- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Securonix Threat Research: Den Iuzvyk, Tim Peck, Oleg Kolesnikov
tl;dr
Exploitation attempts against government organizations by Storm-0978 (RomCom) are leveraging new Microsoft zero-days (CVE-2023-36884) affecting Microsoft Office products. In this advisory, we focus on how the current and future variants of the attacks can be detected using security analytics.
Last week, Microsoft published an advisory highlighting an ongoing campaign led by the threat group Storm-0978 AKA: RomCom. The threat actors were targeting European government officials with phishing emails containing lure documents framed around the current political climate around NATO and the situation in Ukraine.
The threat actors are a cyber criminal organization based out of Russia known for crafty phishing lures which oftentimes lead to ransomware. They’re mostly attributed to their RomCom backdoor and have been very active lately targeting Ukraine including its military in past campaigns.
Brief attack chain overview
The threat was originally discovered by Blackberry’s threat research team who performed a deep analysis of the attack chain, and the parts involved. Their analysis is quite comprehensive so we won’t be going too deep today.
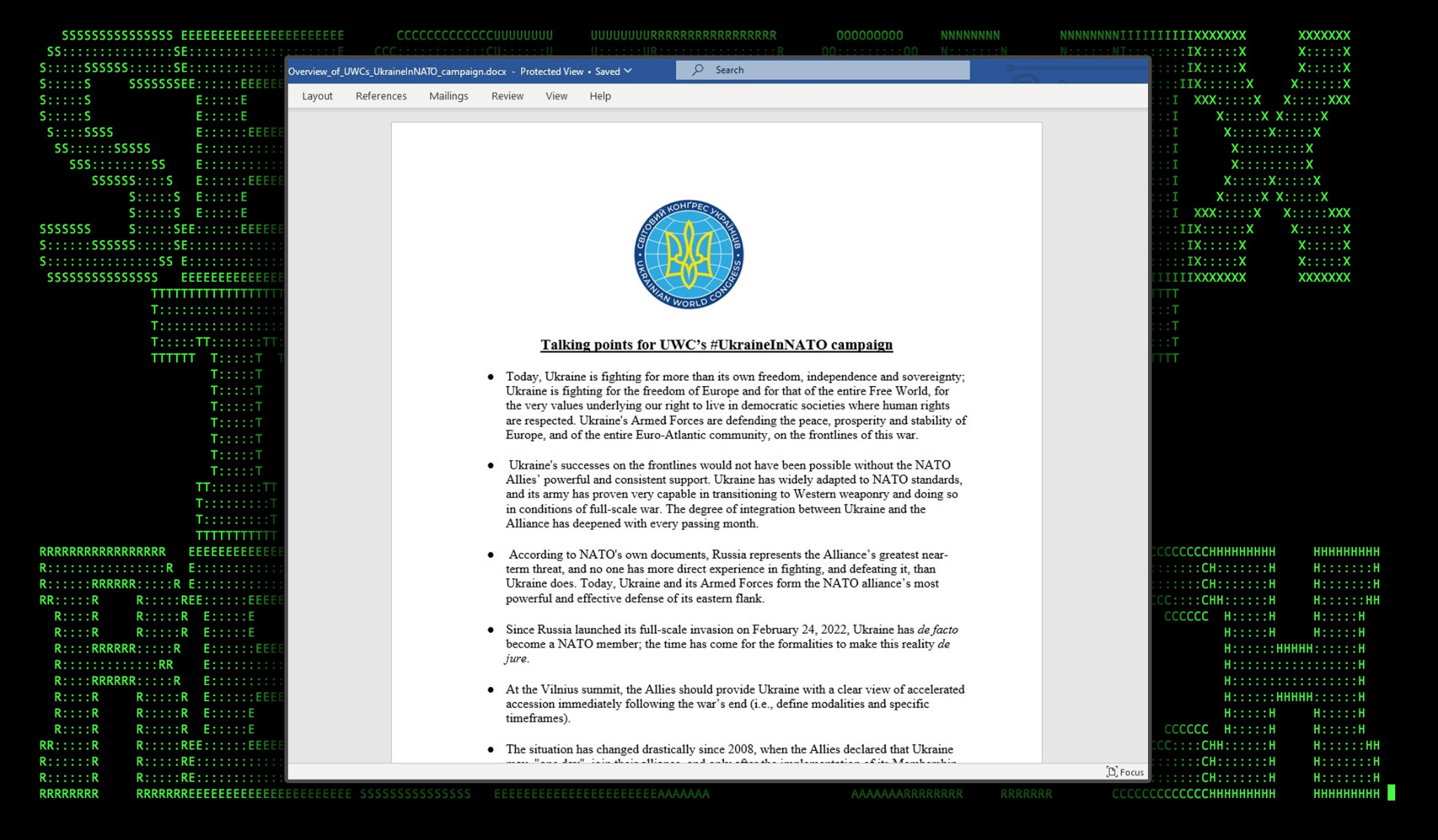
In a nutshell the attack is carried out once the user opens the attached email file, in this case “Overview_of_UWCs_UkraineInNATO_campaign.docx”. The remote code execution vulnerability is triggered once the document is opened. Unlike traditional Office doc attacks, this particular attack does not leverage VBA macros. According to Microsoft, details on the vulnerability associated with CVE-2023-36884 states:
“An attacker could create a specially crafted Microsoft Office document that enables them to perform remote code execution in the context of the victim. However, an attacker would have to convince the victim to open the malicious file.”
