- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
SIEM
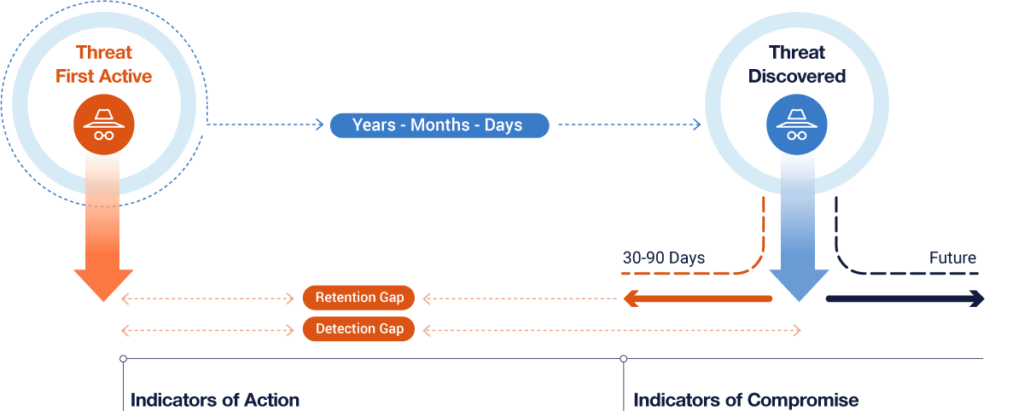
Threat actor campaigns, like Sunburst, that have remained active but undiscovered for years are beginning to come to light. Their ability to slowly wreak havoc while hiding behind legitimate software and users makes such threats particularly difficult to detect. This type of campaign requires specific strategies to mitigate and typically possesses the following characteristics:
- Signatures that can take several days to detect after an advisory release.
- Attacks that unfold over long periods of time and may have started months or even years in the past.
- Often requires sophisticated detection methods like adversary behavioral analysis and access to long-term historical data.
- Are known to garner a lot of negative media attention and gain executive level visibility.
- Can affect entire industries, regions, or even have a global impact if not addressed quickly.
The Need for Cyber Rapid Response
The consequences of leaving low and slow threats unchecked can be both financially devastating and harmful to your organization’s reputation. To mitigate the risk of these types of attacks there are several requirements you should consider from an operational perspective:
- A 24×7 function or capability that continuously monitors the news, advisories, and threat intelligence landscape for anything urgent.
- The ability to quickly develop assessment methodologies for detection.
- Access to large volumes of live and historical data and the ability to search over long periods of time.
- The ability to alert and report on any findings.
Traditionally this would be done by a team of multiple stakeholders that together compose what is often called a Cyber Rapid Response Team. These include the Computer Security Incident Response Team (CSIRT) or Threat Intelligence team, detection engineering, data engineering, and security analysts.
In security organizations with less resources this may be covered by a small group of people, or even a single person juggling many roles and hats. This approach, although feasible, suffers from a lot of friction and high management overhead while yielding little in terms of actual return unless economies of scale are achieved.
On the other hand, organizations that are more service-oriented frequently rely on a managed security service or a managed detection and response provider, usually in the form of managed threat hunting or a rapid response service. For the provider, the same issues of friction and economies of scale apply. For the end user, these types of services can come at a considerable cost unless the provider has a high maturity and is using intelligent automation to reduce the cost and improve responsiveness.
Cyber Rapid Response in a Hybrid World – The Securonix Way
When we started looking at this problem, it very quickly became clear that the solution could not entail throwing even more people at the problem. While an incident can occur at any given time, they rarely do. Putting a dedicated full-time resource in place makes little sense and yields even less return on investment (ROI). It is also not a good use of rare skills and expertise.
In searching for an answer we also quickly realized that while most detection technologies sooner or later release a suitable signature, they often only work on traffic generated during the early phases of a new intrusion. The indicators of compromise (IOCs) and observables in these types of attacks are often historical in nature, and an attacker has had a long time to build out their foothold and hide their traces.
We needed a solution that could act across all manner of different alerts and data types, and do so by going back into the past and searching through long historical time scales. That’s where Securonix Autonomous Threat Sweep (ATS) comes into play.
Acting as your own dedicated cyber rapid response team, ATS is an autonomous threat hunting engine designed to hunt IOCs across customer engagements. Created by expert threat hunters, it is designed to analyze information about emerging threats and proactively hunt through historical data for any signs of compromise.
The solution acts as a force multiplier for security teams, versus adding even more to the analysts workload, and automates menial and repetitive tasks inherent in analyzing threat intelligence to develop detection queries.
It was important to us that ATS did not just search for some IOCs – as you can accomplish that with a simple script. We wanted ATS to automate as much of what a threat hunter does as possible, so we developed a lot of logic and intelligence to analyze and identify indicators of action (IOA) and other anomalous behaviors based on an attacker’s tactics, techniques, and procedures (TTP). If you are already threat hunting, ATS will augment your analysts, allowing them to focus on what only a human can do. If you are a lower maturity organization, ATS gives you baseline coverage to reduce your risk.
Best of all, Autonomous Threat Sweep is an opt-in feature at no additional cost to our customers. Contact us to learn more about our threat sweep capabilities or schedule a demo.
Download the Securonix Autonomous Threat Sweep data sheet.