- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Amit Roshan, Aman Shrivastava
The Monthly Intelligence Insights published by Securonix Threat Labs provides a summary of the total number of threats tracked and highlights the top threats during the month. It also provides a synopsis of the threats, indicators of compromise (IoCs), tactics, techniques and procedures (TTPs), and related tags. This may be followed by a comprehensive threat summary from Securonix Threat Labs and search queries from the Securonix Threat Research team. For a full list of the search queries used on Autonomous Threat Sweeper to detect the below mentioned threats, refer to our Github page.
Threat Labs has analyzed and monitored multiple ransomware operations and espionage campaigns targeting Ukraine and the United States for the month of February. These include MuddyWater, HermeticWiper, IssacWiper, Cyclops Blink, LockBit 2.0, BlackByte ransomware activities, and a recent TrickBot campaign. Additional threat campaigns worth noting include Medusa and Flubot, where two threat actors collaborated to target more than 56 mobile banking applications across the US, Spain and Turkey. This will be an ongoing trend where threat actors continue to collaborate to achieve a common goal.
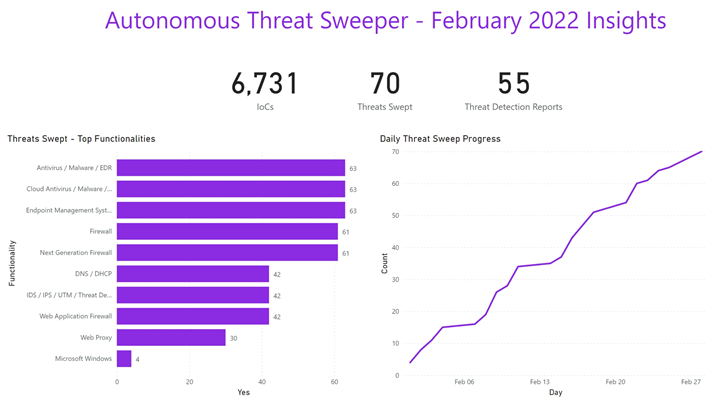
In February, Securonix Autonomous Threat Sweeper identified 6,731 IoCs, 70 distinct threats and reported 55 threat detections. The top three data sources swept against include Antivirus/Malware/EDR, Endpoint Management Systems, and Firewalls.
IssacWiper, HermeticWizard and HermeticRansom Target Ukraine
(Originally Published on: March 1, 2022)
After Russia invaded Ukraine, researchers identified multiple strains of wiper malware targeting Ukraine, subsequently dubbed IssacWiper, HermeticWizard, and HermeticRansom. Interestingly, each malware leveraged the same code signing certificate. Researchers also noticed a decoy ransomware written in Go, dubbed HermeticRansom, to obscure the destructive actions of the malware. As of publishing, these threats have not been attributed explicitly to a particular threat actor, but as geopolitical tensions rise in Eastern Europe, additional and related evidence may be unveiled to a potential nation-state actor.
Threat Labs Summary:
- HermeticWizard spreads HermeticWiper across local networks via Microsoft Windows Management Instrumentation (WMI) and Server Message Block (SMB) protocol.
- The PE timestamp of IssacWiper, dated October 2021, signifies that the malware may have been present in Ukrainian organizations for at least several months, additionally indicating systems being compromised prior to malware identification.
- Eight IoCs are available on Github and have been automatically swept against for Autonomous Threat Sweeper customers.
- TTPs related to HermaticWizard include but are not limited to the following:
- Monitor for commands that gather known local IP addresses using the following Microsoft Windows functions:
- DNSGetCacheDataTable;GetIpNetTable;WNetOpenEnumW(RESOURCE_GLOBALNET, RESOURCETYPE_ANY);NetServerEnum;GetTcpTable;GetAdaptersAddresses
- Monitor for commands that leverage Microsoft Windows WMI or SMB services to further move laterally into the network:
- WNetAddConnection2W; CopyFileW; CoCreateInstance ; CLSID_WbemLocator samr; browser; netlogon; lsarpc; ntsvcs; svcctl
- Monitor for a new process creation on the systems with the argument: “C:\Microsoft Windows\system32\cmd.exe /c start C:\windows\system32\\regsvr32.exe /s /i C:\windows\<filename>.dll”; “cmd /c start regsvr32 /s /i ..\\<filename> & start cmd /c \”ping localhost -n 7 & wevtutil cl System\””
- Monitor for commands that gather known local IP addresses using the following Microsoft Windows functions:
Tags: Malware Family: Disk-wiping | Target Industries: Government, Financial Organizations, Aviation, IT services | Target Countries: Ukraine, Latvia, Lithuania
MuddyWater Targets Organizations Worldwide
(Originally Published on: February 24, 2022)
Authorities from the US and the United Kingdom have released a detailed advisory regarding the cyber espionage activity of MuddyWater, which is an advanced persistent threat (APT) actor purportedly state-sponsored by Iran and works in the interests of the Ministry of Intelligence (MOIS). MuddyWater has been targeting a range of government and private organizations from multiple industries across the globe, including telecom, defense, oil and gas. MuddyWater leverages multiple families of malware in their actions, ranging from PowGoop, Small Sieve, Mori and POWERSTATS, via their preferred threat vector of spear-phishing campaigns, in which they wheedle their targeted victim into downloading ZIP files, containing either a Microsoft Excel file with a malicious macro that communicates with MuddyWater’s Command and Control (C2) server or a PDF file that drops a malicious file to the victim’s network.
