- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
SIEM
By Oliver Rochford, Security Evangelist, Securonix
Whenever a new vulnerability is disclosed, a race begins between defenders and attackers to execute their own action chain to either exploit or mitigate the vulnerability. For an attacker, the three phases are:
- Identify a vulnerability
- Weaponize tactics
- Exploit the vulnerability
The defender follows three steps to remediate:
- Prioritize the threat
- Assess exposure to the organization
- Mitigate the threat

From Exploit to Breach
In most cases, attackers have a head-start, typically of several days, but in many cases there may be a gap of even weeks to months [1]. The gap between when attackers are able to weaponize and exploit a vulnerability and when defenders can assess if they are exposed and deploy mitigating controls (mean time to respond or patch) is a window of vulnerability for organizations and one of opportunity for attackers. Adversaries can often act with impunity if no additional mitigating controls are deployed.
Ultimately, the goal of attackers is to obtain and maintain a first-mover advantage. Defenders aim to close and eliminate the resulting exposure gap.
Attackers and defenders go through cycles of adapting and counter-adapting.
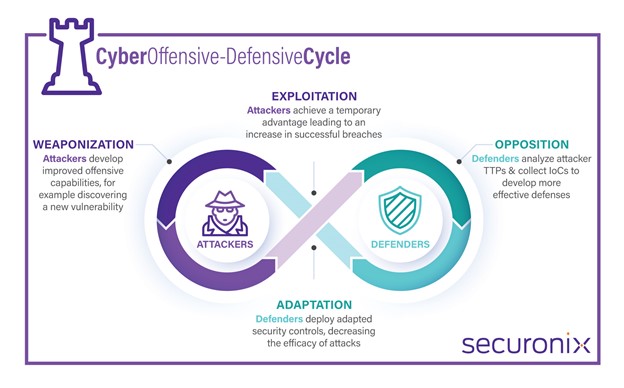
Detecting the Log4j Vulnerability
Log4j was not a single incident or event. Instead, it was an ongoing crisis with many peaks and troughs, and multiple laps around the attacker-defender adaptive cycle.
The original vulnerability resulted in multiple restarts of the attacker-defender race, as Apache released several different updates leaving security teams to go back and repeat most of the work they had just done.
In parallel, reports of exploitation by attackers in the wild increased, adding further pressure on security teams.
Short Build-up to Mass Exploitation
There were only four days between the disclosure and widespread dissemination of the vulnerability and reports of mass exploitation.

December 9 Apache releases the advisory and patch and urges users to act quickly and apply the fix. Securonix Autonomous Threat Sweeper (ATS) publishes proof of concept exploit to GitHub and Twitter.
December 10 CVE-2021-44228 is published on the National Vulnerability Database [2], kicking off a media storm.
December 11 CISA issues an advisory and warning [3].
December 12 Reports begin circulating widely that mass exploitation in the wild is being seen by many researchers and vendors.
December 14 Mandiant confirms that suspected Chinese and Iranian nation-state actors are actively exploiting the vulnerability.
December 15 Apache releases a patch, Log4j 2.16.0 for CVE-2021-45046, kicking off a new adaptive cycle for defenders.
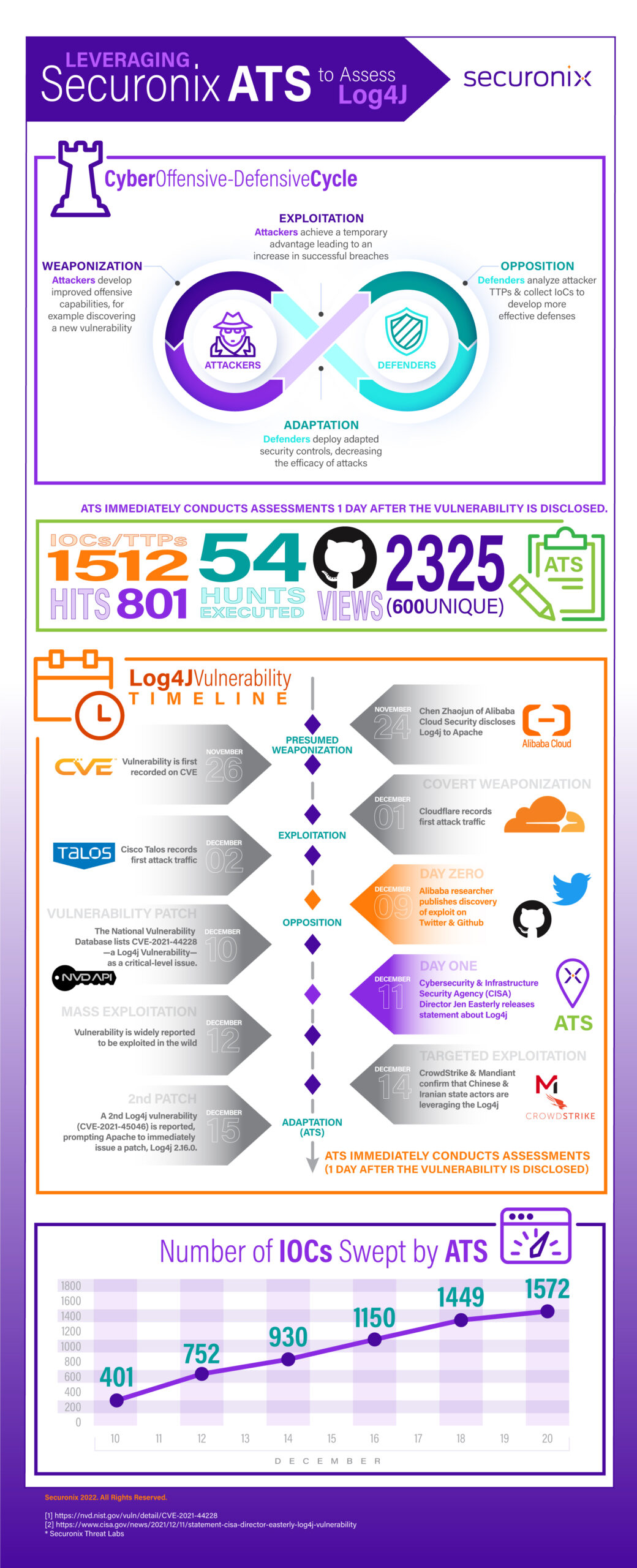
ATS in action* and how the solution was able to detect the Log4j vulnerability in one day.
Read More
As threats evolve and increase while dwell time decreases, organizations are under pressure to detect security gaps almost immediately. Securonix Autonomous Threat Sweeper can retroactively analyze past activity, making it a critical tool for security teams to improve their mean time to respond and ultimately minimize risk to their organizations.
Sources
[1] Tenable Research: QUANTIFYING THE ATTACKER’S FIRST-MOVER ADVANTAGE
[2] https://nvd.nist.gov/vuln/detail/CVE-2021-44228
[3] https://www.cisa.gov/news/2021/12/11/statement-cisa-director-easterly-log4j-vulnerability
* Securonix Threat Labs







