- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, Ella Dragun
The Monthly Intelligence Insights provides a summary of top threats curated, monitored, and analyzed by Securonix Threat Labs during January. The report additionally provides a synopsis of the threats; indicators of compromise (IOCs); tactics, techniques, and procedures (TTPs); and related tags. This may be followed by a comprehensive threat summary from Threat Labs and search queries from the Threat Research team. For additional information on Threat Labs and related search queries used via Autonomous Threat Sweeper to detect the below mentioned threats, refer to our Threat Labs home page.
In January 2023, Threat Labs analyzed and monitored major threat categories, including multiple cyber campaigns involving APT groups, digital ads threats, vulnerability exploitation, and attacks on the Iranian government. Of note are new threat groups such as the pro-Russian hacking group named NoName057(16), Dark Pink APT group, and VagusRAT. In addition, researchers from Mandiant have identified a China-nexus threat actor who exploited a recently patched vulnerability in Fortinet FortiOS SSL-VPN as a zero-day in attacks targeting a European government entity and a managed service provider (MSP) located in Africa.
Furthermore, a number of vulnerabilities were found by EclecticIQ analysts who researched QakBot phishing campaigns that can turn it to a zero-day vulnerability to evade Windows Mark of the Web (MoTW). QakBot may increase its infection success rate as a result of the switch to a zero-day exploit.
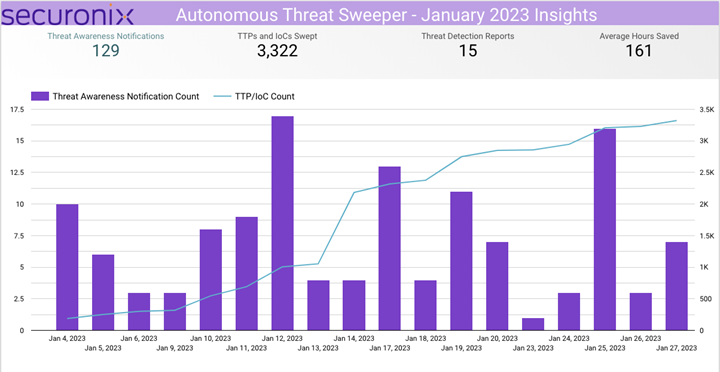
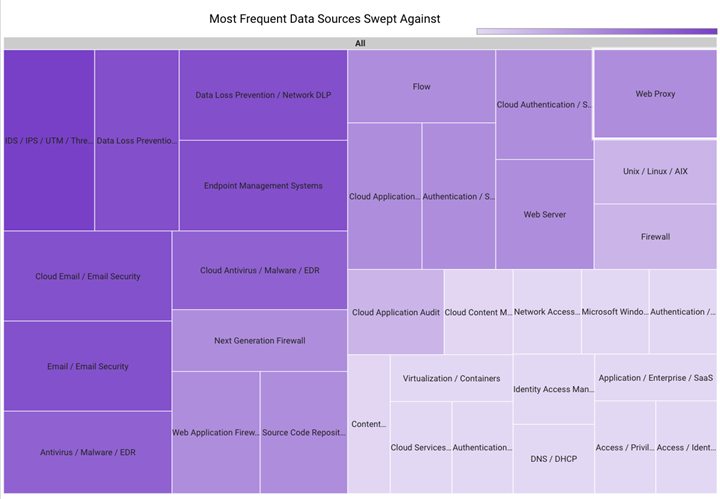
In January 2023, Securonix Autonomous Threat Sweeper identified 3,322 TTPs and IOCs, 129 distinct threats, and reported 15 threat detections. The top data sources swept against include IDS/IPS/UTM/Threat Detection, Endpoint Management Systems, Data Loss Prevention, and Email / Email Security.

Ongoing RAT phishing campaign in January
(Originally published in January 2023)
Securonix researchers identified PY#RATION, a Python-based RAT used in a new attack campaign since at least August 2022 to gain control over compromised systems. In this malware, communications are established via the WebSocket protocol, and data is stolen from the victim host using the command and control (C2) server. Moreover, it offers a host of capabilities for harvesting sensitive information. Phishing campaigns distribute the malware via password-protected Zip files containing two shortcut .LNK files disguised as images, namely front.jpg.lnk and back.jpg.lnk, which appear as British driver’s licenses.
The prevalence of RAT campaigns was acknowledged in a report by CISA, the NSA, and MS-ISAC which found that attackers are increasingly exploiting legitimate remote monitoring and management tools. Additionally, CISA implemented the EINSTEIN intrusion detection system to detect malicious activity on the networks of several federal civilian executive branch agencies. Many other FCEB (Federal Civilian Executive Branch) networks were affected as well by this widespread, financially motivated phishing campaign as reported by Silent Push. Beginning around mid-June 2022, attackers began sending out phishing emails themed around help desks to federal staff members’ personal and government email addresses.
