e-commerce sectors using a custom .NET implant known as CAPI Backdoor. The attackers delivered it via phishing ZIP attachments that contained tax-themed PDF decoys and malicious LNK shortcuts, which execute through rundll32.exe. Once running, CAPI connects to a C2 endpoint over port 443, enumerates installed antivirus products and browser profiles (Edge, Chrome, Firefox), captures screenshots, looks for VM artifacts, and establishes persistence via scheduled tasks or startup links. The malware harvests credentials and session data before exfiltrating to C2 infrastructure under ASN 39087 (P.a.k.t LLC). The use of a lookalike domain and tax-themed lures show focused social engineering and regional targeting of commercial organizations. |
| Confucius Espionage — From Stealer to Backdoor | A South Asian espionage group known as Confucius evolved in 2025 from using the WooperStealer infostealer to deploying a Python-based backdoor called AnonDoor. Early infections used weaponized PPSX and LNK attachments targeting organizations in Pakistan, relying on DLL side-loading and registry-based persistence to steal sensitive documents. By mid-2025 the group began shipping a Python runtime component (python313.dll) and deployed AnonDoor as a PYC-compiled Python implant that collects system information, captures screenshots, enumerates directories, and dumps browser-stored credentials. The actors built a multi-domain C2 architecture and used scheduled tasks to keep the implant stealthy. |
| WarmCookie — Persistent Backdoor Still Active | WarmCookie, also tracked as BadSpace, remains active into late 2025 and is still changing. Recent builds add modular execution handlers for EXE, DLL, and PowerShell payloads, plus a reusable “string bank” that helps create plausible persistence paths (for example, SoftServe\Updater.exe). Newer variants include dual mutexes, campaign IDs and RC4 keys used to segment operator clusters, and reuse of the same expired SSL certificate across builds. These changes shift detection away from simple signature checks toward runtime analysis of rundll32/PowerShell execution chains and short-lived payload spawns, making WarmCookie a durable and adaptable initial-access backdoor. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these malware/backdoor campaigns.
- Restrict software installations to verified vendor domains (microsoft.com) and disable search engine–served ads for software downloads.
- Use ad-blockers or safe-browsing tools that can flag malicious sponsored links.
- Regularly check scheduled tasks and %APPDATA% directories for anomalies like ‘CaptureService’.
- Restrict script execution permissions, disable unnecessary modules, and employ runtime integrity checks.
- Verify code-signing certificate origins and revoke trust for newly registered or unverified publishers.
- Implement advanced email gateway filtering to block ZIP attachments containing LNK or DLL payloads.
- Block or closely monitor the use of rundll32.exe and other system binaries often used for DLL execution.
- Identify hidden persistence mechanisms under names like “AdobePDF” or “Microsoft.lnk” in Startup folders.
- 98 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Oyster Malware include but are not limited to the following:
- Monitor for execution of files named MSTeamsSetup.exe from locations outside Microsoft’s legitimate installer sources (Downloads folder, user profile directories).
- Monitor for creation of scheduled tasks named “CaptureService” or tasks that execute DLL files from %APPDATA%\Roaming directories.
- Monitor for repeated execution of a process or DLL (CaptureService.dll) at regular intervals (every 11 minutes), suggesting persistence or beaconing behavior.
TTPs related to the EvilAI include but are not limited to the following:
- Monitor for creation or execution of temporary JavaScript payloads named in the pattern [GUID]or.js within user directories such as %TEMP% or %AppData%.
- Monitor for network communications encrypted with AES-256-CBC.
TTPs related to the ChaosBot include but are not limited to the following:
- Monitor for creation or execution of DLL files (e.g., msedge_elf.dll) in non-standard directories like C:\Users\Public\Libraries.
- Monitor for the legitimate process identity_helper.exe loading unexpected DLLs, indicative of side-loading activity.
- Monitor for new process behaviors creating channels or sending messages to Discord, especially ones named after hostnames or containing Unicode channel names such as “常规”.
- Monitor for PowerShell processes executing encoded commands that include $OutputEncoding = [System.Text.Encoding]::UTF8 (used consistently by ChaosBot).
- Monitor for creation or transmission of files named like command_result_.txt or screenshot_.png.
- Monitor for execution of FRP (Fast Reverse Proxy) binaries such as node.exe with arguments referencing configuration files (-c c:\users\public\music\node.ini).
- Monitor for processes attempting to patch ntdll!EtwEventWrite (e.g., replacing initial bytes xor eax, eax with ret) to disable ETW telemetry.
