- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
- MSSPs
- Scale multi-tenant security with predictable economics.
-
- Resources
- Partners
- Company
- Blog
Threat Intelligence
From Fragmented Tools to Unified Action
By Beth Dannemiller, Director of Product Marketing
Security leaders know the frustration of having powerful threat intelligence that never quite translates into faster, better defense. Disconnected tools, inconsistent formats, and manual workflows slow everything down leading to delayed responses, alert fatigue, and overextended teams.
The integration of ThreatQ and Securonix Unified Defense SIEM changes that. Instead of siloed systems, you get a unified approach where intelligence flows seamlessly into detection and response and insights flow back into your intel strategy.
The result? A SOC that works smarter, responds faster, and delivers measurable risk reduction.
What Customers Gain Today
This isn’t just an integration—it’s a bi-directional, API-driven connection built to deliver immediate results in your SOC:
- Sharper Detection – ThreatQ curates and enriches threat data from OSINT, commercial feeds, and internal research, then scores, tags, and deduplicates IOCs. Securonix receives only high-fidelity, context-rich intelligence, reducing noise and elevating the alerts that matter most.
- Continuous Improvement – Detection data from Securonix flows back into ThreatQ, creating real-time feedback loops that fine-tune scoring models and make future intel more accurate.
- Operational Efficiency – Intelligence and detection continuously inform each other, forming a closed-loop system that evolves with your environment. Analysts spend less time reconciling tools and more time neutralizing threats.
For CISOs and security leaders, this means:
- Faster time-to-detection and reduced exposure windows
- Higher fidelity alerts for more efficient use of analyst resources
- A direct link between threat intelligence investments and improved security outcomes
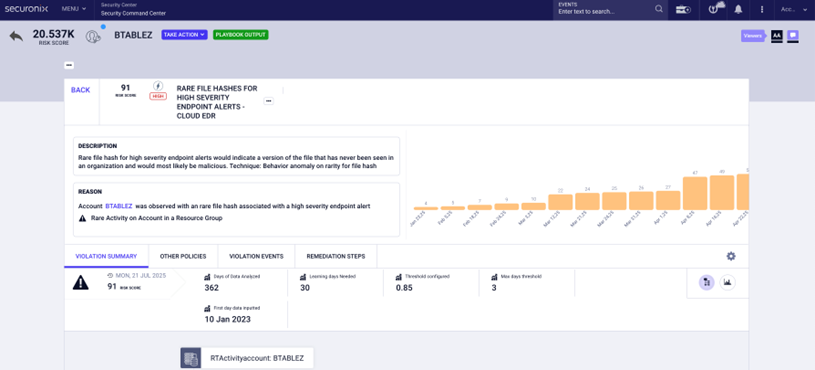
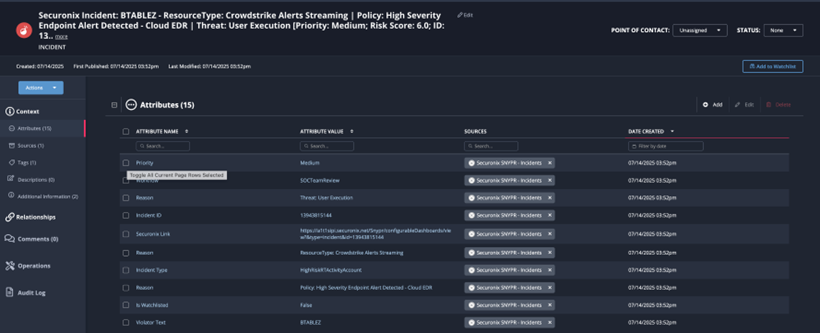
Securonix Violations (Top) ingested as ThreatQ Incidents (bottom) with detailed context
Built for Scale, Not Shortcuts
Unlike brittle connectors or quick fixes, this integration is grounded in a shared product vision and aligned APIs. That means it’s stable, scalable, and designed to grow with your program—delivering lasting value rather than short-term patches.
What It Looks Like in the SOC Now
- Security analysts see enriched, context-aware IOCs in Securonix, already scored for relevance.
- Intel teams can measure the impact of shared intel directly against real-world detections.
- Incident responders move faster because insights flow automatically back into the TIP
Most importantly, your SOC gains a common operational picture, reducing friction across teams and ensuring coordinated response at every stage.