Threat Labs summary
Securonix Threat Labs recommends leveraging our findings to deploy protective measures from phishing attacks. Threat Labs observed a user’s temporary directory was created with ‘Cortana’ and ‘Cortana/Setup’ directories, and additional executable files were downloaded, unpacked, and run from those directories. The malware is not only relatively hard to detect, but the fact that PY#RATION is a Python-compiled binary that makes it flexible, as it can be installed on almost any target including Windows, OSX, and Linux.Securonix Threat Labs recommends that users not click on any link from unknown senders nor give any information on an unsecured site.
31 IOCs are available on our Threat Labs home page repository and have been swept against Securonix Autonomous Threat Sweeper customers.
TTPs related to the PY#RATION malware include but are not limited to the following and can be detected as follows:
- Monitor for rare JavaScript and batch file execution from temp location.
- Example: wscript.exe “%tmp%/CortanaDefault.bat”, wscript.exe “%tmp%/inv.vbs” “%tmp%/settings.bat”
- Monitor for the rare and suspicious usage of the -decode parameter along with Certutil.exe
- Example: certutil -decode “localappdata%/Cortana/setup/unrar.cert” “localappdata%/Cortana/setup/unrar.exe”
- Monitor for the presence of suspicious and rare batch files in the startup directory.
- Example: %appdata%/Microsoft/Windows/Start Menu/Programs/Startup/CortanaAssist.bat
- Monitor for abnormal spike in traffic over port 5555.
Tags: Malware: PY#RATION | Attack type: Phishing email, Phishing sites
Active APT groups in January
(Originally published in January 2023)
Security researchers discovered a new advanced persistent threat (APT) group named Dark Pink. The primary attack vector is spear-phishing emails posing as job applications that trick victims into downloading malicious ISO files. From June to December 2023, at least seven successful attacks were launched. In addition to targeting government agencies and military bodies, the group also uses custom malware to eavesdrop on messages in messengers, steal sensitive information from victims’ browsers, exfiltrate documents, and capture audio from the microphone of infected devices.
Another APT group tracked as Scattered Spider attempted to deploy Intel ethernet diagnostics drivers in a bring your own vulnerable driver (BYOVD) attack to evade detection from endpoint detection and response security products.
According to researchers, a high-severity vulnerability in Intel’s ethernet diagnostics driver known as CVE-2015-2291 allows an attacker to execute arbitrary code with kernel privileges.
In this case, a 64-bit kernel driver used by the threat group has 35 functions and is signed by different certificates stolen from vendors like NVIDIA and Global Software LLC, so Windows does not block it. These drivers are used to disable endpoint security products and reduce defender visibility and prevention capabilities, laying the groundwork for subsequent phases of their operations on the targeted networks.
Lastly, a pro-Russian threat group, NoName057(16), launched distributed denial of service (DDoS) attacks against government, military, telecommunications, and transportation organizations, as well as media agencies, suppliers, and financial institutions in Ukraine, Czech Republic, Denmark, Estonia, Lithuania, Norway, and Poland. As noted by the researchers, the group initially targeted Ukrainian news websites but shifted focus later to NATO-associated websites aimed at silencing their anti-Russian content.
A Telegram Messenger channel is used by NoName057(16) to claim responsibility for disruptions, justify its actions, threaten, and mock targets. They also use GitHub to host tools advertised on their Telegram channel, including DDOSIA, a multi-threaded Python and Golang application. GitHub immediately removed NoName057(16)-associated accounts and repositories after being notified about the nefarious activity.
Threat Labs summary
Securonix Threat Labs is actively monitoring campaigns by multiple threat actors that are targeting victims worldwide, as they are spreading rapidly again.
- Securonix Threat Labs recommends leveraging our findings to deploy protective measures against the threat groups.
- Threat Labs observed that among Dark Pink’s victims are Vietnamese, Malaysian, Indonesian, Cambodian, and Filipino citizens, as well as one European (from Bosnia and Herzegovina).
- Threat Labs observed that the hackers from Scattered Spider attempted to use the BYOVD method to bypass Microsoft Defender for Endpoint, Palo Alto Networks Cortex XDR, and SentinelOne.
- 39 IOCs are available on our Threat Labs home page and have been swept against Securonix Autonomous Threat Sweeper customers.
Tags: Threat Actor: Dark Pink, Scattered Spider, NoName057(16) | Target Sector: Government Agencies, Military Bodies, Telecommunications, Transportation, Media Agencies, Financial Institutions
Increased malvertising threats
(Originally published in January 2023)
Ad-based threats increased this month. Multiple researchers including Sekoia have identified the infection chain that is using about a hundred fake cracked software catalog websites that redirect to several links before downloading the payload hosted on file share platforms, such as GitHub.
The attacks are aimed at users who are looking for cracked versions of software and games on search engines like Google, surfacing fake websites on top by exploiting a search engine optimization (SEO) poisoning technique to persuade victims into downloading and executing the malicious payloads.
The virus result comes with a download link to the promised software that, upon clicking, triggers a five-stage URL redirection sequence. This takes the user to a web page displaying a shortened link, which points to a password-protected RAR archive file hosted on GitHub, along with its password.
