- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
- MSSPs
- Scale multi-tenant security with predictable economics.
-
- Resources
- Partners
- Company
- Blog
Incident Response and Forensics, Threat Research
Securonix Threat Research Security Advisory
Simulating CVE-2025-53770 in SharePoint for Real-World Detection Engineering
Securonix Threat Research: Tim Peck, Abhishek Narasimhan, Sai Tadimeti
Product Management: Kumaramanivel Ramanathan
On July 19, 2025, Microsoft disclosed a critical vulnerability in SharePoint: CVE-2025-53770, a remote code execution (RCE) flaw actively exploited in the wild.
Microsoft Statement: “Microsoft is aware of active attacks targeting on-premises SharePoint Server customers by exploiting vulnerabilities partially addressed by the July Security Update. These vulnerabilities apply to on-premises SharePoint Servers only. SharePoint Online in Microsoft 365 is not impacted.
Microsoft has released security updates that fully protect customers using SharePoint Subscription Edition and SharePoint 2019 against the risks posed by CVE-2025-53770, and CVE-2025-53771. Customers should apply these updates immediately to ensure they’re protected.”
Based on prior exploitation patterns (example: ProxyShell, ProxyLogon, and other SharePoint RCEs), the Securonix Threat Labs team launched a proactive simulation campaign to model potential exploit telemetry. The objective: create robust, behavior-based Out-of-the-Box (OOTB) detection content tailored for this attack class.
Simulating exploitation: What We Did?
To replicate this attack in a lab environment we took a simulation driven approach to understand potential exploitation behavior and generate telemetry that could inform reliable detections. Microsoft’s guidance was invaluable here: they highlighted that malicious actors may abuse SharePoint’s LAYOUTS directory to deploy a file named spinstall0.aspx and that the attack path involves IIS’s w3wp.exe process.
While we did not attempt to reproduce the underlying vulnerability, we emulated post exploitation behaviors consistent with the described attack chain: specifically, creating suspicious files within SharePoint’s LAYOUTS directory and spawning child processes from w3wp.exe. These actions allowed us to capture realistic event data that defenders can use to build and validate detections.
Since exploitation of the IIS process is a result of the attack chain, we can replicate the attack in a controlled way. To do this we can simply use either another known IIS exploit or simply inject into the process to mimic the behavior. This provides accurate logging telemetry and after log verification, telemetry matches that in Microsoft’s guidance report.
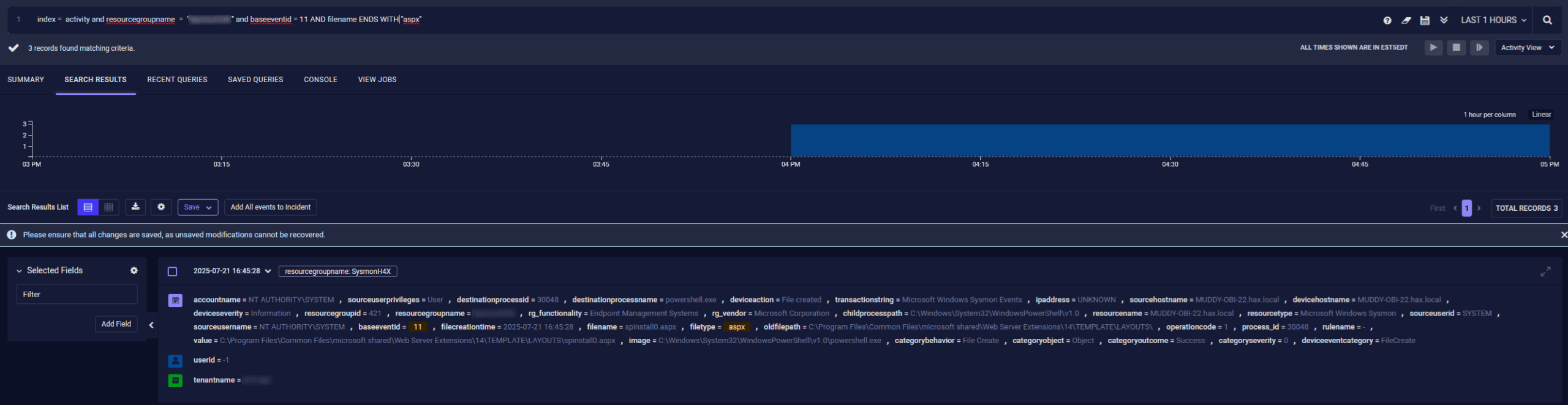
File Creation Simulation (Event ID 11) We simulated a malicious file drop by executing a malicious PowerShell script. This matches Microsoft’s hunting query:
Event ID: 11 (File Create)
Parent Image: w3wp.exe
Image: cmd.exe or powershell.exe
TargetFilename: C:\Program Files\Common Files\microsoft shared\Web Server Extensions\16\TEMPLATE\LAYOUTS\spinstall0.aspx
User: NT AUTHORITY\SYSTEM
This mirrors the exact indicators Microsoft suggested defenders watch for. In our platform, this telemetry is visualized and flagged as part of a new detection we’ve introduced targeting suspicious web-accessible file creation within SharePoint.
