- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Security Analytics, Threat Research
By Oleg Kolesnikov, Securonix Threat Research Team
Introduction
Last month, we learned of a new cyber attack against the 2018 Winter Olympic Games in South Korea. Securonix Threat Research Team has been actively investigating and monitoring this attack since the attack was reported to help our customers understand the techniques used by attackers to enable effective detection, mitigation, and response to such disruptive cyber sabotage attacks.
In light of the recent alleged attribution of the attack to a nation state by Washington Post and some researchers [1], here is a work-in-progress summary of what we currently know and our recommendations on possible mitigations and Securonix predictive indicators that can be used to detect such attacks.
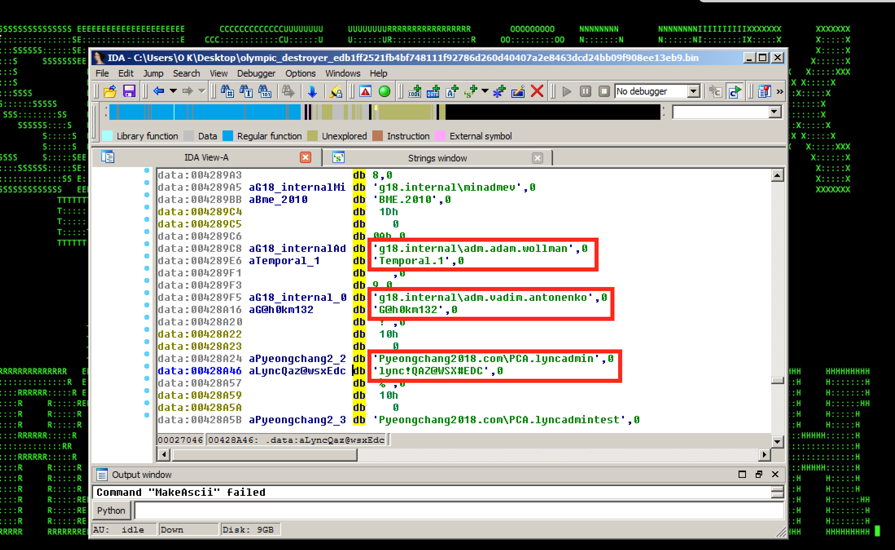
Figure 1: Olympic Destroyer Malicious Implant – Hardcoded Credentials
Summary
Here is a summary of some of the key details about this attack.
Impact:
One of the distinguishing features of the attack was that the attack was a cyber sabotage operation specifically designed to disrupt the Winter Olympic games.
- Attackers managed to disrupt over 300 systems used by the Olympic organization. [1]
- On the day of the opening ceremony, the web site of the 2018 Winter Olympics was brought down for over 12 hours, causing attendees to be unable to print tickets for ceremony, likely resulting in a number of open seats.
- The attack impacted the Olympic stadium’s Wi-Fi access, impacting reporting, and also disrupting the Internet and TV in the press center. [1,2]
- According to some U.S. Intelligence sources and researchers [1,4,5], it is believed that the attack was likely carried out by a nation state while attempting to make it appear as though the intrusion was carried out by North Korea (“false-flag” operation). However, it appears that the available evidence attributing/linking the attack is rather contradictory and may not allow for direct attribution.
Lateral movement:
- Attackers appeared to have a number of technical details regarding the Winter Olympic games internal infrastructure either from an insider or from an earlier reconnaissance stage, including domain and user names (see Figure 1).
- The attack binary also included functionality needed to automatically harvest credentials from the compromised systems including lsass and browsers (see Figure 2). The credentials were then stored in a sqlite database for lateral propagation.
- The main technique used to move laterally between systems was SMB/PSEXEC/WMI-vector leveraging an PSEXEC binary included in the attack binary. [3]
Additional details/possible attribution:
- Some researchers attributed the attack to the Lazarus Group/SWIFT Bangladesh compromise based on the file names and Bluenoroff wiper source code analysis [5];
- Some reports identified possible code sharing between the attack and APT3/10 including functions used to generate AES keys and steal credentials from memory [5];
- The named pipes technique leveraged by the attack binary to pass stolen credentials as well as fragments of the EternalBlue exploit setup (unused) was found to be similar to the techniques used by the Petrwrap/NotPetya ransomware threat we covered last year;
- According to the available details, the initial infiltration vector possibly was a malicious e-mail containing a Microsoft Word attachment that appeared to be from the South Korea National Counter Terrorism site [6].
