- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
- MSSPs
- Scale multi-tenant security with predictable economics.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Nitish Singh, and Nikhil Kumar Chadha
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in September 2025. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. Each threat has a comprehensive summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below-mentioned threats, refer to our Threat Labs home page.
Last month Securonix Autonomous Threat Sweeper identified and analyzed 4,822 TTPs and IoCs, 171 emerging threats, investigated 77 potential threats, and elevated 16 threat incidents. The top data sources swept against include IDS / IPS / UTM / Threat Detection, Data Loss Prevention, Endpoint Management Systems, and Email / Email Security.
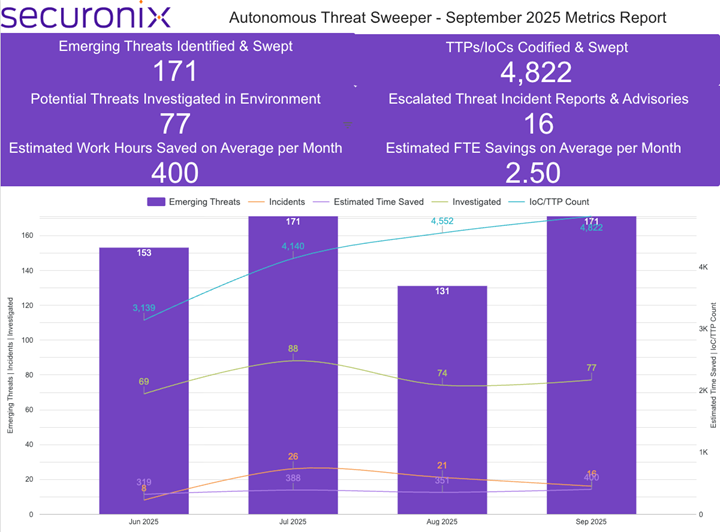
In September 2025, the Autonomous Threat Sweeper team observed a dynamic threat landscape driven by state-aligned operations, evolving backdoors, and increasingly automated phishing and ransomware campaigns. Lazarus targeted DeFi platforms with a layered RAT campaign, Naikon continued espionage across Southeast Asia, and APT37 deployed a Rust-based backdoor and Python loader, while EggStreme malware emerged as a new intelligence-gathering tool. Backdoor activity expanded with the VShell filename-triggered Linux memory-resident variant, AI-driven EviAI malware, modular NotDoor, and an updated Buterat backdoor with advanced evasion. Phishing operations surged, with Homeland Justice targeting diplomatic missions, RaccoonO365 PhaaS attacking Microsoft 365 users, AI-powered phishing content, and Axios-based automation enabling scalable credential theft. Ransomware remained active—Obscura, Yurei, Gunra, The Gentlemen, and Kawa4096 launched new extortion models, while LockBit 5.0 maintained dominance across Windows, Linux, and ESXi systems. The Nimbus Manticore espionage campaign targeted European organizations, highlighting the ongoing focus on strategic intelligence collection. These developments emphasize the growing convergence of AI, automation, and cross-platform threats, underscoring the need for rapid patching, identity and Linux hardening, and proactive detection to mitigate evolving risks.
Recent APT Activities Highlights
(Originally published in August 2025)
A newly identified advanced persistent threat (APT) framework, EggStreme, was observed targeting a Philippine military organization. The attack utilized a fileless, multi-stage toolset leveraging DLL sideloading and reflective loading techniques to maintain persistence and evade detection. Its core component, EggStremeAgent, functions as a fully featured backdoor capable of keylogging, lateral movement, system reconnaissance, and data exfiltration through 58 distinct commands. The framework comprises multiple components—Fuel, Loader, ReflectiveLoader, and Wizard—that communicate via gRPC and use encrypted payloads. The campaign’s complexity and alignment with geopolitical objectives indicate state-sponsored espionage activity.
Another campaign linked to APT37 (North Korea) was identified targeting individuals in South Korea using a Rust-based backdoor and Python loader. The malware, related to the Chinotto and FadeStealer clusters, focuses on espionage and data theft via HTTP-based command-and-control (C2) channels. FadeStealer harvests data from removable media and archives it using embedded RAR utilities before exfiltration. The use of politically themed decoys tied to North Korean affairs suggests targeting of diplomatic and political entities. The activity demonstrates APT37’s continued evolution, leveraging modern programming languages and cloud evasion techniques to enhance persistence and flexibility.
Additionally, interconnected campaigns involving RainyDay, Turian, and a new PlugX variant were observed abusing DLL search order hijacking. Analysis revealed overlapping code, encryption keys, and operational tactics among Chinese-speaking threat actors such as Naikon and BackdoorDiplomacy, indicating possible collaboration. The loaders employ a XOR-RC4-RtlDecompressBuffer decryption chain and similar C2 configurations to deliver payloads directly into memory, bypassing detection. Evidence suggests that the RainyDay backdoor lineage dates back to 2016, with newer PlugX variants adopting identical configuration structures, reinforcing the theory of shared source code and coordinated espionage targeting telecom sectors in Central and South Asia.
