- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
Best Practices for Securonix Next-Gen SIEM Users
Securonix Threat Labs R&D
Contributors
Den Iuzvyk
Kayzad Vanskuiwalla
Oliver Rochford
Oleg Kolesnikov
| Who needs to know | CISO’s, Security Managers, and Security Analysts |
| Why you need to know | The risk of ransomware attacks has escalated acutely after a series of recent high-profile breaches and has been designated a critical threat by many governments. |
| What you need to know | Securonix helps protect against ransomware through preemptive detection in the 5+ days median dwell time before an attack is fully realized. |
| What you can do | Ensure that you are collecting the relevant and requisite data sources to be able to effectively detect ransomware in the early stages and enable all related detection content. |
Introduction
In light of the escalating threat from ransomware activity, we wanted to provide some guidance on how Securonix users can protect themselves.
SIEM technology is primarily intended for detection and is not intended to stop ransomware outbreaks in the final stages of an attack, for example once data encryption has been initiated.
Instead, SIEM can often be used to detect, respond to, and disrupt earlier phases of a compromise leading to a ransomware attack, for example initial exploitation, lateral transfer, or privilege escalation.
Ransomware is designed to be quick – the act of encryption is measured in seconds to minutes – but that represents only the final phase of the compromise. From initial compromise through to identifying the most valuable targets and then gaining access can take several days, if not weeks. One recent research report stated that ransomware operators have a median dwell time of 5 days before executing the final phases of the attack.
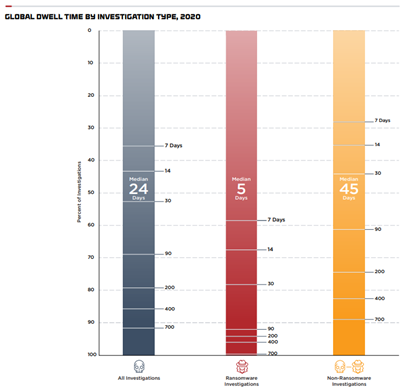
FirEye M-Trends Report 2021: Median Dwell Time by Investigation Type
This median 5-day dwell time presents a crucial window of opportunity to detect an ongoing attack before it completes the full killchain to encrypt and exfiltrate data.
Typical Ransomware Attack Stages
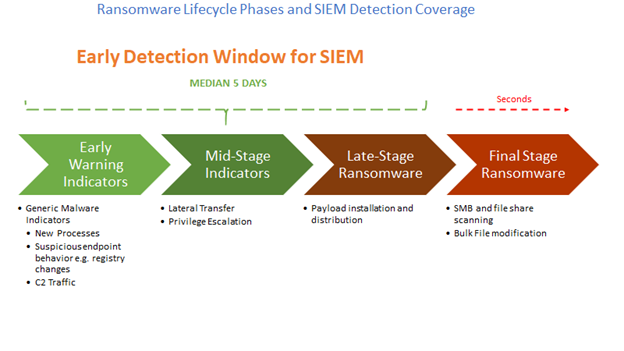
5 Day Early Detection Window for Ransomware Using SIEM
Early Detection and Containment of Ransomware Using Securonix
Securonix Next- Gen SIEM and UEBA both detect a wide variety of indicators of compromise, indicators of action, and behavioral anomalies across the typical long- to mid-term ransomware attack lifecycle. Users are advised to verify and test that all relevant and requisite data sources are collected.