Threat Labs Summary:
- A new Python backdoor, dubbed Small Sieve, is notable as it can avoid detection by using custom string and traffic obfuscation schemes together with the Telegram Bot application programming interface (API).
- The use of a single byte XOR encrypts communications with the key 0x02 to adversary-controlled infrastructure.
- PowGoop malware was used as the main loader in malicious operations which consisted of a DLL loader and a PowerShell-based downloader.
- Canopy/Starwhale malware was distributed through a spear-phishing campaign with malicious attachments
- MuddyWater operates the Mori backdoor, which uses domain name system (DNS) tunneling to communicate with the group’s C2 infrastructure.
- The POWERSTATS backdoor was used to run PowerShell scripts to maintain persistent access to the victim systems.
- 29 IoCs are available on Github and have been automatically swept against for Autonomous Threat Sweeper customers.
- TTPs related to MuddyWater include but are not limited to the following:
- Monitor for the following rare processes being executed:
- gram_app.exe, index.ex
- Monitor for the following rare files / DLLs being created:
- Cooperation terms.xls, FML.dll, MicrosoftWindowsOutlookDataPlus.txt
- Monitor for persistence with any modifications to the current user startup folder
- file path contains \Windows\Start Menu\Programs\Startup
- Monitor for rare registry modifications:
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run\OutlookMicrosoft
- Monitor for the following rare processes being executed:
Tags: Adversary: MuddyWater, Static Kitten | Target Industries: Government, Telecom, Oil & Gas, Defense | Target Continents: Asia, Europe, NorthAmerica, Africa | Malware: PowGoop, Small Sieve, Mori and POWERSTATS
HermeticWiper Malware Targets Ukraine
(Originally Published on: February 23, 2022)
On the evening of February 23, 2022, the State Service of Special Communication and Information Protection of Ukraine declared that a number of government and banking institutions had undergone a massive Distributed Denial-of-Service (DDoS) attack. Soon after this announcement, the ESET Research team discovered a new data wiper malware (Win32/KillDisk.NCV) that attacked Ukraine’s computer network nationwide with the objective of destroying data and disrupting businesses. The initial analysis of data wiper malware suggests that it is an executable file signed with a likely stolen certificate issued to a Cyprus-based company Hermetica Digital Ltd. Hence, the researchers named malware as ‘HermeticWiper’.
Threat Labs Summary:
- Upon execution, HermeticWiper enables process token privileges, which gives read access control to any file.
- It checks and verifies the operating system architecture, then drops the copy of the EaseUS Partition Manager driver accordingly.
- Re-enables the process token privileges to load and unload device drivers, followed by the disabling of crash dumps and volume shadow services (VCC).
- HermeticWiper corrupts all master boot records (MBR) for every physical drive present in the system, and also corrupts all the available disk partitions, including NTFS and FAT file systems.
- 58 IoCs are available on Github and have been automatically swept against for Autonomous Threat Sweeper customers. As this is a developing threat, the Autonomous Threat Sweeper will continue to identify and sweep additional related IoCs.
- TTPs related to HemeticWiper include but are not limited to the following:
- Monitor for registry key changes to disable crashdumps (CrashDumpEnabled = 0) from the path “HKLM\SYSTEM\CurrentControlSet\Control\CrashControl”
- Monitor for rare registry key changes to disable “ShowCompColor”, “ShowInfoTip” from the path “\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced”
- Monitor for rare privilege escalation attempts related to the following privileges (SeShutDownPrivilege, SeBackupPrivilege, SeLoadDriverPrivilege)
- Monitor for rare commands executed to identify the operating system version ( i.e. command line contains VerSetConditionMask; VerifyVersionInfoW)
- Monitor for rare processes spawned from command prompts such as “expand.exe”
- Monitor for rare sys files created on system folders (Eg: %WINDIR%\system32\driver\<random_2chars>dr.sys)
Tags: Malware Family: Disk-wiping | Target Industries: Government, Financial Organizations, Aviation, IT services | Target Countries: Ukraine, Latvia, Lithuania
Sandworm from Russia uses Cyclops Blink malware
(Originally Published on: February 23, 2022)
Authorities from the US and UK have come across a new strain of malware dubbed Cyclops Blink, which is said to be a replacement of an infamous malware called VPNFilter which wreaked havoc by infecting half a million routers in 2018. This malware has been attributed to a well-known APT group called Sandworm, which is formally connected to Russia’s military intelligence unit (GRU) and associated with a major power outage in Ukraine in 2015. Cyclops Blink has been in the wild since 2019 and has expanded its targets to small office/home office routers (SOHO) including but not limited to the WatchGuard Firebox.
