Autonomous Threat Sweeper
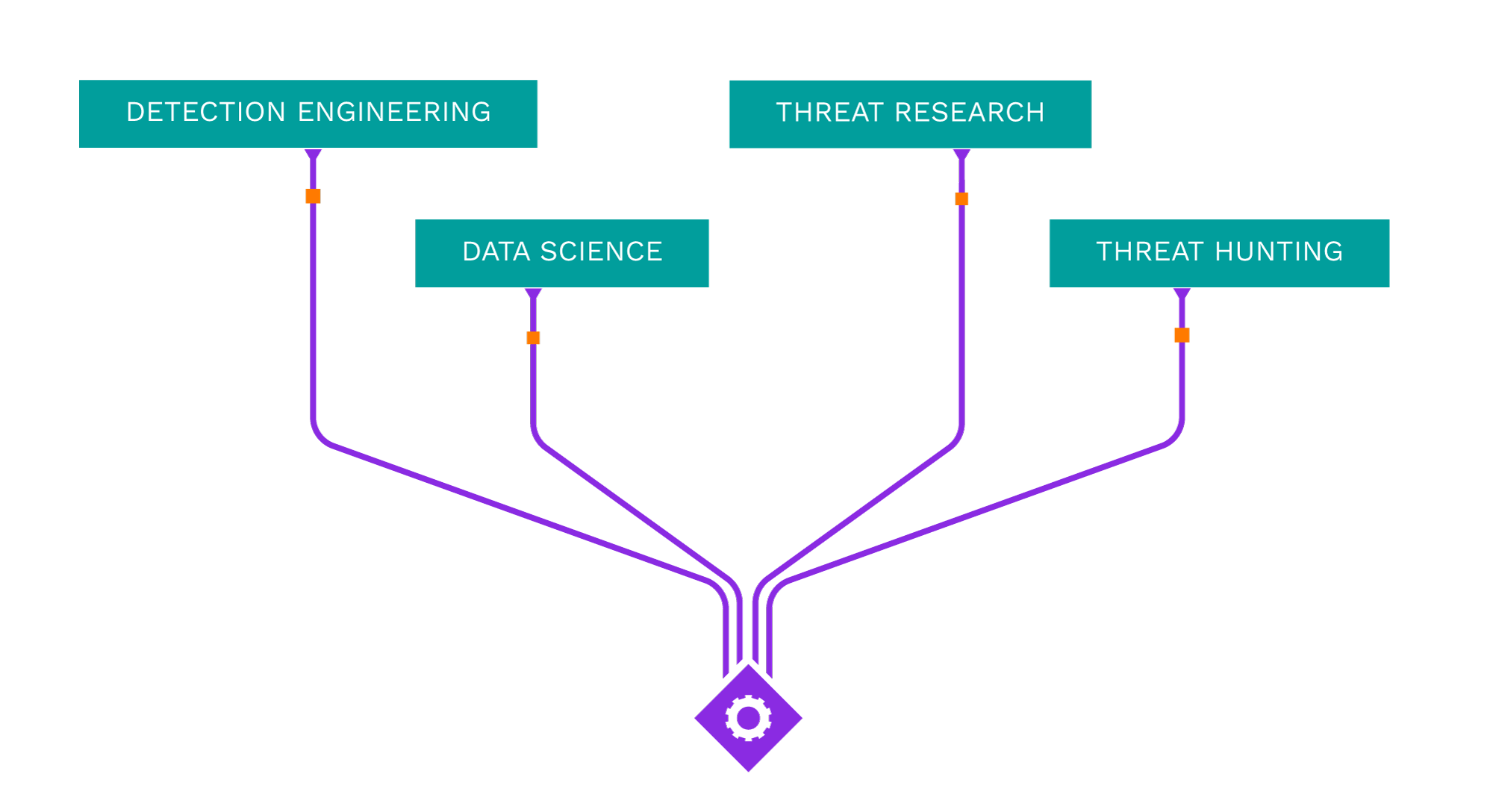
Acting as your own dedicated Cyber Rapid Response Team, Securonix Autonomous Threat Sweeper (ATS) automatically and retroactively hunts for new and emerging threats based on the latest threat intelligence from our Threat Labs Team.
Latest ATS Entries
All indicators of compromise (IOC) and Spotter queries are available on our GitHub repository.
—
- Intel Source:
- WPScan
- Intel Name:
- A_Malware_Campaign_Targeting_WP_Automatic_Plugin
- Date of Scan:
- 2024-04-26
- Impact:
- LOW
- Summary:
- Researchers from WPScan have discovered a dangerous malware campaign targeting websites that use the WP-Automatic plugin. The campaign exploits a critical vulnerability in versions of the plugin prior to 3.9.2.0, allowing attackers to execute unauthorized database queries via SQL injection (SQLi). This flaw poses a significant risk as attackers can gain admin-level access, upload malicious files, and potentially take control of affected websites.
Source:
https://wpscan.com/blog/new-malware-campaign-targets-wp-automatic-plugin/
—
- Intel Source:
- Sekoia
- Intel Name:
- Sinkholing_the_PlugX_USB_Worm_Botnet_by_Unplugging_PlugX
- Date of Scan:
- 2024-04-26
- Impact:
- MEDIUM
- Summary:
- Researchers have sinkholed a command and control server for a variant of the PlugX malware and observed in six months more than 2.5 million connections from unique IP addresses. Since last September, the sinkhole server received over 90,000 requests every day from infected hosts in more than 170 countries.