And the result produces logs that would match this query:
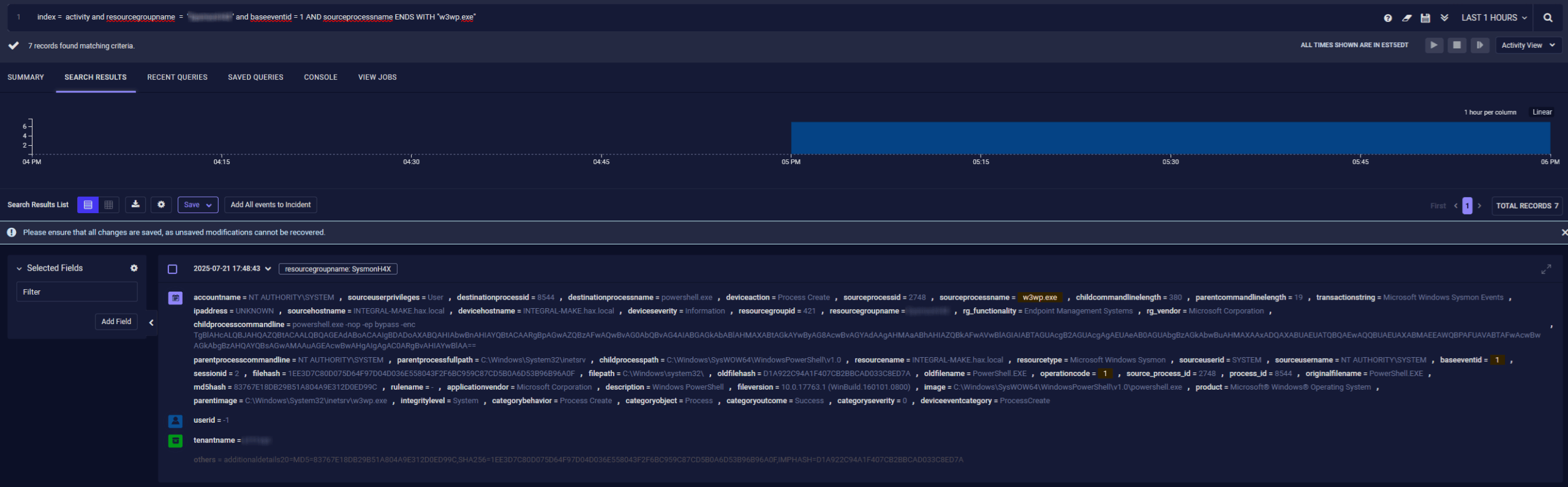
Post-Exploitation Behavior (Sysmon Event ID 1) To simulate likely follow-on actions by an attacker post-exploit, we executed a PowerShell command under w3wp.exe via a simulated code execution vector. This generated a Sysmon Event ID 1, showing a child process spawned by the IIS worker process:
Event ID: 1 (Process Create)
ParentImage: C:\Windows\System32\inetsrv\w3wp.exe
Image: powershell.exe or cmd.exe
CommandLine: powershell.exe -w 1 -nop -ep bypass -enc UwBlAHQALQB…
User: NT AUTHORITY\SYSTEM
This activity strongly resembles webshell behavior, especially when executed from w3wp.exe under SYSTEM context. In our telemetry, we tagged and correlated this event to our second detection logic, which flags unexpected PowerShell (or cmd.exe) execution from IIS/SharePoint worker processes.
By using simulation, we were able to closely mirror the expected behaviors of a real exploit chain without relying on a PoC. This allowed us to test, tune and validate detections proactively before any public tooling or widespread abuse of surfaces.
