Cloud Security Monitoring Software
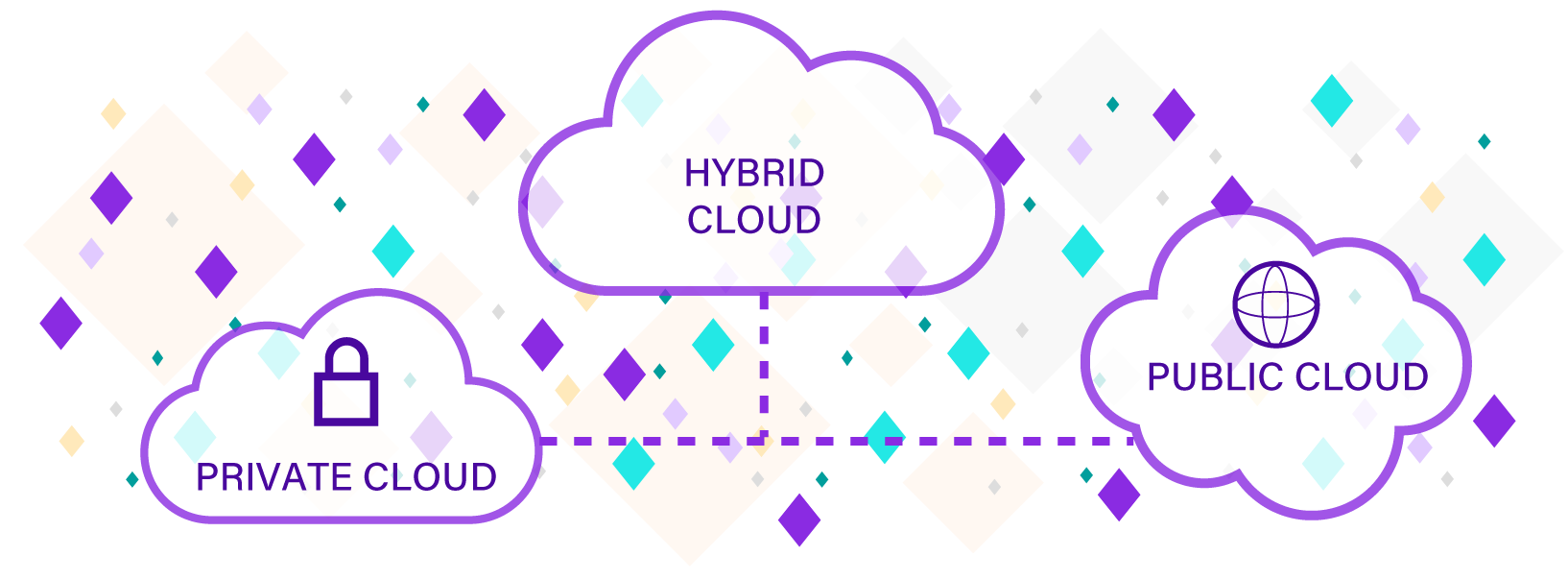
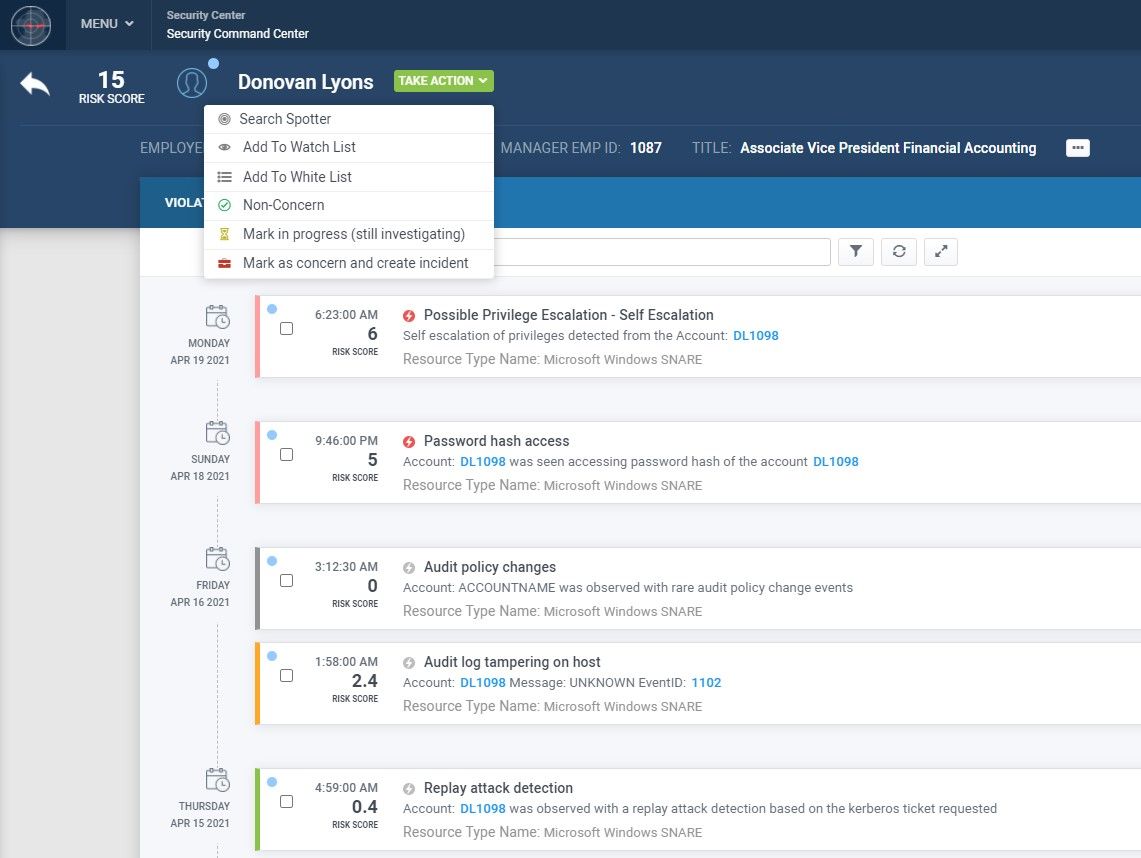
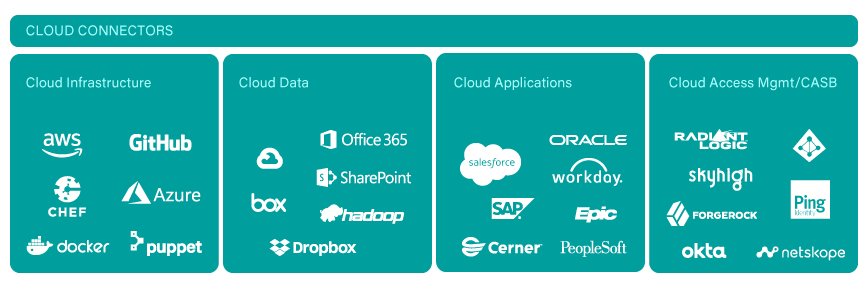
Unlock unparalleled flexibility and scalability for superior cloud data security with our advanced monitoring software. Protect your cloud environment from unauthorized access and threats with real-time detection, comprehensive visibility, and seamless integration with all major cloud service providers.