Recommended Data Sources
To ensure sufficient visibility and have an effective chance at preemptively detecting ransomware, we recommend that the following data sources are collected:
- RDP logs
- Storage/Backup system logs
- VPN/jump server logs
- MFA/authentication logs
- Powershell script blog logging
- Raw EDR logs
- NTA logs, including JA3[S] visibility
- MFA/authentication logs
- HTTPS termination logs (if feasible)
Recommended Detections
Some of the relevant detections developed by Securonix Threat Labs R&D to help identify different “early warning” behaviors and TTP’s associated with common ransomware include:
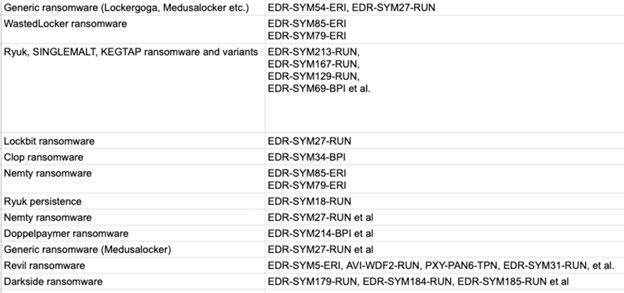
AVI-WDF2-RUN, EDR-SYM9-BPI, EDR-SYM90-ERI, EDR-SYM91-ERI, WEL-SVC1-ERI, EDR-SYM18-RUN, EDR-SYM67-RUN, WEL-SHR6-RUN, EDR-SYM93-RUN, WEL-OTH1-RUN, WEL-PSH12-RUN, EDR-SYM5-ERI, AVI-WDF2-RUN, EDR-SYM11-ERI, EDR-SYM7-ERI, EDR-SYM70-BPI, EDR-SYM21-RUN, EDR-SYM34-BPI, EDR-SYM69-BPI, PXY-PAN6-TPN, EDR-SYM31-RUN, EDR-SYM71-RUN, EDR-SYM167-RUN, EDR-SYM129-RUN, WEL-TAR10-BPI, EDR-SYM79-ERI, EDR-SYM100-RUN, EDR-SYM27-RUN, EDR-SYM85-ERI, EDR-SYM79-ERI, EDR-SYM182-RUN, EDR-SYM211-RUN, EDR-SYM212-RUN, EDR-SYM213-RUN, EDR-SYM214-BPI, and others.
For more detailed examples of mapping of detections to ransomware families, see Appendix I.
Other Recommended Best Practices
In addition to enabling the correct data sources and detection content in the SIEM, the best practices listed have also proven helpful.
- Review your backup version retention policies and make sure that your backups are stored in a location that cannot be accessed/encrypted by operator placed targeted ransomware. (e.g. consider remote write-only backup locations).
- Implementing security monitoring for your automated backup systems to enable early detection of possible malicious disruptions by ransomware operators and affiliates as part of a potential breach.
- Implement security monitoring, particularly for high-value targets (HVT), including users and critical systems in your environments to detect possible malicious ransomware operator placement activities earlier.
- Following the relevant ransomware frameworks and guidelines from CISA, IST, NIT, UK National Cyber Security Centre, Europol, and other relevant entities to help mitigate ransomware risk.
- Improving cyber hygiene and security hardening are crucial in making ransomware operators’ lives difficult, and more importantly, increasing their dwell time to improve our chances of detecting them prior to detonation. Every incremental maturity increase pays dividends in breathing room and peace of mind.
- Review user and access roles and permissions and rationalize your policies towards least privilege.
- Review if you can create tighter network segments.
- Disable commonly targeted and exploited features and services like autorun, remote desktop, and macros.
- Review your open vulnerabilities and prioritize the ones being targeted by ransomware.
- Many ransomware attacks begin with a phishing email or drive-by-exploitation, so raising awareness to increase organizational vigilance can reduce your susceptibility to these types of social engineering attacks.
- We hope for the best but prepare for the worst – so ensure you have functional data backups and a disaster recovery plan to improve your resilience against attack.
NIST has also released a preliminary draft of a risk management framework for ransomware.
Additional Security Measures to Reduce the Risk From Ransomware
We also provide additional security measures that can be highly effective on defending against ransomware.
Autonomous Threat Sweep
This is free for our customers. ATS Cyber Rapid Response is a microservice that autonomously gathers threat intelligence for emerging threats, automatically extracts IoC’s and IoA’s and then retrospectively hunts in your collected security data to see if you have been compromised. Early warning and detection can aid in detecting ransomware while it is still dormant, and by using historical data requires no new attack data to be generated or collected.
Securonix SOAR
Ransomware acts at machine speed, so manual processes cannot keep up. Instead, automated rapid response and containment are required to fight machine with machine. Securonix SOAR can speed up and automate incident investigation and qualification, and even automate containment actions such as disabling user accounts or network access.
Appendix I