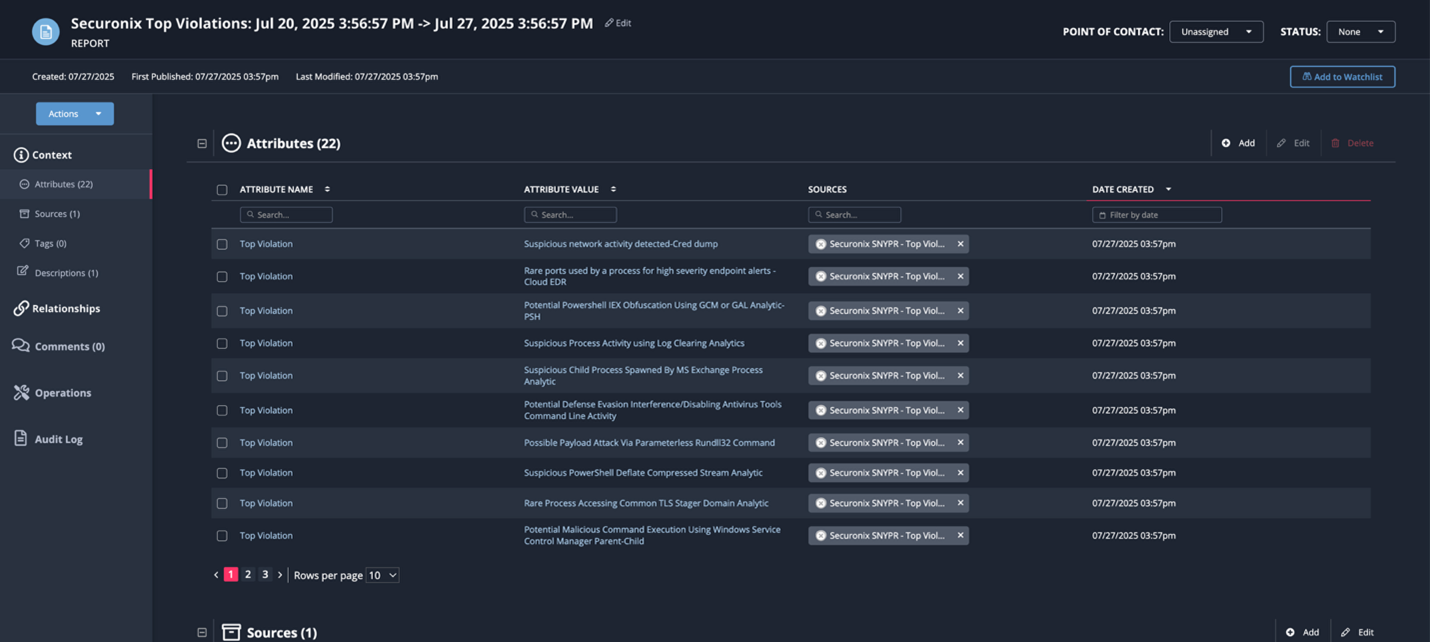
Securonix Top Violations, Violators, and Threats ingested into ThreatQ
Looking Ahead: The Future of SIEM + TIP
With Securonix and ThreatQ now under one roof, the roadmap goes well beyond integration. Customers will gain powerful new capabilities designed to drive faster, smarter outcomes across the SOC:
- Unified Threat Graphs – A complete view that connects global threat data with internal incidents, giving analysts the full context they need to act decisively.
- Adaptive Correlation – Detection logic that adjusts in real time, reducing noise while surfacing the most relevant alerts.
- Role-Aware AI – Tailored assistance for CISOs, hunters, and analysts, ensuring every persona gets the insights and automation they need.
- Persona-Specific Threat Briefings – Dynamic reporting delivered inside the SIEM, aligned to the priorities of each stakeholder.
- Collaborative Threat Modeling – The combined power of behavioral analytics and curated intel to anticipate and disrupt threats before they strike.
These aren’t distant promises, they’re in active development, with the goal of giving your team more context, more automation and more confidence.
