- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
SIEM
Brian Robertson, Senior Product Marketing Manager
Any great symphony requires all parts, sections, and instruments to work in unison and build off each other to produce the right tone, tempo, and sound. When done right it is a thing of beauty. Like a symphony performing in perfect unison, threats need to be properly detected, investigated, and mitigated across many parts of your security toolset.
Keeping up with sophisticated threats requires forward-looking innovation. That’s why we have introduced a significant number of innovations over the last 24 months. Among them are the Securonix Content Library, Securonix Autonomous Threat Sweeper, and Securonix Investigate. Individually these products and capabilities deliver significant value in the fight against highly complex and aggressive threat actors, but when combined, they can help drive more proactive threat detection that equates to threats being mitigated before they can negatively impact the organization.
The importance of timely and easy to implement threat content
We know when it comes to threat detection, investigation, and response that content is critical to keep pace with new threat tactics, techniques, and procedures (TTPs). There are three main considerations when implementing new content:
- How is content created and how has it been vetted? One of the best things about the cybersecurity community is the willingness to share and provide threat intelligence. Because intelligence originates from many sources it may not be completely accurate or effective depending on the source. An important first step is to be able to validate and vet new threat intelligence. However, organizations often do not have the resources in place to analyze and validate new threat intelligence. They must either take the threat intelligence at face value or depend on vendors to validate new threat intelligence and generate the content needed.
- How can you keep up with the latest threat content? It is important to consider how often content is created and how quickly you can implement it. Having a process where new or updated content is made available in rapid succession allows a SIEM to be up to date, but if that content is difficult to get and take advantage of it doesn’t deliver a lot of value.
- How can threat content be leveraged within your environment? Obviously, once the threat content is implemented, your SIEM will look for signatures, conditions and policy violations related to the new content moving forward. However, many SIEMs do not actively look to see if the condition existed beforehand, requiring security analysts to search through historical data to see if there is a pre-existing condition.
Securonix sees up-to-date threat content as the cornerstone of an effective threat detection, investigation, and response approach. This blog post will explore how Securonix Advanced Content Capabilities can come together to help your organization more effectively combat threats. Take a look at the diagram below – If you look at the Securonix Unified Defense SIEM as a platform, consider the storage and analytics capabilities as the core functions. These advanced capabilities serve as add-ons that can add complementary value by improving how threat content is created, delivered and leveraged.
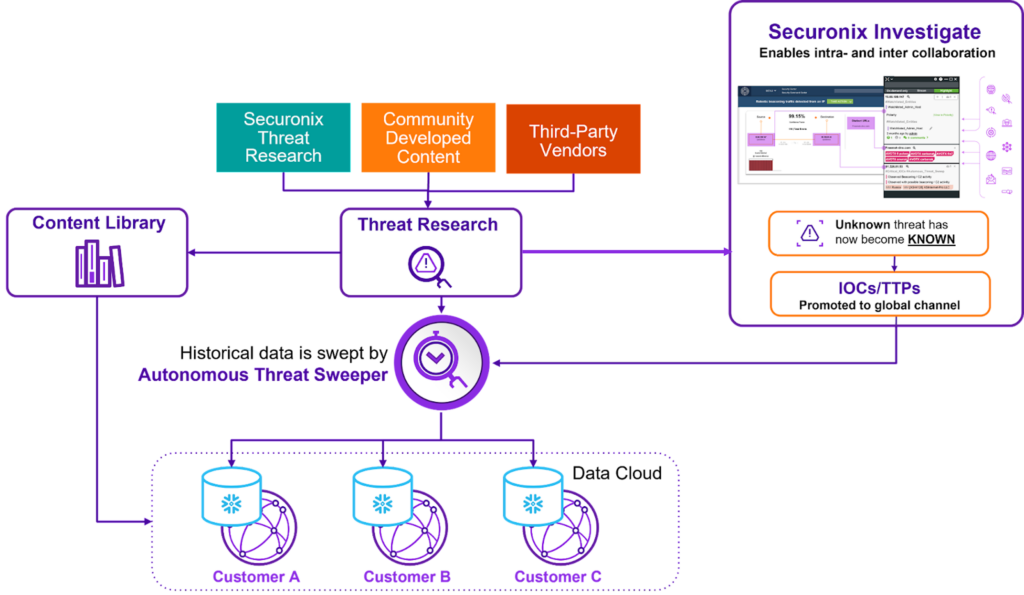
Figure 1.Threat Labs, Autonomous Threat Sweeper and Securonix Investigate combine to provide proactive threat detection.