TTPs related to the CAPI Backdoor include but are not limited to the following:
- Monitor for execution of .LNK files from email attachments or ZIP archives — especially filenames resembling payroll, tax, or HR documents (“Перерасчет заработной платы 01.10.2025.lnk”).
- Monitor for command-line invocations of rundll32.exe executing unusual DLLs from temporary or user profile directories (rundll32.exe <path>\adobe.dll,config).
- Monitor for DLL files created or executed from paths under %AppData%, %Roaming%, or %Temp% directories named like adobe.dll or client6.dll.
- Monitor for screen capture activities — creation of .png image files with date/time stamps or API calls like Graphics.CopyFromScreen()
- Monitor for unusual ZIP file creation in temporary folders with names like:
- edprofile_*.zip – containing Edge browser data
- chprofile_safe.zip – containing Chrome browser data
- ffprofile_safe.zip – containing Firefox data
TTPs related to the Confucius Espionage include but are not limited to the following:
- Monitor for creation or modification of DLL files such as Mapistub.dll or python313.dll under %LocalAppData% or %AppData% directories.
- Monitor for registry changes under: HKCU\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\load pointing to suspicious executables in user directories.
- Monitor for scheduled tasks named “NetPolicyUpdate” or similar, executing pythonw.exe from a Scoop environment every few minutes.
- Monitor for repeated POST requests containing parameters like value1, value2, value3, or unusual delimiters such as $!!$, @$$@, or !$$$!, consistent with WooperStealer or AnonDoor communication formats.
- Monitor for scripts using Directory.GetLogicalDrives or GetDiskFreeSpaceExW APIs to enumerate drives, collect volume information, or report free space.
- Monitor for Python scripts performing actions labeled as CmdExecution, Screenshot, PasswordDumper, FolderDownload, or similar modules fetched dynamically from external domains.
- Monitor for attempts to extract browser data files for Firefox and Edge via Python scripts (Fohjdfj783mq9XX.py, Fodkh3897mgfdjiuED.py).
- Monitor for PowerShell commands containing numeric arrays piped through decoding loops like %{char} — a hallmark of script reconstruction.
- Monitor for hidden or attribute-modified files (FileAttributes.Hidden) such as winresume.pyc placed in user directories.
TTPs related to the WarmCookie include but are not limited to the following:
- Monitor for child processes of rundll32.exe or PowerShell.exe spawning executables such as conhost.exe or unknown binaries, especially within AppData or ProgramData paths.
- Monitor for creation of scheduled tasks using legitimate-sounding company names (e.g., SoftServe, VectorformUpdater) or paths under C:\ProgramData\ with randomly generated vendor-like folder names.
- Monitor for task creation commands using the /u parameter (replacing the older /p), which may indicate an updated WARMCOOKIE variant.
- Monitor for file or process names containing campaign keywords such as aws, bing, capo, lod2lod — linked to specific WARMCOOKIE clusters.
- Monitor for outbound HTTPS connections using self-signed or default certificates, especially with the issuer C=AU, ST=Some-State, O=Internet Widgits Pty Ltd, even if expired.
Tags: Malware: Oyster, Broomstick, CleanUpLoader, EvilAI, ChaosBot, CAPI Backdoor, WooperStealer, AnonDoor, WarmCookie | Tools/Techniques: SEO poisoning, malvertising, fake installer, scheduled task persistence, AI-generated JavaScript, Node.js execution, AES-256-CBC encrypted C2, control-flow flattening, Unicode obfuscation, Discord API C2, WMI lateral movement, reverse proxy (frp), VS Code Tunnel misuse, PowerShell execution, ETW bypass, Spear-phishing ZIPs, LNK loader, rundll32 execution, WMI queries, browser credential theft, Phishing emails, malicious PPSX and LNK files, DLL side-loading, Python-based PYC execution, PowerShell loaders, rundll32 execution, PowerShell payload delivery, “String Bank” evasion, RC4 encryption, campaign ID segmentation, dual mutex persistence | Target Sector: Corporate IT administrators, Enterprise networks, Manufacturing, Government, Healthcare, Technology, Retail, Education, Financial, Construction, Financial services, Automobile industry, E-commerce sector, Military, Defense Contractors | Target Location: India, United States, Europe, Brazil, Canada, Vietnam, Asia-Pacific, Russian Federation, South Asia, Global | Target Platforms: Microsoft Windows (Teams installation vector), Node.js runtime (Windows/Linux environments), Microsoft Windows, Microsoft Windows (.NET framework), Microsoft Windows (with embedded Python runtime execution)
Unmasking the Latest Cyber Campaigns
(Originally published in October 2025)
OceanLotus, also known as APT32 or APT-Q-31, has intensified its cyber-espionage operations across China and Southeast Asia through the deployment of Havoc Demon, a modular remote access trojan built on the Havoc post-exploitation framework that is delivered via DLL hollowing and Vectored Exception Handler execution using a crafted msmpi.dll loader to inject shellcode into memory, achieves persistence by modifying HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\MicrosoftMPI, dynamically resolves system APIs through hashing to evade static analysis, communicates with encrypted C2 channels, and leverages in-memory execution, anti-sandbox techniques, and legitimate process masquerading such as SyncHost.exe to avoid detection, reflecting the group’s technical evolution and continued focus on intelligence collection against government, defense, and research targets.