During the investigation of the suspicious activity, Cyfirma researchers observed the campaigns closely and provided preliminary analysis of a new RAT known as “VagusRAT” and its possible attribution to Iranian threat actors. VagusRAT is also delivered to the victims by exploiting Google ads. The Cyfirma research team during different stages communicated with VagusRAT malware authors and the authors assured them that the malware could be changed based on the need of the user. It seems like the RAT authors are able to be more creative to make a better made version that lets users compromise many different alternatives using the builder, including putting custom file extensions.
Threat Labs summary
- Securonix Threat Labs recommends leveraging our findings to deploy protective measures for increased ads threats.
- Implement network segmentation and maintain offline backups of data to ensure limited interruption to your organization.
- Disable unused ports and enable multi-factor authentication (MFA).
- 322 IOCs are available on our Threat Labs home page and have been swept against Securonix Autonomous Threat Sweeper customers.
Tags: Malware: VagusRAT | Target Platforms: GitHub |Target exploitation: Google Ads
Attack on the Iranian government
(Originally published in January 2023)
Iran has been targeted again by cybercriminals. Researchers say the Playful Taurus threat group has existed since as early as 2010. As part of its constellation-themed naming process, the ATP was given this nickname. The group has been referred to as BackdoorDiplomacy, Vixen Panda, APT15, KeChang, and Nickel as well. New attacks against the Iranian government have been linked to it.
Playful Taurus uses phishing techniques to target government and diplomatic agencies across North and South America, Africa, and the Middle East. In the recent toolkit update, the group added a new variant of the Turian backdoor as well as its command-and-control infrastructure.
According to researchers, between July and late December 2022, four Iranian organizations tried to communicate to the malicious infrastructure via an IP address controlled by the hackers – 152[.]32[.]181[.]16. The organizations included the Ministry of Foreign Affairs and the Agricultural and Natural Resources Engineering Organization.
Threat Labs summary
Securonix Threat Labs is actively monitoring running campaigns by Playful Taurus threat actors that are targeting Iranian government organizations as they begin spreading once again.
- Threat Labs observed that the Turian backdoors have been updated with additional obfuscation and a more efficient decryption algorithm for extracting the C2 servers.
- Threat Labs observed that the malware offers basic functionality, such as updating the C2 server, executing commands, and spawning reverse shells.
- 14 IOCs are available on our Threat Labs home page repository and have been swept against Securonix Autonomous Threat Sweeper customers.
Tags: Threat Actor: Playful Taurus, BackdoorDiplomacy, Vixen Panda, APT15, KeChang, Nickel | Target Sector: Government Organizations | Threat Actor Location: China | Target Location: Iran
Vulnerabilities exploited in January
(Originally published in January 2023)
Eclecticiq warned customers of QakBot phishing campaigns exploitation. Their analysts researched QakBot phishing campaigns which used a zero-day vulnerability to evade Windows Mark of the Web (MoTW). QakBot may be able to increase its infection success rate as a result of the switch to a zero-day exploit. The research showed that QakBot was using phishing emails with a malicious URL inside. When the victim clicks on the malicious URL it starts to download an encrypted ZIP folder that has a malicious ISO image. If the victim opens the ISO image, it can bind it on a disk and open another File Explorer window that contains the final QakBot loader as a JavaScript format which can be executed by a simple user click.
Wordfence researchers observed attack attempts over the Christmas and New Year holidays, which specifically targeted the Downloads Manager plugin by Giulio Ganci. The first spike was on December 24, 2022, with a second spike on January 4, 2023. 92,546,995 scan attempts were seen during the first spike, and the second spike went up to 118,780,958 scan attempts in one day. During that period, Wordfence researchers tracked 466,827 attacking IP addresses. All of these IP addresses kept trying to utilize these vulnerabilities on 2,663,905 protected websites.
In another campaign discovered by Mandient, researchers identified a China-nexus threat actor who exploited a recently patched vulnerability in Fortinet FortiOS SSL-VPN as a zero-day in attacks targeting a European government entity and a managed service provider (MSP) located in Africa. Mandient detected a new Windows variant of BOLDMOVE backdoor and a Linux variant. It was created to hit and run on FortiGate Firewalls. This new chain of Chinese cyber espionage attacks targets internet-facing devices.
Threat Labs summary
- Securonix Threat Labs continues to actively monitor vulnerabilities and exploits while identifying notable threats that could have a tremendous impact if not addressed.
- Securonix Threat Labs recommends updating vulnerable applications to the latest version immediately and following the mitigation guidelines.
- 30 IOCs are available on our Threat Labs home page repository and have been swept against Securonix Autonomous Threat Sweeper customers.
Tags: Vulnerability: QakBot phishing campaigns, the Downloads Manager plugin, Fortinet FortiOS SSL-VPN | Exploitation: Unauthorized Access, Remote Code Execution, Privilege Escalation
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Threat Labs home page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at scia@securonix.com.
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Sina Chehreghani, Dhanaraj K R, Tim Johny







