- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, Ella Dragun
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs in May. The report additionally provides a synopsis of the threats; indicators of compromise (IoCs); tactics, techniques, and procedures (TTPs); and related tags. This may be followed by a comprehensive threat summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below mentioned threats, refer to our Threat Labs home page.
In May 2023, Threat Labs analyzed and monitored major threat categories, including the ongoing Kimsuky campaign, ransomware campaign, the exploitation of critical vulnerability CVE-2023-32243, phishing campaigns using meme-filled code to Drop XWorm payloads and Volt Typhoon activity.
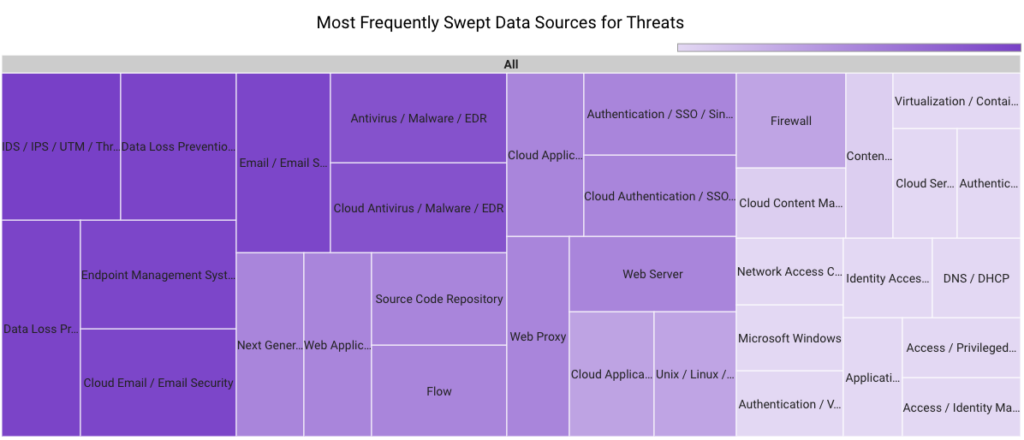
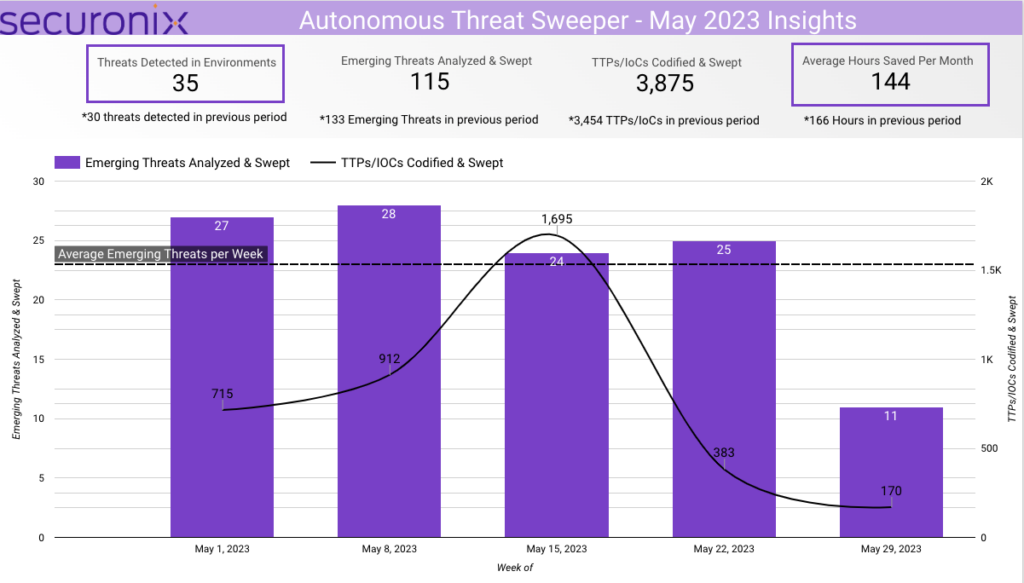
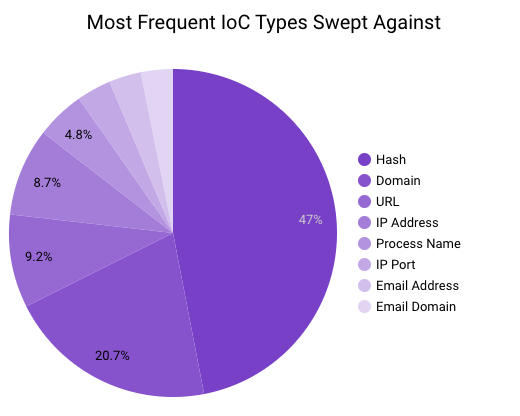
In May 2023, Securonix Autonomous Threat Sweeper identified 3,875 TTPs and IOCs, 115 distinct threats, and reported 35 threat detections. The top data sources swept against include IDS/IPS/UTM/Threat Detection, Endpoint Management Systems, Data Loss Prevention, and Email/Email Security.