In another case, three remote access trojans (RATs) — POOLRAT, PondRAT, and ThemeForestRAT — were attributed to the Lazarus Group. These malware families target Windows, macOS, and Linux systems, showcasing cross-platform adaptability and integration with previously known Lazarus operations. The campaigns use Themida-packed loaders, proxy tools, and Mimikatz-based credential stealers to establish persistence and enable remote command execution. Additional tactics such as DLL phantom loading, timestomping, and reverse proxy deployment were observed. The overlap in infrastructure, configuration, and capabilities underscores Lazarus’ ongoing shift toward unified, multi-OS espionage frameworks.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these APT group’s campaigns.
- Implement proactive hardening and Attack Surface Reduction (PHASR) to restrict legitimate but high-risk tools like wmic.exe and msdt.exe that attackers frequently abuse.
- Block malicious CHM, LNK, and compressed attachments, which APT37 uses for spear-phishing.
- Regularly update Windows Help files and scripting components (mshta.exe, PowerShell) to reduce code injection opportunities.
- Prevent unauthorized DLL loading by implementing application whitelisting and restricting execution directories for legitimate binaries.
- Extend endpoint visibility across Windows, Linux, and macOS to identify indicators linked to POOLRAT, PondRAT, and ThemeForestRAT.
- 142 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the EggStreme include but are not limited to the following:
- Monitor for execution of legitimate binaries (WinMail.exe, xwizard.exe, msdt.exe, MsMpEng.exe, explorer.exe, or winlogon.exe) loading unexpected DLLs such as mscorsvc.dll, xwizards.dll, or ielowutil.exe.mui, indicating potential DLL sideloading.
- Monitor for creation or modification of files in uncommon paths like %APPDATA%\Microsoft\Windows\Windows Mail\, %LOCALAPPDATA%\Microsoft\WindowsApps\, or %WINDIR%\en-US\ containing .mui extensions used to hide encrypted payloads.
- Monitor for creation or modification of on-disk configuration or encrypted files such as %APPDATA%\Microsoft\Windows\Cookies\Cookies.dat or %LOCALAPPDATA%\Microsoft\Vault\Vault.dat, possibly encrypted using RC4 or XOR keys.
- Monitor for process injection behavior involving API calls like VirtualAllocEx, WriteProcessMemory, CreateProcessWithToken, or ResumeThread, particularly when used by non-administrative processes.
- Monitor for registry or file permission modifications granting ownership to BUILTIN\Administrators using APIs like SetEntriesInAclA() or SetNamedSecurityInfoA().
TTPs related to the APT37 (North Korea) include but are not limited to the following:
- Monitor for PowerShell processes reading or decoding embedded payloads and writing executables (C:\ProgramData\3HNoWZd.exe, tele_update.exe) to disk.
- Monitor for creation of scheduled tasks (MicrosoftUpdate), configured to execute 3HNoWZd.exe every 5 minutes using schtasks.
- Monitor for registry Run key modifications under HKCU\Software\Microsoft\Windows\CurrentVersion\Run associated with suspicious executables or names impersonating legitimate services (OneDriveStandaloneUpdater, TeleUpdate).
- Monitor for processes performing Base64 decoding and HTTP POST requests to unknown or suspicious external servers, especially with query parameters such as U= and R=.
- Monitor for execution of renamed legitimate binaries (tele_update.exe) or unusual Python-based executables in system directories.
- Monitor for use of Windows Transactional NTFS (TxF) APIs and functions like CreateFileTransactedW, NtCreateSection, and RollbackTransaction followed by process injection behavior.
- Monitor for recurring use of RAR utilities or creation of password-protected archives (e.g., using hardcoded password NaeMhq[d]q) in %TEMP%\VSTelems_Fade\.
TTPs related to the RainyDay, Turian, and a new PlugX variant include but are not limited to the following:
- Monitor for legitimate executables (such as MicrosoftEdgeUpdate.exe or other trusted applications) loading unexpected DLLs from non-standard directories, indicating DLL search order hijacking.
- Monitor for processes that read, decrypt, and execute shellcode from files with unusual extensions (.afx, .dat, .src) in the executable directory.
- Monitor for use of Windows APIs such as GetModuleFileNameA, RtlDecompressBuffer, and SetUnhandledExceptionFilter by non-standard binaries to decrypt and decompress payloads in memory.
- Monitor for in-memory injection or reflective loading activity where decrypted shellcode is injected into the parent process or a new process like explorer.exe or wabmig.exe.
- Monitor for RC4 and XOR-based encryption routines used to decrypt configuration or payload data, especially when combined with LZNT1 decompression.
- Monitor for processes attempting to gain elevated privileges via SeDebugPrivilege or SeTcbPrivilege acquisition.