Once the document is opened a hidden contained OLE object from within the docx file is loaded which establishes a connection to a remote SMB share at:
\\104.234.239[.]26\share1\MSHTML_C7\file.url
Next, the file “file001.url” is downloaded and executed. The file builds a path to the victim user’s temp directory which is used for staging further payloads.
C:\Users\username\appdata\local\temp\
In addition to the directory above, further payloads including the main RomCom RAT payload are staged from:
C:\Users\Public\AccountPictures\Defender
Three additional HTTP requests are made to download and execute the contents of a “smart.xml” file from the same C2 server. Stagers and payloads are then downloaded with the end result being a portable executable file being downloaded with the name “Calc.exe” which contains the RomCom RAT payload.
How Securonix can help defend against RomCom RAT and CVE-2023-36884
Phishing emails continue to be a wildly popular method of malware delivery from threat actors. Always be extra vigilant with unsolicited emails especially when a sense of urgency is stressed. While most threat actors have been shifting away from Office document files, it’s important to remain extra vigilant despite their decreased usage.
When it comes to prevention and detection, the Securonix Threat Research Team recommends:
- Avoid opening any attachments especially from those that are unexpected or are from outside the organization, MS Office files in particular in regard to this campaign.
- Deploy Microsoft’s mitigation strategy via the FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION registry key found on the CVE details page
- Deploy additional process-level logging such as Sysmon and PowerShell logging for additional log detection coverage
The Threat Research team is continuing to monitor the progression of this particular zero-day and associated attack chain. Below are some relevant detection coverage policies, and Spotter queries threat hunters can use to check for signs of infection.
Relevant Securonix detection policies
- EDR-ALL-30-ER
- EDR-ALL-730-ER
- CEDR-ALL-30-ER
- EDR-ALL-1171-ERR
- EDR-ALL-1215-ERR
- WEL-ALL-1186-ERR
- EDR-ALL-1163-RU
- EDR-ALL-1242-RU
- NTA-ALL-890-ERR
Relevant Spotter queries (be sure to remove [] brackets)
- rg_functionality= “Endpoint Management Systems” and baseeventid = 3 and destinationprocessname IN (Onenote.exe, Winword.exe, Excel.exe, Onenotem.exe, Mspub.exe, Msaccess.exe, Powerpnt.exe, Outlook.exe, Excelcnv.exe, Visio.exe) and (destinationport=445 or destinationport=139)
- (rg_functionality = “Next Generation Firewall” OR rg_functionality = “Web Proxy”) AND ipaddress IN (“104.234.239[.]26″,”74.50.94[.]156″,”138.124.183[.]8″,”45.9.148[.]118″,”45.9.148[.]123″,”209.159.147[.]170″,”65.21.27[.]250″,”209.127.116[.]190”)
- index=activity AND (rg_functionality=”Next Generation Firewall” OR rg_functionality = “Web Proxy”) AND destinationhostname NOT NULL AND (destinationhostname CONTAINS “finformservice[.]com” OR destinationhostname CONTAINS “bentaxworld[.]com” OR destinationhostname CONTAINS “baltimata[.]org”)