Detection Engineering: OOTB Use Cases You Can Deploy Today
Based on our telemetry, we engineered a suite of detections now shipping with Securonix OOTB content packages. These cover both pre-exploitation indicators and post-exploitation behaviors:
Possible Web shell Activity by Suspicious Parent Child Process Analytic (EDR-ALL-1000-RU)
Functionality: Endpoint Management Systems
Policy Logic:
Detects known dual-use tools or LOLBINs (example: certutil.exe, bitsadmin.exe, powershell.exe, cmd.exe) launched from suspicious parent processes like w3wp.exe, php-cgi.exe, or tomcat.exe
Covers a broad range of process creation telemetry sources (ProcessCreate, ChildProc, SyntheticProcessRollup2, etc.)
Why It Works: A classic signature of web shell access is a system binary or script engine launched directly from a web-facing service. These analytic flags rare or dangerous utilities typically abused post-exploitation.
Possible Webshell Activity – Rare process spawned from Web server worker process (EDR-ALL-81-ER)
Functionality: Endpoint Management Systems
Policy Logic:
Triggers when w3wp.exe spawns LOLBINs such as rundll32.exe, regsvr32.exe, or mshta.exe
Focuses on rare process lineage paths and out-of-profile child binaries
Why It Works: The SharePoint worker process should not normally execute these binaries. Such events strongly correlate with remote code execution for payload delivery.
Rare encoded PowerShell Command (PSH-ALL-113-ER)
Functionality: Microsoft Windows Powershell
Policy Logic:
Detects PowerShell scripts using -enc, -encodedCommand, invoke-obfuscation, or other encoding techniques
Applies to ScriptBlock and CommandLine metadata fields
Why It Works: Encoded PowerShell is a hallmark of obfuscation and staging in malware and offensive frameworks. This analytic target evasive script delivery during or post exploitation.
Suspicious File Drop in SharePoint Layouts Folder Analytic
Functionality: Endpoint Management Systems
Policy Logic:
Monitors creation of new or unusual files in:
\Web Server Extensions\16\TEMPLATE\LAYOUTS
\Web Server Extensions\15\TEMPLATE\LAYOUTS
\Web Server Extensions\14\TEMPLATE\LAYOUTS
Example: File names like spinstall0. *
Why It Works: The LAYOUTS folder is served directly to clients. Attackers may abuse this location to persist on malicious ASPX pages or load stagers through authenticated access.
Possible Web shell Activity – Rare process spawned from Web server worker process – Cloud EDR (CEDR-ALL-81-ER)
Functionality: Cloud Antivirus / Malware / EDR
Policy Logic:
Flags child process launches from cloud-hosted web server applications
Why It Works: For this particular RCE, Microsoft has claimed Attacks on SharePoint are limited to traditional on-prem environments. This detection ensures visibility into process anomalies through EDR telemetry logs.
For Threat Hunters: Guided Hunt Queries
Use the following spotter queries as a starting point for proactive hunting:
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “Process Create” OR deviceaction = “ProcessCreate” OR deviceaction = “Process Create (rule: ProcessCreate)” AND sourceprocessname = “w3wp.exe” AND (destinationprocessname = “cmd.exe” OR destinationprocessname = “powershell.exe”)
rg_functionality = “Endpoint Management Systems” AND (deviceaction ENDS WITH “Written” OR deviceaction = “File created”) AND customstring49 ENDS WITH “.aspx” AND customstring49 CONTAINS “\Web Server Extensions\” AND customstring49 CONTAINS “\TEMPLATE\LAYOUTS”
Final Thoughts
While the exact exploit mechanism behind CVE-2025-53770 remains unconfirmed, organizations can and should act now.
By simulating exploitation behaviors and focusing on downstream effects, such as abnormal process spawning, anomalous payload delivery, and unauthorized outbound traffic, organizations can stay ahead of adversaries.
Our Threat Labs team continues to collaborate closely with researchers to refine these detections. Future updates will incorporate concrete indicators as our further analysis evolves.
Next Steps for Customers:
- Apply Microsoft’s July 2025 SharePoint security patches immediately and enable AMSI integrations
- Enable logging for IIS, Sysmon, and PowerShell
- Deploy Securonix OOTB detections as recommended above
- Monitor detections and tune baselines using the guided hunt queries above
Stay tuned for deep-dive technical updates from our Securonix Threat Labs team in the coming days.
References:
- Customer guidance for SharePoint vulnerability CVE-2025-53770
https://msrc.microsoft.com/blog/2025/07/customer-guidance-for-sharepoint-vulnerability-cve-2025-53770/ - From SOC Alert Triage to 0-day Mass Exploitation
https://research.eye.security/sharepoint-under-siege/







