- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Security Analytics, SIEM
By Abhishek RVRK Sharma, Senior Technical Marketing Engineer at Securonix
From a security standpoint, today’s enterprise IT environment has changed significantly over the past few years. A few years ago, a security analyst would have had to deal with separate dashboards for their antivirus, email gateway, firewall, switches and routers, and load balancers on several different screens.

Look familiar? Today’s security analyst works with a very different set of tools in order to deal with a threat landscape where the rules of the game have changed. The number of security-oriented infrastructure solutions has shot up; from identity and access management (IAM) solutions to cloud-based SD-WAN, today’s networks are both a lot more diverse as well as a lot more populated. This has brought a couple of security facts into focus:
- Data overload – Security systems now must manage an overload of information from a variety of data types including logs, network traffic, internet of things (IOT) events, threat intelligence, and more.
- Complicated attacks – Attacks today don’t take place in an instant but are spread out over a period of time. Multiple stages are involved in the modern threat chain including information gathering (reconnaissance), infiltration, delivery, and more.
Clearly, relying on a single indicator of compromise (IOC) – without any context around that activity – is no longer a good way to find threats. IOCs need to be tied together in a pattern in order to accurately track and prioritize threats.
How can security analysts correlate millions of alerts across a variety of event types to identify a pattern of attack?
Enter Threat Chains
In order to combat evolving threats that happen over a period of time, you need to be able to stitch together related alerts. This allows you to prioritize and identify low, slow threats that occur over several steps. These events or alerts may not be significant on their own, but when tied together into a threat chain connected to a single entity (user, IP address, login ID, etc.) it can indicate a severe security event.
Securonix threat chain models are based on industry standard threat modelling, including the MITRE ATT&CK framework and US-CERT Cybersecurity Framework, among others.
How Is a Threat Chain Created?
Threat chains are enabled by connecting threats to entities. In a typical threat chain, a single event may not be an event of significant interest. However, as multiple related events get tagged to the same entity, the significance of each event grows. When tied together the total risk from multiple related events is much more than the sum of the individual incidents. Individual IOCs in the threat chain can be either behavior based, or defined rules and alerts from other security tools.
Relationship Tracking and Pivoting Across Entity-Linked Assets
Most alerts use different identifiers depending on the solution. For example, firewall-identified threats are differentiated using IP addresses, while login failure alerts would link to user IDs. The Securonix analytics engine can identify the relationships across all assets linked to an entity.
Behavioral Analytics
Behavior analytics uses machine learning to automatically learn normal baselines and detect outlier activities in your environment. This is critical in today’s complex environment where a traditional rule-based approach would result in an abundance of false positives.
A Sample MITRE-Based Threat Chain
One of the most structured and universally recognized threat chain frameworks is the MITRE ATT&CK framework. The framework includes a comprehensive list of attacks and illustrates how these attacks can be chained together for successful infiltration. Securonix threat chains work in conjunction with the MITRE model.
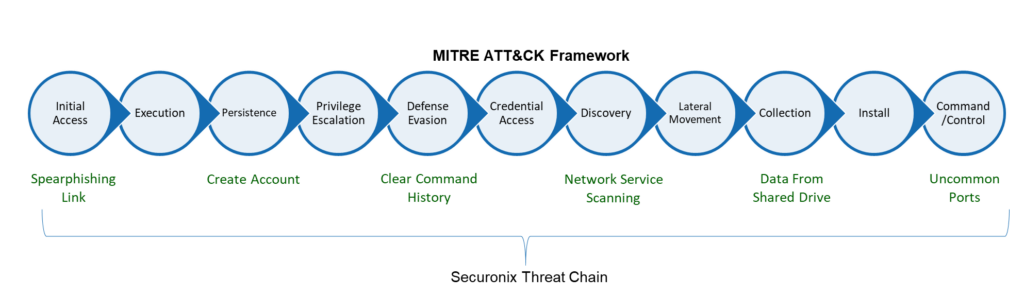
The threat chain above is mapped to the MITRE ATT&CK framework.
- An employee inadvertently clicks on a spearphishing link in an email, giving the attacker access their credentials (corresponding to the Initial Access and Execution stages on the MITRE matrix).
- The attacker uses the credentials to create a new account to ensure persistence, then uses system commands to escalate the account’s privileges (Persistence and Privilege Escalation).
- The attacker erases any trace of their work by removing entries from system logs (Defense Evasion).
- The attacker uses the escalated privileges of the compromised account to gain access to internal systems and probes the network to see what they can discover (Credential Access, Discovery and Lateral Movement).
- Identifying sensitive data, the attacker accesses the shared drive and starts exfiltrating data to the attacker’s destination of choice (which may happen over ports that are not commonly used) (Collection, Install, and Command/Control).
Risk Modeling
Once the threat chain is identified, risk modeling is used to elevate the risk associated with the attack. The Securonix risk modeling algorithm utilizes two scoring models, static and exponential scoring, to assign risk values to chained alerts.
Static scoring works best for known, preconfigured threat models where a set of events happening collectively indicate a significantly elevated risk. For example, a user copying a large amount of data across the network may not be a high-risk event, but if the user is a flight risk, it elevates the event’s risk score.
Predictive exponential scoring works in situations where a threat event escalates in importance as events occur that move the attempt through multiple threat stages. For example, a reconnaissance attempt made by a tool such as Nmap is not identified as high risk by itself. When the attacker identifies an open port and attempts to gain access the risk score is increased substantially.
Securonix offers multiple threat chain solutions as packaged content for common use cases, along with the ability to create your own threat chains for threats that may be unique to your environment. Packaged applications focus on specific industry and threat use cases, covering a wide gamut of threats in associated areas.
Don’t let legacy SIEM security slow you down.Download this whitepaper to learn more about intelligent threat analytics from Securonix. |


