- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, and Ella Dragun
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in December. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. Each threat has a comprehensive threat summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below-mentioned threats, refer to our Threat Labs home page.
In December 2023, Threat Labs analyzed and monitored the following major threat categories: exploitation of CVE-2023-26360, Play ransomware group breach, new cyber espionage threat targeting the US aerospace industry, sophisticated Star Blizzard attacks, and Operation HamsaUpdate.
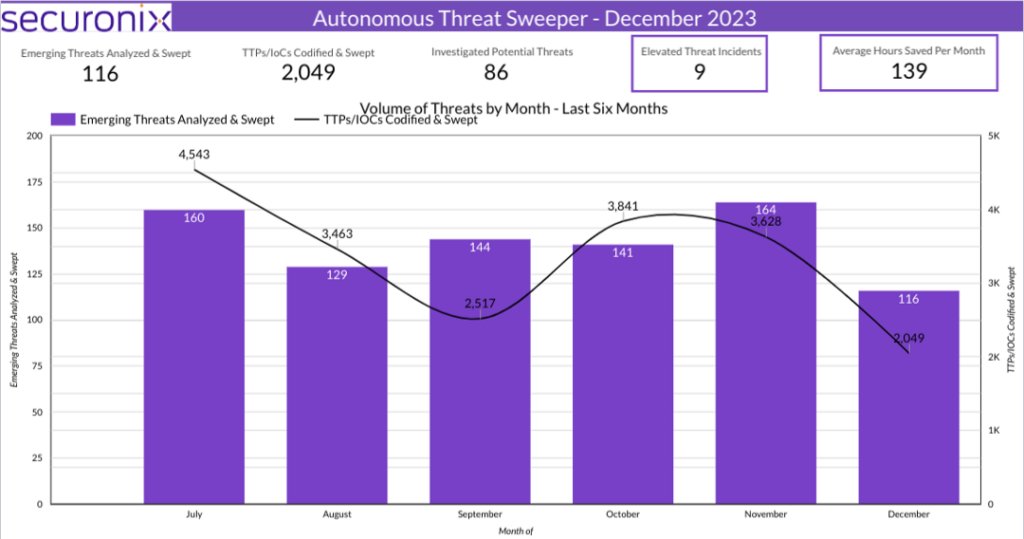
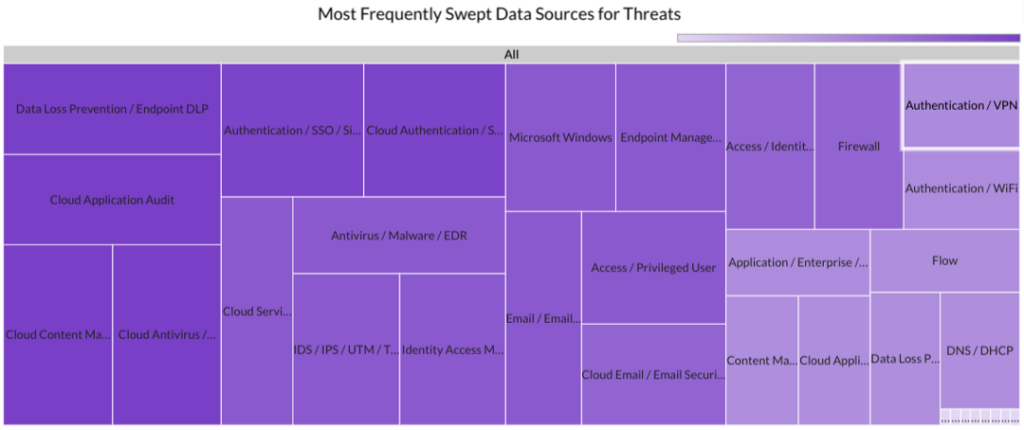
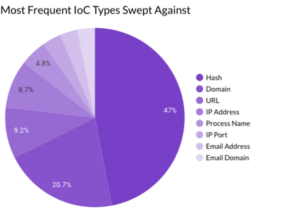
In December 2023, Securonix Autonomous Threat Sweeper identified 4,383 TTPs and IoCs, analyzed 164 emerging threats, investigated 183 potential threats and elevated 10 threat incidents The top data sources swept against include IDS/IPS/UTM/Threat Detection, Endpoint Management Systems, Data Loss Prevention, and Email/Email Security.
