- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Insider Threat
By Abhishek RVRK Sharma, Senior Technical Marketing Engineer
When the trusted becomes malicious
Insider threats. You’ve surely heard the term, and how it is the most dangerous and damaging cyberthreat an enterprise can face. The US Department of Homeland Security defines an insider threat as “a current or former employee, contractor, or other business partner who has or had authorized access to an organization’s network, system, or data and intentionally misused that access to negatively affect the confidentiality, integrity, or availability of the organization’s information or information systems.” According to Cybersecurity Insiders’ 2019 Insider Threat Report, 60% of surveyed enterprises faced at least one insider threat over the past year.
But then again, insider threats aren’t new. Here’s a picture of a historically famous ‘insider threat.’

The Trojan Horse, taken into the city by the Trojans themselves, led to the sack of Troy. By bringing the horse inside city walls, the Trojans gave the people hidden inside the horse access to a well-protected, secure resource – and paid a heavy price.
Other examples abound, such as Ephialtes at the Battle of Thermopylae, who revealed the location of the secret path that led to King Leonidas’s defeat and death. No Persians knew of the path – but Ephialtes was swayed by the promise of reward from the Persian King, and thus revealed inside information that only a local Greek could provide.
These days, data is the biggest asset under threat. Insider threats and commercial espionage have been around for decades. However, when information was contained within paper documents and on-premises servers, it was more difficult for an insider to make off with sensitive information. Most information was on storage media which could be confiscated, email attachments were too small to accommodate a lot of information, and flash drives were not yet in vogue.
Then came cloud and portable storage technology. As it became easier for insiders to exfiltrate information, it has become a lot more difficult to track insider threats. Insiders are trusted.
Insiders can both be witting and unwitting. The unwitting or careless insider is an individual with legitimate accesses but who through poor judgment commits a security infraction that results in potential consequences for his organization (such as inserting an infected USB key into their laptop).
The witting or malicious insider is an individual that makes the conscious decision to abuse his access in order to obtain sensitive and/or financial information for personal gain or purposeful malicious intent (such as Chelsea Manning or Edward Snowden).
A third type of insider is the remote actor who has compromised legitimate credentials in order to gain privileged access to an organization’s network.
One thing that all three have in common is that, once inside, perimeter security can do little to deter their actions – much like the Trojans were powerless to stop the soldiers inside the horse, once they were inside city walls.
How an insider threat develops
Here’s how a typical insider threat develops – and how seemingly innocuous, low risk actions can turn into a multimillion-dollar cost to your company.
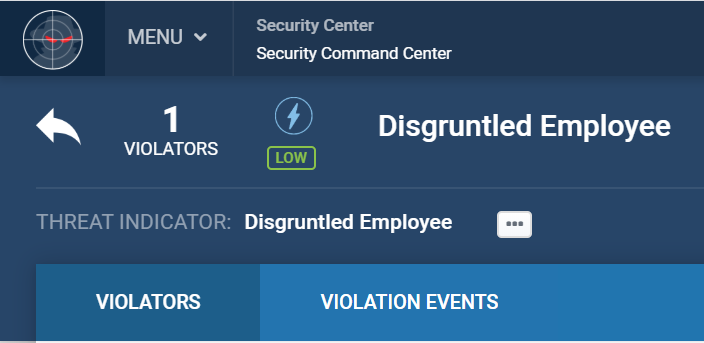
Friday, 3:00 PM, Dallas, Texas
Kevin’s Performance Appraisal
Performance Rating: Poor
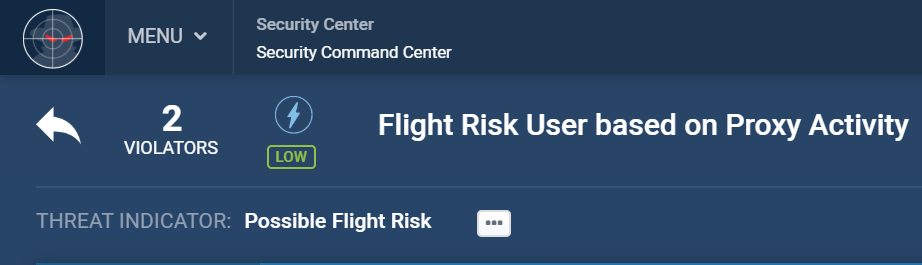
Friday, 4:00 PM
Google Search: Resignation Letter
Kevin’s had it – he’s looking to resign from his role.