Threat Labs Summary:
- Cyclops Blink is a malicious Linux ELF executable, compiled for the 32-bit PowerPC (big endian) architecture.
- It is generally deployed as part of a firmware update designed to achieve persistence when the device is rebooted, making any attempts at remediation much more difficult.
- WatchGuard estimates approximately 1% of active WatchGuard firewall appliances have been affected.
- Sandworm has the capability to create huge sets of botnets from these firewall devices.
- 37 IoCs are available on Github and have been automatically swept against for Autonomous Threat Sweeper customers.
- TTPs related to Cyclops Blink include but are not limited to the following:
- Cyclops Blink executes downloaded files using the Linux API function execlp.
- Monitor rare command line parameters for the process “kworker” with the command line “/proc/self/exe”
- Cyclops Blink communicates over non-standard ports on HTTP and HTTPS protocols.
- Monitor for C2 communication on HTTP and HTTPS protocols for non-standard ports
- Cyclops Blink is capable of uploading files to a C2 server.
- Monitor for exfiltration to C2 server over covert channels such as SSH, Telnet, Microsoft Remote Desktop Protocol (RDP), DNS
- Cyclops Blink executes downloaded files using the Linux API function execlp.
Tags: Adversary: SandWorm, VoodooBear | Target Industries and Products: Energy, WatchGuard Firewall, Routers| Target Countries: Ukraine, Georgia
TrickBot Targets Global Financial Organizations’ Customers
(Originally Published on: February 16, 2022)
Researchers from CheckPoint have analyzed a campaign by TrickBot operators who have been targeting major global organizations, the majority of whom are financial institutions. TrickBot leverages multiple on-demand modules including anti-analysis techniques which makes it difficult for security researchers to send automated requests to C2 servers to receive fresh web-injects. According to additional research from AdvIntel, the TrickBot campaign has been taken over by Conti ransomware operators, taking advantage of TrickBot’s sophisticated nature to gain initial access to their victims’ corporate network.
Threat Labs Summary:
- TrickBot operators leveraged three modules: injecDll, tabDll and pwgrabc
- APAC and Europe are currently major targets of Trickbot
- The malware used the EternalRomance exploit to spread via the SMBv1 network share.
- This campaign, one of the most critical campaigns in February, has targeted more than 60 major firms of which most of them are US-based.
- 3 IoCs are available on Github and automatically swept against for Autonomous Threat Sweeper customers
- TTPs related to TrickBot include but are not limited to the following:
- Monitor for the rare behavior where O365 applications call rundll32.
- Monitor for rare parent-child process combinations where the source is one of: ”word, excel, ppt, outlook” and the target is “rundll32.exe”
- Monitor for the rare behavior where PowerShell creates remote threads in legitimate Windows binaries.
- Monitor for rare parent child–process combinations where the source is “powershell” and the target is any of these binaries: “svchost.exe, csrss.exe, gpupdate.exe, explorer.exe, services.exe, winlogon.exe, smss.exe, wininit.exe, userinit.exe, spoolsv.exe, taskhost.exe”
- Monitor for suspicious and rare named pipe creation that enables communication with C2.
- Monitor for pipes created with names ending in lacesomepipe.
- Monitor for the spike in the number of attempts to access hives and folders for more than one credential source, such as Mozilla Firefox, Google Chrome, Internet Explorer, VNC, and RDP.
- Monitor for the rare behavior where O365 applications call rundll32.
Tags: Malware Family: TrickBot | Industries: Financial Organizations | Associated Malware: Bazar Backdoor
BlackByte Ransomware Targeted Critical Infrastructure
(Originally Published on: February 11, 2022)
In the second week of February, the FBI released an advisory regarding the indicators of compromise (IoCs) for BlackByte ransomware. Multiple compromises have been linked to BlackByte since November 2021, where the targets ranged from multiple US and foreign businesses, including entities in at least three US critical infrastructure sectors (government facilities, financial, and food and agriculture). Additionally attackers exploited a known Microsoft Exchange Server vulnerability to gain initial access. As a result of these attacks, victims found a ransom note in all directories where files were encrypted. A day after the advisory was released, the San Francisco 49ers, a US National Football League team, revealed that they had been compromised by BlackByte, as the threat actors listed the team in their victim list on the dark web.
Threat Labs Summary:
- BlackByte encrypts files without communicating with external IP addresses.