Exploiting CVE-2023-26360
(Originally published in December 2023)
The U.S. CISA issued a warning this month about threat actors aggressively exploiting a critical vulnerability (CVE-2023-26360) in Adobe ColdFusion to breach government agencies.
This weakness is an Improper Access Control that can let a remote attacker execute arbitrary code. The vulnerability can also lead to arbitrary file system read and memory leak.
The vulnerability has impacted Adobe ColdFusion versions 2018 Update 15 (and earlier) and 2021 Update 5 (and earlier).
Earlier this year, threat actors exploited the vulnerability against government agencies. During that time the flaw was a zero-day and U.S. CISA added the critical vulnerability CVE-2023-26360 with a CVSS score of 8.6.
The US Cyber Defense Agency warned this time that threat actors are still exploiting the flaw CVE-2023-26360 in targeted attacks and shared that the attacks breached two federal agency systems in June. The impacted servers were both running outdated versions of Adobe ColdFusion.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures against increased threats from this campaign.
- Continually perform backups and store the results offline or on a different network.
- On your computer, smartphone, and other connected devices, turn on automatic software upgrades whenever possible.
- Conduct employee awareness training regularly.
- Secure configurations and incident response planning.
- Continual vigilance, proactive security measures, and staying informed about emerging threats are essential in safeguarding against malware, BlueCharlie specifically.
- Use a trusted antivirus and internet security software suite on all connected devices, including your computer, laptop, and mobile.
- Avoid opening email attachments without first verifying their legitimacy and clicking on dubious links.
- 7 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Attack Type: Exploitation | Impact: The vulnerability could also lead to arbitrary file system read and memory leak.| Target Product: Adobe ColdFusion versions 2018 Update 15 (and earlier) and 2021 Update 5 (and earlier).
The Play ransomware group breach
(Originally published in December 2023)
This month the FBI, CISA, and the Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC) posted their combined advisory about Play ransomware, with analysis, tactics, techniques, and procedures (TTPs). Play ransomware actors use a double-extortion model, encrypting systems after exfiltrating data, and have big impacts on a wide range of businesses and critical infrastructure organizations in North America and South America.
This group was responsible for multiple severe attacks on major American cities and was responsible for more than 300 successful incidents since 2022.
The threat actors used a variety of tools and tactics to steal information and to scan for and disable antivirus software.
This group usually adds the .play extension to filenames after splitting compromised data into smaller groups and exfiltrating it to hacker-controlled accounts.
The hackers use targeting to get account credentials and public-facing applications, specifically targeting vulnerabilities CVE-2018-13379 and CVE-2020-12812 in popular products like the FortiOS , as well as ProxyNotShell vulnerabilities in Microsoft tools.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy defensive measures against these campaigns.
- Continually perform backups and store the results offline or on a different network.
- On your computer, smartphone, and other connected devices, turn on automatic software upgrades whenever possible.
- Conduct employee awareness training regularly.
- Secure configurations and incident response planning.
- Continual vigilance, proactive security measures, and staying informed about emerging threats are essential in safeguarding against malware, BlueCharlie specifically.
- Use a trusted antivirus and internet security software suite on all connected devices, including your computer, laptop, and mobile.
- Avoid opening email attachments without first verifying their legitimacy and clicking on dubious links.
- 9 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: APT Group: Play ransomware| Goal: targeting account credentials and public-facing applications in popular products like the FortiOS with vulnerabilities CVE-2018-13379 and CVE-2020-12812, as well as ProxyNotShell vulnerabilities in Microsoft tools | Target Geo-Location: North America, South America |
Spear phishing campaigns
(Originally published in December 2023)
An adversary known as AeroBlade, which was initially targeted in September 2022 during a “testing phase,” has been seen launching cyberattacks against the aerospace organization over the past year. The adversary used updated tools in July 2023 after first targeting the organization in September 2022.