Observed Artifact Hash Values:
EDB1FF2521FB4BF748111F92786D260D40407A2E8463DCD24BB09F908EE13EB9
D934CB8D0EADB93F8A57A9B8853C5DB218D5DB78C16A35F374E413884D915016
3E27B6B287F0B9F7E85BFE18901D961110AE969D58B44AF15B1D75BE749022C2
28858CC6E05225F7D156D1C6A21ED11188777FA0A752CB7B56038D79A88627CC
F188ABC33D351C2254D794B525C5A8B79EA78ACD3050CD8D27D3ECFC568C2936
A7D6DCDF5CA2C426CC6C447CFF76834D97BC1FDFF2CD14BAD0B7C2817408C334
AE9A4E244A9B3C77D489DEE8AEAF35A7C3BA31B210E76D81EF2E91790F052C85
19AB44A1343DB19741B0E0B06BACCE55990B6C8F789815DAAF3476E0CC30EBEA
AB5BF79274B6583A00BE203256A4EACFA30A37BC889B5493DA9456E2D5885C7F
 Figure 2: Olympic Destroyer – Credential Stealing
Figure 2: Olympic Destroyer – Credential Stealing
Olympic Destroyer – Cyber Sabotage Behaviors
As mentioned earlier, one of distinguishing characteristics of this attack was that the attack was designed for cyber sabotage with the goal of impacting and disrupting as much of the target infrastructure as possible.
As shown in Figure 1, attackers likely had some prior knowledge of the target environment that was probably gained from an earlier attack stage or an insider, including the user names and domain names associated with the target. The knowledge was then leveraged as part of the lateral movement stage. Some of the artifacts/indicators that you are going to see in the logs for this attack include a high number of 4625/4776 credential validation failures and 4648 logons with explicit credentials.
You are also likely going to see a large number of 7040 SCM events associated with the attack attempting to disable your system services by setting them from start to enabled as shown in Figure 3 before rebooting the system. From the credentials used in the attack, the attackers likely compromised the local SIEM and a number of local admin users as the credentials were included in the malicious binary (addc.siem, PCA.WEBAdmin, PCA.SDAdmin etc), which probably provided some further situational awareness insights that were leveraged in the attack.