- Monitor for recurring outbound C2 beaconing patterns and use of VTCP 10.12.08 library strings within process memory or binaries.
TTPs related to the Lazarus Group include but are not limited to the following:
- Monitor for visits to fake scheduling websites such as calendly[.]live, picktime[.]live, or oncehub[.]co that mimic legitimate meeting tools.
- Monitor for abnormal activity involving the SessionEnv or IKEEXT Windows services, including:
- Creation or loading of phantom DLLs such as TSVIPSrv.dll or wlbsctrl.dll.
- Use of the sc config sessionenv start=auto command.
- Monitor for unauthorized modifications to:
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SessionEnv\RequiredPrivileges
- Particularly if SeDebugPrivilege or SeLoadDriverPrivilege are added.
- Monitor for files named perfh011.dat in System32, indicating encrypted payloads used by PerfhLoader to launch RATs.
- Monitor for creation or execution of tools such as: Screenshotter, Keylogger, Chromium browser dumper, MidProxy, Mimikatz, frpc, and Proxy Mini.
- Monitor for files written to:
- %TEMP%\tmpntl.dat or %TEMP%\TMP01.dat (keylogger output).
- %LocalAppData%\IconCache.log (browser cookie/credential dump).
- %LocalAppData%\Microsoft\Software\Cache (screenshot storage).
- Monitor for unauthorized proxy connections or tunnels using Fast Reverse Proxy (frpc), especially version 0.32.1.
- Monitor for files named netraid.inf (Windows), /var/crash/cups (Linux), or /private/etc/imap (macOS) of ~43 KB in size.
- Monitor for files encrypted using Windows DPAPI, with loader names like DPAPILoader or RemotePELoader.
- Monitor for files being overwritten with random data and renamed multiple times (e.g., AAAAAAA.AAA → BBBBBBB.BBB), used by Lazarus malware to securely erase traces.
- Monitor for Themida-packed executables such as cmui.exe or Quasar variants.
Tags: Threat Actor: APT37 (ScarCruft / Reaper / Velvet Chollima), Suspected Chinese APT group, Naikon and BackdoorDiplomacy (possible collaboration), Lazarus Group (APT38 / Hidden Cobra) | Adversary Origin: China (Chinese-speaking APTs), North Korea | Target Sector: Defense / Military, Political, Diplomatic, and Academia, Telecommunications, Financial, Defense, Technology | Target Location: Philippines, South Korea, Central and South Asia (Kazakhstan, Uzbekistan, etc.), Global (multi-regional targeting) | Target Systems: Windows-based military systems, Individual and institutional Windows machines, Corporate and network infrastructure endpoints, Enterprise and personal endpoints (Windows, macOS, Linux) | Target Platforms: Windows OS, Cross-platform (Windows, macOS, Linux) | Malware / Framework / Tools: EggStreme (multi-component APT framework), Rustonotto (Rust-based backdoor), Chinotto (PowerShell), FadeStealer (Python loader and stealer), RainyDay backdoor, Turian loader, PlugX variant, POOLRAT, PondRAT, ThemeForestRAT, PerfhLoader, DPAPILoader, RemotePELoader
Insights of Phishing Campaigns
(Originally published in September 2025)
| Homeland Justice Phishing Campaign | A sophisticated spear-phishing campaign leveraging a compromised email account from Ministry of Foreign Affairs of Oman. The operation has been attributed to Iranian-aligned threat actors associated with the Homeland Justice group, linked to Iran’s Ministry of Intelligence and Security (MOIS). The attackers distributed emails masquerading as legitimate diplomatic correspondence, targeting embassies, consulates, and international organizations worldwide. These emails contained a malicious Microsoft Word attachment disguised as a registration form, which deployed a malware payload through encoded numerical sequences decoded via embedded VBA macros. Additionally, the attackers used 104 compromised email accounts to distribute 270 phishing emails, indicating a large-scale, coordinated espionage campaign. The operation notably coincided with sensitive ceasefire negotiations involving Hamas, highlighting its geopolitical motivation. |
| RaccoonO365 Phishing Operation | A Phishing-as-a-Service (PhaaS) operation dubbed RaccoonO365, responsible for large-scale credential theft targeting Microsoft 365 users, has been successfully dismantled. The group offered phishing kits and subscriptions-based services to cybercriminals, enabling them to easily launch credential-harvesting campaigns. These phishing campaigns involved emails with malicious links, attachments, or QR codes that redirected victims to a fake Microsoft login page. Before reaching the phishing page, users encountered a CAPTCHA screen designed to appear legitimate. Once victims entered their credentials, RaccoonO365’s system acted as a man-in-the-middle, capturing both passwords and session cookies that allow attackers to bypass MFA and access victim accounts, files, and emails. The group operated a Telegram-based subscription service called RaccoonO365 Suite which offer multiple plans and accepted payments exclusively in cryptocurrency. |
| AI-obfuscated phishing campaign | A credential phishing campaign leveraged AI-generated code within an SVG file to hide its malicious behavior. The attackers utilized a LLM to generate complex, business-themed code that appeared legitimate while secretly executing malicious scripts. The phishing emails were sent from a compromised small business account, disguised as file-sharing notifications with an attachment masquerading as a PDF. When opened, this file redirected users to a fake CAPTCHA page and then led them to a counterfeit login page to steal credentials. Instead of traditional encryption, the attackers encoded the payload using business-related terms such as revenue, operations, and risk, which hidden JavaScript later decoded into active malicious code that redirected users, collected browser data, and tracked their activity. Although this campaign was limited and mainly targeted U.S. organizations, it highlights how attackers are increasingly using AI to create sophisticated and deceptive phishing campaigns. |
| Axios Phishing | A significant surge in stolen credentials tied to automated, large-scale phishing that weaponizes the Axios HTTP client together with Microsoft Direct Send. The attackers abuse the JavaScript HTTP client Axios as a fake user-agent to automate credential phishing workflows from delivering phishing pages and QR-code lures to capturing session tokens, MFA codes, and SAS tokens. Once victims enter their details, attackers can steal session tokens to replay Azure authentication flows, effectively bypassing MFA and gaining access to sensitive APIs. Early attacks focused on executives in finance, healthcare, and manufacturing but the campaign has since expanded to general users, showing its scalability. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these phishing campaigns.