 Ongoing Kimsuky campaign (Originally published in May 2023)
Ongoing Kimsuky campaign (Originally published in May 2023)
SentinelLabs has observed ongoing attacks from Kimsuky, a North Korean state-sponsored APT that has a long history of targeting organizations across Asia, North America, and Europe. One of ongoing campaigns uses a new malware component called ReconShark, which is actively delivered to specifically targeted individuals through spear-phishing emails, OneDrive links leading to document downloads, and the execution of malicious macros. ReconShark operates as a reconnaissance tool with unique execution instructions and server communication methods and is a new BabyShark reconnaissance variant. ReconShark exfiltrates information about the infected platform, such as running processes, battery connected to the system, and deploys endpoint threat detection mechanisms.
SentinelLabs also tracked the Kimsuky campaign targeting information services, as well as organizations supporting human rights activists and defectors related to North Korea. The campaign focuses on file reconnaissance, and exfiltrating system and hardware information, laying the groundwork for subsequent precision attacks using a variant of the RandomQuery malware.
RandomQuery uses Microsoft Compiled HTML Help (CHM) files for their long-running tactic to deliver diverse sets of malware with RandomQuery being a main element in Kimsuky’s history. This campaign specifically uses a VBScript-only implementation. The malware’s ability to exfiltrate valuable information, such as hardware, operating system, and file details, indicates its pivotal role in Kimsuky’s reconnaissance operations for enabling tailored attacks.
This campaign also indicates the group’s approach of delivering malware through CHM files, such as keylogging and clipboard content theft malware.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these attacks.
- Ensure your organization’s networks are scanned for any potential malware with the latest signatures using AV and EDR solutions.
- Implement network segmentation and maintain offline backups of data to ensure limited interruption to your organization.
- Organizations and individuals need to be aware of the TTPs used by North Korea state-sponsored APTs and take necessary precautions to protect themselves against such attacks.
- 109 IOCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Threat Actor: a North Korean state-sponsored APT Kimsuky | Threat Actor Location: North Korea | Attack: focuses on file reconnaissance and exfiltrating system and hardware information | Malware: ReconShark
Prominent ransomware attacks (Originally published May 2023)
Researchers have identified the BlackSuit ransomware gang as a threat to Windows and Linux users. The BlackSuit ransomware for Linux is similar to the Royal ransomware but retains its unique onion site communication technique and does not reveal any information about the victims. It is a 32-bit executable program developed in C/C++ that uses the GetCommandLineW function to fetch command-line arguments as it runs.
The list of victims for the new Akira ransomware operation has been progressively growing as it infiltrates corporate networks globally, encrypts files, and then demands a million-dollar ransom. Using a double-extortion method, the Akira ransomware steals and encrypts victims’ data to increase the likelihood that they will pay. If the ransom for decrypting the data is not paid, the attackers then threaten to sell or expose the stolen material on the dark web.
Akira asserts that they have already attacked 16 businesses in a variety of sectors, including manufacturing, education, banking, real estate, and consulting. Although confusing, this ransomware is not related to Akira, another ransomware that was launched in 2017.
The .akira extension is added to the file name along with the encryption when files are encrypted by ransomware. However, the Recycle Bin, System Volume Information, Boot, ProgramData, and Windows folders are not encrypted by the ransomware. Additionally, it will not encrypt files with the file extensions.exe,.lnk,.dll,.msi, and.sys that are part of the Windows system.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from these ransomware attacks.
- Maintain consistent backup procedures and store those backups offline or on a different network.
- Wherever practical and possible, enable automatic software updates on your computer, smartphone, and other linked devices.
- On your linked devices, such as your PC, laptop, and mobile, use a reputable anti-virus and Internet security software package.
- Avoid clicking on suspicious links and opening email attachments without first checking their legitimacy.
- 11 IOCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers
TTPs related to the Akira ransomware include but are not limited to the following:
- Monitor rare and suspicious usage of powershell commands to execute a WMI query that deletes the shadow copy.
- “powershell.exe -Command \”Get-wmiobject Win32_Shadowcopy | Remove-wmiobject\””
Tags: Target Sectors: manufacturing, education, banking, real estate, consulting services | Attack Type: ransomware | Target System: Windows, Linux | Ransomware: BlackSuit, Akira
A Volt Typhoon Chinese state–sponsored threat actor activity (Originally published May 2023)
Microsoft has discovered secret and malicious activity that targets credential access and network system discovery attacking critical infrastructure organizations in the United States. The attack is carried out by Volt Typhoon, a state-sponsored actor based in China that focuses on espionage and information stealing. Microsoft reports that this Volt Typhoon campaign is pursuing the development of capabilities that could disrupt critical communications infrastructure between the United States and Asia region during future crises.
The United States and various authorities including CISA, FBI issued their joint Cybersecurity Advisory (CSA) to share their summary about recently discovered activity of People’s Republic of China (PRC) state-sponsored cyber actor Volt Typhoon. Private sector partners have identified that this activity affects networks across U.S. critical infrastructure sectors, and the authoring agencies believe the actor could apply the same techniques against these and other sectors worldwide.