—
- Intel Source:
- Canada CA
- Intel Name:
- Cyberattacks_Affecting_Cisco_ASA_VPNs
- Date of Scan:
- 2024-04-26
- Impact:
- MEDIUM
- Summary:
- The Australian Cyber Security Centre of the Signals Directorate, the Canadian Centre for Cyber Security (Cyber Centre), and the National Cyber Security Centre (NCSC) of the United Kingdom have been assessing persistent hostile cyber activity since the beginning of 2024. This activity has been directed towards virtual private network (VPN) services that are utilized by critical national infrastructure networks and government agencies worldwide. The capabilities point to espionage carried out by a highly skilled and resourceful state-sponsored operator.
Source:
https://www.cyber.gc.ca/en/news-events/cyber-activity-impacting-cisco-asa-vpns
—
- Intel Source:
- CYFIRMA Research
- Intel Name:
- The_Path_of_an_Obfuscated_Batch_Script_to_Monero_Mining
- Date of Scan:
- 2024-04-26
- Impact:
- LOW
- Summary:
- Researchers from CYFIRMA have discovered a stealthy miner malware that is present in the wild. To compromise defense systems, this malicious software uses advanced methods like privilege escalation, process injection, and AMSI bypass. The malware notably includes a number of anti-analysis and anti-debugging techniques.
—
- Intel Source:
- Huntress
- Intel Name:
- Unveiling_the_macOS_Variant_of_LightSpy_Malware
- Date of Scan:
- 2024-04-26
- Impact:
- LOW
- Summary:
- Huntress researchers have observed the emergence of LightSpy targeting macOS highlights the evolving landscape of threats against Apple devices. While recent samples uploaded to VirusTotal from India provide some insight, caution is advised in drawing definitive conclusions without additional evidence of active campaigns or specific targeting. Although previous research has linked LightSpy to APT 41, attribution remains complex. Apple’s proactive security measures, such as Lockdown Mode and enhanced XProtect modules, underscore the importance of regular updates across all platforms to mitigate emerging threats effectively.
Source:
https://www.huntress.com/blog/lightspy-malware-variant-targeting-macos
—
- Intel Source:
- Morphisec
- Intel Name:
- New_Variant_of_IDAT_Loader
- Date of Scan:
- 2024-04-26
- Impact:
- LOW
- Summary:
- Researchers at Morphisec have identified a new variant of IDAT loader, which is utilized to distribute various malware payloads depending on the attacker’s analysis of the targeted system. IDAT incorporates distinctive functionalities such as code injection and execution modules, distinguishing it from traditional loaders.
Source:
https://blog.morphisec.com/threat-bulletin-new-variant-idat-variant
—
- Intel Source:
- Sentinelone
- Intel Name:
- The_Ransomware_Evolution
- Date of Scan:
- 2024-04-25
- Impact:
- LOW
- Summary:
- Researchers at SentinelOne have studied the ways in which ransomware affiliates have changed over time, concentrating on how they are increasingly utilizing stolen data to make extra money on top of the initial ransom demands. It looks at current examples that shed information on the growing field of cyber extortion, such as the cooperation between affiliates and organizations like Dispossessor, Rabbit Hole, and RansomHub.
—
- Intel Source:
- Securonix Threat Labs
- Intel Name:
- An_Investigation_of_Ongoing_FROZEN_SHADOW_Attack_Campaign
- Date of Scan:
- 2024-04-25
- Impact:
- MEDIUM
- Summary:
- Securonix researchers discovered an interesting attack campaign that uses SSLoad malware and Cobalt Strike implants, allowing the attackers to pivot and seize control of the entire network domain. Securonix has dubbed the campaign FROZEN#SHADOW. It also includes the use of the ConnectWise ScreenConnect remote desktop software and Cobalt Strike.
—
- Intel Source:
- Cisco Talos
- Intel Name:
- ArcaneDoor_Unmasked
- Date of Scan:
- 2024-04-25
- Impact:
- LOW
- Summary:
- Cisco Talos researchers have discovered a campaign called “ArcaneDoor” aimed at perimeter network devices made by different companies. These devices are important because they control how data goes in and out of networks. The campaign is run by a skilled group, called UAT4356 by Talos, who use special tools like “Line Runner” and “Line Dancer” to do bad things, like changing settings and spying on network traffic.
—
- Intel Source:
- CYFIRMA Research
- Intel Name:
- A_Sophisticated_Anti_Analysis_Info_Stealer_Named_Fletchen_Stealer
- Date of Scan:
- 2024-04-25
- Impact:
- LOW
- Summary:
- CYFIRMA researchers identified an information stealer called Fletchen Stealer, a malware designed with sophisticated anti-analysis tactics and sold as a service by its maker, posing a huge cybersecurity concern. The study investigates the variety of anti-analysis strategies used by threat actors to mask the true nature of the malware through in-depth analysis.

Shared Security Content on Sigma
Securonix Threat Labs publishes up-to-date IOCs and threat hunting queries on Sigma, allowing you to tap into a vast community of collective defense and stay ahead of emerging threat research.
What's New from Threat Labs
-
BlogAnalysis of DEV#POPPER: New Attack Campaign Targeting Software Developers Likely Associated With North Korean Threat ActorsLearn More
-
BlogSecuronix Threat Research Security Advisory: Analysis of Ongoing FROZEN#SHADOW Attack Campaign Leveraging SSLoad Malware and RMM Software for Domain TakeoverLearn More
-
BlogSecuronix Threat Research Knowledge Sharing Series: Detecting DLL Sideloading Techniques Found In Recent Real-world Malware Attack ChainsLearn More