- Enable real-time link scanning to recheck URLs upon user click and block dynamic phishing redirects.
- Activate cloud-delivered protection and Zero-hour Auto Purge (ZAP) to automatically quarantine sent or delivered phishing emails.
- Apply Conditional Access policies and session controls in Azure AD to prevent token replay and session hijacking using stolen SAS tokens.
- Continuously monitor domain clusters, phishing kits, and PhaaS infrastructures that facilitate large-scale credential harvesting.
- Filter or sandbox QR-code–based and Direct Send emails frequently abused in Axios-style phishing operations to bypass email gateways.
- Implement phishing-resistant MFA to mitigate risks from stolen or replayed session and MFA tokens.
- Enhance Email Authentication Controls to reduce spoofed sender exploitation observed in diplomatic phishing and credential theft.
- 121 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Homeland Justice Phishing campaign include but are not limited to the following:
- Monitor for inbound emails originating from @fm[.]gov[.]om, as these may indicate phishing attempts.
- Monitor for the presence or execution of VBA macro functions dddd(), laylay(), and RRRR(), which are used to encoded payloads, avoid sandboxing and execute malicious code using the vbHide parameter.
- Monitor for the creation or modification of files at the path C:\Users\Public\Documents\ManagerProc.log, as this location is used to write decoded payloads prior to execution.
- Monitor for the presence of .log files in public directories, as these may serve as disguised executable payloads masquerading as benign log files.
- Monitor for the execution or persistence of sysProcUpdate.exe, which is used to maintain persistence across system reboots and facilitate C2 communication.
TTPs related to the RaccoonO365 Phishing Operation include but are not limited to the following:
- Monitor for inbound emails containing PDF attachments that appear to originate from DocuSign, SharePoint, Adobe, or Maersk, as threat actors are actively impersonating these brands for phishing delivery.
- Monitor for outbound network traffic to domains ending with [.]workers[.]dev.
Tags: Threat Actor: Homeland Justice| Target Sector: Government, Finance, Health care, and Manufacturing | Target Location: Oman, US | Target Systems: Microsoft 365, Microsoft Direct Send, Azure authentication, MFA workflows.
Backdoor Activity Highlights
(Originally published in September 2025)
| VShell Filename triggered Linux Memory Resident Backdoor | A Go-based backdoor delivered through RAR archives and unsafe shell handling: if automation scripts expand $file directly, a filename with shell metacharacters gets executed. The loader pulls arch-specific ELF (x86/x64/ARM/ARM64), keeps payloads in memory, and talks to C2 with simple XOR—plus support for reverse shells/port forwarding. Overlaps noted with Chinese APTs (UNC5174/Earth Lamia/CL-STA-0048/UNC5221). Watch for shells executing on filenames, curl/wget chains fetching ELF per-arch, and short-lived ELF children of bash. |
| EviAI Malware | Malvertising and look-alike “productivity” installers drop a Node.js backdoor. The chain writes JS to %TEMP%, spawns node.exe, sets a scheduled task (e.g., sys_component_health_{GUID}) and a Run key, then profiles the browser, kills Chrome/Edge, and copies “Web Data/Preferences” for theft before HTTPS C2. Telemetry shows a global victim set (India, US, EU, Brazil) across manufacturing, government, healthcare, retail. Detect node.exe spawned by new apps, that scheduled task name, and bulk reads of browser profile files. |
| NotDoor Malware | A stealthy Outlook-based backdoor that rides Microsoft’s own components. The actor plants/edits VbaProject.OTM, lowers Outlook macro security, and DLL-sideloads via OneDrive.exe to run Base64 PowerShell on command. Tasks can be email-triggered, and stolen files are mailed out as attachments—keeping C2 traffic low-profile. Activity is associated with a Russia-aligned cluster (APT28/Fancy Bear) and observed across NATO countries. Hunt for OneDrive loading unknown DLLs, new VbaProject.OTM, and PowerShell launched from Outlook context. |
| New Buterat Backdoor Malware | A quiet foothold built for staying power. Buterat typically lands alongside a few helper programs, tucks itself under the user profile, and blends into everyday processes. Once established, it injects into trusted apps, decrypts its own strings as needed, and checks in on a simple schedule keeping noise low while it waits for tasks. What to watch: a cluster of similarly named helpers from the same installer, thread-injection by unknown processes, and a brief burst of outbound traffic after logon. |
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these malware/backdoors.
