- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
The phrase “Mind the Gap” has its origins in the London Underground, specifically the subway system known as the Tube. The phrase was used to alert passengers to the potential danger posed by the gap between the train and the platform.
Gaps in security coverage also pose a risk as it allows threat actors or insiders to exploit vulnerabilities. That’s why Securonix created a solution that helps security professionals leverage our Unified Defense SIEM to “mind the gap” and boost ROI while protecting your environment’s entry points. Securonix now lets you easily see your coverage, and gaps in coverage, in a single dashboard.
Security information and event management (SIEM) solutions are used to solve the complex challenge of detecting and responding to cyber and insider threats. Although SIEMs are complex tools, using them shouldn’t be complicated.
To make using a SIEM less complicated and gain ROI faster, Securonix introduced Threat Coverage Analyzer. This terrific capability helps security professionals identify and close gaps in threat coverage, recommend and get help implementing use cases, and understand the before and after picture of your MITRE ATT&CK or Insider Threat coverage.
How does Threat Coverage Analyzer work?
Many organizations want to adopt the highly-regarded MITRE ATT&CK framework, and with good reason. MITRE ATT&CK helps you take data collection further by providing a framework to understand threat actors’ tactics and techniques throughout the entire attack sequence. This framework greatly helps organizations increase their security posture. While organizations recognize the importance of embracing a holistic view of the threat chain, the question remains: How can you ensure that there are no visibility gaps in your SIEM?
Threat Coverage Analyzer, now available in the Securonix Unified Defense SIEM, takes the guesswork out of instituting MITRE ATT&CK, PCI, insider threat and more. With Threat Coverage Analyzer’s planner feature, security professionals can type in a capability for MITRE’s technique Microsoft Windows Powershell and see the total MITRE coverage that Securonix policies can offer. This analysis includes how many of the top 10 techniques are covered, the number of tactics and techniques, and much more.
The Advisor feature then allows analysts to reference the MITRE tactics and techniques from Threat Coverage Analyzer rather than navigating to the MITRE ATT&CK website directly. It also provides the content of the exact version of the ATT&CK framework used in the Threat Coverage Analyzer for easy alignment.
A very beneficial advisor that a lot of customers like is the APT Advisor as this unique capability allows customers to view MITRE techniques associated with their industry or their industry’s targeted APT groups. This information can then be leveraged in the planner to strategically deploy new tools or data sources for protection.
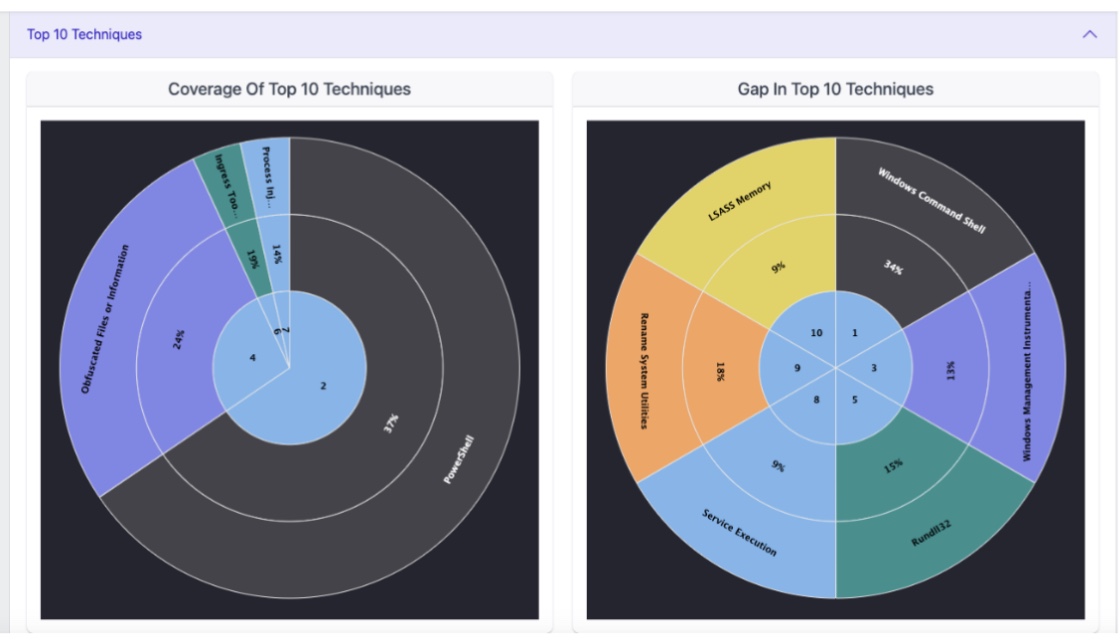
An example of MITRE ATT&CK tactic coverage information Threat Coverage Analyzer’s planner feature gives you.
What about understanding what frameworks you can cover based on your current data sources?
Planning is great, but it’s also critical to understand the current state of your cybersecurity posture. Threat Coverage Analyzer features reflectors that give you an understanding of the data sources you currently are feeding into the SIEM and how well those sources map to the MITRE framework. This current state analysis is visualized with dashboards and gives you an idea of what is covered today. Paired with the Planner, you’ve got the tools you need to see the current state versus the future state for SIEM content and coverage.
What if I don’t have a framework to adhere to or just want advice on what policies to institute?
Needing advice on what policies to institute is a common concern and one that is addressed with Threat Coverage Analyzer. Our solution actually helps recommend policies based on your personalized survey results within the tool. With Securonix Security Assessment (SSA), you have access to an interactive survey that produces measurements that will help you identify SOC maturity gaps in the following areas: Processes, KPIs, data source ingestion, watchlists, threat intel integrations, threat hunt capabilities, vulnerability management activities/processes, risk assessment, SOAR capabilities, staffing needs, training needs, threat team capabilities, physical security, and more.
What if I’m transitioning from a different SIEM to Securonix Unified Defense SIEM?
Due to the heartburn associated with switching vendors, many organizations will stay with their chosen SIEM until it becomes legacy technology. Transitioning to a new SIEM can be painful because the organization loses the sunk cost from its previous SIEM for content, policies, or use cases.
Would you appreciate help migrating your specific organizational use cases to Securonix? That’s where Use Case Migration (UCM) comes in. UCM will recommend possible matches based on our 2,000 out-of-the-box content library. UCM uses fuzzy matching and MITRE techniques matching to help make recommendations to make the transition to Securonix smoother and easier.
Want to learn more about Threat Coverage Analyzer and Unified Defense SIEM? Schedule a demo today.