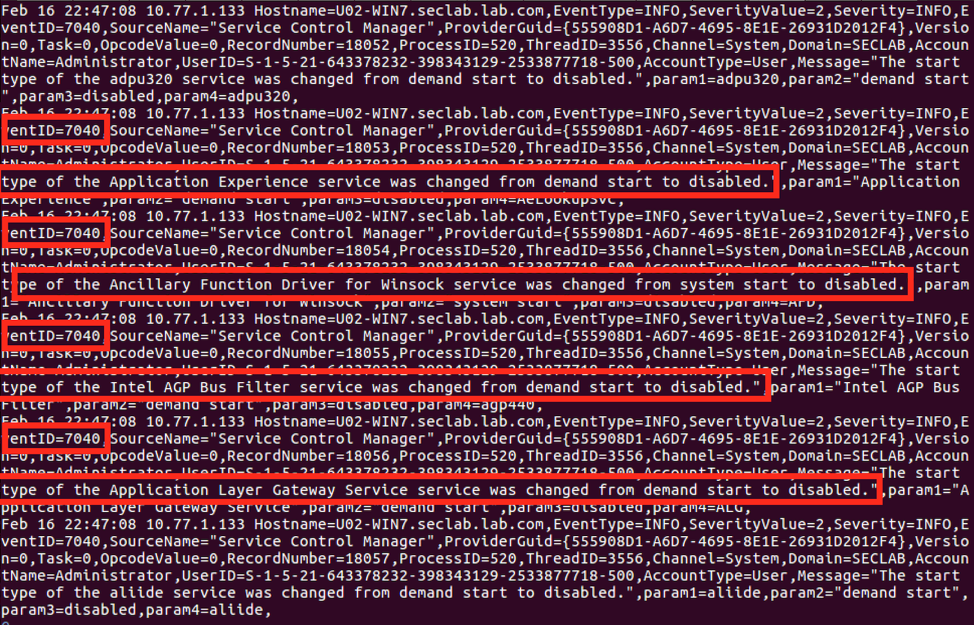
Figure 3: Olympic Destroyer in the Logs
Some further quick highlights pertaining to the cyber sabotage functionality used in the attack include disabling automated shadow volume copies, prohibiting wbadmin to restore individual files, disabling Windows recovery console repair etc:
C:\Windows\system32\cmd. exe /c c:\Windows\system32\vssadmin.exe delete shadows /all /quiet
cmd. exe /c wbadmin.exe delete catalog -quiet
cmd. exe /c bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no
And running some other commands including cscript/vbs staging/lateral movement behaviors as depicted in Figure 4:
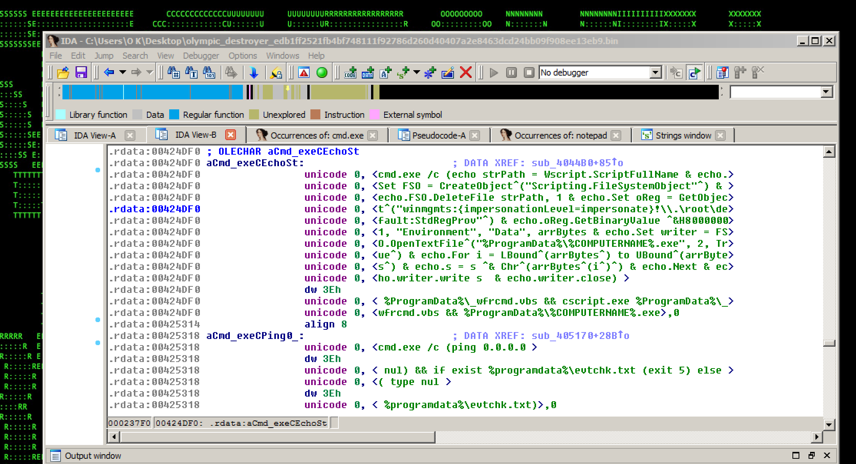
Figure 4: Olympic Destroyer – Embedded Second Stage Payload
you can read some more about the commands ran, including notepad injection etc (see Figure 5) here [3]. Further in-depth technical details of the behaviors including the payloads (see Figures 4-5) were covered by a number of researchers [3,4,5] and are out-of-scope for this article.
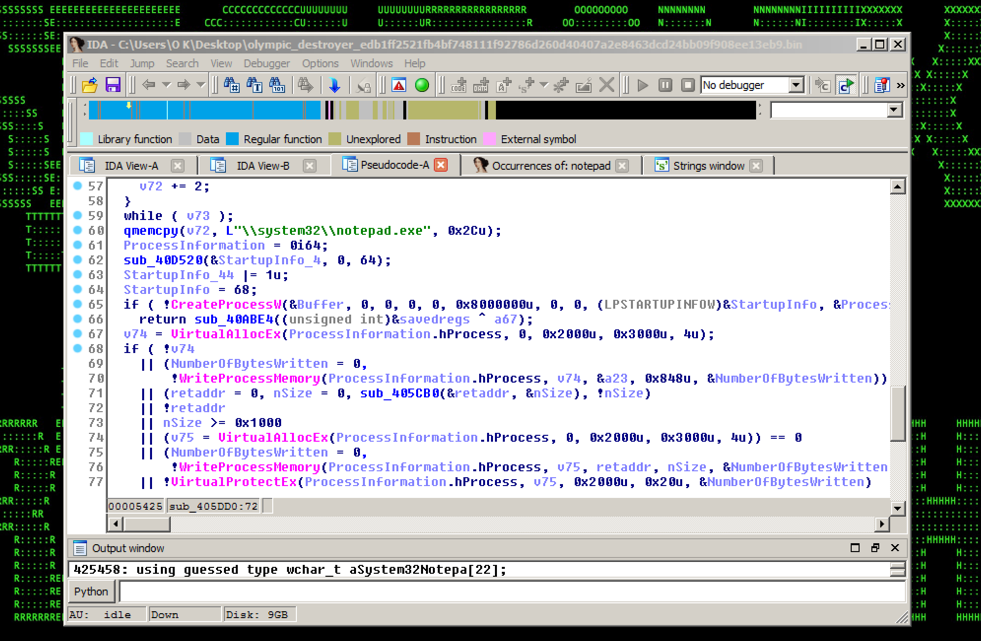
Figure 5: Olympic Destroyer – Notepad Process Migration
Mitigation and Prevention – Scanning
You can check for some possible targets for an SMB-based lateral movement in your environment using a trivial scan e.g.# nmap -sS -O -p139,445 <your_internal_cidr>
Mitigation and Prevention – Securonix Recommendations
Here are some of the Securonix recommendations to help customers prevent and/or mitigate the attack propagation:
- If SMB is not required for your business-as-usual (BAU) activity, reference these recommendations to disable SMB on all internal systems as soon as possible: https://support.microsoft.com/en-us/help/2696547/how-to-enable-and-disable-smbv1,-smbv2,-and-smbv3-in-windows-vista,-windows-server-2008,-windows-7,-windows-server-2008-r2,-windows-8,-and-windows-server-2012