- Turn off or strictly limit macros and alert if Outlook’s macro file changes unexpectedly.
- Stop OneDrive plug-in abuse and only allow OneDrive to load trusted add-ons.
- Fix risky Linux scripts and don’t let file names run as commands; clean and validate inputs in any automation.
- Hunt memory-only Linux malware and alert when a shell script launches a short-lived program that vanishes but keeps a network connection.
- Watch for quiet Windows footholds and investigate when several new helper programs appear together or when an unknown app injects into a trusted one.
- Block fake installers and allow software only from trusted stores/sites; quarantine anything that looks like a “helpful utility” download.
- Flag unusual Node.js activity. On non-developer PCs, investigate if a new install suddenly starts node.exe and adds a scheduled task.
- Protect browser data and alert if a non-browser process closes Chrome/Edge and copies profile files (a sign of data theft).
- 34 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the VShell Filename triggered Linux Memory Resident Backdoor include but are not limited to the following:
- Monitor for inbound RAR attachments where the filename itself contains shell-metacharacters; look for shells executing eval, find, or ls on untrusted $file variables.
- Monitor for second-stage Bash scripts that fetch arch-specific ELF (x86/x64/ARM/ARM64) and then exec a memory-resident backdoor via execve().
- Monitor for XOR-encoded C2 over TCP/UDP and signs of port-forwarding / reverse shells; process names attempting to masquerade as kernel threads.
TTPs related to the EviAI Malware include but are not limited to the following:
- Monitor for users clicking gofile[.]io links and downloading/extracting password-protected archives named like SAP_Ariba_QuoteBuilder_v2.zip.
- Monitor for node.exe spawned by newly-installed “productivity/utility” apps; JS payloads stored in %TEMP% then executed silently.
- Monitor for scheduled task sys_component_health_{GUID} repeating every 4 hours; Run key entries that auto-start the dropper.
- Monitor for WMI/PowerShell discovery of browsers, followed by taskkill /F /IM msedge.exe / chrome.exe, and copying “Web Data”/“Preferences” files suffixed with Sync.
TTPs related to the NotDoor Malware include but are not limited to the following:
- Monitor for OneDrive.exe loading an unexpected DLL (DLL side-loading, e.g., SPSCUl.dll/SPSCUI.dll paths under C:\ProgramData\…).
- Monitor for creation or modification of VbaProject.OTM and Outlook security keys (e.g., Software\Microsoft\Office\16.0\Outlook\Security\Level).
- Monitor for email-triggered command execution and Base64-encoded PowerShell spawned from Outlook context; exfil as email attachments from %TEMP%.
TTPs related to the New Buterat Backdoor Malware include but are not limited to the following:
- Monitor for droppers named amhost.exe, bmhost.exe, cmhost.exe, dmhost.exe, lqL1gG.exe landing under user profiles.
- Monitor for outbound to ginomp3.mooo[.]com.
- Monitor for thread-injection behavior using SetThreadContext, plus encrypted/obfuscated strings at runtime.
Tags: Target Sector: Government, Enterprise, Manufacturing, Healthcare, Retail | Target location: Global | Threat actor: APT28 / Fancy Bear| Malware: NotDoor, VShell, Buterat, EvilAI | Target system: Microsoft Outlook / Office, Linux servers | Target platform: Windows, Linux
Cyber-Espionage: Nimbus Manticore Targets Europe
(Originally published in September 2025)
An Iranian state-aligned threat actor, Nimbus Manticore (also known as UNC1549 or Smoke Sandstorm), has intensified cyber-espionage operations targeting defense, telecommunications, and aerospace sectors across Denmark, Sweden, Portugal, and Israel. The campaign exhibits nation-state–level sophistication aligned with IRGC intelligence goals
Attackers use spear-phishing emails impersonating HR recruiters on LinkedIn and Outlook, luring victims to fake job portals themed after companies like Boeing and Airbus. These deliver malicious ZIP files that trigger a multi-stage DLL sideloading chain exploiting low-level Windows APIs for stealth
The campaign employs two main tools: MiniJunk, an evolved backdoor capable of file access, process creation, and data exfiltration; and MiniBrowse, a lightweight browser credential stealer. Both features encode C2 communications, heavy obfuscation, and use Azure App Service and Cloudflare for resilient infrastructure.