Meanwhile, the China-linked UNC5221 group is conducting a large-scale espionage campaign following the confirmed F5 BIG-IP source code leak, weaponizing the stolen data with the BRICKSTORM backdoor, a statically compiled Go ELF implant for Linux appliances that uses TLS-encrypted WebSocket tunnels over HTTP/2 multiplexed with Yamux for stealthy multi-channel C2, persists via systemd service units, disguises exfiltration as normal web activity using multipart/form-data and base64 compression, employs protocol tunneling, proxy chaining, and credential harvesting through servlet filters, and uses ELF variants such as Pg_update, Listener, and Vmprotect to enable long-term infiltration of federal and enterprise networks.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these APT group’s campaigns.
- Urgently patch all affected F5 systems listed under vulnerabilities (CVE-2025-53868, CVE-2025-60016, CVE-2025-61955, etc.).
- Remove public exposure of BIG-IP management interfaces. Restrict access via VPN, bastion hosts, or internal-only subnets.
- Enable certificate pinning and SSL inspection where feasible to detect hidden TLS tunnels.
- Remove the persistence entry (MicrosoftMPI) and delete the loader DLLs (msmpi.dll, shellcode.dll).
- Reinstall or restore critical system DLLs (certmgr.dll) from trusted installation media.
- Enable DNS and proxy logging to detect anomalies such as fake SyncHost.exe connections.
- Enable command-line logging (Event ID 4688) to detect rundll32 abuse.
- 5 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the OceanLotus include but are not limited to the following:
- Monitor for the creation or modification of registry keys such as HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\MicrosoftMPI — indicative of persistence being established for automatic execution at startup.
- Monitor for DLL loading activity involving msmpi.dll, certmgr.dll, or advapi32.dll being injected or manipulated by rundll32.exe, especially when DLL hollowing or VEH (Vectored Exception Handling) mechanisms are used for execution.
- Monitor for processes such as rundll32.exe performing DLL injection into legitimate system binaries (advapi32.dll, certmgr.dll), which may indicate hollowing activity.
- Monitor for unusual use of VEH exception handling (RtlAddVectoredExceptionHandler) callbacks — these are often used by OceanLotus loaders to execute shellcode while avoiding traditional detection methods.
- Monitor for creation of mutex objects like Global\MicrosoftMPI, which the malware uses to ensure only a single instance runs at a time.
- Monitor for processes dynamically resolving API addresses through hash-based function resolution, as this technique hides malicious API calls (e.g., GetProcAddress, LoadLibraryA).
- Monitor for processes loading or modifying system DLLs such as certmgr.dll, Kernel32.dll, Ntdll.dll, and iphlpapi.dll — especially if these are loaded into unexpected memory regions or show injected code.
- Monitor for command-line execution of rundll32.exe referencing msmpi.dll, for example: rundll32.exe “C:\Windows\System32\OceanLotus\msmpi.dll”,MPI_Init
- Monitor for consistent use of AES-256-CTR encryption in POST payloads, with patterns involving “Havoc Magic Head” markers or custom structured data containing host, user, and OS information.
TTPs related to the UNC5221 include but are not limited to the following:
- Monitor for systemd service creation or modification (systemctl enable, systemctl daemon-reload) indicative of persistence setup.
- Monitor for creation or modification of systemd unit files or startup scripts referencing unfamiliar ELF executables such as Pg_update or Listener.
- Monitor for files or processes that masquerade as legitimate update helpers (Pg_update, Vmprotect) on F5 appliances.