- If PSEXEC is not required for BAU, consider disabling PSEXEC/WMIC either altogether or using a temporary targeted approach e.g. one possible temporary workaround could be setting the IFEO registry key for psexec/wmic to prevent the PSEXEC service from running.
- Disable/rename vssadmin, if feasible, and consider creating regular backups using other means e.g. system restore points with wmic: wmic.exe /Namespace:\\root\default Path SystemRestore call CreateRestorePoint “%DATE%”, 100, 7
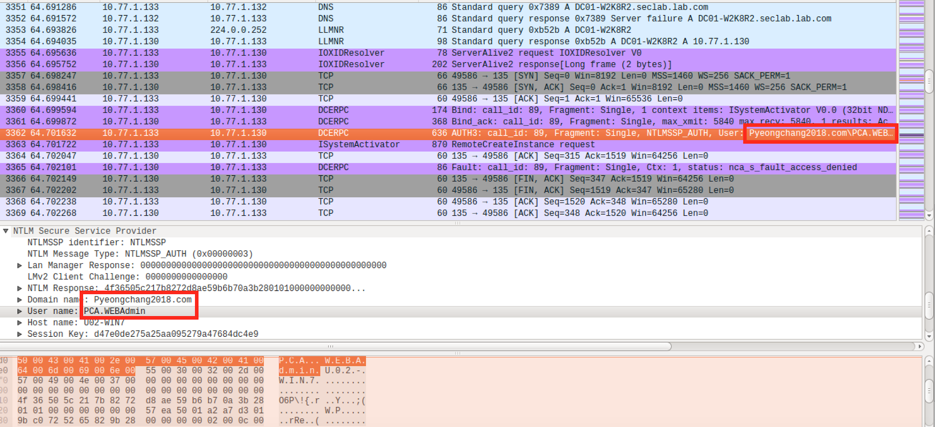
Figure 6: Olympic Destroyer – Lateral Movement using SMB/DCERPC/PSEXEC
Securonix Detection – Some Examples of Securonix Predictive Indicators
Here is a summary of some of the relevant Securonix predictive indicators to increase the chances of early detection of such attacks on your network:
WEL-SCM3-BPI Suspicious Process Activity – Peak Service Disable Analytic
EDR-SYM18-RUN Suspicious Process Activity – Shadow Copy/Backup Deletion Analytic
WEL-OTH1-RUN Suspicious System Activity – Targeted – Log Clearing Analytic
EDR-SYM27-RUN Suspicious Process Activity – Targeted – Boot Recover Disable Analytic
EDR-SYM6-ERI Suspicious Process Activity – Rare Process/MD5 For Host Analytic
WEL-ACC6-BPI Suspicious Account Activity – Peak Sensitive Privilege Access For a Host Analytic
WEL-ACC7-BPI Suspicious Account Activity – Peak Explicit Credentials Distinct Account Name For Host Analytic
WEL-DC1-BPI Suspicious DCOM Activity – Peak Distinct DCOM Destination Communication Error Analytic
WEL-ACC10-RUN Suspicious Account Activity – Peak Credential Validation Distinct Account Name For Host Analytic
WEL-ACC11-RUN Suspicious Account Activity – Peak Credential Validation Increase For Host Analytic
WEL-SHR1-ERI Suspicious Network Activity – Rare IPC$ Share Access Source For Host Behavior
References
- Annie Palmer. Russia was behind the ‘Olympic Destroyer’ malware and tried to pin the cyber attack on North Korea, report claims. AFP. 25 February 2018. http://www.dailymail.co.uk/sciencetech/article-5433083/Russia-hacked-Olympics-computers-turned-blame-N-Korea-report.html. Last accessed: 2-26-2018.