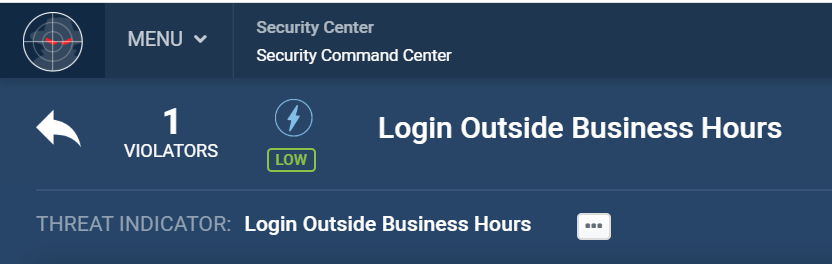
Saturday, 1:05 AM
After Hours Badge In
Kevin decides to use his access, and credentials he has taken and stored to gain access to confidential company data. He comes into the office when there is no one at work.
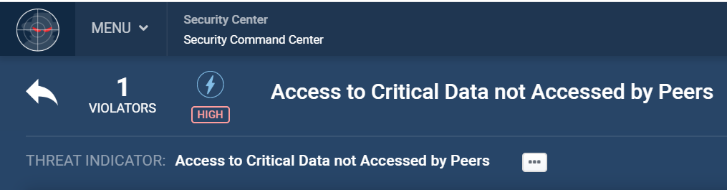
Saturday, 2:00 AM
Critical Data Access
Kevin accesses critical, sensitive company data.
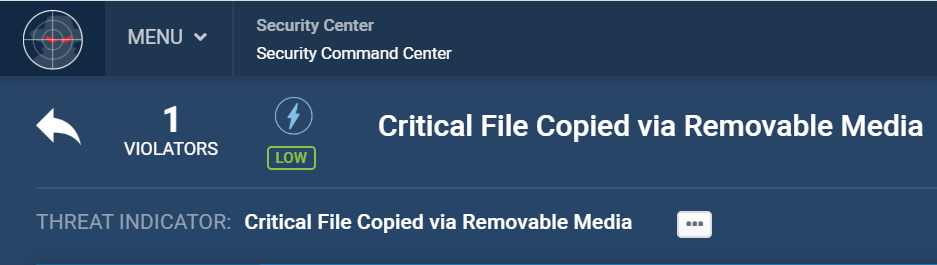
Saturday, 2:00 AM
Unauthorized file copy
Kevin uses a privileged account password to access and copy internal documents and copy/print them.
And that is that – business critical company information, taken and given to a competitor by a disgruntled former employee. This could potentially cause millions in losses if the competitor makes changes to their product to counter your product plans and undercuts pricing to make your new launch a failure.
Let’s face it, insider threats are a reality. Even with zero-trust security capabilities, insiders will always have the means to access sensitive data – because without trust, productivity is impossible. And often, it is not the fault of the employee. Unwitting insider threats, such as individuals with weak passwords, are still threats that need to be managed. You need a security platform in place that detects insider threat behavior and responds and prioritizes threats in order to nip insider threats in the bud.
Behavior analytics are key to identifying and nullifying insider threats.
These threats come along in many forms:
- Copy data to a USB drive
- Send an email to somebody outside of the company
- Download a large amount of data
- Request access to a new file
- Request an account privilege escalation
Notice something here? None of these actions by themselves can be classified as a malicious event. There are times during an employee’s day-to-day operations where they will need to do these things as part of their job. The threat can only be found when these events happen together with other indicators – such as bad performance reviews, flight risk behavior, or a termination mandate. Tying these together, with context and entity linkage, is what is needed to detect insider threats. Management of insider threats requires a comprehensive program, backed by a strong platform.
About the Securonix Platform
Securonix, out of the box, provides packaged content that includes use cases specific to insider threat detection and response, among other industry and use case specific content.
With Securonix, insider threats are correlated and prioritized with an industry-leading UEBA.
Learn more about how Securonix addresses the risk of Insider Threats.







