- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
UEBA
We’ve all seen big data breaches in the news. We also know there are many more breaches that did not make it into the evening news. The insider attack vector – whether it is a malicious insider, an unsuspecting compromised employee, or accidental misuse, is a common theme across most of these data breaches. According to the 2018 Inside Threat Report by Cybersecurity Insiders 90% of organizations surveyed feel vulnerable to insider threats.
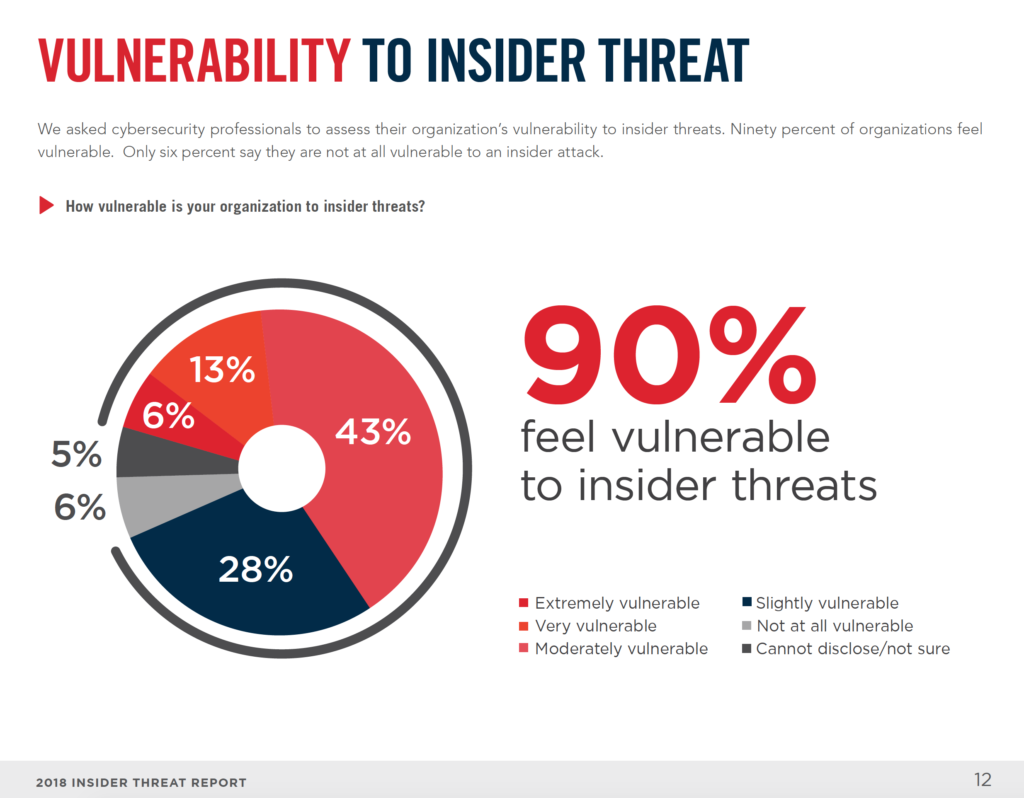
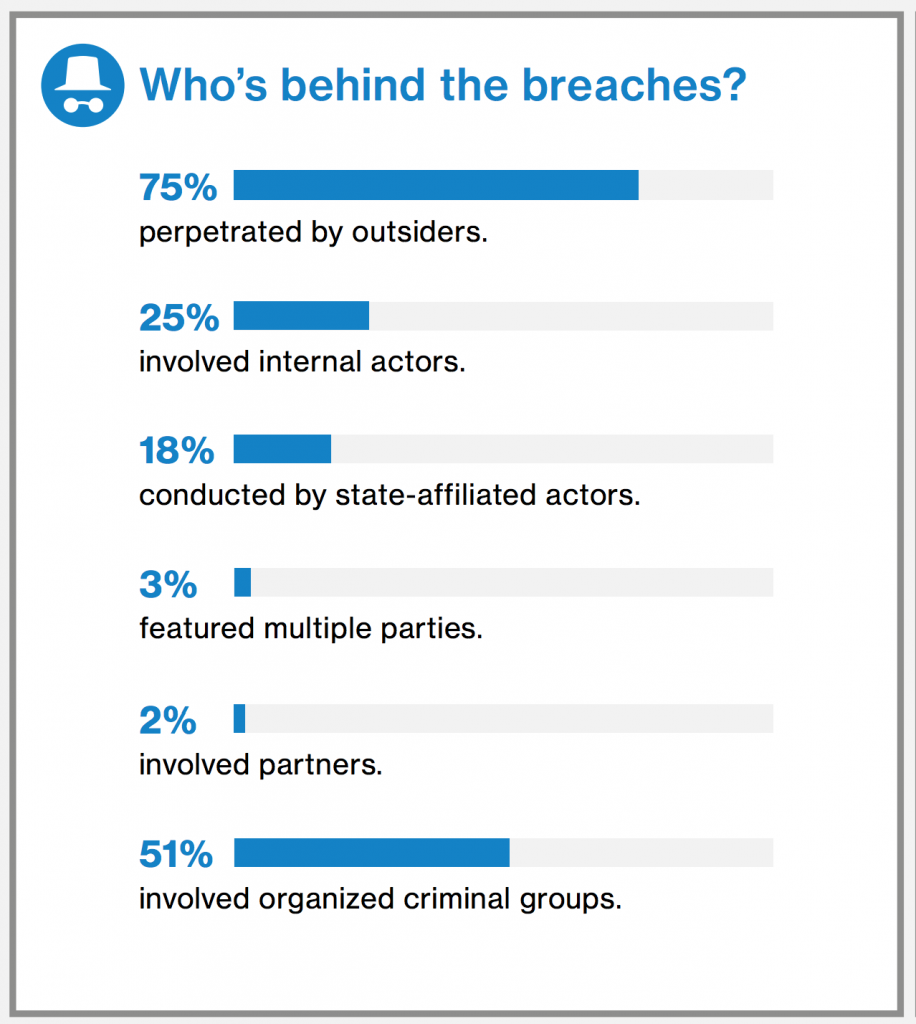
Security environments have historically focused on keeping external actors out, however, according to the 2017 Verizon Data Breach Investigations Report, one out of every four identified breaches involved an internal actor.
User and Entity Behavior Analytics (UEBA) has been specially created to combat these types of threats. As you research UEBA solutions, however, it helps to understand the five core use cases to look for.
- Insider Threats – Discover compromised users; including actively malicious activity by trusted insiders or innocent mistakes made by employees.
- Privileged Account Misuse – Monitor accounts with elevated permissions to make sure they are not being used in a manner they are not supposed to be.
- Cyber Security Threats – Discover if a system in your network starts acting in a way that indicates that it has been compromised or if it is being used in a way it shouldn’t be.
- Application Monitoring – Discover if your applications start acting in a way that indicates they have been compromised or are being used in a way they shouldn’t be.
- Cloud Security Monitoring – Discover if your cloud assets start acting in a way that indicates they have been compromised or are being used in a way they shouldn’t be.