- index = activity AND rg_functionality = “Endpoint Management Systems” AND (deviceaction contains “ProcessRollup2” OR deviceaction contains “Procstart” OR deviceaction contains “Childproc” OR deviceaction contains “Process” OR deviceaction contains “Process Create” OR deviceaction contains “Trace Executed Process” OR deviceaction contains “Process Create (rule: ProcessCreate)” OR deviceaction contains “Process Activity: Launched” OR deviceaction contains “Process Activity: Open”OR deviceaction contains “CreateProcessArgs” OR deviceaction contains “ProcessExecOnPackedExecutable” OR deviceaction contains “ProcessRollup2Stats” OR deviceaction contains “SyntheticProcessRollup2” OR deviceaction contains “WmiCreateProcess” OR deviceaction contains “ProcessCreated” OR deviceaction contains “ingress.event.process” OR deviceaction contains “ingress.event.childproc” OR deviceaction contains “endpoint.event.procstart”) AND destinationprocessname STARTS WITH “C:\Users\Public\AccountPictures”
MITRE ATT&CK matrix
| Tactic | Technique |
|---|---|
| Initial Access | T1566: Phishing T1566.001: Phishing: Spearphishing Attachment |
| Execution | T1204.002: User Execution: Malicious File |
| Defense Evasion | T1036: Masquerading T1055.002: Process Injection: Portable Executable Injection T1218.011: System Binary Proxy Execution: Rundll32 |
| Persistence | T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Command and Control | T1573.001: Encrypted Channel: Symmetric Cryptography T1105: Ingress Tool Transfer T1571: Non-Standard Port |
| Lateral Movement | 1021: Remote Services |
| Exfiltration | T1041: Exfiltration Over C2 Channel |
Associated file hashes
| File Name | SHA256 (IoC) |
|---|---|
| Overview_of_UWCs_UkraineInNATO_campaign.docx | a61b2eafcf39715031357df6b01e85e0d1ea2e8ee1dfec241b114e18f7a1163f |
| Letter_NATO_Summit_Vilnius_2023_ENG(1).docx | 3a3138c5add59d2172ad33bc6761f2f82ba344f3d03a2269c623f22c1a35df97 |
| afchunk.rtf | e7cfeb023c3160a7366f209a16a6f6ea5a0bc9a3ddc16c6cba758114dfe6b539 |
| File001.url | 07377209fe68a98e9bca310d9749daa4eb79558e9fc419cf0b02a9e37679038d |
| Calc.exe | 1a7bb878c826fe0ca9a0677ed072ee9a57a228a09ee02b3c5bd00f54f354930f |
| Overview_of_UWCs_UkraineInNATO_campaign.LNK | d3263cc3eff826431c2016aee674c7e3e5329bebfb7a145907de39a279859f4a |
Network infrastructure
| IP/URL | Description |
|---|---|
| 104.234.239[.]26 | Used for initial SMB/HTTP requests |
| 74.50.94[.]156 | Host zip files over HTTP |
| 138.124.183[.]8 45.9.148[.]118 45.9.148[.]123 |
RomCom RAT connection IP |
| 209.159.147[.]170 74.50.94[.]156 209.127.116[.]190 |
Accessed Share on port 3389 |
| 65.21.27[.]250 | SH communication HTTP communication |
| finformservice[.]com | SSH communication |
| bentaxworld[.]com | HTTPS RomCom RAT connection URL |
| hxxp://finformservice[.]com altimata[.]org |
HTTP RomCom RAT connection URL |
References:
- CVE-2023-36884: Office and Windows HTML Remote Code Execution Vulnerability
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-36884 - Microsoft: Storm-0978 attacks reveal financial and espionage motives
https://www.microsoft.com/en-us/security/blog/2023/07/11/storm-0978-attacks-reveal-financial-and-espionage-motives/ - Unattributed RomCom Threat Actor Spoofing Popular Apps Now Hits Ukrainian Militaries
https://blogs.blackberry.com/en/2022/10/unattributed-romcom-threat-actor-spoofing-popular-apps-now-hits-ukrainian-militaries - Blackberry: RomCom Threat Actor Suspected of Targeting Ukraine’s NATO Membership Talks at the NATO Summit
https://blogs.blackberry.com/en/2023/07/romcom-targets-ukraine-nato-membership-talks-at-nato-summit