A related cluster, Subtle Snail, shares overlapping code and infrastructure but uses less obfuscated payloads, indicating shared development resources.
The operation reflects persistent Iranian espionage efforts leveraging code signing, DLL sideloading, and cloud-based C2 to evade detection. Its timing alongside Iran–Israel tensions highlights Iran’s continued pursuit of strategic intelligence collection in Europe and the Middle East.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these ransomware groups.
- Deploy advanced email filtering and sandbox analysis to detect spear-phishing attempts impersonating HR or defense organizations.
- Enforce URL rewriting and time-of-click protection to block malicious career portals hosted on domains like *.azurewebsites[.]net or those mimicking aerospace and telecom firms.
- Block DLL sideloading behavior through application control and process integrity policies.
- Implement TLS inspection to detect anomalous HTTPS traffic using non-standard User-Agent strings (“WinHTTP Example”).
- Disable the saving of passwords in Edge and Chrome, especially on high-value endpoints.
- Ensure all Windows components (particularly Windows Defender binaries) are fully patched to mitigate DLL hijacking vulnerabilities.
- Regularly verify third-party code signing certificates to detect misuse of legitimate signing services.
- 165 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Nimbus Manticore include but are not limited to the following:
- Monitor for inbound emails or LinkedIn messages that impersonate HR recruiters or defense contractors (Boeing, Airbus, Rheinmetall, FlyDubai) containing links to career portals or ZIP file attachments.
- Monitor for downloads of ZIP archives (Survey.zip, JobOffer.zip) followed immediately by execution of embedded .exe files.
- Monitor for creation or loading of DLLs (userenv.dll, xmllite.dll, dxgi.dll) from temporary or user profile folders, especially when the legitimate version resides in C:\Windows\System32\.
- Monitor for process creation events involving low-level Windows API calls such as RtlCreateProcessParameters or RtlCreateUserProcess, which are rarely used in benign contexts.
- Monitor for creation of scheduled tasks or registry autorun keys pointing to executables under %AppData%\Local\Microsoft\MigAutoPlay\.
- Monitor for file renaming operations where Setup.exe or userenv.dll are copied and renamed as MigAutoPlay.exe or similar.
- Monitor for network POST requests from browser processes (chrome.exe, msedge.exe) sending files such as Login Data or Web Data to unknown servers.
- Monitor for frequent invocation of API-resolving functions (repeated GetProcAddress or GetModuleHandle calls), which can indicate obfuscated backdoors.
Tags: Threat Actor: Nimbus Manticore | Aliases: UNC1549, Smoke Sandstorm, Iranian Dream Job, Subtle Snail (linked cluster) | Target Sectors: Defense Manufacturing, Aerospace and Aviation, Telecommunications (especially satellite communications), Airlines, Government and Security Organizations, Technology and IT Service Providers (secondary impact) | Target Locations: Primary: Western Europe — Denmark, Sweden, Portugal, Secondary: Israel (historic targeting) and United Arab Emirates (UAE), Operational Reach: Expanding into European defense supply chains | Target Systems: Windows-based endpoints and servers, Systems running Microsoft Defender components (abused for DLL hijacking), Corporate user workstations — especially those used by HR, R&D, and engineering staff in defense and telecom sectors | Target Platforms: Windows OS (primary), Microsoft Azure Cloud Services — abused for command-and-control (C2) hosting, Web browsers: Microsoft Edge and Google Chrome (via credential-stealing modules)
Ransomware Landscape Evolution: Emerging & Resurgent Threats
(Originally published in September 2025)
The past month witnessed a surge in ransomware activity marked by the resurgence of established actors and the emergence of several new, sophisticated groups. These developments underscore the growing professionalization, diversification, and cross-platform targeting trends within the ransomware ecosystem.