- Largely runs executables from c:\windows\system32\ and C:\Windows\.
- 42 IoCs are available on Github and have been automatically swept against for Autonomous Threat Sweeper customers.
- The campaign was critical for the month as the ransomware operators have modified their TTPs compared to 2021 and industry targets expanded from healthcare to manufacturing in the U.S, Europe and Australia.
- TTPs related to BlackByte ransomware include but are not limited to the following:
- Monitor for print bombing where the process “cmd” launches “wordpad” or “notepad” doc files and prints using “/p” command. Monitor for a spike in this activity.
- Monitor for mounting of external volumes via malicious drivers through the process “mountvol.exe”
- Monitor for rare command line parameters for mountvol.exe
- Malicious registry modifications by enabling “LongPathsEnabled” within the Filesystem control
- Monitor cmd.exe where rare registries are added, specifically look for “SYSTEM\CurrentControlSet\Control\FileSystem”
- Monitor attempts at disabling User Access Control (UAC) remote restrictions CommandLine
- Detecting a rare modification of the “LocalAccountTokenFilterPolicy” registry key that can be used to disable UAC remote restrictions. Monitor for rare activity for this behavior.
- Monitor any firewall rules modification
- Detect modification of firewall with “netsh” command
- Monitor any rare scheduled tasks modifications and/or being disabled to avoid possible detection of their malware/tools and activities
- eg: “schtasks.exe /DELETE /TN”
- Monitor rare processes or files spawned from the following locations
- %AppData%,Program Files\Microsoft\Exchange Server,%HOMEPATH%,
Tags: Ransomware: BlackByte | Industries: Government, Healthcare, Construction, Manufacturing | Tools: PowerShell, Cobalt Strike | Targets: Europe, US, Australia
LockBit Ransomware TTPs and IoCs
(Originally Published on: February 04, 2022)
February 2022 began with an FBI Flash report on LockBit ransomware, which listed IoCs and TTPs for LockBit 2.0. The LockBit group operates in the ransomware-as-a-service (RaaS) model and has been actively operating for nearly three-and-a-half years, while constantly shifting their identified TTPs. In the last six months, the LockBit group has attacked more than 50 organizations across multiple industries across the globe per their leak site on the dark web. It was also discovered that the malware comes with a hidden debug window that can be activated during the infection process. Interestingly, LockBit 2.0 will not infect a system if Russian or closely related languages from similar territories are detected.
Threat Labs Summary:
-
- Initial access is gained via exploiting unpatched vulnerabilities and zero-day exploits.
- Automatically encrypt devices in a Microsoft Windows domain using Active Directory (AD) group policies.
- Uses various methods to exfiltrate the data like–admin panel via HTTP, rclone and MEGAsync file sync services.
- Use Stealbit application to remove defined file types.
- LockBit ransomware operators are best described as consistent and versatile that adapt the current trends to attack an organization. Threat Labs believes that LockBit operators will continue their level of activity and advises organizations to update themselves with the latest TTPs and IoCs shared below.
- 12 IoCs are available on Github and have been automatically swept against for Autonomous Threat Sweeper customers.
- TTPs related to LockBit 2.0 ransomware include but are not limited to the following:
- Monitor any impact against built-in recovery and logging mechanisms
- Detect processes like “cmd.exe” with parameters “/c vssadmin Delete Shadows /All /Quiet”; “cmd.exe /c bcdedit /set {default} recoveryenabled No”; “cmd.exe /c bcdedit /set {default} bootstatuspolicy ignoreallfailures”
- Monitor any impact against built-in recovery and logging mechanisms
- Monitor for deletion of log data using “wevtutil” or deleting the ransomware itself by running the following parameters: “(del /f /q “<PATH>\Lsystem-234-bit.exe”)”
-
- Monitor for rare files created or processes executed from the following paths:
- C:\Users\<Username>\Desktop\ , C:\Windows\SysWOW64\ , these files usually contain the extension .ico/.tmp.bmp/.lockbit (Lockbit file)
- The ransomware note is usually a text file of the form “Restore-My-Files.txt “
- Monitor for rare files created or processes executed from the following paths:
Tags: Ransomware: LockBit | Targeted Industries: Financial, Professional Services, Manufacturing | Tools: Mimikatz, PsExec, Stealbit malware | Targeted Regions: NorthAmerica, Europe, Asia Pacific
For a full list of the search queries used on Autonomous Threat Sweeper to sweep for these threats detailed above, refer to our Github page. The page also references a list of relevant policies with the attacker group.
We would like to hear from you. Please reach out to us at aths@securonix.com.
Note: The TTPs when used in a silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Rajesh Lohani, Tim Johny, Yashraj Manshani, Mohammed Zibran, Kayzad Vanskuiwalla, Sina Chehreghani