Tags: Threat Actor: UNC5221, OceanLotus (APT32 / APT-Q-31) | Adversary Origin: China, Vietnam | Target Sectors: Government and federal networks (U.S.), IT infrastructure providers, Cloud and telecom sectors, Critical infrastructure using F5 BIG-IP, Government (especially Chinese ministries), Defense & Military research, Energy and critical infrastructure, Healthcare, Scientific institutions | Target Geography: United States (primary), targeting organizations deploying F5 devices, China (primary), Other East and Southeast Asian countries (Vietnam, Laos, Cambodia, etc.) | Malware/Backdoor: BRICKSTORM, Havoc Remote Access Trojan (RAT) | Target Platforms: Linux-based network appliances (F5 systems), Microsoft Windows 10 / 11 | Known CVEs/Vulnerabilities: CVE-2025-53868, CVE-2025-60016, CVE-2025-61955, CVE-2025-59781, CVE-2025-61974
Vulnerability Spotlight
(Originally published in October 2025)
Attackers are going after Windows Server Update Services (WSUS) with a remote, unauthenticated deserialization flaw that lets them run code through the WSUS web endpoints. In the cases observed, the web service process (w3wp.exe or the WSUS service) pivots straight into a short shell chain cmd into PowerShell and runs quick recon like whoami, ipconfig /all, and domain user lookups before staging the next steps. The trigger has shown inside crafted SOAP requests (including base64-encoded arrays), which explains why the first breadcrumbs are often in IIS/WSUS logs and the process tree on the server itself.
Zooming out, internet scans show many WSUS servers exposed on 8530/8531, and telemetry already includes probing and live exploitation. That combination makes WSUS a high-leverage target: compromise the patch hub, and you gain a launchpad for lateral movement or even poisoned software updates. The near-term playbook is simple: patch the CVE, take WSUS off the public internet (or at least restrict those ports), watch for deserialization errors in logs around suspicious requests, and alert when WSUS/IIS unexpectedly spawns shells. If you do catch execution, isolate the host, rotate credentials, and review your software distribution settings before bringing the service back online.
Threat Labs summary
Securonix Threat Labs Recommends leveraging these findings to strengthen defenses against these vulnerability campaigns.
- Patch first. Apply the vendor fix for CVE-2025-59287 on every WSUS server.
- Remove internet exposure. Do not publish WSUS to the open web.
- Lock down the service and run WSUS/IIS with least-privilege service accounts; no interactive logon; rotate creds after patching.
- Harden the web tier and turn on IIS request filtering, disable unused WSUS web services/SOAP endpoints, and limit request body size to reduce deserialization attack surface.
- Constrain script abuse and enable PowerShell script-block logging and AMSI on the server; use WDAC/AppLocker so IIS/WSUS cannot launch unknown binaries.
- Egress control and limit outbound traffic from WSUS to require Microsoft to update endpoints only; block webhook/unknown destinations.
- Detect early (EDR) and alert if w3wp.exe or wsusservice.exe spawns cmd.exe → powershell.exe, or if recon commands like whoami / ipconfig / net user run right after a web hit.
- 4 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the WSUS Unsafe Deserialization (CVE-2025-59287) include but are not limited to the following:
- Monitor for IIS w3wp.exe or wsusservice.exe spawning cmd.exe → powershell.exe on WSUS servers.
- Monitor for quick recon right after web hits: whoami, ipconfig /all, net user /domain.
- Monitor for WSUS/IIS logs showing ClientWebService/client.asmx or cookie handlers throwing deserialization exceptions.
- Monitor for outbound callbacks from WSUS hosts to webhook-style endpoints immediately after recon.
- Monitor for unsolicited internet traffic to ports 8530/8531 destined for WSUS servers.