Getting the effective content you need, quickly and with ease
Securonix Threat Labs is a global team of security experts who monitor our industry for threats in the wild while also reviewing and examining new threat intelligence as it becomes available. This threat intelligence is derived from community developed content, 3rd party vendors, and from our own in-house research. Once new threat intelligence becomes available our Threat Labs team vets the information and validates it. As threat intelligence is validated we create new content that can be leveraged in a couple ways:
- New threat content is added to our Content Library where Unified Defense SIEM users can access it. Because Securonix is cloud-native this new content is readily available to you as soon as it is added to the library. It just takes a few simple clicks to choose it and deploy it in your Securonix SIEM.
- Retroactively search existing data. New content will always look for new threats from the time it is implemented and onward. However, it does not look for pre-existing conditions or incidents of those newly defined threats. This is often done manually by security analysts searching the existing data. Securonix Autonomous Threat Sweeper can search through historic data to look for signs of compromise from newly defined threat incidents. Once an incident is identified, it generates a report for the security analysts to know exactly how to mitigate it.
Deriving updated threat content from your environment
Threat content developed by Securonix Threat Labs is applicable to most organizations. However, there may be incidents of compromise (IOCs) or TTPs specific to your environment. To better leverage data within your environment Securonix Investigate extracts key information by automating the gathering of system level data and publicly available threat intelligence. Securonix Investigate also fosters team collaboration to share and validate insights found during the investigation process. This information enhances log data with insights about user assets, identified suspicious domains, data from open-source intel reports, and even relevant dark web chatter. This information is used to develop IOC and TTP intelligence content.
Like the content developed by the Securonix Threat Labs team, the content created through Securonix Investigate can be added to the SIEM and Securonix Autonomous Threat Sweeper to look for new threats and the presence of existing threats.
These capabilities come together to allow your organization to take advantage of vetted and validated threat content, deploy it quickly and apply it to historical data. This process allows your Securonix Unified Defense SIEM to leverage threat content that applies to new and emerging threats for up-to-date threat detection, faster investigations, and more effective threat mitigation.
Leveraging peer and partner threat intelligence
So far we have addressed threat content or intelligence derived from Securonix Threat Labs and threat intelligence gathered from your internal systems and external sources. One of the most powerful forms of content is the content created and used by security professionals around the globe. These are your peers and Securonix partners. Securonix ATS allows users to use their threat intelligence to look for threats in their environment. ATS will then sweep their environment looking for threats based on the submitted intelligence. What is unique is once that intelligence is submitted ATS uses that intelligence to sweep all other subscribers’ environments for organizations who have opted into the intelligence-sharing community. If a threat in those other environments is discovered the analysts for those environments are notified of the threat. In this scenario analysts could be notified of threats they weren’t necessarily looking for thanks to security experts in other organizations.
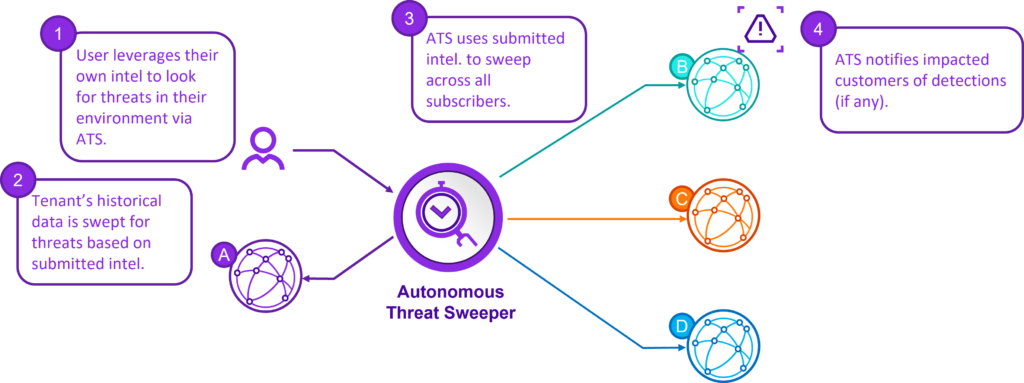
Figure 2:Autonomous Threat Sweeper takes advantage of communal knowledge by automatically searching subscribers’ environments, who have opted into the intelligence-sharing community, using queries created by peers and partners.
Working together to stay ahead of emerging threats
Combining the threat content within Securonix Content Library, Securonix Investigate, and Securonix Autonomous Threat Sweeper work in symphony. As new content is made available it is critical to not only look for new threats from that moment forward, but also retrospectively search for the newly identified threats that may already exist in your environment. Securonix ATS and Securonix Investigate have the ability to look through historical data to identify these newly identified threats.
Learn more about the Securonix Unified Defense SIEM here.