At a minimum, these are the five basic use cases that a UEBA solution needs to be able to accomplish. Beyond these five basic use cases, there is a set of key capabilities that your UEBA solution should have in order to address the use cases above.
A basic UEBA solution must be capable of two things at a minimum:
- Collecting user and entity information from various disparate sources and enriching the data with context in real-time.
- Applying multiple sophisticated analytics techniques including unsupervised machine learning, peer analysis, and robotic patterning to the information in order to find the anomalies.
An intermediate UEBA solution will go beyond detecting anomalies and include security operations functions so you can respond to threats faster. Such as:
- Search and Investigation – Easily search and dig down through enriched events, visualize connections between related events, and run ad-hoc reports as needed.
- Incident Response and Case Management – Semi- or fully-automated incident response playbooks with built-in case management workflows are provided so you can easily take action on alerts. Alternatively, smoothly integrate your UEBA solution with your existing case management tool.
An advanced UEBA solution will expand these capabilities to your cloud environment. With increasing numbers of organizations moving more business functions to the cloud, the ability to extend the same level of security to your cloud assets is critical.
Learn more and view a live demonstration of Securonix User and Entity Behavior Analytics in action in this recorded webinar hosted by Nitin Agale, Senior Vice President of Products at Securonix, and David Swift, Principal Engineer at Securonix.