| LockBit 5.0: Cross-Platform Resurgence | LockBit 5.0 resurfaced after earlier disruptions, showcasing a major technical evolution while retaining its core architecture. The latest variant reinforces cross-platform targeting with dedicated payloads for Windows, Linux, and VMware ESXi, employing advanced obfuscation and anti-forensic techniques such as ETW patching and event log wiping to evade detection. It also features 16-character randomized file extensions, regional avoidance mechanisms, and faster encryption, particularly on ESXi systems, where it can encrypt virtual infrastructures in a single execution. |
| Kawa4096: Psychological Warfare Through Brand Mimicry | Kawa4096, a newly identified ransomware operation, adopts psychological manipulation as part of its strategy by mimicking branding and interfaces of well-known ransomware like Akira to induce panic and legitimacy among victims. It uses the Salsa20 cipher with partial encryption to optimize performance, employs mutex locking to avoid redundant processes, and deletes all Volume Shadow Copies to hinder recovery. Its infrastructure includes a Tor-based negotiation portal, and its double-extortion model highlights growing operational sophistication among emerging actors. |
| The Gentlemen: Tailored Attacks on Enterprise Networks | The Gentlemen ransomware group represents a tailored, enterprise-focused threat known for developing custom payloads and tools to disable specific security solutions. Their campaigns have targeted multiple sectors, including manufacturing, healthcare, and construction, across 17 countries. The group demonstrates advanced tactics such as Group Policy abuse, privilege escalation via PowerRun, and data exfiltration using encrypted channels like WinSCP. Their meticulous operational approach, complete MITRE ATT&CK mapping, and sustained persistence through remote tools indicate a highly organized and professional adversary. |
| Gunra Ransomware: A Global Threat Avoiding U.S. Targets | Gunra Ransomware emerged as a double-extortion actor that strategically avoids U.S. targets while focusing on victims in Asia, Europe, and the Middle East. Notably, its operations feature WhatsApp-themed negotiation portals hosted on Slack infrastructure and multiple Tor-based victim panels. Gunra uses Microsoft-themed phishing lures for initial delivery, with executables capable of encrypting terabytes of data rapidly using ChaCha20/Salsa20. Despite inconsistencies in ransom demands, the group’s infrastructure and expanding Linux variant reflect its ongoing evolution toward a hybrid cloud-oriented ransomware model. |
| Yurei: The Ghost of Open-Source Malware | Yurei, another newcomer, demonstrates how open-source ransomware codebases are increasingly enabling low-skilled actors to enter the threat landscape. Built upon publicly available code, Yurei targets organizations primarily in South Asia and Africa, encrypting files using ChaCha20 and leveraging Go-based concurrency for faster execution. However, operational oversights, such as failure to remove system shadow copies—reveal limited sophistication. Despite this, its rapid proliferation signals the growing scalability of open-source ransomware threats. |
| Obscura: A Stealthy Enterprise-Scale Infiltrator | Finally, Obscura ransomware has surfaced as a stealthy, enterprise-scale variant developed in Go, exhibiting domain-level propagation capabilities. It spreads through Windows domain controllers, leveraging scheduled tasks and shared network resources for lateral movement. The ransomware terminates a wide range of security and backup processes, deletes shadow copies, and uses XChaCha20 encryption with structured metadata headers. Its operational design reflects an experienced development team adept at coordinated enterprise intrusions. |
Threat Labs summary
Securonix Threat Labs recommends leveraging these findings to strengthen defenses against these ransomware campaigns.
- Protect VMware ESXi and Linux servers with strict access controls, multi-factor authentication (MFA), and network segmentation.
- Isolate critical systems, ensuring file servers and backups aren’t accessible from endpoints.
- Implement kernel-mode driver signing enforcement to block exploitation of signed but vulnerable drivers (KillAV tools).
- Protect both Windows and Linux environments against ChaCha20/Salsa20-based encryption attacks.
- Block and monitor Go-based executables built from open-source ransomware templates (Prince-Ransomware).
- Restrict write permissions to SYSVOL and NETLOGON, ensuring only trusted admins can modify scripts or policies.
- 43 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the LockBit 5.0 ransomware include but are not limited to the following:
- Monitor for processes that patch or disable Event Tracing for Windows (ETW) functions such as EtwEventWrite or invoke EvtClearLog API to wipe event logs post-execution.
- Monitor for creation of files with randomized 16-character extensions following encryption activities across Windows, Linux, or ESXi systems.
- Monitor for creation of or access to ransom notes named ReadMeForDecrypt.txt across user and system directories.
- Monitor for command-line execution of binaries containing parameters such as -d, -b, -i, -v, or –m, particularly when used to define encryption or exclusion directories.
TTPs related to the Kawa4096 Brand Mimic Ransomware Extortion include but are not limited to the following:
- Monitor for execution of suspicious processes that automatically restart with command-line arguments like -all, indicating potential self-relaunch or full encryption routines.
- Monitor for creation of a mutex named “SAY_HI_2025”, which may indicate the ransomware is preventing multiple instances from running simultaneously.
- Monitor for termination of legitimate processes such as sqlservr.exe, excel.exe, outlook.exe, winword.exe, or powerpnt.exe prior to file encryption, a common pre-encryption cleanup step.
- Monitor for creation of files with extensions matching the format .., suggesting encryption by Kawa4096.
- Monitor for the appearance of ransom note files named “!!Restore-My-file-Kavva.txt” in multiple directories, especially in system roots or user folders.
- Monitor for commands executed via vssadmin.exe or wmic shadowcopy delete that delete shadow copies or backups (vssadmin.exe Delete Shadows /all /quiet).