Their TTPs allow the actor to bypass detection by getting into normal Windows system and network activities, avoid endpoint detection and response (EDR) products that would alert on the introduction of third-party applications to the host, and limit the amount of activity that is captured in default logging configurations.
Threat Labs summary
Securonix Threat Labs is actively monitoring running campaigns by Volt Typhoon
- Securonix Threat Labs recommends the following guidelines
- Implement network segmentation and maintain offline backups of data to ensure limited interruption to your organization.
- Apply the vendor patches immediately.
- Add users to the Protected Users Security Group.
- 28 IOCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the Volt Typhoon Chinese state sponsor threat actor include but are not limited to the following:
- Monitor for the rare and suspicious commands attempting to dump NTDS from Domain Controllers.
- Example: powershell ntdsutil.exe ‘ac i ntds’ ‘ifm’ ‘create full c:\users\public’ q q
- Monitor for the combination of new accounts created, addition of these accounts to the local Administrators group and later removal of the previously created local administrator account
- Example: C:\Windows\system32\net user z Lh199211* /add
C:\Windows\system32\net localgroup administrators z /add
net user z /delete
- Monitor for the abnormal spike in SMB (TCP/445) traffic from Domain Controllers.
- Monitor for the rare and suspicious commands to dump hashes from SAM via registry.
- Example: reg save hklm\system system
reg save hklm\sam sam
reg save HKLM\security sec
- Monitor for modification of firewall configurations to enable RDP access to systems.
- Example: netsh advfirewall firewall set rule group=remote desktop new enable=Yes
- Monitor for the execution of utilities and commands to clear event logs.
- Example: wevtutil.exe el
wevtutil.exe cl [LOGNAME]
- Monitor the spike in installation of remote access tools, such as TeamViewer and LogMeIn.
- Detect attackers carrying out Windows logon bypass techniques where they leverage sethc.exe and narrator.exe to get a command prompt without logging in to the system.
- Example: HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\narrator.exe /v Debugger /t REG_SZ /d C:\windows\system32\cmd.exe /f
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe /v Debugger /t
REG_SZ /d C:\windows\system32\cmd.exe /f
Tags: Campaign: Chinese (PRC) state-sponsored cyber actor: Volt Typhoon | Target location: the United States and Asia region
The exploitation of critical vulnerability CVE-2023-32243 (Originally published May 2023)
Essential add-ons for Elementor, a well-known WordPress plugin, has a security flaw that has been assigned the tracking number CVE-2023-32243 (CVSS rating: 9.8, Critical), which could let hackers take control of the websites that are vulnerable. Versions 5.4.0 to 5.7.1 are impacted.
With more than 90 imaginative parts and extensions, the plugin, which has over a million active installs, enables administrators to enhance their Elementor page-building experience.
The password reset function does not validate a password reset key, which leads to the CVE-2023-32243 issue. Instead, it immediately modifies the user’s password. This indicates that, without requiring authentication, any user on the vulnerable WordPress site can elevate their privileges to those of any other user.
The vendor has updated the plugin to version 5.7.2, which was released on May 11, 2023, to address the CVE-2023-32243 vulnerability. Users of Essential Addons for Elementor are urged to update as soon as possible to the most recent version of the plugin in order to shield their WordPress websites from the security flaw.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from this vulnerability.
- Website owners who use the Essential Addons for Elementor plugin are urged to install version 5.7.2 or later right away in order to deploy the latest security patch.
- We strongly advise all plugin users to upgrade as soon as possible to protect their websites from this vulnerability.
- To thwart this and other attacks, website administrators should use the indicators of compromise and add the offending IP addresses to a blocklist.
- 8 IOCs are available on our Threat Labs home page repository and have been swept against Autonomous Threat Sweeper customers.
Tags: Vulnerability: CVE-2023-32243
Ongoing MEME#4CHAN phishing campaign (Originally published May 2023)
Securonix threat experts have identified an ongoing phishing campaign that employs a distinctive attack chain to infect target PCs with the XWorm malware.
The attacks start with phishing attempts to spread fake Microsoft Word documents that weaponize the Follina vulnerability (CVE-2022-30190, CVSS score: 7.8) to drop an obfuscated PowerShell script instead of using macros.
From there, the threat actors use the PowerShell script to get through Microsoft Defender, disable Antimalware Scan Interface, establish persistence, and finally launch the.NET binary that contains XWorm.
According to a cursory investigation, it appears that the perpetrator or perpetrators of the attack may be of Middle Eastern or Indian descent, however the precise attribution has not yet been established.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased threats from this campaign.
- Although Microsoft decided to disable macros by default, phishing emails still occasionally include Microsoft Office documents. Today, however, we are seeing evidence that it is still vital to be cautious about malicious document files, particularly in this instance when there was no VBscript execution from macros.
- 50 IOCs are available on our Threat Labs home page and have been swept against Autonomous Threat Sweeper customers.
Tags: Attack Type: Phishing | Target Location: Germany | Target Sector: Manufacturing, Healthcare
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at scia@securonix.com.
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Sina Chehreghani, Tim Johny, Dhanaraj K R