- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Threat Research
Ransomware On The Rise With Bad Rabbit
For about a week now, a new ransomware campaign has been sweeping across computers. This is the third major ransomware campaign after WannaCry and NotPetya this year. Securonix Threat Research Labs has been tracking this campaign since its inception (technical details here), and here is what we know so far.
Initial targets are across Europe
The ransomware has struck organizations across Eastern Europe, with reports coming from Russia, Ukraine as well as parts of Turkey, Poland, and Germany. However, the ransomware does not seem to be limited to this geography and will certainly spread if precautionary steps are not taken.
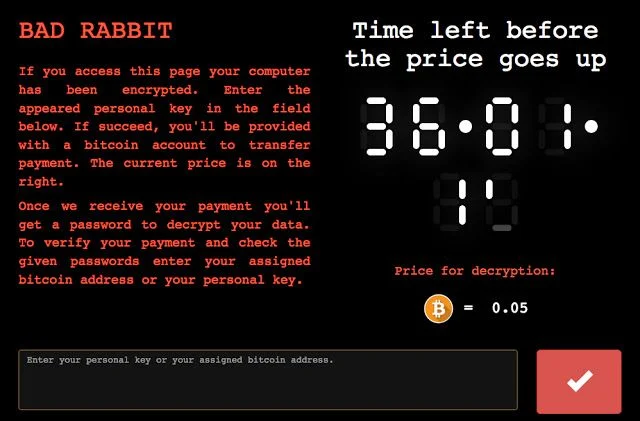
Ransomware: Payment via Bitcoin
As with most other ransomware strains, Bad Rabbit makes itself very visible as soon as the encryption part of the attack is completed. The device user is informed that their files are no longer accessible to them, and they may retrieve the files with a payment of 0.05 Bitcoin, which currently converts to about $285. This is in line with other variants that also demand initial payments of $300 – $500. The user has 40 hours to make the payment (a countdown timer is shown) after which the ransom goes up.
Infection Uses Fake Flash Plugin Update
This ransomware is spread through compromised websites that are hosting a JavaScript payload. The user visiting the site is instructed to update their Flash plugin. When the user accepts the download, the malicious code is installed on their machine via HTML injection. There are also “drive-by-download” versions that have been seen, in which the user’s device is infected just by browsing to the compromised website.
Lateral Movement Is Possible
The Bad Rabbit ransomware code, once downloaded to a user’s device has the capability to scan for, and move laterally via SMB shares. The ransomware utilizes default credentials for SMB user and password combinations to access other devices on the organization’s network. This capability, of course, makes the entire organization vulnerable to a crippling, large-scale ransomware attack and associated loss of service on affected devices/applications.
Common Sense Prevention Steps
Ransomware is, unfortunately, becoming a highly effective attack vector used by hackers to quickly and easily monetize their effort. While detection is critical to slow down the spread of Bad Rabbit across organizational networks, internet users must follow the basic guidelines that govern safe online activity. These habits include:
- Browsing only to safe sites and staying away from questionable web content.
- Maintaining a healthy suspicion of any update or download requests from websites
- If you suspect you have been a victim, quickly escalating the threat to your IT security teams
Securonix equips all implementations with the necessary machine learning algorithms and Spotter threat hunting queries for SOC analysts to find undiscovered instances of Bad Rabbit, and to quickly gather the information necessary to prevent a major impact to their organization.