TTPs related to the Gentlemen Enterprise Wide Double Extortion include but are not limited to the following:
- Monitor for abuse of legitimate signed drivers (ThrottleBlood.sys) or tools (All.exe, Allpatch2.exe) attempting to terminate or disable endpoint security processes.
- Monitor for execution of PowerRun.exe to perform high-privilege operations or disable security controls.
- Monitor for registry modifications weakening authentication or enabling insecure RDP access, such as:
- RestrictSendingNTLMTraffic = 0
- DisableRestrictedAdmin = 0x0
- RDP security layer changes under HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server.
- Monitor for encoded PowerShell commands querying domain controllers ((Get-ADDomain).PDCEmulator).
- Monitor for WebDAV connections to multiple internal shares (davclnt.dll, DavSetCookie) potentially indicating data collection or exfiltration staging.
- Monitor for outbound encrypted file transfers using WinSCP to unknown external IPs or domains.
- Monitor for PowerShell commands disabling Windows Defender (Set-MpPreference -DisableRealtimeMonitoring $true) or adding exclusion paths/processes.
- Monitor for dropping of ransom notes (README-GENTLEMEN.txt) or appearance of the file extension .7mtzhh.
TTPs related to the Gunra Ransomware include but are not limited to the following:
- Monitor for spear-phishing attachments or links leading to executables named similarly to Net-Admin-Supporto-Remoto-.ClientSetup.exe, which have been associated with ConnectWise misuse and remote-access trojans.
- Monitor for execution of binaries that create .ENCRT extensions on files — this marks the encryption phase of Gunra infections.
- Monitor for processes invoking wmic.exe with queries like SELECT * FROM Win32_ShadowCopy WHERE ID=’{8FD052FE-440B-4B35-B239-BD9DD042C664}’, which indicates shadow copy deletion (anti-recovery).
- Monitor for creation of mutexes such as kjsidugiaadf99439, which may be unique to Gunra infections.
- Monitor for binaries compiled with Microsoft Visual C/C++ or GCC 14.2.0–17 targeting x64 Linux systems, particularly if they perform encryption using Salsa20 or ChaCha20 stream ciphers.
- Monitor for creation or modification of files titled R3ADM3.txt, as this ransom note format is inherited from Conti and reused by Gunra.
TTPs related to the Yurei Ransomware include but are not limited to the following:
- Monitor for processes that append the “.Yurei” file extension or modify large volumes of files within a short time period.
- Monitor for use of ChaCha20 encryption routines and ECIES public-key operations originating from non-standard executables.
- Monitor for the creation of _README_Yurei.txt ransom notes in multiple directories.
- Monitor for attempts to change the desktop wallpaper using PowerShell or .NET assembly compilation under temporary paths like %TEMP%\Wallpaper.png.
- Monitor for binaries referencing or compiled from Prince-Ransomware or SatanLockV2 codebases, or containing directory strings like D:\satanlockv2\.
TTPs related to the Obscura Ransomware include but are not limited to the following:
- Monitor for executables appearing in domain controller paths such as C:\WINDOWS\sysvol\sysvol\[domain].local\scripts\ — indicating possible abuse of the NETLOGON share for widespread deployment.
- Monitor for Go-compiled binaries with embedded base64-encoded data or ransom notes written as README_Obscura.txt or C:\README-OBSCURA.txt.
- Monitor for scheduled tasks named SystemUpdate or with random alphanumeric names (iJHcEkAG) that execute from NETLOGON or Temp directories.
- Monitor for command-line executions of cmd.exe /c vssadmin delete shadows /all /quiet — a strong signal of shadow copy deletion to prevent recovery.
- Monitor for RDP being enabled via commands like netsh firewall set service type = remotedesktop mode = enable — especially when executed by non-administrative users or scripts.
- Monitor for newly created or modified ransom note files named README_Obscura.txt across multiple endpoints.
Tags: Ransomware: LockBit, Kawa4096, The Gentlemen, Gunra, Yurei, Obscura | Target Sectors: Enterprise networks, Virtualization service providers, Critical infrastructure, IT/Cloud environments, Finance, Education, Managed services, Technology, Manufacturing, Construction, Healthcare, Insurance, Government contractors, Food manufacturing, Supply chain, Small and mid-sized enterprises (SMEs), IT-managed service providers, Cloud, virtualization-dependent businesses. | Target Locations: Global (including Europe, Asia-Pacific, North America), Japan, United States, Global spread (multinational firms), Global (notably Thailand, U.S., Asia-Pacific, 17 countries total), South Korea, Brazil, UAE, Egypt, Canada, Panama, Europe, Sri Lanka, India, Nigeria (developing markets), Global (likely North America & Europe targets) | Target Systems: Windows endpoints, Linux servers, VMware ESXi hosts, Windows, Domain controllers, Enterprise networks, Endpoints, Windows (EXE), Linux (ELF), Windows servers
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected].
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Dheeraj Kumar, and Sina Chehreghani