- Ellen Nakashima. Russian spies hacked the Olympics and tried to make it look like North Korea did it, U.S. officials say. Washington Post. 24 February 2018. https://www.washingtonpost.com/world/national-security/russian-spies-hacked-the-olympics-and-tried-to-make-it-look-like-north-korea-did-it-us-officials-say/2018/02/24/44b5468e-18f2-11e8-92c9-376b4fe57ff7_story.html?utm_term=.4441e6cbaae7. Last accessed: 2-26-2018.
- Warren Mercer et al. Olympic Destroyer Takes Aim At Winter Olympics. CIsco Talos Blog. February 12, 2018. http://blog.talosintelligence.com/2018/02/olympic-destroyer.html Last accessed: 2-26-2018.
- Panda Labs. Cyber Sabotage at the Winter Olympics. Panda Labs. February 15, 2018. https://www.pandasecurity.com/mediacenter/pandalabs/cyber-sabotage-winter-olympics/. Last accessed: 2-26-2018.
- Paul Rascagneres et al. Who wasn’t responsible for Olympic Destroyer. Cisco Talos. February 26, 2018. http://blog.talosintelligence.com/2018/02/who-wasnt-responsible-for-olympic.html. Last accessed: 2-26-2018.
- Zaid Shoorbajee. McAfee Uncovered New Malware In Olympics Hacking Campaign. McAfee Blog. February 3, 2018. https://www.cyberscoop.com/winter-olympics-hacking-mcafee/. Last accessed: 2-26-2018.




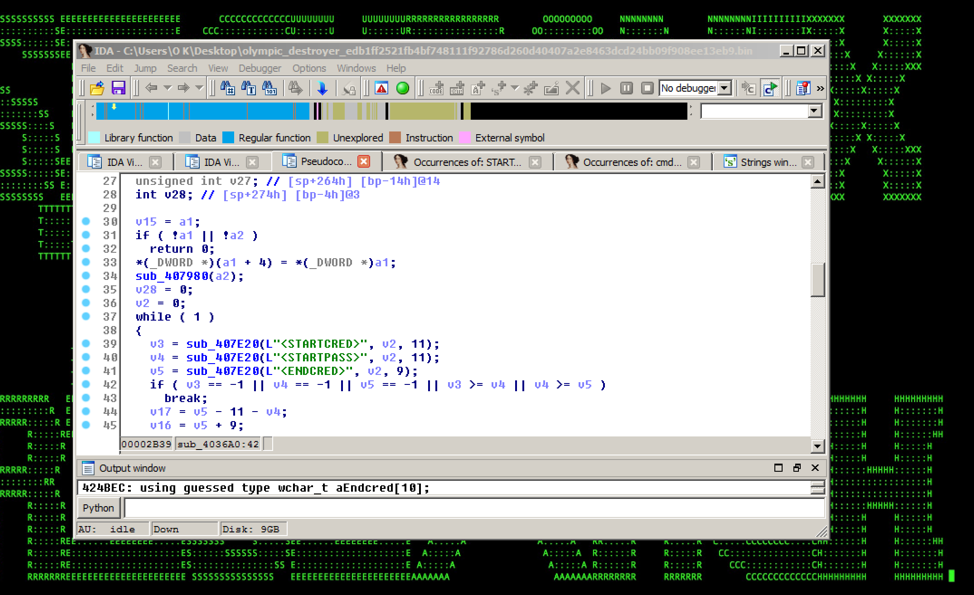 Figure 2: Olympic Destroyer – Credential Stealing
Figure 2: Olympic Destroyer – Credential Stealing