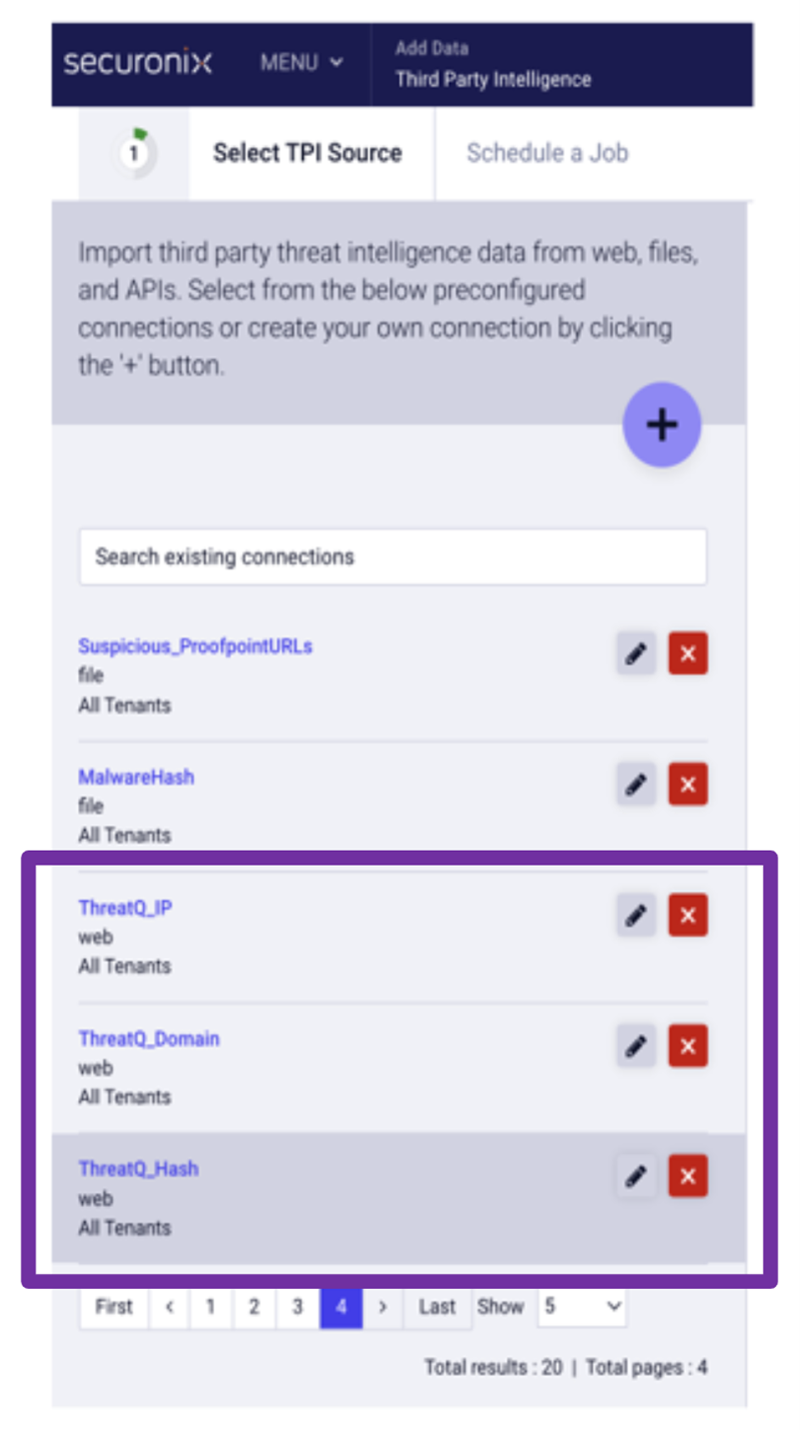
High-fidelity ThreatQ Intelligence configured as intelligence feeds into Securonix
Why This Matters for You
Whether you start with ThreatQ or Securonix, the benefits are immediate:
- ThreatQ users get faster operationalization of intelligence, no new integrations required.
- Securonix users gain access to enriched, scored, and prioritized intel out of the box.
- Your security team benefits from streamlined workflows, faster detection, and clearer context.
- Your organization gets measurable efficiency, clarity, and resilience today—with a platform that keeps learning and adapting over time.
Get Started Today
The integration is live. That means your team can start realizing the benefits of unified threat operations today—faster detection, better outcomes, and a more resilient SOC.
Contact your Customer Success Manager to activate the full ThreatQ-Securonix integration suite and see what coordinated defense looks like in action.
To Learn more visit our Threat Intelligence Platform overview.