Tags: Target System: WSUS web services on IIS | Target Platform: Windows Server | Observed behavior: w3wp.exe/wsusservice.exe → cmd.exe → powershell.exe; quick recon (whoami, ipconfig /all, net user /domain) | CVE exploited: CVE-2025-59287
Ransomware Highlights
(Originally published in October 2025)
| BlackSuit Ransomware | A key trend in global ransomware activity between March and August 2025 showed that BlackSuit emerged as the most active ransomware family during this period until a U.S. government takedown in July significantly reduced its operations. Clop remained active, highlighting the persistence of high-impact ransomware within corporate networks, while Black Basta maintained significant activity despite an earlier operational leak, with detections observed across multiple regions. Notably, some ransomware detections originated from endpoint sensors on HMI systems, highlighting the importance of multi-layered visibility across both network and endpoint environments. The United States was the most targeted region, followed by the United Kingdom and Japan, with manufacturing, transportation, and consumer services sectors most affected. |
| Chaos Ransomware | A new Chaos ransomware variant written in C++ has emerged, combining fast file encryption with destructive behavior and a unique clipboard hijacking feature. Distributed through a fake “System Optimizer v2.1” installer, it logs its activity in the temp directory to avoid detection. Once executed, it creates a mutex and checks prior to infection before encrypting files using AES-256-CFB or a fallback XOR method if CryptoAPI is unavailable. The ransomware deletes shadow copies, modifies recovery settings, and corrupts or deletes files based on their size, appending a.chaos extension and leaving a ransom note with payment details. It also monitors the clipboard to replace Bitcoin wallet addresses with an attacker-controlled wallet to silently redirect payments. |
| Agenda Ransomware | A new cross-platform Agenda ransomware campaign has emerged, expanding its scope beyond Windows to target Linux systems. The attackers delivered their payloads through fake CAPTCHA pages and leveraged RMM tools to move laterally across networks. They employed a bring-your-own-vulnerable-driver (BYOVD) technique to disable security defenses and extract credentials from Veeam backup databases, effectively neutralizing recovery mechanisms. To further conceal their activities, the operators blended malicious commands with legitimate application paths associated with backup and virtualization vendors. The Linux encryptor exhibited advanced control capabilities, including hypervisor-specific targeting for ESXi and Nutanix AHV environments. Overall, the campaign demonstrates a highly organized and technically adept operation aimed at enterprise-scale disruption through backup suppression, cross-platform execution, and sophisticated defense evasion. |
Threat Labs summary
Securonix Threat Labs Recommends leveraging these findings to strengthen defenses against these ransomware campaigns.
- Implement detection mechanisms for BYOVD abuse and cross-platform payloads by monitoring unsigned or suspicious driver loads, DLL sideloading activity.
- Enhance visibility across Windows and Linux environments to identify hybrid attack patterns, cross-platform payload deployments, and lateral movement attempts in real time.
- Enforce phishing-resistant multi-factor authentication (MFA) and apply strict conditional access policies.
- Mandate MFA enforcement across all remote access interfaces, including RMM tools and privileged administrative accounts.
- Apply strict network segmentation between corporate IT, operational technology (OT), and cloud management layers to contain lateral movement and limit adversarial propagation.
- Enhance endpoint and network telemetry collection to improve visibility into lateral movement techniques, encryption behaviors, and ransomware precursors.
- Implement file integrity monitoring (FIM) to detect unauthorized file modifications, encryption attempts, or other indicators of tampering across critical systems and directories.
- 128 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Chaos Ransomware include but are not limited to the following:
- Monitor for creation of ransom notes README.txt in multiple system directories.
- Monitor for Mutex – SvcHost_Mutex_7z459ajrk.
- Monitor for encryption activity involving file renaming and extensions appended with [.]chaos.
- Monitor for shadow copy deletions and commands involving vssadmin delete shadows /all /quiet.
- Monitor for creation or execution of suspicious .NET binaries.
TTPs related to the Agenda Ransomware include but are not limited to the following:
- Monitor for creation of unexpected administrative accounts named Supportt.
- Monitor for execution or loading of msimg32.dll and ThrottleStop.sys that act as droppers and subsequently write or deploy driver files to temporary directories.
- Monitor for presence, loading, or installation attempts of the eskle.sys driver and associated behaviors that disable security controls, terminate protection processes, or modify AV components.
- Monitor for rundll32.exe spawning with in-memory DLL loads, especially DLLs located under C:\ProgramData\Veeam\ (for example C:\ProgramData\Veeam\socks64.dll) or other unrecognized Veeam paths.
- Monitor for multiple local SOCKS proxy processes or injected SOCKS proxy DLLs consistent with the COROXY backdoor.
- Monitor for powershell.exe executions with encoded commands (EncodedCommand / -e) that interact with Veeam databases or attempt credential extraction/decryption routines
Tags: Target Sectors: Manufacturing, Transportation, Consumer Services, technology, financial services, healthcare | Target Locations: United States, United Kingdom, Japan, India, France, Canada | Target Systems: Windows endpoints, HMI Endpoints, Veeam backup infrastructure, domain controllers, SQL databases, file servers, ESXi, Nutanix AHV, Windows WSL.
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Nitish Singh and Nikhil Kumar Chadha