The two campaigns used identical lure documents, provided a reverse shell as the ultimate payload, and used the same IP address for the command-and-control (C&C) server, all of which suggested that they were focused on cyber espionage. On the other hand, the second attack was more covert and used more evasion strategies, and the final payload had more capabilities.
Cyber Experts claim that the spear-phishing email used in both attacks contained a malicious Word document. Upon opening, the page used a remote template injection technique to introduce an additional step that ran an XML file, generating a reverse shell.
The threat actor known as COLDRIVER has been improving its detection evasion techniques while continuing to steal credentials from organizations that Russia considers strategically important. Star Blizzard (formerly SEABORGIUM) is the cluster that the Microsoft researchers are monitoring. Other names for it include Gossamer Bear, Calisto (sometimes written Callisto), Blue Callisto, BlueCharlie (or TAG-53), and TA446.
The adversary, the report said, “continues to heavily target academic institutions, information security firms, and other entities aligned with Russian state interests, as well as individuals and organizations involved in international affairs, defense, and logistics support to Ukraine.”
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these phishing campaigns.
- The threat actors used identical lure documents in the phishing stage of both operations and the ultimate payload was a reverse shell connecting to the same C2 IP address.
- The researchers hypothesize that the purpose of the data theft was to either sell the knowledge, give it to rival aerospace companies abroad, or use it as leverage to blackmail victims.
- Researchers reported seeing the attacker use server-side scripting, eschewing hCaptcha in favor of rerouting the browser session to the Evilginx server, to thwart automated scanning of the actor-controlled infrastructure beginning in April 2023.
- The server-side JavaScript code is made to determine whether the page is being viewed by an automation tool such as Selenium or PhantomJS and to see whether any plugins are installed in the browser. It then sends the information back to the server as an HTTP POST request.
- 252 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the spare phishing attacks include but are not limited to the following:
- Monitor for Detect Spear-Phishing FROM EmailLogs
- Monitor for Execution Chain FROM ProcessLogs
- Monitor for weblogs for user agent
Tags: APT Group: AeroBlade | Target Geo-Location: United States | Targeted Organizations: US Aerospace Sector | Attack Type: Spear-phishing
Operation HamsaUpdate
(Originally published in December 2023)
A highly organized and focused attack on Israeli infrastructure is exemplified by the Hamsa Wiper campaign. The Israel National Cyber Directorate issued an urgent alert warning on December 19th about a phishing attempt that was specifically targeting Israeli users of F5’s network devices. This initiative is known as Operation HamsaUpdate. It involves the introduction of a recently created malware called Wiper that targets Linux and Windows servers. The effort uses sophisticated social engineering techniques along with a convincingly written email in Hebrew to coerce victims into running the malicious code on their servers. The last attack provides a destructive wiper or a multi-stage loader, each version tailored for Windows or Linux systems.
Threat Labs summary
The following main events and techniques during Operation HamsaUpdate are summarized below. .
- The spearhead of the attack is a deftly constructed phishing email that is notable for its flawless Hebrew, devoid of the common typos and grammar mistakes found in such schemes. The email’s content demonstrates a highly skilled use of social engineering, evoking a strong sense of urgency in the recipient.
- The “Handala Hack Team” has taken credit for several recent cyberattacks. They portray themselves as a recently established group of pro-Palestinian activists, but it’s unclear who these people are behind the scenes on social media.
- There are two known ZIP file variations that are supplied for the Windows version. The single file in both ZIP files is an executable called F5UPDATER.EXE, a.NET program that appears to be an F5 system update tool. It acts as the attack’s initial stage loader.
- Upon examination of the downloaded script, it was discovered to contain an obfuscated payload. The ‘eval’ command is used to execute the payload, which is hidden via five Base64 encoding steps. After decoding, it turns out to be a bash script designed to wipe data.
- 17 IoCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Attack Type: Phishing | Target Geo-Location: Israel | Targeted Product: F5’s Network Devices | Malware: Wiper | Target System: Windows and Linux Servers
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at scia@securonix.com.
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Sina Chehreghani, Dhanaraj K R